What’s the single biggest thing you can do to improve your cloud security posture management? It’s not detecting advanced malware developed by nation states. You can dramatically improve your cloud security with a far more mundane task: making sure your cloud resources are configured correctly.
According to the shared responsibility model, a concept that outlines which entities are responsible for cloud security, cloud service providers take care of the physical infrastructure that underlie their services but customers must ensure that they’re using those services in a secure manner. That means keeping an up-to-date inventory of all cloud assets and resources, and ensuring all those entities adhere to security best practices. Turns out it’s surprisingly difficult to get comprehensive visibility across so many services and accounts.
Solve the Cloud Configuration Challenge
To solve this challenge, Uptycs has introduced a new integration with AWS that extends the types of data in our SQL-powered security analytics platform. Now, Uptycs customers have visibility into the AWS services that function as the control plane for cloud-hosted workloads.
For comprehensive cloud workload security, you need both a view of workloads from the outside and a view from the inside. Data from AWS services and resources provides an outside-in view of the cloud environment to complement the inside-out view from within hosts and containers that Uptycs already provides. Better still, Uptycs customers can get all this outside-in/inside-out data in a single place.
What types of risks can you expect to uncover with our new cloud security posture management offering? There are hundreds of insecure configurations and vulnerabilities that can lead to data leaks, privilege escalation, stolen credentials, and more, such as:
- The infamous open S3 bucket
- Insecure credential usage and settings, such as the “root” account on IAM not using hardware MFA
- APIs that might be exposing data or credentials
- Potential IAM policy violations, such as when an IAM role is created to establish a trusted relationship with a third party or when a deprecated IAM policy is used
- Evasion techniques, such as the deletion of VPC Flow Logs or when a new inbound rule is added to a security group
- Attacker network activity matched to Uptycs’ threat intelligence database against AWS CloudTrail logs and VPC Flow Logs
- Dangling DNS records in AWS Route 53 zones
Watch the short video below to see how our new cloud security offering works.
Answering cloud configuration and security questions fast
Streaming AWS data into Uptycs makes it possible to easily answer questions such as: “Which hosts and resources are non-compliant?” “Do I have a vulnerability?” and “Have my hosts been compromised?”
This ability to query your cloud infrastructure helps with inventory, policy monitoring, compliance, and threat detection in the cloud.
Keep an up-to-date inventory of all cloud assets and resources
You can’t secure what you can’t see, and right now, organizations can’t easily see or manage all of the resources and assets running across their AWS accounts. Uptycs’ cloud security posture management equips organizations with inventory capabilities for AWS resources and services and the assets that are consuming them. Users can group and tag their cloud-based assets and resources across accounts, and run queries and reports for information such as service configurations. In a single place, you can answer questions about your entire cloud estate such as “What cloud-based assets do I have running and where?” and “What are my cloud service configurations?”
Adhering to best practices to avoid data leaks, stolen credentials, and more
Uptycs makes it easy for security teams to ensure that their AWS resources across accounts are adhering to best practices. This helps you hold up your part of the shared responsibility model and proactively identify and remediate risk.
Uptycs ingests and analyzes AWS services data to alert teams to insecure configurations, track configuration history, and provide details that engineers need to quickly remediate issues. With Uptycs in place to monitor for risk and alert in real time, security teams can mitigate risk by continuously monitoring the security posture of cloud workloads and resources, and strike a balance between protecting the data and applications and enabling developers and operations teams to move fast.
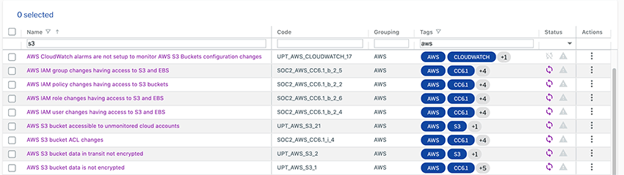
A sample of the rules representing security best practices for AWS S3. Uptycs makes it possible to easily monitor major services such as EC2, EBS, and RDS as well as newer container-focused services such as ECS and EKS. (Click to see larger version.)
Compliance with standards such as CIS Benchmarks for AWS
Many businesses need to comply with various standards to do business (SOC 2, PCI DSS, FedRAMP) or to demonstrate adherence to best practices (CIS Benchmarks for AWS). It is time consuming to gather the evidence needed to demonstrate compliance to auditors.
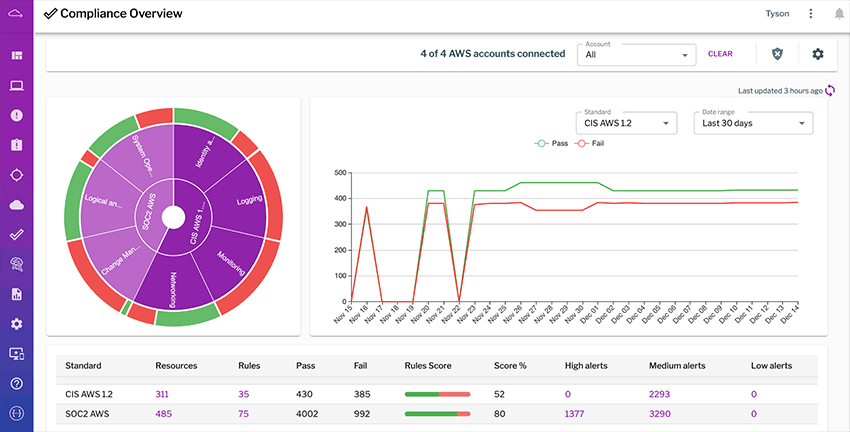
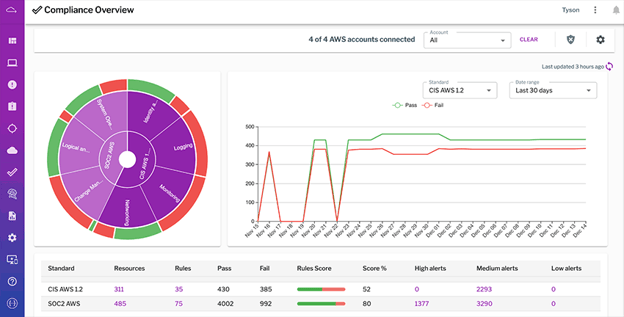
Uptycs makes demonstrating compliance with detailed evidence much faster. Security and compliance teams will know where they need to target their remediation efforts. Uptycs users can view summary visualizations of their compliance posture and they have the ability to drill down into non-compliant resources, associated evidence, and remediation guidance. They can instantly see the latest failed configuration checks, most non-compliant resources, time to resolve non-compliance, and more.
Uptycs makes compliance reporting easy by automatically gathering evidence and other needed information. (Click to see larger version.)
Detect risks and threats in the cloud
To minimize damage, security teams need to be aware of attacks directed against their cloud resources and be able to rapidly investigate possible incidents. Uptycs offers several powerful detection and investigation capabilities for the cloud:
- Uptycs ingests IAM policy rules to perform security assessments. In the cloud, if attackers can gain access or escalate their privileges through IAM, then they have the keys to the kingdom. As one of our customers has said, "IAM is a firewall for the cloud," because if IAM configurations are insecure, then other preventative protections become less relevant. Uptycs enables users to see which permissions are being used by entity (user and role) and when permissions were last used. Uptycs also produces alerts on policies with excessive permissions and monitors least-privilege access.
- Uptycs ingests AWS CloudTrail and VPC Flow Logs, and other relevant data, and matches this information against its curated threat intelligence database to detect threats in the cloud.
- To trace user activity during incident investigation, Uptycs also correlates activity with AWS CloudTrail logs and VPC Flow Logs.
Extending SQL-powered security analytics
With the new AWS security offering, Uptycs extends the concept of SQL-driven analytics that began with the osquery agent deployed for hosts and containers. Now data from your AWS resources is represented in SQL tables alongside data from hosts and containers, enabling you to derive even greater connected insights. For example, if you see an alert from AWS CloudTrail data, you can tie that back to activity on an individual host and vice versa.
Kevin Paige, CISO for the freight logistics platform Flexport, says: “As a cloud-based company running on AWS, finding a platform to solve all of our security needs across all of our accounts and services was a top priority. But finding a single solution that could solve for audit and inventory of our cloud assets, as well as endpoint detection and response, was a challenge—until we found Uptycs. Now we’re able to do more with less, and save time, while maintaining a strong cloud security posture.”
In 2021 and beyond, you can look forward to Uptycs adding more structured data sources, making SQL-powered analytics the essential foundation for end-to-end security observability.
Schedule a demo to see Uptycs’ new AWS security offering in action.