Today, Uptycs is announcing enhanced container and Kubernetes capabilities that make it much simpler to secure containers at scale. These capabilities in Kubernetes security posture management (KSPM), container governance, threat detection, and vulnerability scanning ensure that container-based workloads have the comprehensive security they deserve, without the pain points.
The new Uptycs capabilities promote good security practices that help protect organizations as they adopt Kubernetes technology. According to the Red Hat 2022 State of Kubernetes Security Report, survey respondents cited misconfigurations/exposures as their top concern in container and Kubernetes environments. The new offering from Uptycs is designed to simplify container and Kubernetes security, helping teams to easily highlight the top risks and threats.
Wrangling a Secure Container Fleet
We are still in the early stages of Kubernetes and container adoption, and the problems for securing these new attack surfaces are only growing. With so many objects, images, and configurations to track there has been a notable shift left to become more developer-centric in our approach to good security.
To wrangle their container fleets, Security teams and their DevOps partners need: first, just to get clear visibility into their container assets and Kubernetes control plane and the risk therein; and second, to perform the actual security work of investigating detections, remediating or mitigating CVEs, monitoring compliance with regulatory standards, and enforcing secure policies. To accomplish this, security teams need real-time solutions that provide a unified approach that encompasses everything from the control plane all the way down to individual images.
Orchestrating Container Security with Uptycs
Uptycs has extended the open-source osquery to develop Kubequery, which provides in-depth visibility into the K8s control plane. Access to the control plane through Kubequery means you can monitor 50+ K8s objects for security and compliance purposes. Kubequery analyzes K8s cluster telemetry to provide security observability into the policies behind your container orchestration.
Uptycs supports the Gatekeeper policy controller, enabling SecOps teams to set and enforce policies during the admission of new Kubernetes resources. When security policies are updated, Uptycs will audit K8s resources and then alert your team accordingly.
The new K8s control plane telemetry added to the Uptycs platform also enables broader threat detection coverage. Uptycs provides powerful customizability when it comes to runtime security and compliance alerting, and offers 100+ out-of-the-box rules for detecting runtime threats specific to containers and K8s systems.
Uptycs supports fully-managed Kubernetes environments (AWS EKS, Azure AKS, Google GKE) and self-managed ones, including VMware Tanzu and Google Anthos. For containers, Uptycs supports multiple container runtimes (Docker, containerd, CRI-O).
Uptycs Container and Kubernetes Features
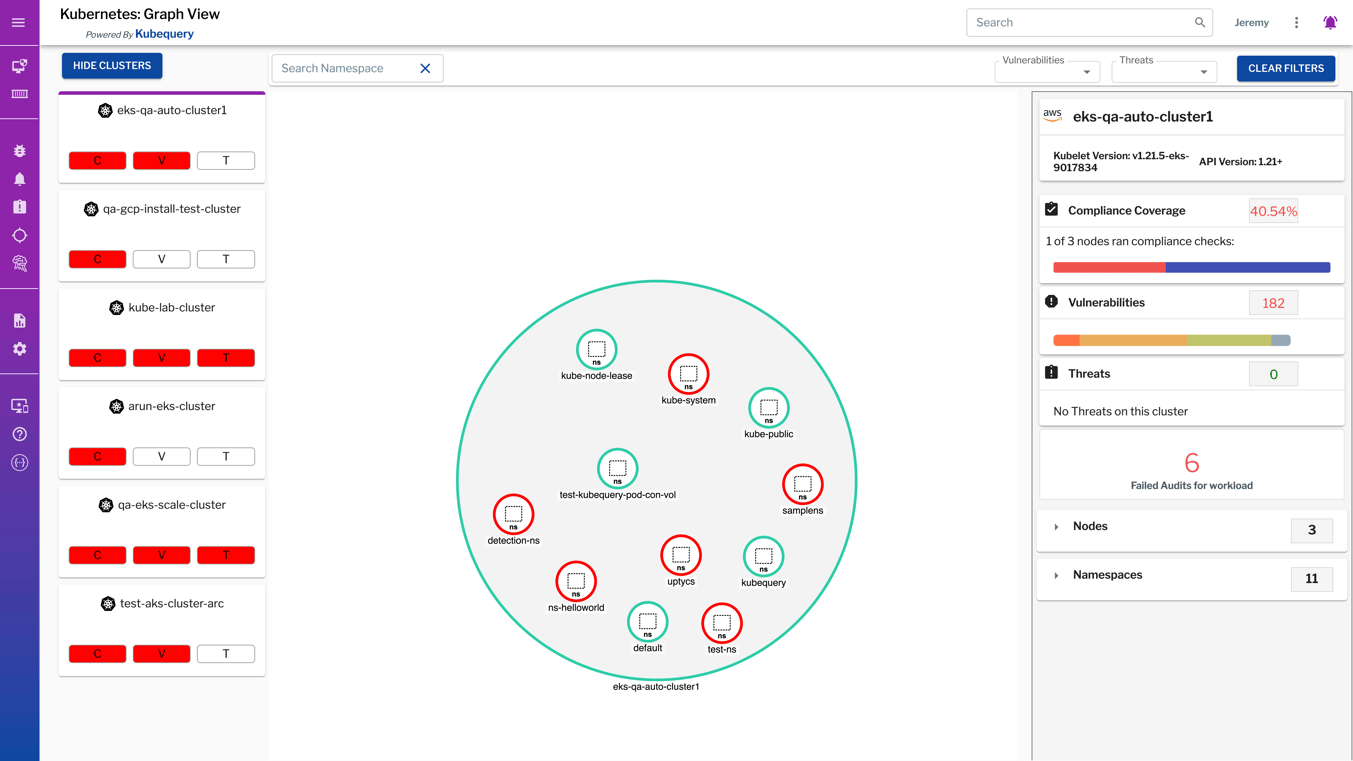
Inventory K8s Resources and Map Relationships
Easily see all your K8s clusters across on-premises and cloud environments; visually map relationships between clusters, nodes, and pods; filter and search for vulnerabilities and threats by namespace; and drill down into vulnerability, compliance, and threats for each cluster and node.
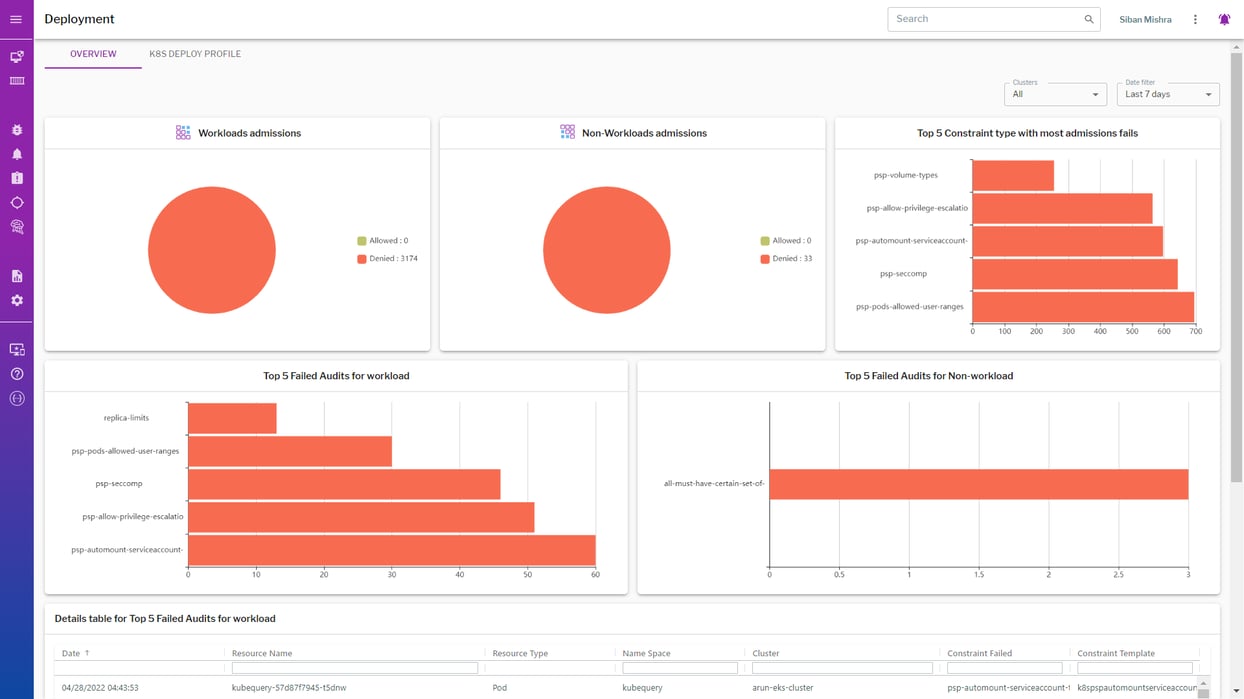
Audit and Enforce Policies
Gain observability for the Kubernetes control plane and perform proactive image assurance to ensure secure image configurations, validate existing K8s resources against continuously evolving OPA constraints, and enforce policies (through the Gatekeeper policy controller) during admission of K8s resources and audit of the K8s resources using the most recent security policies.
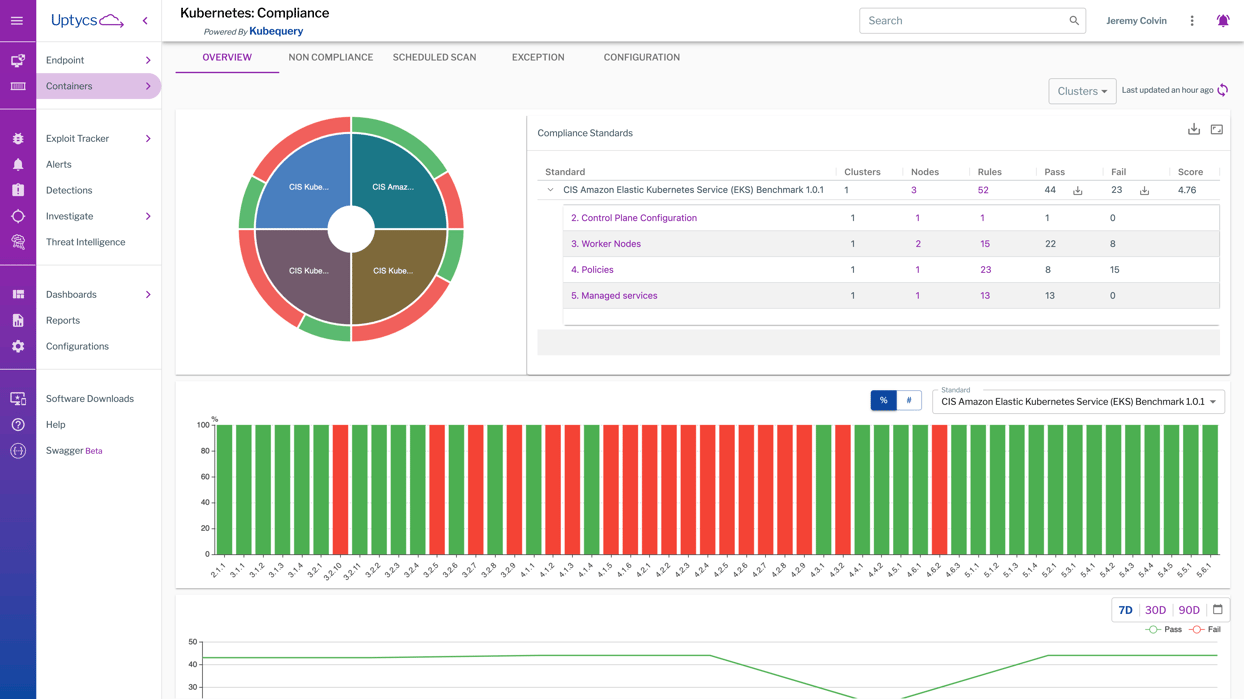
Simplify Compliance At Scale
Continuously monitor for compliant configurations (CIS Benchmarks, PCI-DSS, and SOC 2), build customizable audit rules, and identify images with failed policy checks. Uptycs offers compliance monitoring and reporting for both the Kubernetes control plane as well as nodes/pods/containers.
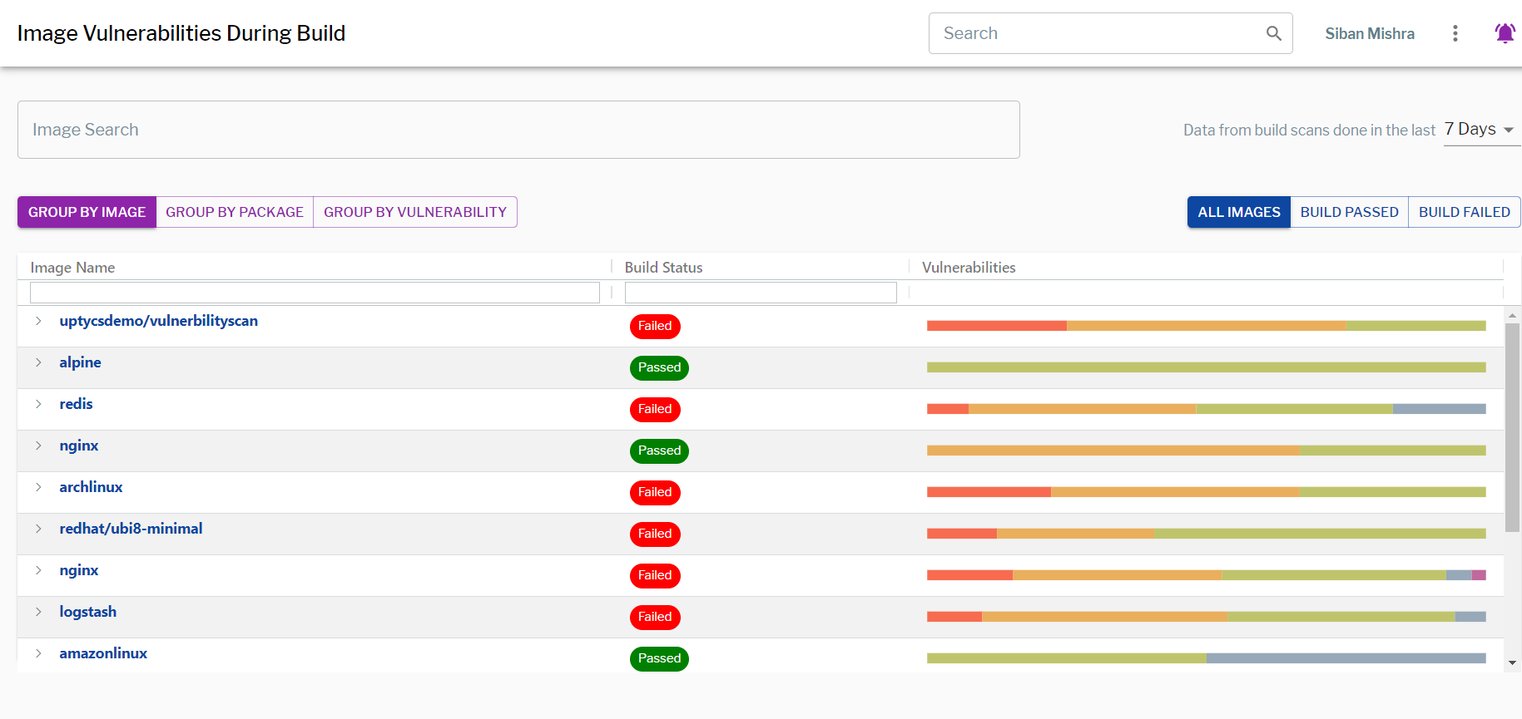
Secure The DevOps Pipeline
Scan containers for vulnerabilities at the build, deploy, and runtime stages of your CI/CD pipeline to reduce or mitigate risk in production. Enable agile DevOps workflows by reducing the time to secure and deploy containers. Scan runtime resources in real-time, immediately understanding the scope and scale of vulnerabilities in your production Kubernetes resources.
Detect and Respond to Real-Time Malicious Behavior
Create flexible YARA rules for scanning container processes with 200+ out-of-the-box YARA rules incorporated already, map container-specific behavioral detections to the MITRE ATT&CK framework, monitor known bad domains and IP addresses, and proactively scan for threats with a constantly updated APT database.
Check out this on-demand webinar to learn more about the securing the CI/CD pipeline with Uptycs.