As enterprises shift their workloads to the cloud, cloud security posture management has become an imperative.
Gartner forecasts that worldwide public cloud spending will increase by 18.4% in 2021 to a total of $304.9 billion. The market research firm predicts that the proportion of IT spending shifting to the cloud will accelerate, with the cloud projected to make up 14.2% of the total global enterprise IT spending market in 2024, up from 9.1% in 2020.
As organizations shift IT spending more to cloud services, they are facing more regulations, a high rate of data loss, and a surge in attacks on their cloud apps.
To confront these challenges, they will need to gain visibility and security for their software-as-a-service (SaaS), platform-as-a-service (PaaS), and infrastructure-as-a-service (IaaS) clouds. There are several tools out there that can help organizations provide security for their cloud environments. Below, we’ll examine at a high-level four options that are growing in adoption.
CASB (Cloud Access Security Broker)
The Cloud Access Security Broker (CASB) is essentially a firewall for cloud services. It provides a security policy enforcement gateway to ensure that users’ actions are authorized and compliant with company security policies.
A CASB can identify all the cloud services used by an organization, including shadow IT/unapproved or unmanaged SaaS and PaaS products, and raise alerts when necessary. It enables cloud usage tracking, reporting, and logging, assessing the risks posed by shadow IT, and event monitoring.
A CASB has auditing and reporting tools for regulatory compliance, including cloud-stored data. These tools provide user authentication and authorization and policy enforcement, such as moving and encrypting files, changing permissions, and filtering messages.
Threat protection is another area where a CASB can help an organization. A CASB protects cloud services for authorized users and applications and provides anti-phishing, account takeover, URL filtering, malware detection, and sandbox protections.
In terms of data security, Cloud Access Security Broker solutions can monitor access to data and enforce data-centric security policies by providing granular access controls, such as access to cloud services only through designated devices or platforms. It also offers policy-based encryption.
What Does a CASB Do?
Acting as a gatekeeper, a CASB allows organizations to extend the reach of their security policies beyond their own infrastructure.
What Are the 4 Pillars of CASB?
The 4 pillars of CASB as categorized by leading analyst firm Gartner by various functionalities are as follows: Visibility, Compliance, Data Security, and Threat Protection.
What Is a CASB Example?
Solutions Consolidating multiple types of security policy enforcement, examples of CASB policies include authentication, single sign-on, authorization, credential mapping, device profiling, encryption, tokenization, logging, alerting, malware detection/prevention among others.
CWPP (Cloud Workload Protection Platform)
A Cloud Workload Protection Platform (CWPP) provides a workload-centric security protection solution for all types of workloads, including physical servers, virtual machines (VMs), containers, and serverless workloads. CWPP furnishes a single pane of glass for visibility and protection across on-premises and cloud environments.
What Does a CWPP Do?
Designed to provide comprehensive and targeted protection for workloads on-prem or in the cloud, CWPP scans cloud environments for improperly configured security settings or ones that violate corporate security policies or regulatory compliance requirements.
Gartner Peer Insights™ defines CWPPs as workload-centric security products designed to protect server workloads across hybrid, multicloud data center environments. These platforms ensure consistent visibility and control over physical machines, virtual machines (VMs), containers, and serverless workloads, irrespective of their location. CWPPs achieve this protection through a combination of system integrity protection, application control, behavioral monitoring, intrusion prevention, and optional runtime anti-malware protection.
According to Gartner, CWPP encompasses eight layers of control. In order of importance, these capabilities include:
- Hardening, configuration, and vulnerability management, including scanning for vulnerabilities before software is pushed to production
- Network firewalling, visibility, and microsegmentation
- System integrity assurance
- Application control and allowlisting
- Exploit prevention and memory protection
- Server workload EDR, behavioral monitoring, and threat detection and response
- Host-based IPS with vulnerability shielding
- Anti-malware scanning
What are the Benefits of Cloud Workload Protection?
As one of the biggest advantages of the cloud is the ability to scale resources up and down on demand, CWPPs are cloud-based, enabling organizations to achieve the same level of flexibility with regard to application and workload security.
A CWPP provides a number of benefits, including the ability to identify vulnerabilities earlier in the CI/CD process, faster detection of exploits and active threats, and greater context and investigative capabilities when responding to an incident. CWPP solutions that map observed activity to the MITRE ATT&CK enterprise matrix provide analysts and investigators with greater context and help them understand the severity of an incident.
What Is a Workload in Computing?
Also referring to the amount of work (or load) that software imposes on the underlying computing resources, an application’s workload is related to the amount of time and computing resources required to perform a specific task or produce an output from inputs provided.
CSPM (Cloud Security Posture Management)
While CWPP protects workloads from the inside, cloud security solutions like Posture Management protects workloads from the outside by assessing secure and compliant configurations of the cloud platform’s control plane.
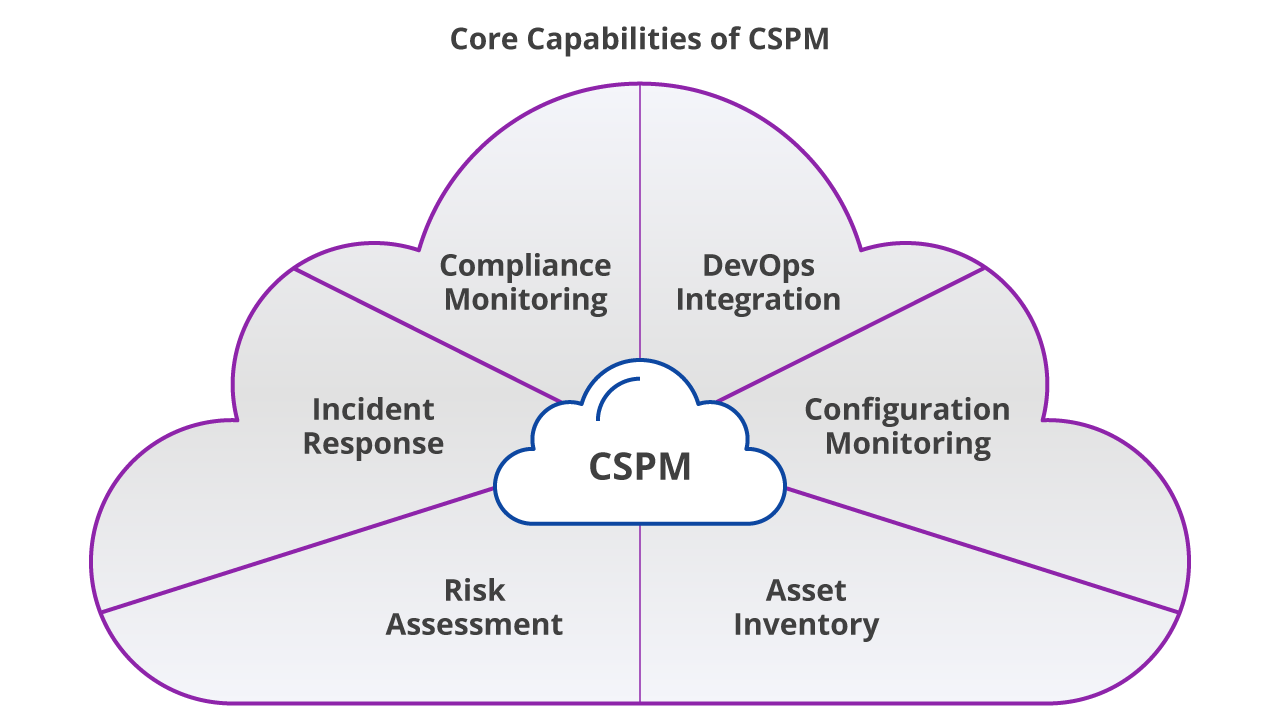
To accomplish this, CSPM provides a set of tools that support compliance monitoring, integration with DevOps processes, incident response, risk assessment, and risk visualization.
A CSPM solution identifies unknown or excessive risk across an organization’s entire cloud estate, including cloud services for compute, storage, identity and access, and more. It offers continuous compliance monitoring, configuration drift prevention, and security operations center investigations.
What Is a CSPM?
Important for its purpose of programming to continuously monitor cloud infrastructure for security gaps in security policy enforcement, Cloud Security Posture Management (CSPM) is a market segment for IT security tools that are designed to identify misconfiguration issues and compliance risks in the cloud.
CWPP vs CSPM: What’s the Difference?
Cloud Workload Protection Platforms (CWPP) and Cloud Security Posture Management (CSPM) both play essential roles in cloud security but focus on different aspects of the cloud environment.
CWPP primarily focuses on securing workloads within the cloud, such as virtual machines, containers, and serverless functions. It offers protection through system integrity monitoring, application control, threat detection, and behavioral analysis. CWPP provides comprehensive workload-centric protection across multiple environments, both on-premises and in the cloud, ensuring visibility, control, and security regardless of workload type or location.
In contrast, CSPM is concerned with securing the cloud infrastructure itself. CSPM tools continuously monitor the cloud environment for misconfigurations, compliance violations, and other security issues. They automate the detection and remediation of these issues, ensuring that the cloud infrastructure aligns with best practices and regulatory standards such as the Center for Internet Security (CIS) benchmarks for cloud providers and the MITRE ATT&CK cloud matrix. CSPM is essential for identifying potential risks and gaps in security policies, helping organizations avoid breaches and maintain a consistent security posture.
The tl;dir? While CWPP protects the workloads, CSPM ensures that the infrastructure surrounding those workloads is secure, offering a holistic approach to cloud security when used together.
CSPM vs DSPM
Once again, CSPM (Cloud Security Posture Management) and DSPM (Data Security Posture Management) are both essential tools for securing cloud environments – but they focus on different aspects of security.
CSPM primarily addresses the security and compliance of the cloud infrastructure itself, ensuring that the configuration of cloud resources is correct and compliant with industry standards. It automates the detection and remediation of misconfigurations that could lead to security vulnerabilities, helping to avoid breaches and ensuring cloud environments are secure.
On the other hand, DSPM focuses on protecting the sensitive data stored within the cloud. It helps organizations locate, classify, and secure sensitive information such as personally identifiable information (PII) or intellectual property, ensuring that data is only accessible by authorized users and complies with data privacy regulations like GDPR or HIPAA. DSPM is especially valuable in protecting data within SaaS applications and detecting any risks associated with it.
While both solutions are valuable on their own, using them together provides comprehensive security. CSPM secures the infrastructure, while DSPM safeguards the data within it, providing end-to-end protection across cloud environments.
CNAPP (Cloud-Native Application Protection Platform)
A cloud-native security model that encompasses cloud security platforms such Cloud Security Posture Management (CSPM), Cloud Service Network Security (CSNS), and Cloud Workload Protection Platform (CWPP), Cloud Native Application Protection Platform (CNAPP) is the single holistic platform overarching each aforementioned solution. 40% of companies reported using a CNAPP, and an additional 45% plan to implement one by the end of 2024.
Securing cloud-native applications involves a continuous set of processes focusing on identifying, assessing, prioritizing, and adapting to risk in cloud-native applications, infrastructure, and configuration.
Cloud-native applications require a systematic approach to identity and entity management and embrace a least privileged, or zero trust cloud security posture. Robust cyber hygiene around user identity management for developers and users must be a part of the strategy.
CNAPP vs CSPM: What’s the Difference?
While both CNAPP (Cloud-Native Application Protection Platform) and CSPM (Cloud Security Posture Management) are integral to securing cloud environments, they serve distinct purposes.
The short version is: CSPM focuses on cloud infrastructure security and configuration, while CNAPP offers a broader, unified solution that includes workload protection, threat detection, and application security, giving teams an end-to-end view of risks across both cloud infrastructure and cloud-native applications. Here’s a bit more detail:
CSPM focuses on ensuring that the cloud infrastructure is configured correctly. Its primary function is to continuously monitor the cloud environment for misconfigurations, compliance violations, and other security risks. CSPM tools automatically detect and remediate these issues to maintain a secure and compliant infrastructure. It ensures that the cloud platform's control plane—such as network configurations, identity access management (IAM), and storage—is secure and aligned with industry benchmarks like CIS or the MITRE ATT&CK cloud matrix.
On the other hand, CNAPP tools go beyond just securing the infrastructure. They provide comprehensive protection across workloads, data, and cloud-native applications, offering visibility and unified security measures across both development (DevOps) and security operations (SecOps) teams. A CNAPP consolidates the capabilities of CWPP (Cloud Workload Protection Platform) and CSPM into a single solution, giving security teams a unified view of risks across the entire cloud environment—covering workloads, configurations, and data.
Which Is Your Best Option?
Which tools an organization selects depends on its priorities. If its primary concern is to control enterprise cloud usage, then CASB is probably the best option.
If the organization’s priority is to protect its workloads on the cloud and reinforce application security, CWPP is likely the better choice. The organization should evaluate if its current workload security solution can cope with the cloud services it uses now. For example, if it is using containers, its workload security product should be able to inspect the containers for security risks.
If the company’s most pressing need is to comply with cloud configuration best practices, then CSPM is most likely the best solution. CSPM tools use the cloud provider’s application programming interfaces to automate security benchmarks and audit checks that enable you to avoid having a leaky S3 bucket with customer data exposed to the internet, for example.
In choosing the right platform, an organization should clearly define its cloud security needs and communicate with stakeholders and business executives about those needs.









