There's a big disconnect between best practice frameworks and the real-life nitty gritty. Many of these frameworks broadly approach the overarching principles that a robust security program should encompass and why these principles are important; however, they don't usually say specifically what kind of attacker behavior a defender should anticipate when building their security programs, nor do they detail how an attacker would work to thwart those vaulted best practices. Often, that's left up to the security practitioner to suss out themselves in their copious spare time.
Bridging the gap between theory and practice can be challenging even for the most seasoned security veterans, which is why we recommend enterprises take a serious look at the MITRE ATT&CK framework for guidance.
What's MITRE ATT&CK & Why Is It a Useful Framework?
MITRE, being well-known in security circles for their vulnerability identification and threat research, created the ATT&CK framework based on all the real-world threat detail they encounter and study, which are all threats that enterprises frequently face.
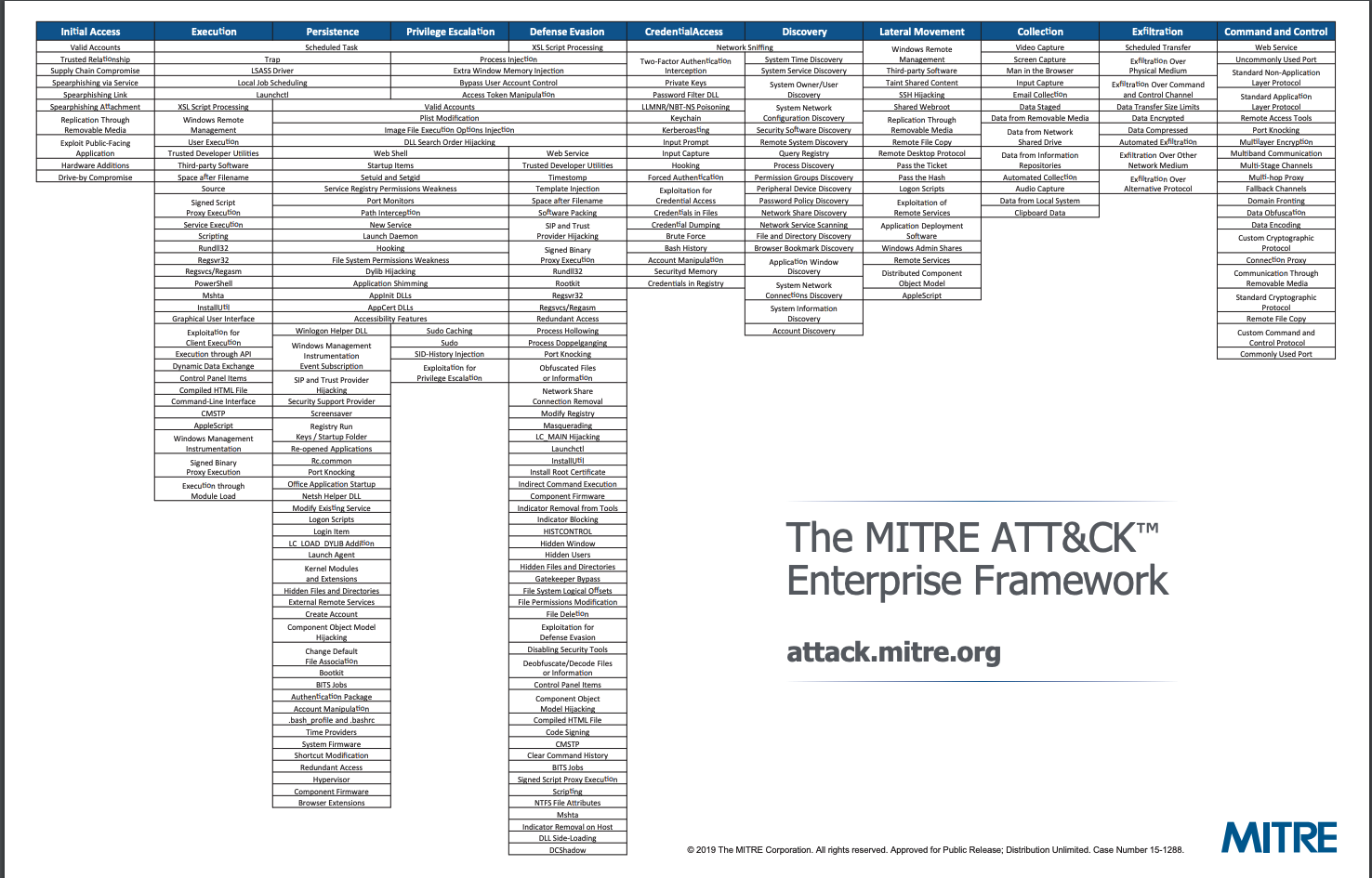
As such, their ATT&CK framework is grounded in practical, actionable advice and gives specific recommendations for mitigation and remediation tactics. It spans operating systems and device types, with 12 columns naming specific attack tactics frequently used against enterprises. Each of those columns then contains numerous techniques that attackers often use to carry out their tactic, and exactly how the attacker would carry out that technique.
For example, under the Privilege Escalation column, ATT&CK lists 28 possible techniques an attacker may try, such as bypassing user access control (UAC). ATT&CK then details exactly how bypassing UAC tends to occur, what operating systems tend to be vulnerable — in this case, Windows — and what tools are frequently deployed by attackers to escalate privileges. The framework then details mitigation recommendations, from making policy-level changes to monitoring specific registry keys that attackers tend to modify.
While many other security frameworks are quite high-level and strategic, and in some cases proprietary, MITRE ATT&CK merges well the tactical and practical to help organizations build a robust roadmap to better organizational security. It's also completely free to use.
Why osquery is a great fit for the ATT&CK framework
Osquery is an open-source, cross-platform tool that allows you to query and monitor your endpoints as if they were a relational database. It's fast, flexible, and highly extensible, allowing you to glean a wealth of information from endpoints in comparison to older monitoring tools with slower agents. The comprehensive real-time results that osquery generates make it a natural fit in a defender's arsenal, enabling easy continuous monitoring of the endpoints on the network for events, what the endpoints are connected to, what processes they are (or aren't) running — just to name a few. Since osquery essentially turns your endpoint operating systems into a fast virtual database, the logs that osquery generate also slot well into your existing security ecosystem for analysis and action.
To demonstrate how organizations can leverage osquery's powerful monitoring capabilities and pair it with the MITRE ATT&CK framework's recommendations, it’s helpful to use a real-world example: The 2018 Singapore Health breach. In this incident, nearly 1.5 million patients had their personal health information (PHI) stolen. Singapore Health’s breach is a learning opportunity for security professionals thanks to its comprehensive post-breach report, which painstakingly outlines the specific attack vectors used and the multiple failure points that lead to the breach.
Let’s take a look at one example point in the Singapore Health breach, and how an organization using osquery within the ATT&CK framework might prevent similar missteps.
Examples from the Singapore Health breach: What happens after initial infiltration
While there's some disagreement about how it got there in the first place, the Singapore Health breach investigators determined that attackers first got a foothold in the network by placing malware on at least one workstation, and the malware in question seemed to exploit a vulnerability in Microsoft Outlook. Once exploited, the attacker was able to download a payload onto the infected machine, which included malicious PowerShell scripts masquerading as innocuous .jpg files.
From there, the attacker gained a foothold on the compromised machine, from which they were able to download additional payloads and quietly lurk until they were able to move laterally to another machine and eventually infiltrate servers containing PHI nearly half a year later. Being able to stop that initial foothold via malicious PowerShell scripts could have seriously disrupted, if not stopped, this attack.
- ATT&CK framework mapping: PowerShell (T1086) is one of the many specific techniques outlined in ATT&CK's Execution tactic.
- How osquery could be used here: Osquery can be set up to detect and flag obvious malicious Powershell events on monitored endpoints, but it can also look at the overall number of lines, or total size, of PowerShell scripts running on endpoints in the first place. Malicious payloads are often larger than the typical PowerShell script, and often contain encoded shellcode. By detecting large scripts and investigating their content, we can detect potential attempts to run malicious codes. So if normally innocuous PowerShell scripts are pretty concise, and suddenly they become verbose and balloon in line size, even if what they're doing is not obviously malicious to your average anti-virus, it's clear that something is up that's worth flagging. Osquery can keep an eye on the size of PowerShell code it normally sees, and send up a flag if that number starts to suddenly deviate from the norm.
Free Webinar: Get more information on using osquery with MITRE ATT&CK where more robust defensive measures could and should have stopped the attacker's progress. This post is just a taste of what osquery could do, and how it could help organizations harden their defenses and monitor their endpoints in real-time.ak/?utm_source=blog_post&utm_medium=website&utm_campaign=Q1%202021%20MITRE%20ATT%26CK%20Evaluation" rel="noopener" data-mce-disabled-user-modify="true">
Learn more about osquery: