Orchestration engines such as Palo Alto Networks Cortex XSOAR give security professionals the freedom to integrate multiple services into coordinated, automated workflows. Simple REST APIs allow the transfer of data from one application or service to another in a reliable, straight-forward manner. With the appropriate data sources, users are enabled to create workflows and reports for incident investigation and response. In removing the human element, orchestration engines can improve the overall efficiency and consistency of incident response, while freeing up time for other tasks.
Uptycs leverages the open-source osquery agent in order to acquire real-time data about nearly any facet of your infrastructure (more about osquery here). This data is streamed, aggregated, and stored in the Uptycs backend and then made accessible via our API, allowing the integration of Uptycs data with other services.
Cortex XSOAR Integration
The Uptycs-Cortex XSOAR integration (available here in the Cortex XSOAR Integration catalog) allows customers of both solutions the use of Uptycs data within their Cortex XSOAR instance. The data is presented in a standardized JSON format such that it plays nice with other integrations and grants the user the freedom to create uniquely specialized automated workflows. There are various commands built into the integration allowing the user access to this data. A “run query” command exists as a failsafe, allowing the user to run any query against the Uptycs backend for cases in which a particular out of the box command does not exist. The result is a robust framework for developing automated response playbooks based on Uptycs, or other third-party alerts.
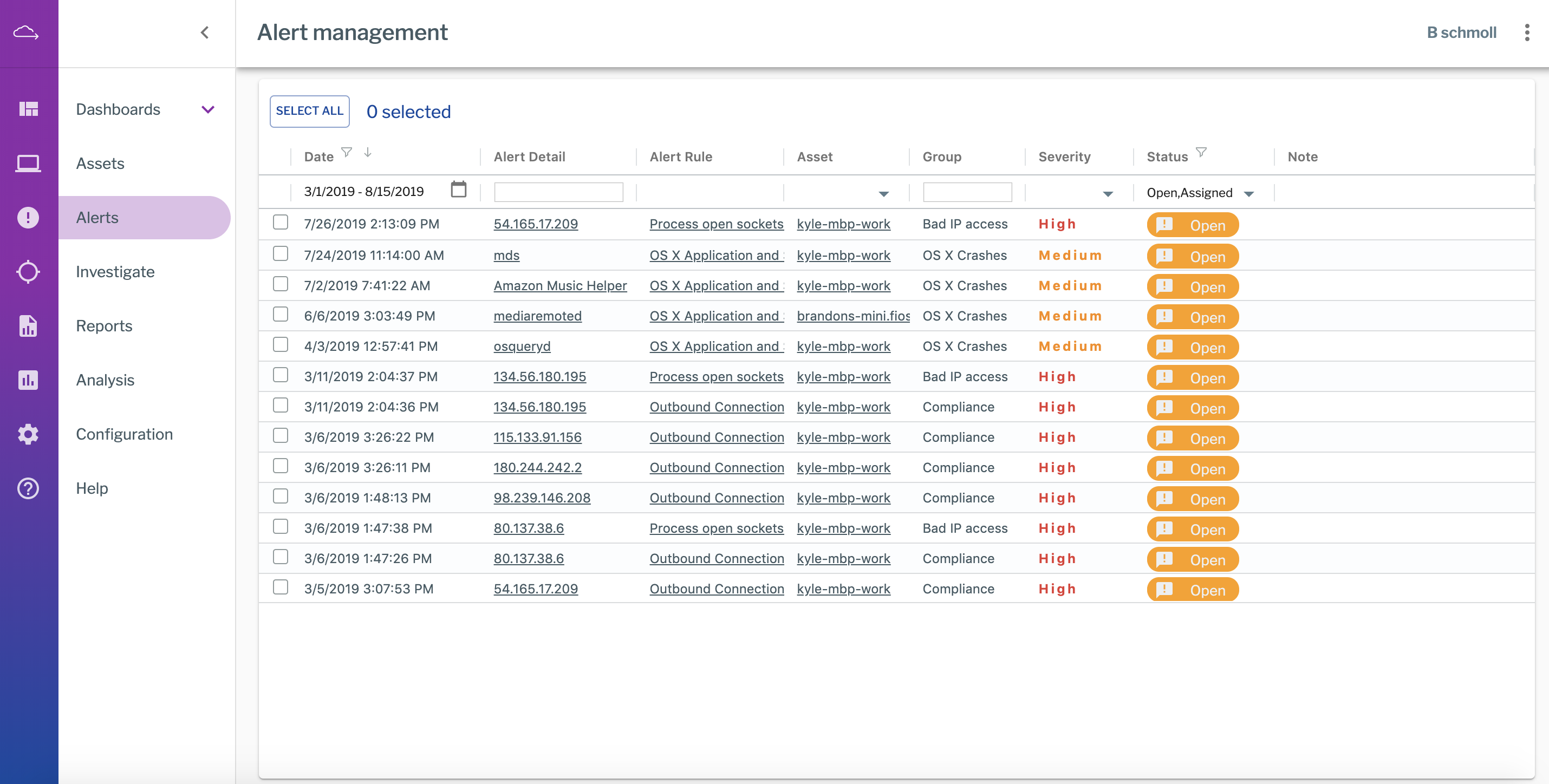
Alert Management View in Uptycs
Cortex XSOAR Incident Overview Dashboard with Uptycs Alerts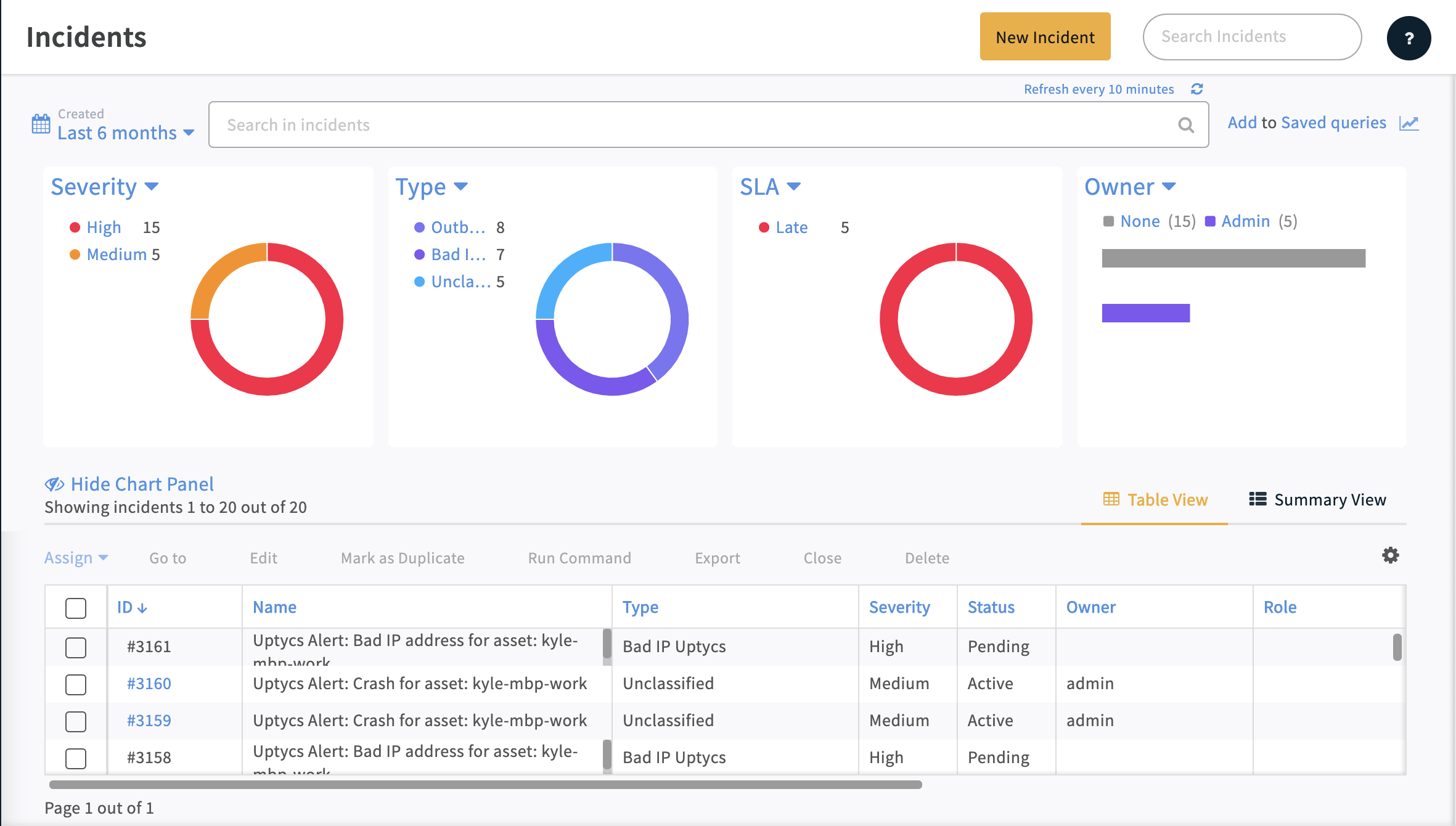
Example Incident Investigation Use Cases
Bad IP Enrichment
Public databases contain lists of many, many known threat sources. When connections to a known Bad IP address pop up, Uptycs fires an alert notifying the user of the event. With Cortex XSOAR, a Bad IP Enrichment playbook exists which will make the appropriate API requests to return information on the connection that was opened, the process which opened the connection, the parent process of the process which opened the connection, and the child processes of said parent process all in an organized and easy to navigate format. The user is then able to investigate the incident quickly and with confidence.
Example: Cortex XSOAR Bad IP Playbook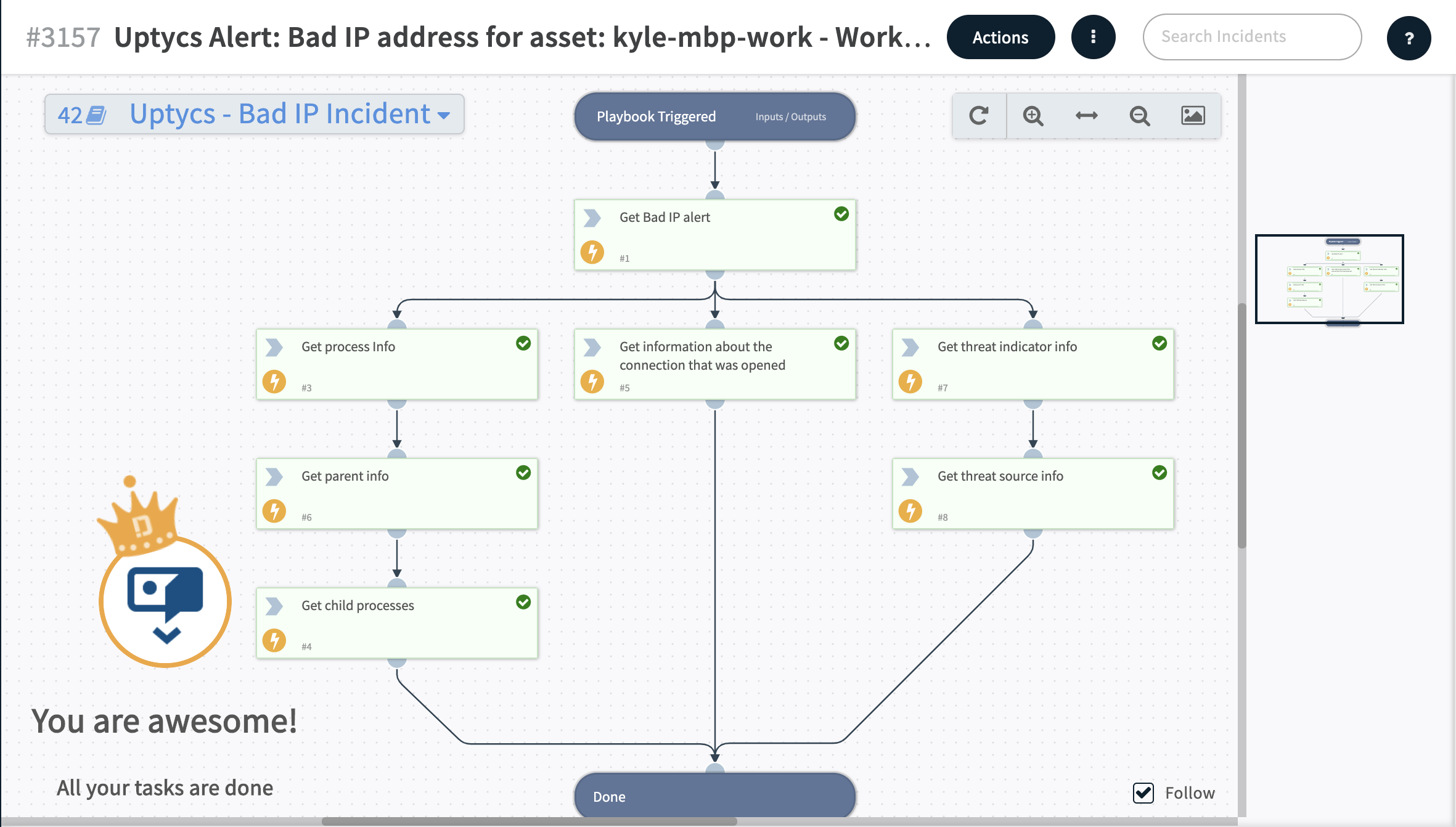
Real-Time Global Investigation in Uptycs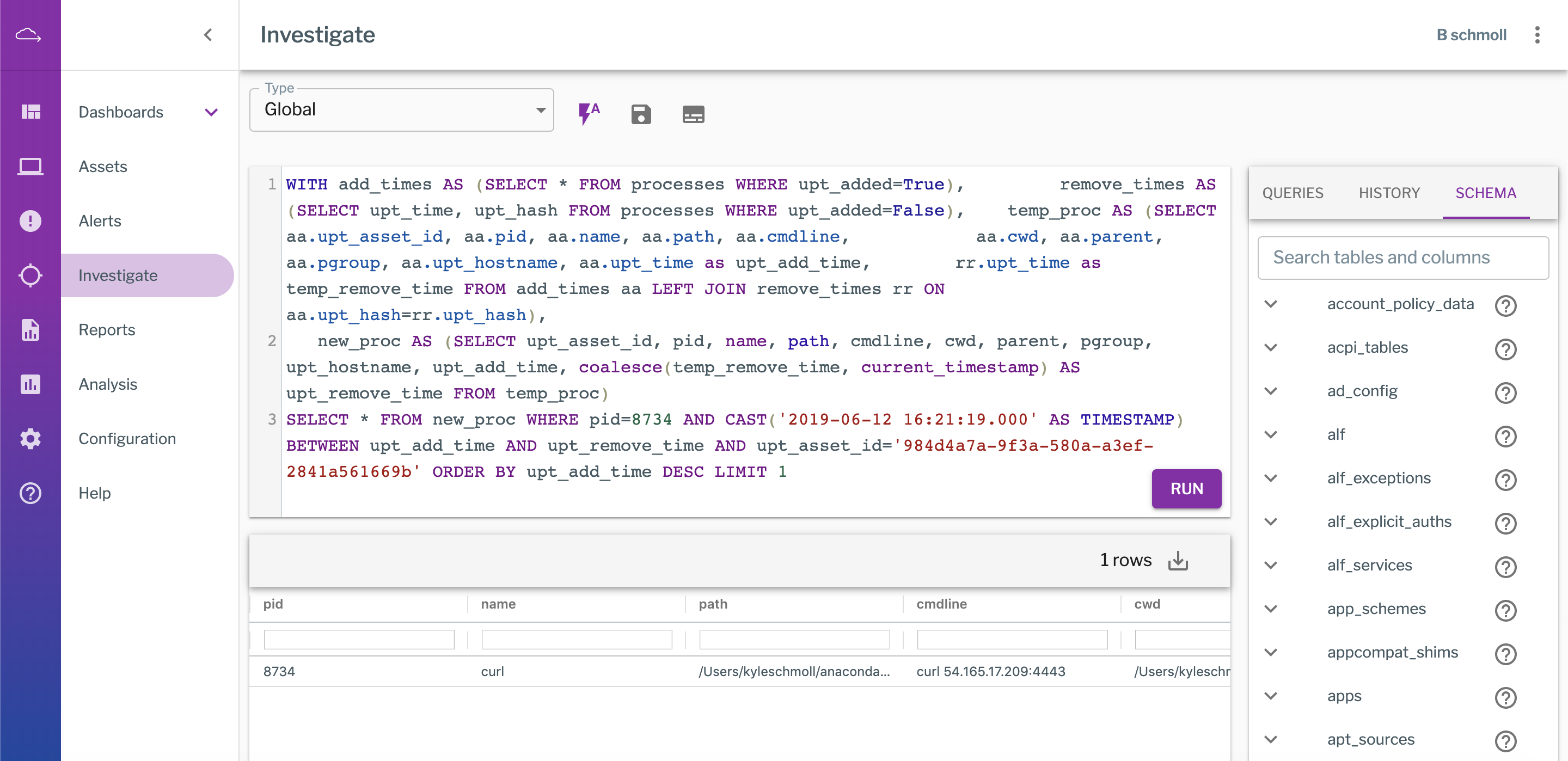
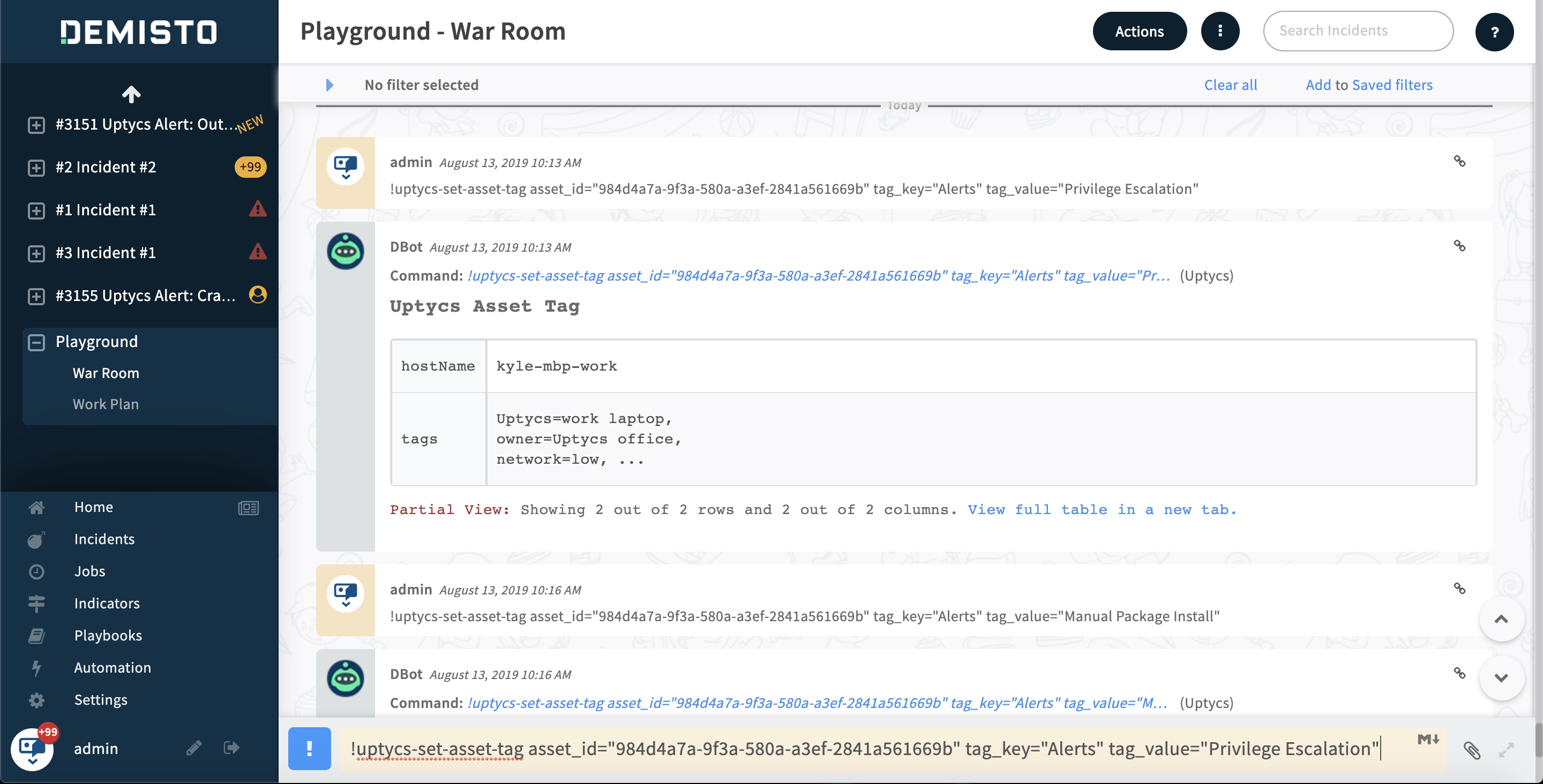
Asset Tagging
With the asset tagging command in the Cortex XSOAR UI, users can tag assets enrolled with Uptycs in order to run specific query packs for different asset tags. Running targeted query packs this way can be more efficient in terms of performance and data storage. A related step that could be added to Cortex XSOAR playbooks is to automate the process of tagging an asset in Uptycs when an alert is generated. This would allow for subsequent execution of one or more query packs against that tag for additional data collection.
Remote Process Termination
Using the Uptycs integration the details of a process associated with an alert, including the PID, can be used as part of a workflow. Cortex XSOAR's D2 agent allows for remote execution of commands on an endpoint from the Cortex XSOAR UI. This functionality allows for the immediate remediation of threats which are detected on remote endpoints. Automate the process using a playbook, so that an alert immediately causes the process which generated the alert to be terminated.
Endless Possibilities
The breadth of endpoint telemetry Uptycs makes available combined with the ability to write custom alert rules creates an enormous potential to respond to unique situations which vary from environment to environment. We’re excited about the integration with Cortex XSOAR and the flexibility it provides our shared customers.







