In 2023, the cybersecurity landscape was characterized by an escalation of sophisticated cyber threats and continued exploitation of critical vulnerabilities. From the alarming exploitation of the Apache ActiveMQ vulnerability to the persistent menace of advanced malware on major operating systems, the year was marked by persistent and evolving challenges in cyber defense.
The Uptycs Threat Research Team catalogs and analyzes these threats every quarter. Here’s a look at the major trends our research uncovered during 2023 and an analysis of what they may portend for the year ahead.
The rising tide of sophisticated malware
Windows platforms grappled with the prevalence of Amadey, AgentTesla, and RedLine malware. Amadey, a multifaceted botnet malware, emerged as a significant threat, functioning as an infostealer and a loader for malicious payloads. AgentTesla evolved into a sophisticated tool for initial access and exfiltration of sensitive data, while RedLine Stealer proved its potency as a data collection tool.
The year's malware landscape showcased the need for more robust defense mechanisms against such versatile cyber threats.
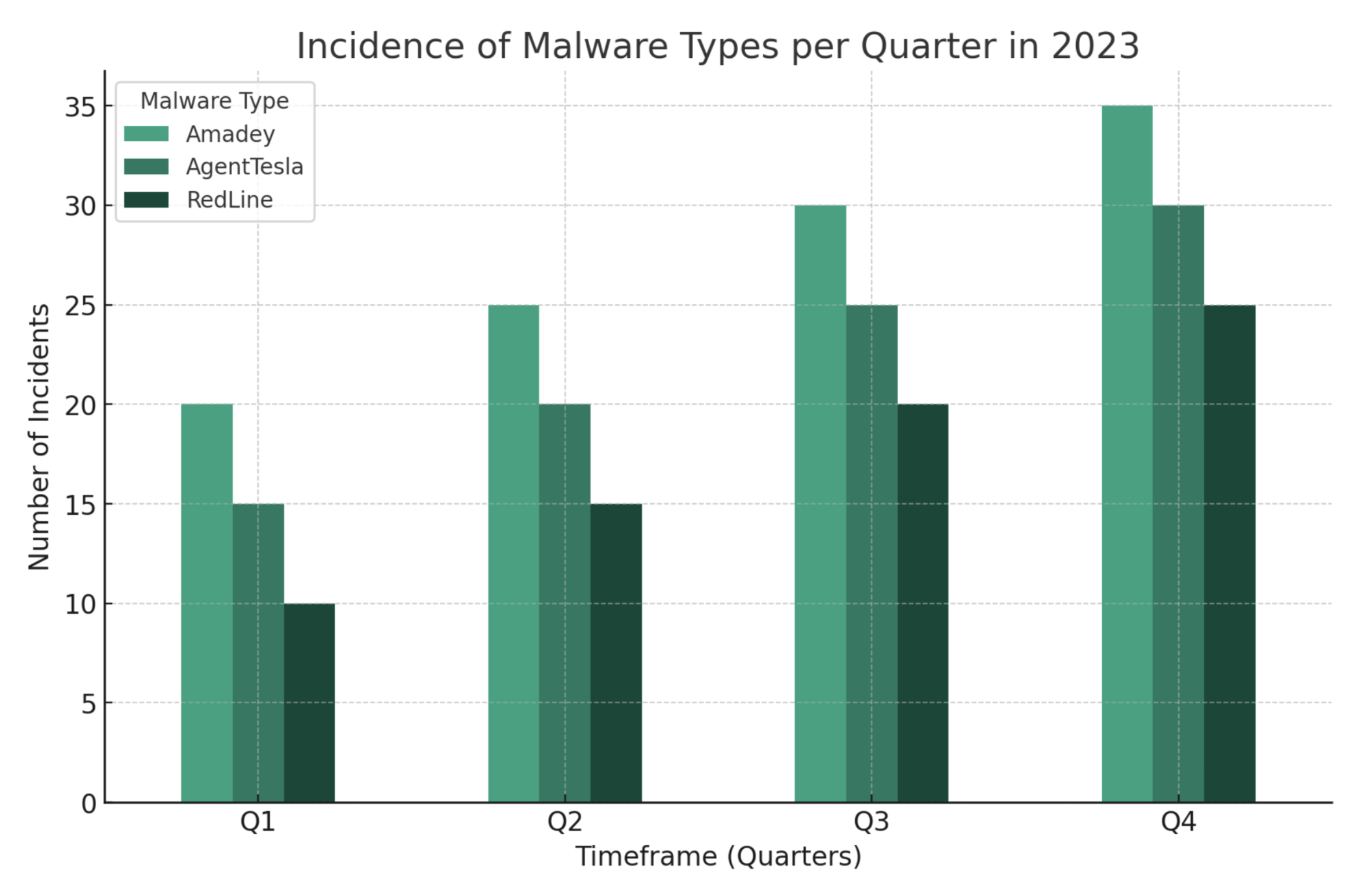 The bar chart depicts the incidence of three malware types (Amadey, AgentTesla, and RedLine) across different quarters in 2023
The bar chart depicts the incidence of three malware types (Amadey, AgentTesla, and RedLine) across different quarters in 2023
Vulnerabilities: The Achilles heel of cybersecurity
The CVE-2023-46604 vulnerability in Apache ActiveMQ put the cybersecurity community on high alert. This critical vulnerability and rampant exploitation of other software vulnerabilities across Windows, Linux, and macOS underscored a persistent challenge in cybersecurity– managing software vulnerabilities. The range of affected software was a stark reminder of the ubiquitous nature of cybersecurity risks.
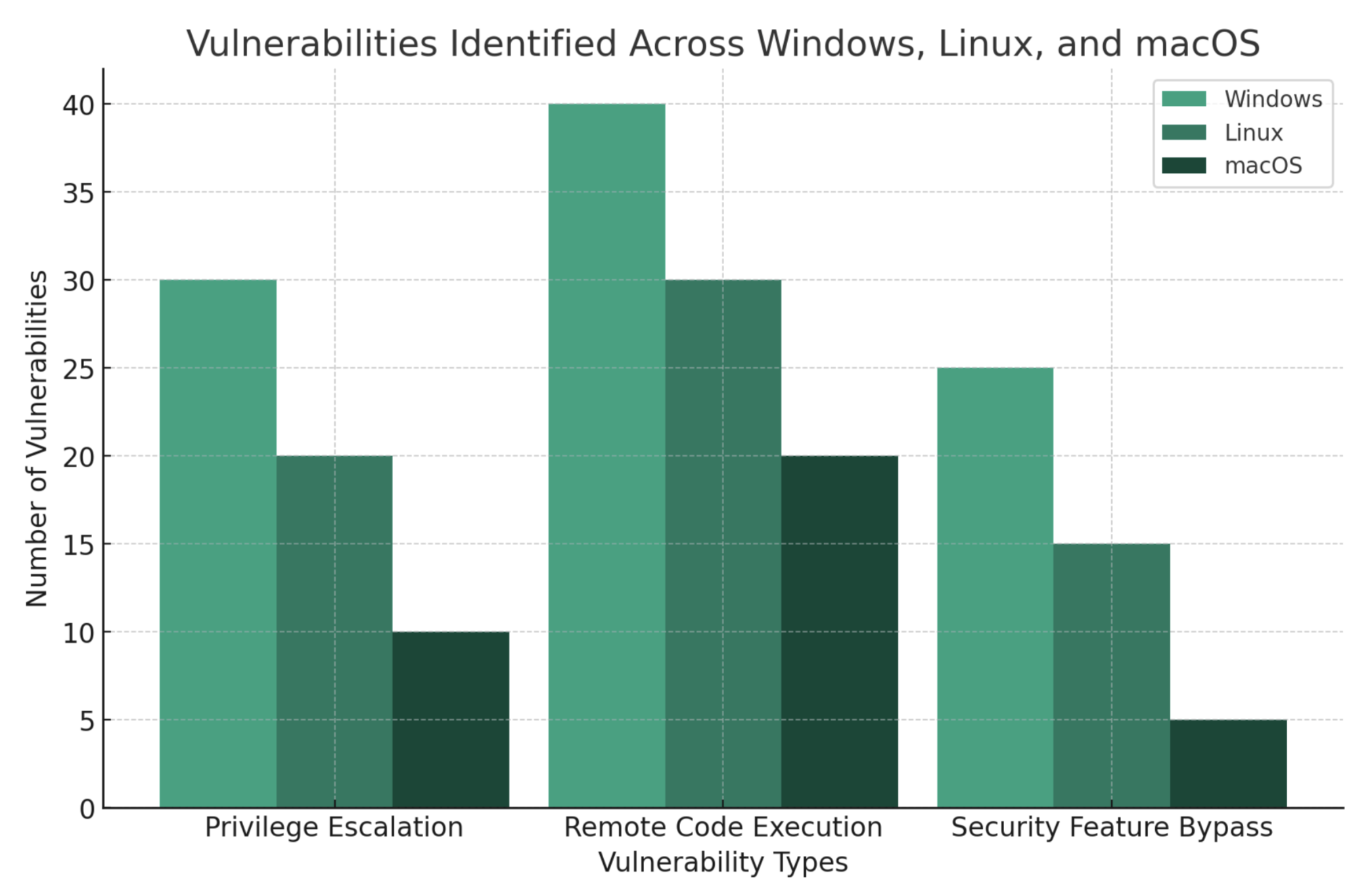 The chart illustrates the distribution of different types of vulnerabilities (Privilege Escalation, Remote Code Execution, and Security Feature Bypass) across Windows, Linux, and macOS platforms
The chart illustrates the distribution of different types of vulnerabilities (Privilege Escalation, Remote Code Execution, and Security Feature Bypass) across Windows, Linux, and macOS platforms
The menace of advanced persistent threat (APT) actors
Sophisticated threat actors such as the Lazarus Group, SideWinder, Kimsuky, AridViper, and APT29 were notable in 2023. These groups, linked to state-sponsored initiatives, demonstrated advanced capabilities in exploiting vulnerabilities and conducting targeted cyber espionage. The Lazarus Group's exploitation of Log4j vulnerabilities and APT29's use of HTML smuggling techniques exemplified these actors' strategic and technical sophistication.
Evolving landscape of threat techniques
Cybercriminals increasingly adopted more elusive techniques. The concept of "living off the land," where attackers use built-in operating system utilities to evade detection, gained traction. Utilities such as rundll32.exe on Windows and crontab on Linux were frequently abused, demonstrating a shift in attack methodologies.
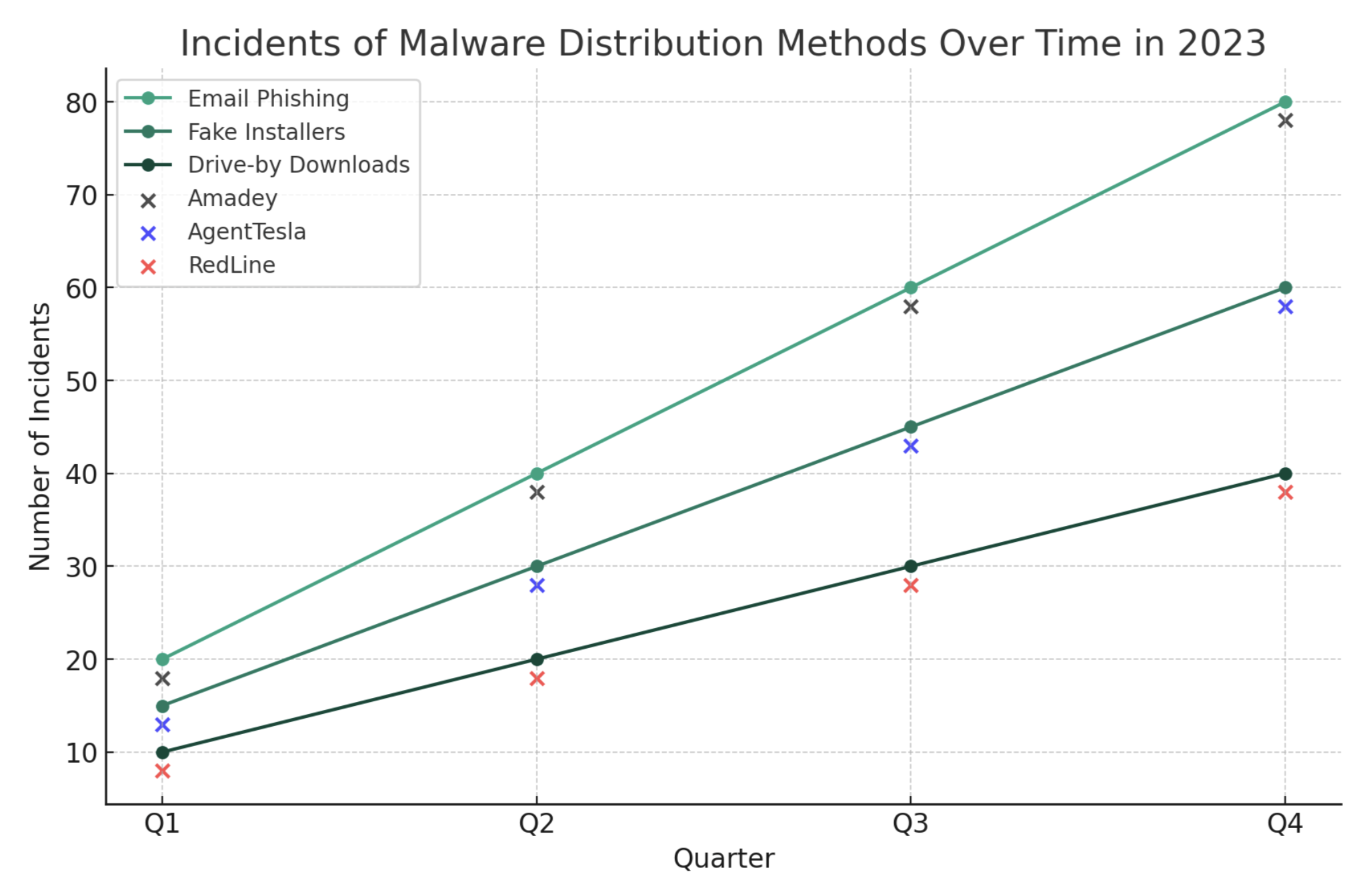
Based on the analysis of the malware distribution methods for 2023, several key characteristics and trends can be identified:
- Diversification of techniques: There was a noticeable diversification in the distribution methods used by cyber attackers. Traditional methods like email phishing remained prevalent, but more sophisticated techniques like fake installers and drive-by downloads were also significantly used. This diversification suggests that attackers constantly innovate and adapt their strategies to circumvent security measures and exploit user vulnerabilities.
- Email phishing as a dominant method: Email phishing continued to be a dominant method for malware distribution throughout the year. This enduring popularity of phishing can be attributed to its effectiveness in exploiting human errors and the ease with which it can be scaled and targeted.
- Rise in more sophisticated methods: Methods such as fake installers and drive-by downloads indicated a shift towards more sophisticated and nuanced attack vectors. These methods often require a deeper understanding of user behavior and typically exploit vulnerabilities in software or user negligence, making them harder to detect and prevent.
- Quarterly increase in incidents: There was a clear upward trend in incidents for all distribution methods over the quarters. This increase suggests that malware threats are becoming more frequent and that attackers are constantly refining their methods and finding new ways to distribute malware.
- Overlay of specific malware types: The overlay of specific malware types on the distribution methods chart below provided insights into how different malware favor certain distribution techniques. For example, malware like RedLine may have preferred a method like drive-by downloads, indicating a strategic choice based on the malware's design and intended targets.
- Adaptation and evolution: The evolution of distribution methods throughout the year reflects the adaptability and evolution of cyber attackers in response to changing cybersecurity defenses and user awareness. It underscores the need for continuous adaptation in cybersecurity strategies.
Preparing for 2024 with Uptycs
As we look toward 2024, the lessons of 2023 emphasize the need for a multi-faceted approach to cybersecurity, combining robust technological defenses, proactive threat intelligence, and a comprehensive understanding of the evolving cyber threat landscape.
Here, the Uptycs platform can play a significant role. It offers unified visibility, risk-based prioritization, and rapid threat detection, investigation, and remediation across hybrid multi-cloud environments. Uptycs' real-time visibility addresses cloud blind spots and disjointed workflows, enabling SecOps teams to track changes in security posture and manage cloud operating expenditures efficiently.
Uptycs' advanced analytics and threat-hunting capabilities empower teams to proactively investigate threats across hybrid multi-cloud environments, ensuring that security visibility, compliance controls, and threat prevention are consistent across complex multi-cloud environments. The platform's ability to automatically prioritize risks based on threats, anomalies, vulnerabilities, and potential business impact enables organizations to focus on the most urgent issues first, streamlining the process of securing intricate multi-cloud environments.
As we navigate the challenges of 2024, Uptycs stands as a pivotal ally in cybersecurity, helping teams protect private and public cloud assets, ensuring rapid response to incidents, and instilling confidence that their cloud environment is protected. The trends from 2023 serve as a roadmap for enhancing cybersecurity measures, and with Uptycs' platform, organizations are well-equipped to navigate the evolving digital landscape with resilience and preparedness.
More insights from the frontline
Want to know what trends seasoned cyber professionals are predicting for 2024? For better or for worse, 2024 rings in with uncertainty, fear, and hope aplenty. Check out From the Experts: Cybersecurity Hopes, Fears, and Best Advice for 2024. Discover their insights, join the discussion on LinkedIn, and shape your strategies for the year ahead.







