Trusted by
Unified Protection
Uptycs security analytics platform has been built ground up for scale, correlation, runtime detection and response with rich contextualization for real-time decision making. Uptycs provides a foundational platform based on first principles to Observe, Analyze and Contextualize everything to protect and secure your cloud infrastructure.
Hybrid cloud security at your fingertips
See with context everything you build and deploy in the cloud from development to runtime.
Prevent threats before they can cause damage and continuously harden security posture.
Focus on the threats and risks that matter with insights that correlate runtime and historical data across multiple attack surfaces.
Uptycs Solutions
Real-time hybrid and multi-cloud security
Workload Protection
Protect diverse technologies with agentless coverage, deep telemetry, and rich security.
Posture Management
Continuously monitor cloud resources to detect misconfigurations, contextualize risk, identify violations, and enforce least privilege.
Detection & Response
Real-time threat detection mapped to MITRE ATT&CK, securing workloads with full attack path visibility
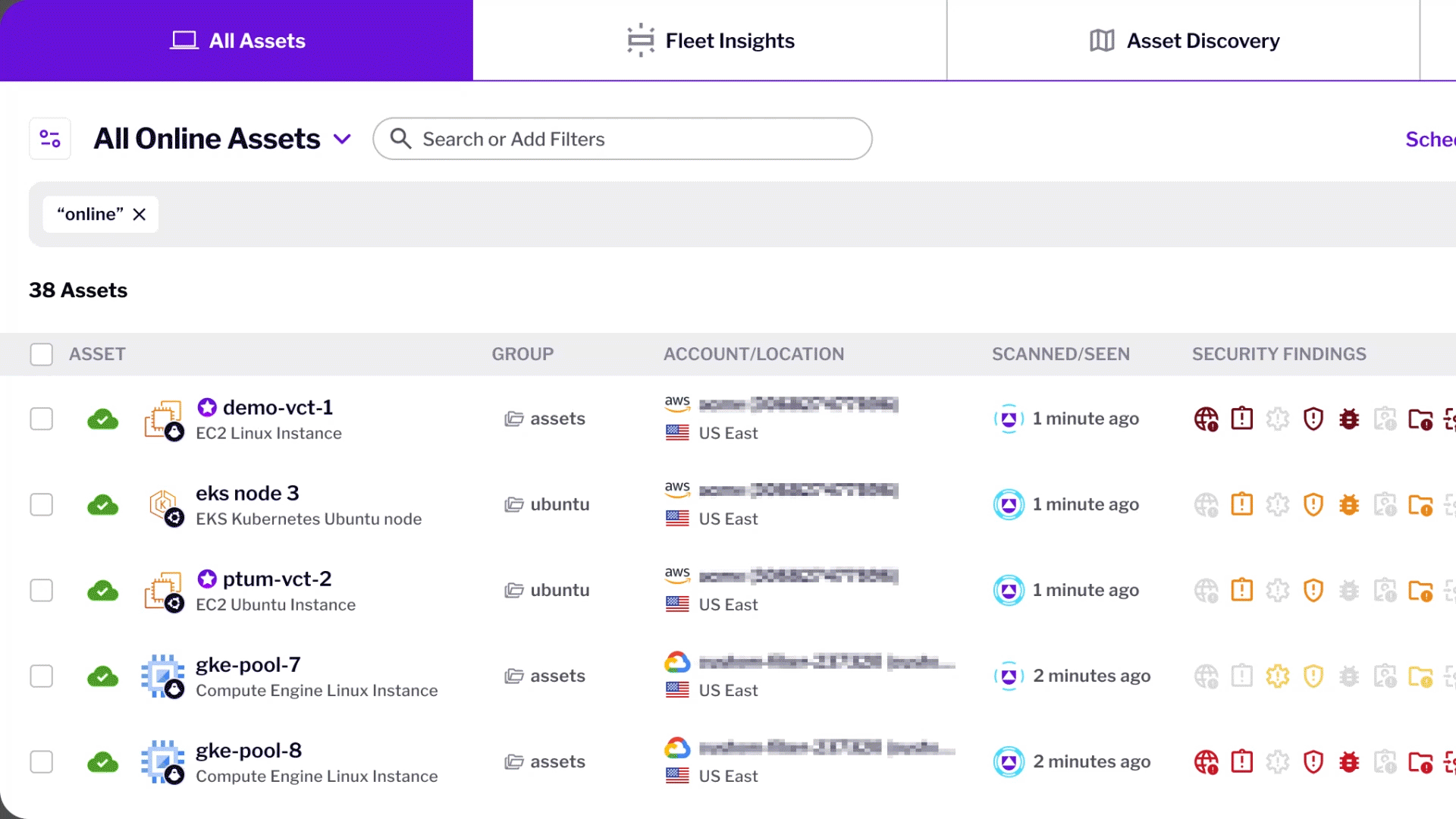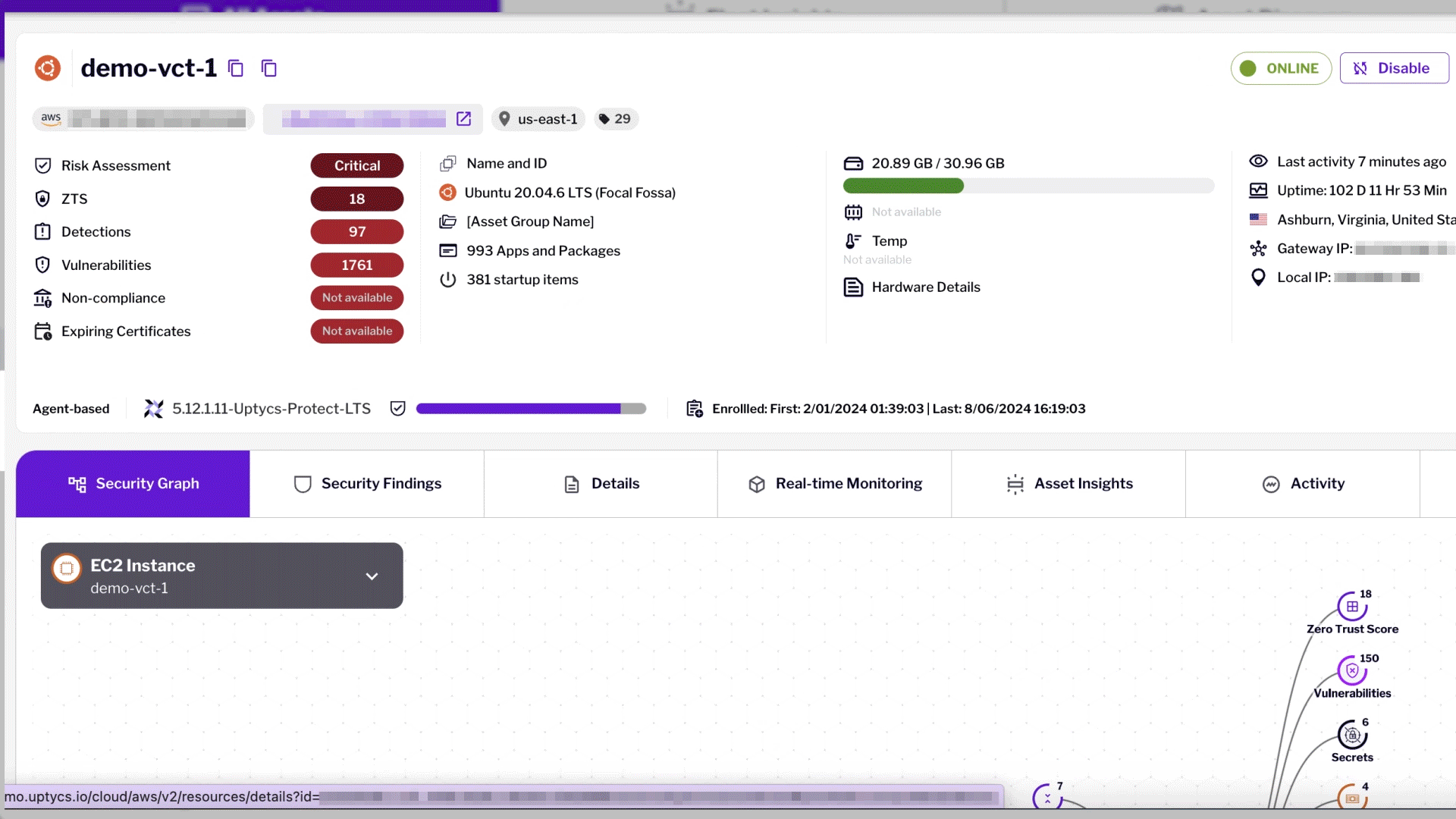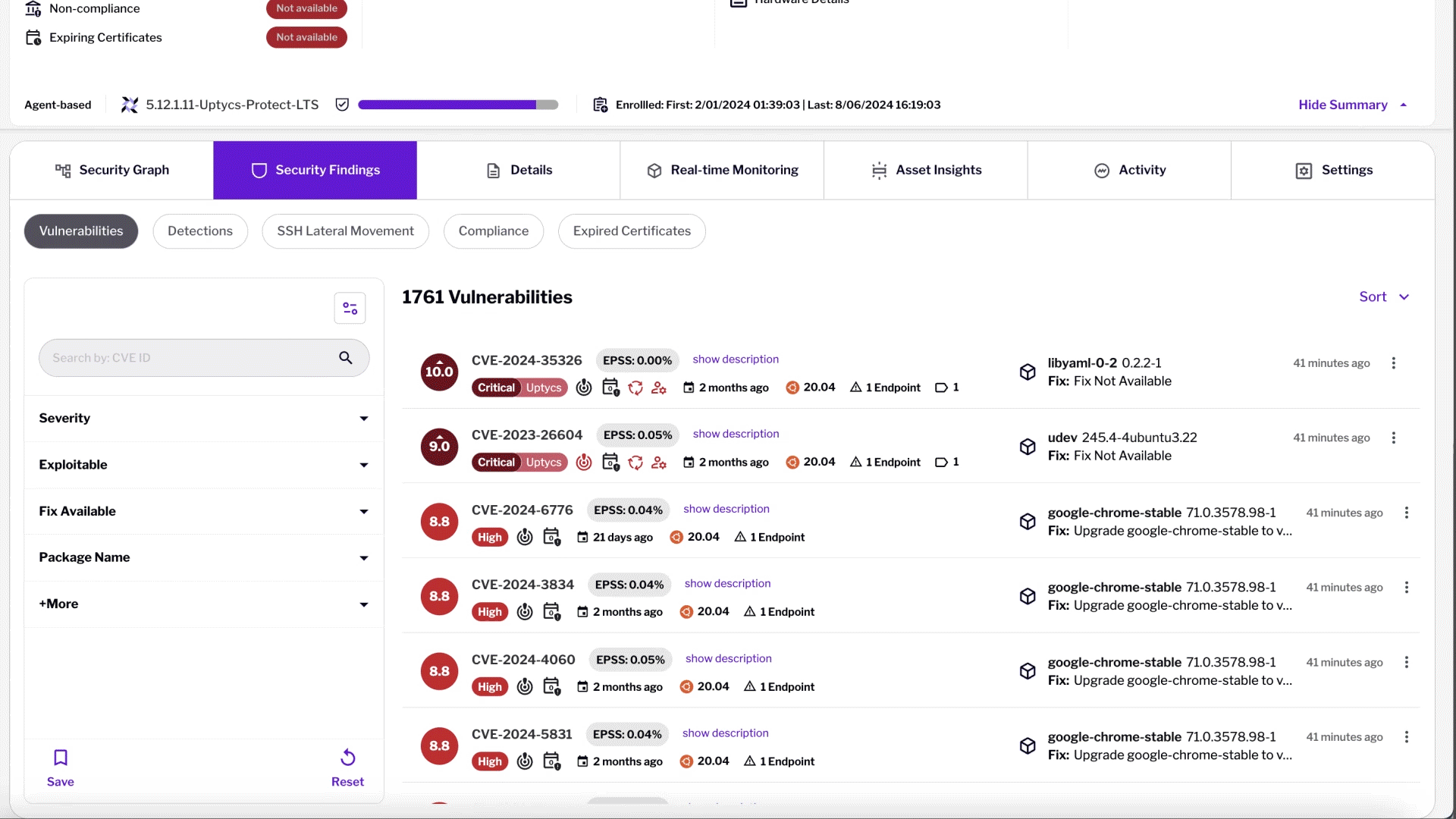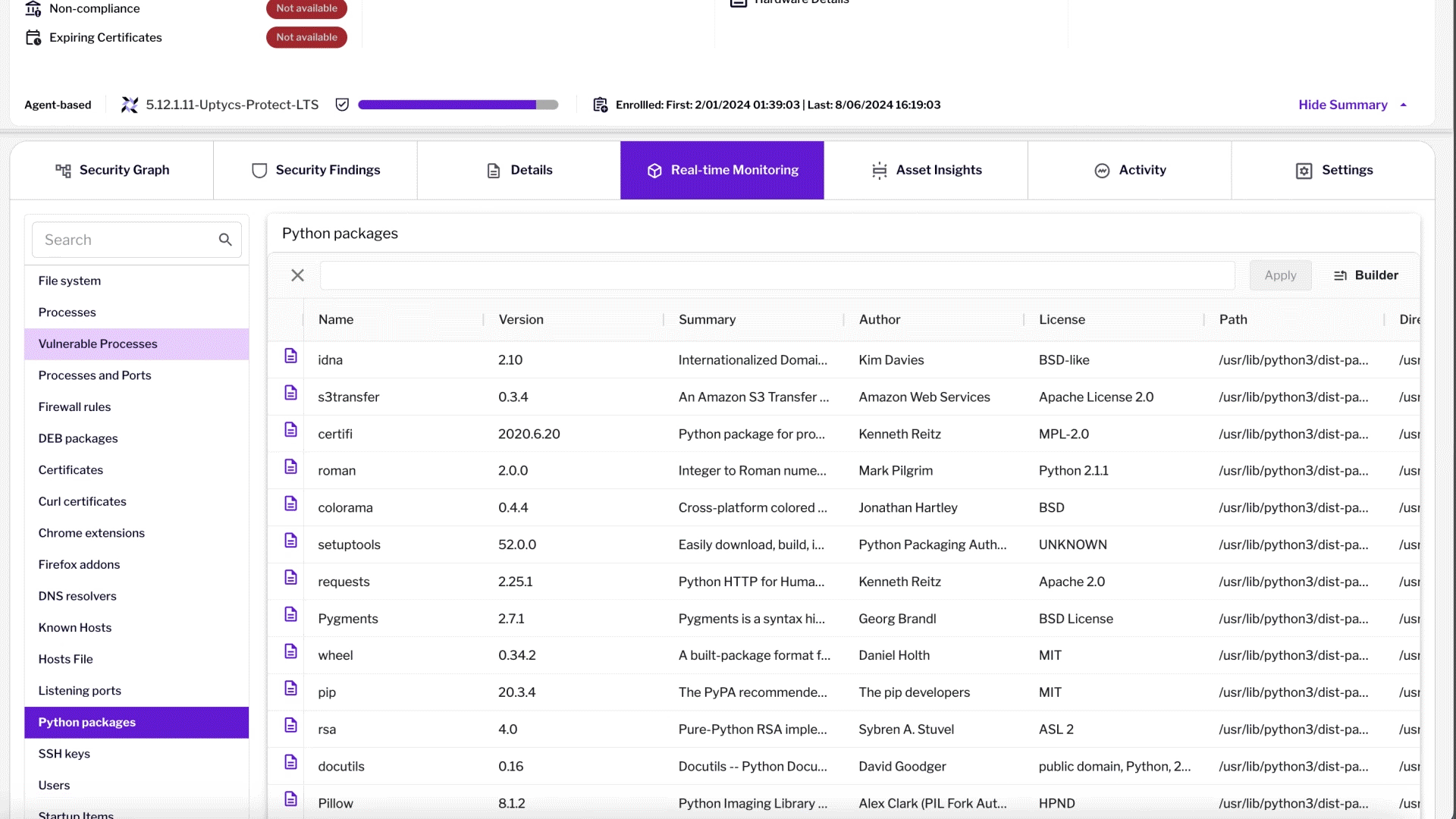
Asset Management
Identify cloud assets in real-time without using a sensor, ensuring an up-to-date inventory of both ephemeral and persistent cloud assets.
Risk & Compliance
Map compliance standards, customize for security, and use best practices. Prioritize findings across clouds.
Vulnerability Management
Centralized vulnerability view across apps, systems, and clouds. Prioritize, track metrics, manage exceptions, and automate remediation.
Software Pipeline Security
Scan CI/CD images for vulnerabilities, misconfigurations, and malware. Monitor and enforce security policies.
Top 3 Reasons Industry Leaders Choose Uptycs
- 1
- 2
- 3
Security Observability at Scale with Uptycs
Uptycs introduces the first cloud security solution with streaming telemetry-based observability, ensuring comprehensive protection of dynamic cloud infrastructure.
Observe Everything: Harness telemetry for configuration, state changes, behavioral shifts, and input/output flows.
Advanced Telemetry: Uptycs captures runtime (eBPF, Cloud-trail), configuration, and flow telemetry for scalable cloud signal extraction and correlation.
High-Fidelity Observability: Uptycs' eBPF-based syscall observability ensures seamless monitoring without affecting OS kernel stability.
Advanced Signal Processing and Analysis with Uptycs
Scalable Signal Processing: Utilizes a lambda architecture for real-time streaming and batch/ML processing of vast telemetry data.
Continuous Analysis: Constantly analyzes runtime data, including eBPF syscalls, to detect suspicious or malicious activity through graph-based and time-indexed correlation.
Context-Rich Security: Combines signal processing, lambda analytics, graph correlation, and ML to provide low-latency, high-fidelity findings.
Efficient Threat Operations: Delivers actionable insights for effective threat detection, response, and vulnerability management.
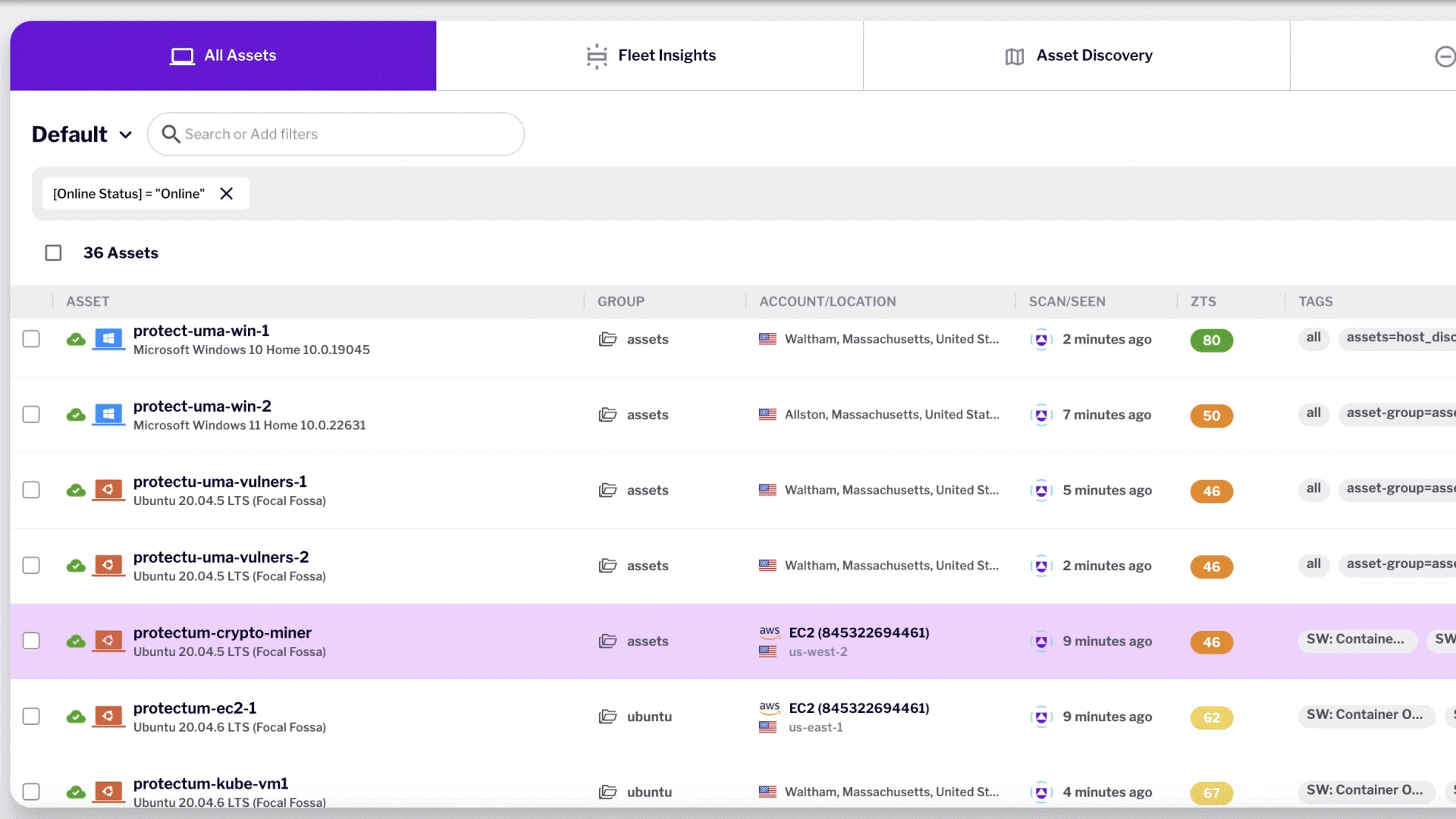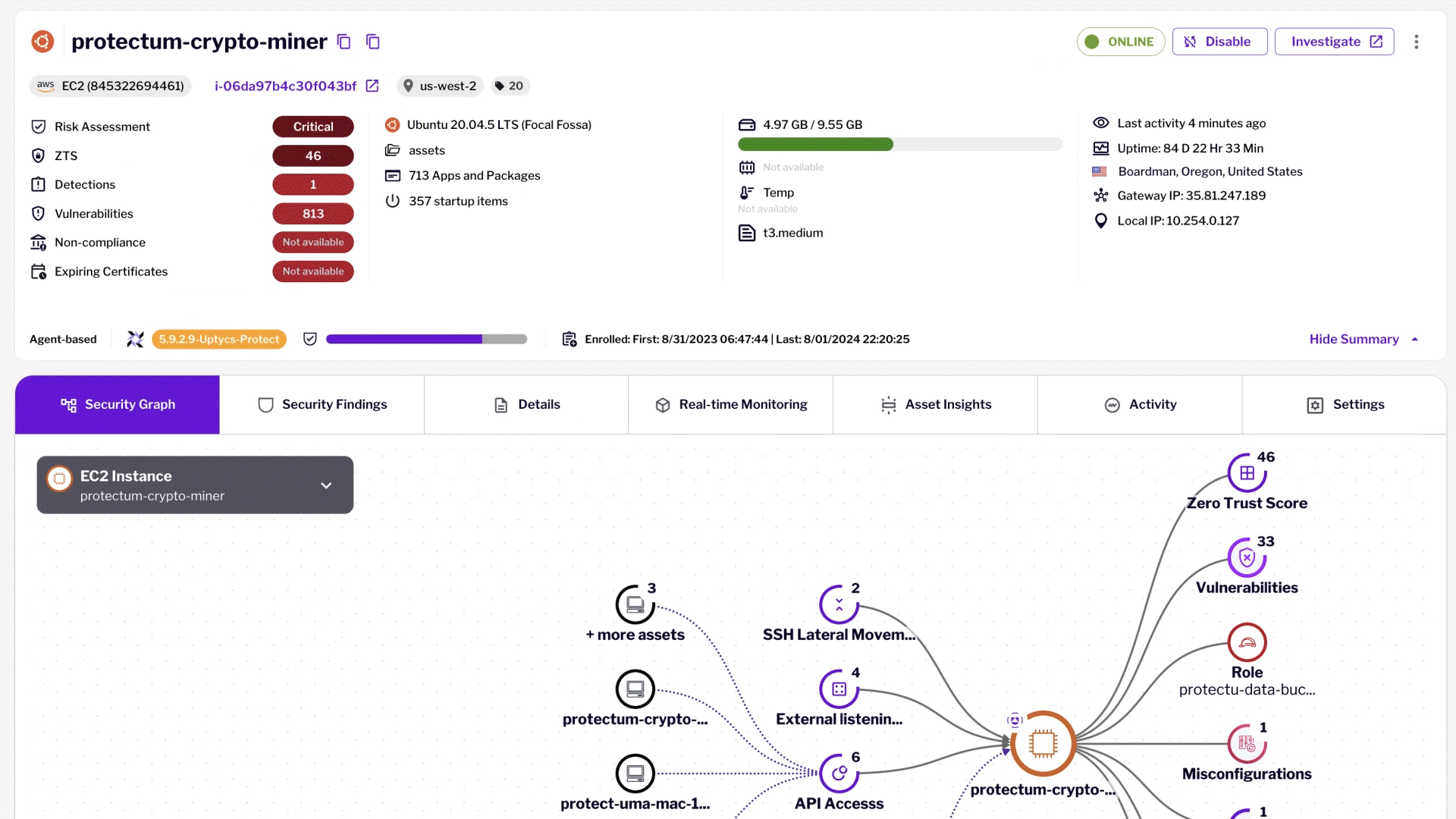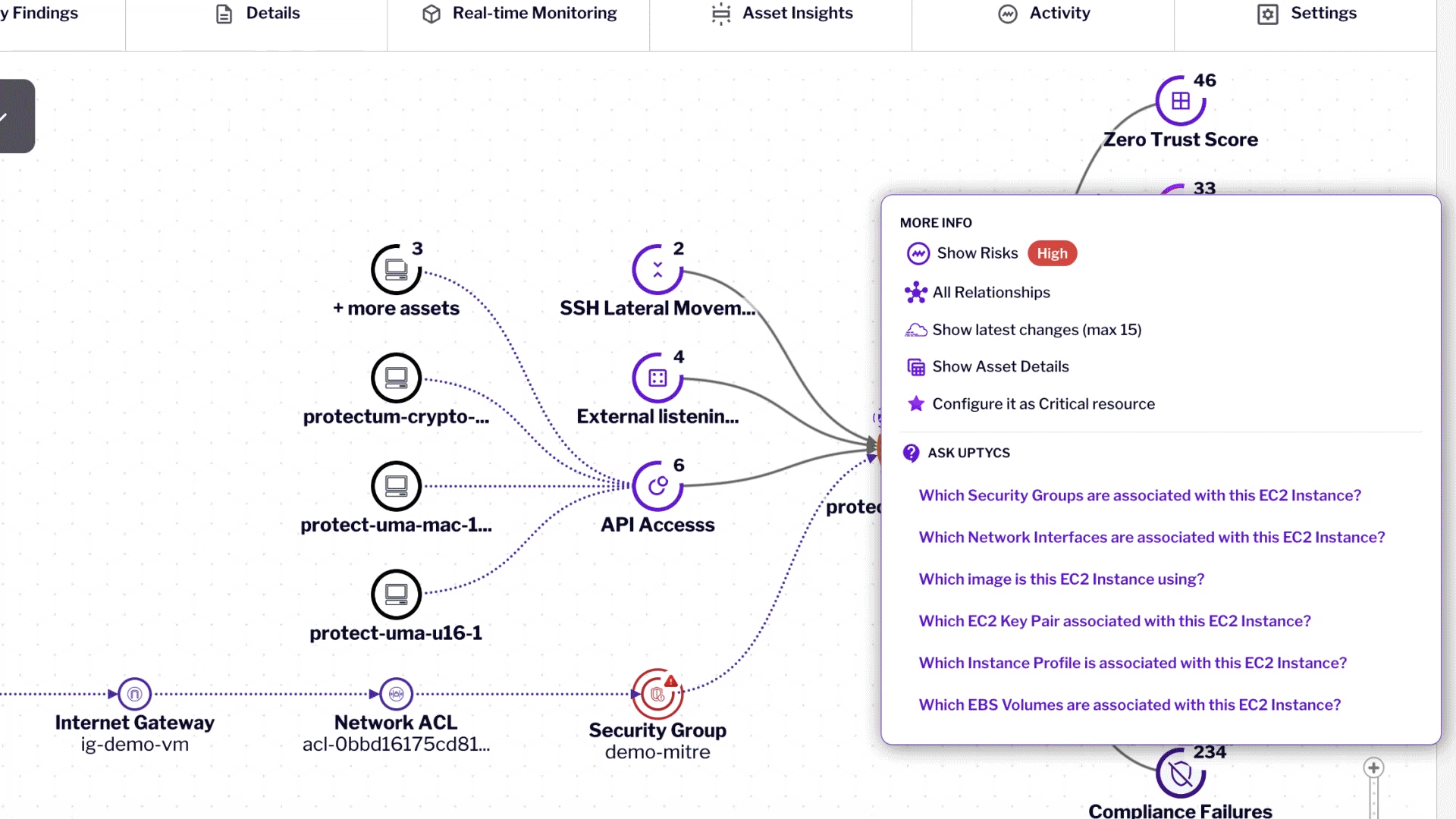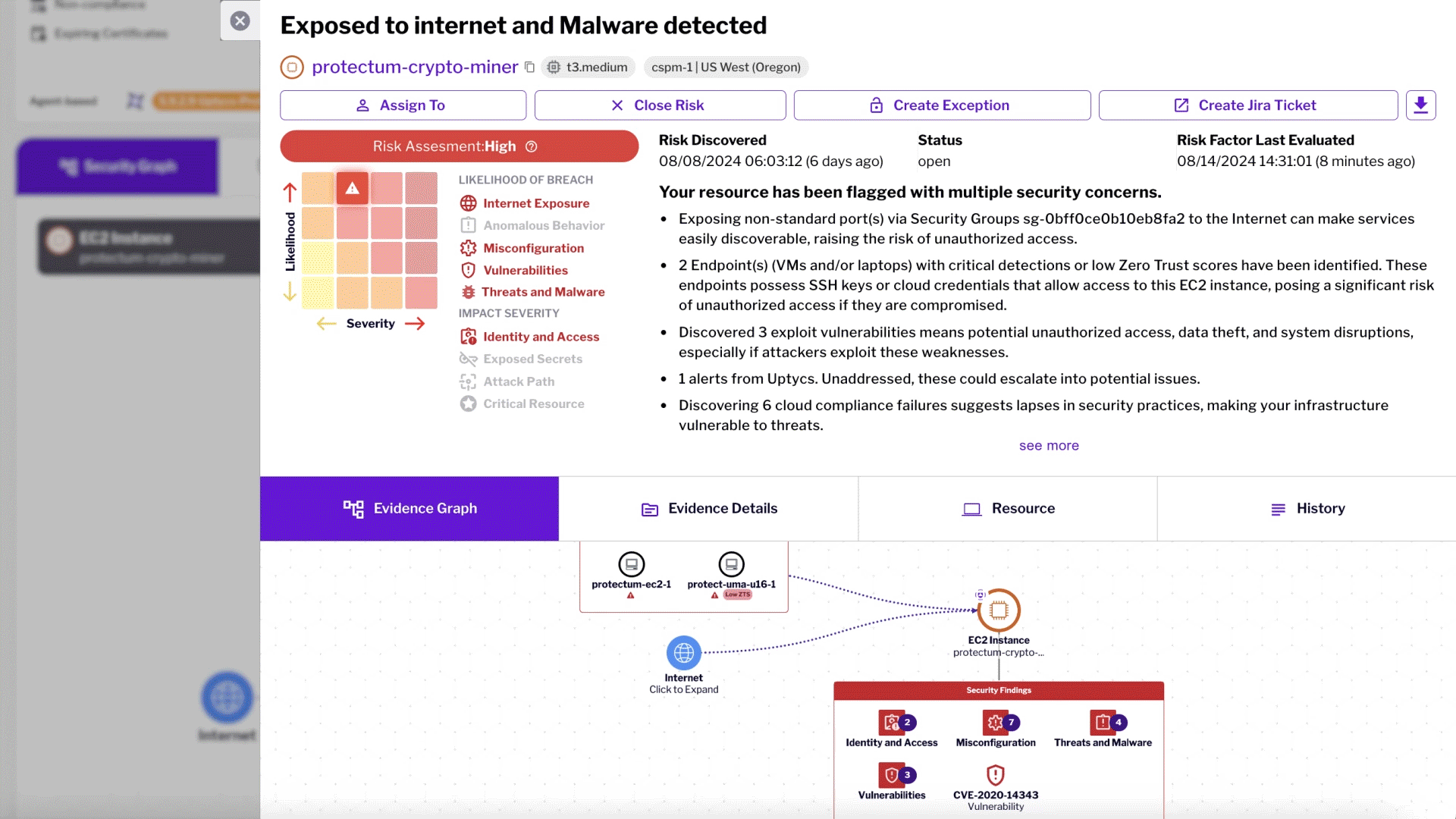
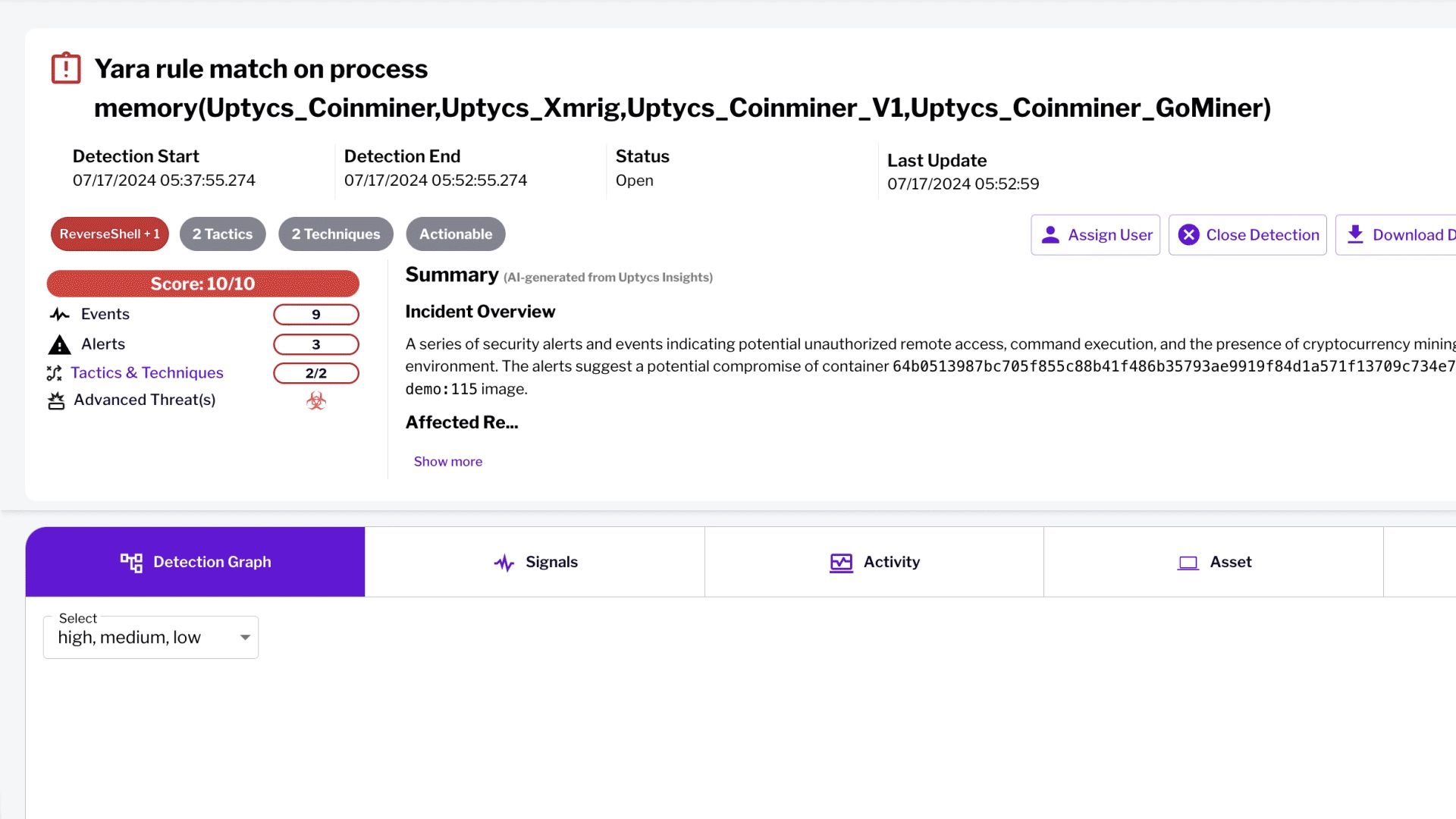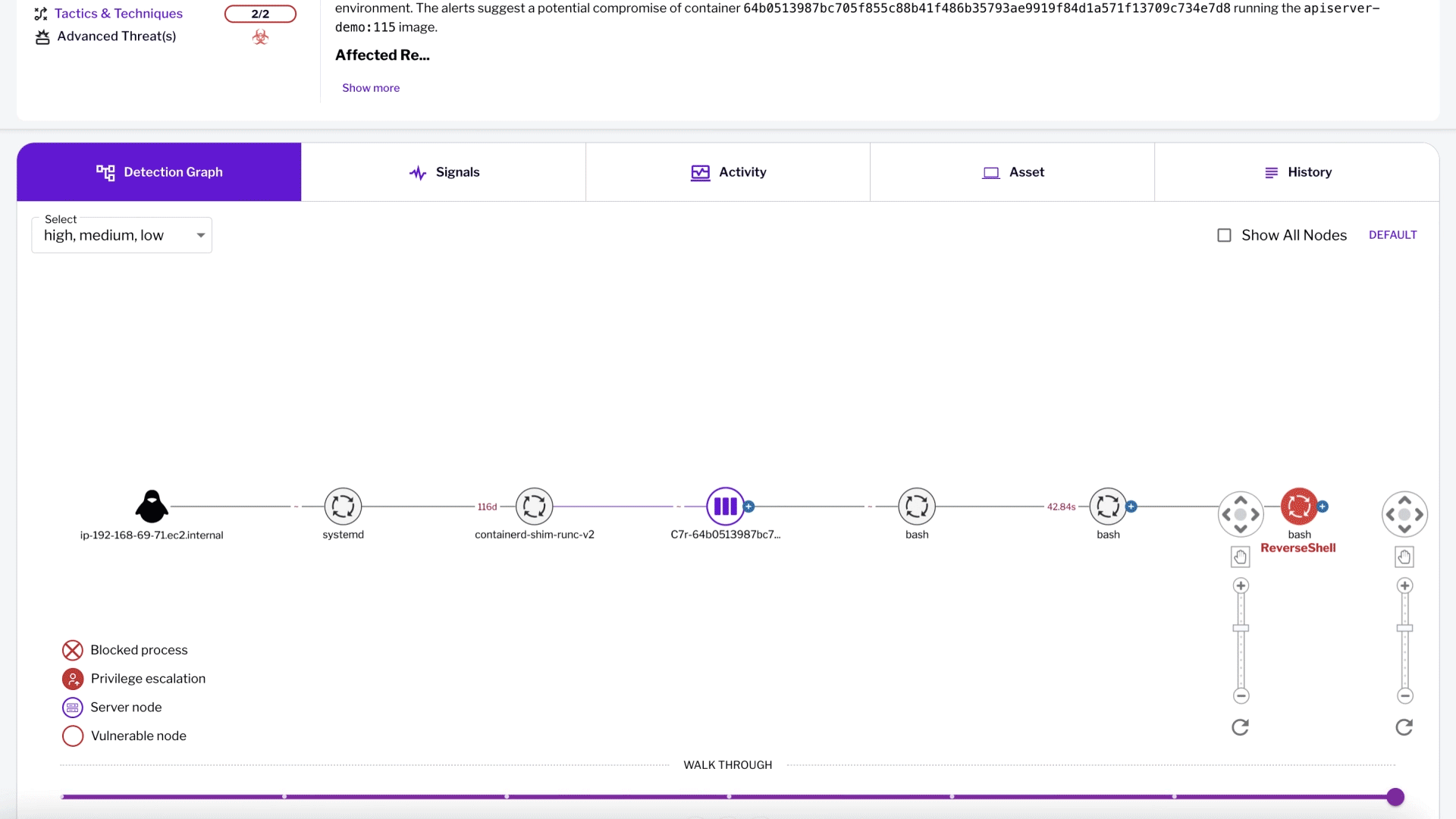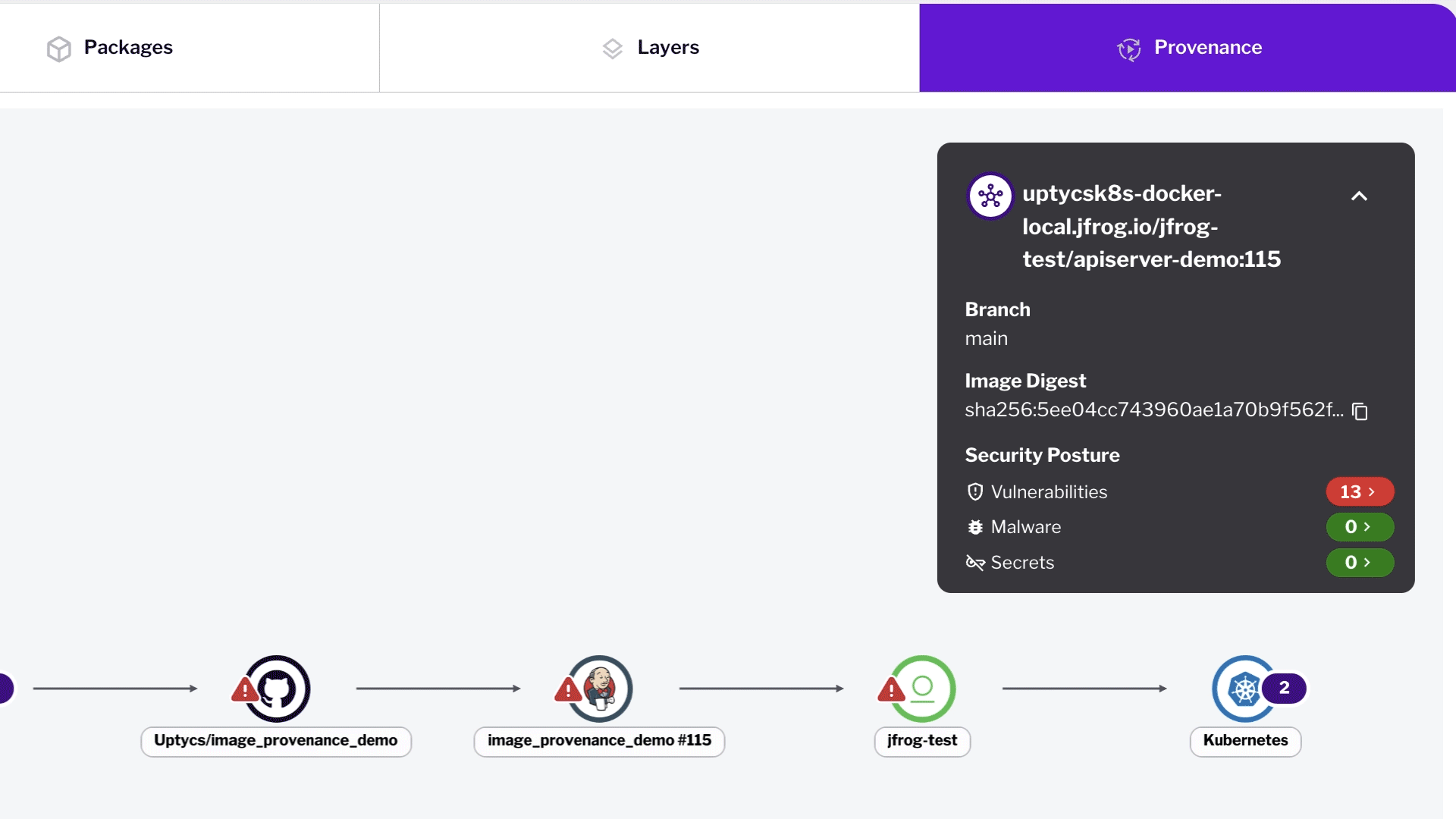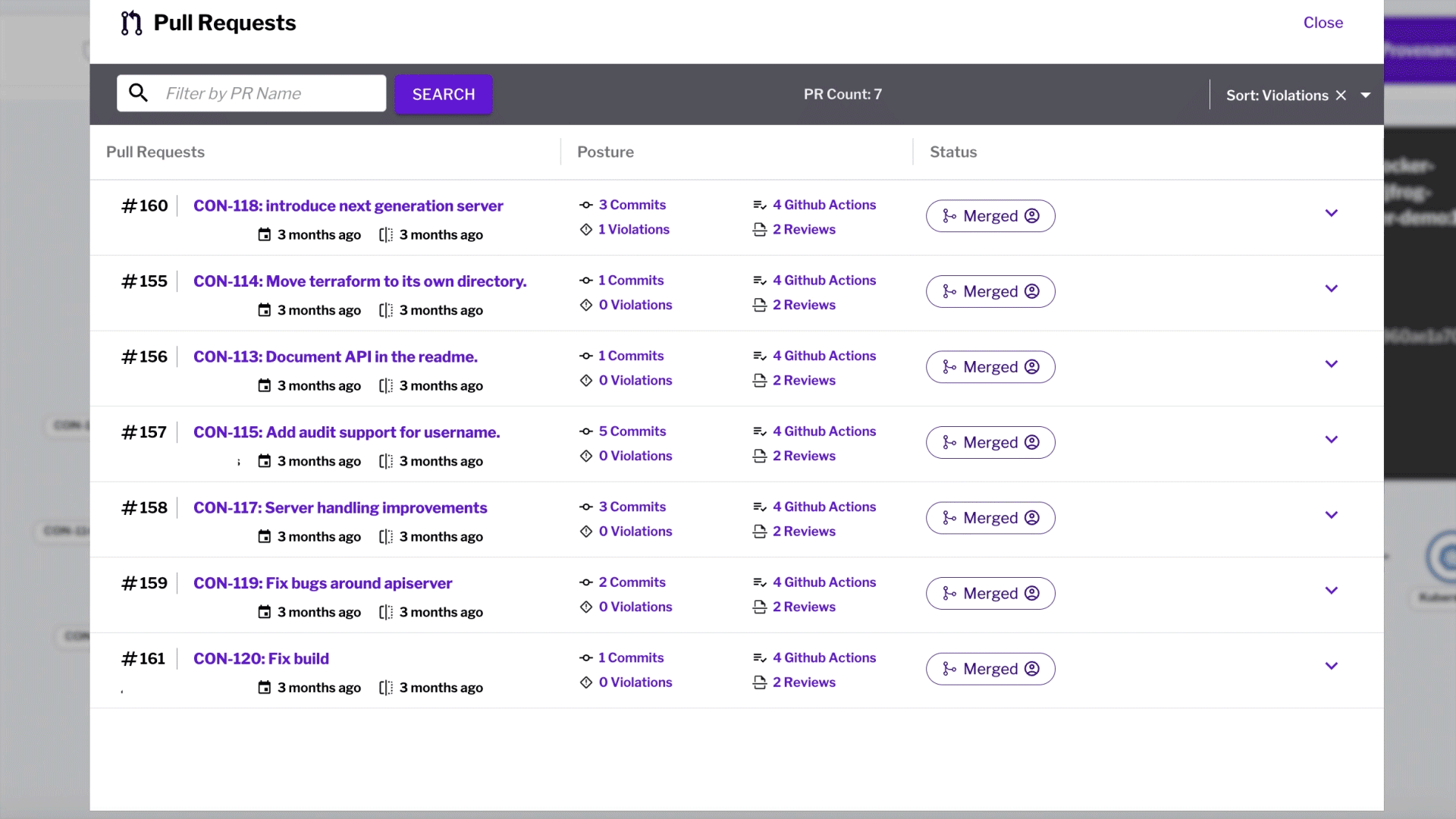
Unified Risk Prioritization and Protection with Uptycs
Uptycs integrates advanced features to streamline cloud risk prioritization and reduce alert fatigue.
Unified Risk Scoring: Combines static agentless posture management with runtime security insights for effective risk prioritization.
Centralized Risk Management: Consolidates risky combinations from across attack surfaces into a single location, focusing on critical threats.
Real-Time Threat Detection: Leverages advanced analytics and threat intelligence to detect and respond to malicious activity instantly.





.png)