There’s a dangerous myth among some Mac users that, unlike Windows, the platform is impervious to malware. Since nothing is bulletproof, it would be dangerous to assume Mac fleet security, so let’s recognize why Macs have historically been low risk and why that looks to be changing.
Attackers are opportunists - Windows is the largest attack surface
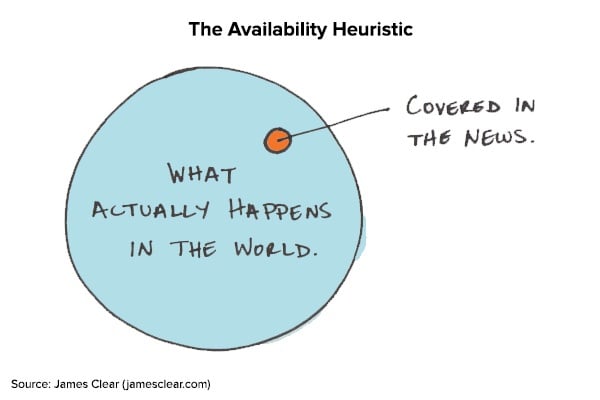
The first information humans trust is personal memory. When trying to determine whether your systems are likely to get compromised by malware, you think of the assets you’ve seen infected before, and then, any major news you’ve read about malware campaigns. This memory shortcut of recalling examples to assess a risk is what behavioral economists call the “availability heuristic”. It often leads people to make inaccurate conclusions about the true likelihood that an event will take place and why the stories haven’t reached them.
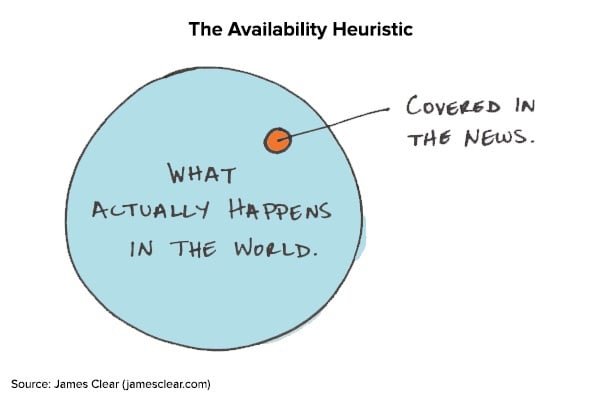
Some IT administrators infer that they don’t need to monitor their Macs because “they are so much more secure than Windows”. The relative rarity of Mac malware, by comparison, doesn’t indicate bulletproof security, but rather a lower assumed rate of success. Since ninety percent of desktop computers sold over the past decade have been Windows, organized criminal groups and opportunistic malware authors have maximized their chances of success by targeting Windows systems the vast majority of the time. That is, until employee demand drove enterprises to start supporting thousands of Macs and a dramatic increase in Mac malware followed.
Many Mac users are high-value targets in the organization
I wouldn’t expect Macs to overtake the Windows majority in my lifetime, but that’s unnecessary if attackers are realizing enough value from the Macs they are able to compromise. Most organizations provision Macs for the people at the core of their business: software engineers, operations professionals, and executives. The impact of ransomware and other compromise becomes more damaging (yet profitable for the criminal) if the assets involved are used to access production environments, source code, and highly confidential information.
Having these high value assets in mind, organized criminal groups have increased the amount of Mac malware they purchase and use. These crimes don’t yield the major windfall of Tony Soprano and crew defrauding a bank with a HUD mortgage scheme, but they are designed to yield a profit at a much lower chance of getting caught.

Attackers are clearly seeing a return because the upward trend has been significant enough to finally start making headlines. These available examples should lead organizations to think through how well they can detect the compromise of one of their corporate Macs.
It’s time to review your Mac monitoring strategy
Macs may be more secure than Windows, but recent malware development has shown that it just doesn’t matter. No system is inherently secure enough to resist all compromise and cybercriminals simply needed to feel like the incentives were there. Your organization is unlikely to revert its policy back to not allowing Macs (nor should they), so the focus needs to shift to how to reach a comforting level of detection for Mac fleet security. Installing osquery on your Macs starts the process of Mac monitoring by getting you access to host-level behavior and configurations. [Read this to learn how easy it is to find malware on macs using osquery]
The next step is to determine how you’ll consume the osquery data for alerting and investigation -- many organizations try a SIEM first, but the context of thousands of each endpoint’s characteristics fail to translate into logs. This is why you need a centralized solution which understands osquery data, stores it historically, and facilitates its analysis.
Antivirus and prayer might have gotten you through supporting the fringe Mac users, but letting a remote Macbook access critical systems warrants some inspection of what’s installed, how it’s configured, and whether there are indicators that it’s been compromised. Just make sure you consider the many systems which are rarely on your physical network. If your business is seeing an increase in remote work, as most are, you need visibility at the endpoint level — logs will never be enough.
Imagine instead of having to piecemeal together the root cause from an incomplete set of events while the Mac is on the corporate network, you can simply look through all system changes on the day in question, regardless of where the Mac was located. This is the vision we had when designing the new Uptycs Mac EDR Dashboard.
If you’re looking to gain visibility into your Macs, let us know. We’d love to show you just how much information Uptycs can provide.