In the intricate world of cloud security, identifying and navigating the Attack Path is crucial to understanding and mitigating potential breaches. Traditional defenses often provide fragmented insights, missing the critical link between initial exposures, like Internet Exposure, and the ensuing Lateral Movement that can occur within cloud infrastructure. Uptycs leads the charge with its advanced Attack Path analysis, which not only reveals possible points of entry and internal movements but also enables organizations to strengthen their security measures proactively. This approach is transformative, altering the defense of cloud environments against a complex array of cyber threats.
In concert with this, Uptycs' Risk Prioritization integrates with the Attack Path data to spotlight the most critical vulnerabilities. This synthesis of real-time data and contextual analysis guides security teams to focus on the highest risks, fostering a proactive rather than reactive, cloud security posture. The result is a more resilient defense system adept at pre-empting and disrupting cyber threats before they fully materialize.
Internet exposure: The breach gateway
Imagine an AWS cloud infrastructure as a complex, yet vulnerable, ecosystem. Internet exposures, often stemming from misconfigured resources associated with your EC2 instances, serve as the breach gateway for attackers. These exposures, akin to leaving a window open in a fortress, provide the first step in an elaborate Attack Path. The vulnerabilities that allow such exposures are the initial dominoes in a series of events leading to a potential security breach.
Consider an EC2 instance named ‘jenkins-test’ in an AWS environment that is inadvertently exposed to the internet, often due to an overly permissive security group or an erroneously assigned public IP address. While certain EC2 instances, like web servers, require internet exposure for legitimate reasons, others may be exposed unintentionally, creating vulnerabilities. In such cases, attackers, employing sophisticated techniques like brute force attacks using tools such as Hydra, can discover and exploit these vulnerabilities to gain unauthorized access. This instance of unintended exposure and subsequent breach marks a critical starting point on the Attack Path, underscoring the importance of vigilant and precise security configurations in cloud environments.
Lateral movement: The attacker's route within the attack path
Curling the IMDS: Credential access
After successfully brute-forcing their way inside the EC2 instance ‘jenkins-test’, the attacker exploits the Instance Metadata Service (IMDS) to obtain temporary security credentials associated with the IAM role ‘EC2-Devs’ attached to the EC2 instance. By executing a simple curl command to the IMDS, they extract credentials that provide them with additional privileges within the AWS environment.
![[1]](https://www.uptycs.com/hs-fs/hubfs/%5B1%5D.png?width=2879&height=1799&name=%5B1%5D.png)
Security group verification
From the compromised EC2 instance, the attacker then initiates a series of commands to identify a new target EC2 instance in the environment named ‘dev-integration-prod’, its attached security group(s), and its instance profile. They then verify the security groups governing the target EC2 instance (dev-integration-prod) permits SSH traffic from the EC2 instance they’re on (jenkins-test). This step ensures that their lateral movement is not hindered by network access controls.
![[2]](https://www.uptycs.com/hs-fs/hubfs/%5B2%5D.png?width=2874&height=1793&name=%5B2%5D.png)
Lateral movement: Infiltrating the network
They employ the ec2-instance-connect:send-ssh-public-key API to push a temporary SSH public key from the ‘jenkins-test’ instance to the ‘dev-integration-prod’ instance. This maneuver is critical for lateral movement within the cloud environment.
![[3]](https://www.uptycs.com/hs-fs/hubfs/%5B3%5D.png?width=2876&height=1795&name=%5B3%5D.png)
Target instance compromise: Credential escalation
Upon successfully SSH-ing into the target EC2 instance ‘dev-integration-prod’ within 60 seconds of pushing the temporary SSH public key, the attacker repeats the process of curling the IMDS for the credentials of the ‘DataStoresAdmin’ role. This time, they acquire a different set of temporary security credentials, escalating their access level within the AWS infrastructure.
![[4]](https://www.uptycs.com/hs-fs/hubfs/%5B4%5D.png?width=2872&height=1799&name=%5B4%5D.png)
S3 data breach
Using the new credentials, the attacker gains access to S3 buckets. They then proceed to download sensitive files, searching for valuable data. It is not uncommon for such files to inadvertently contain configuration details or even direct credentials for other AWS services.
![[5]](https://www.uptycs.com/hs-fs/hubfs/%5B5%5D.png?width=2870&height=1799&name=%5B5%5D.png)
RDS database compromise
Among the stolen data, the attacker discovers a file named 'rds_password.txt' stored in an S3 bucket that contains credentials for an RDS database instance. After conducting further reconnaissance to identify the RDS instance, they establish a connection to this critical asset within the cloud environment to assess the value of the data.
![[6]](https://www.uptycs.com/hs-fs/hubfs/%5B6%5D.png?width=2873&height=1798&name=%5B6%5D.png)
Data exfiltration
Having infiltrated the RDS instance and confirmed the data, the attacker begins the process of data exfiltration through shared snapshots to their own AWS account using the ‘DatasStoresAdmin’ role credentials. This stage represents the culmination of the Attack Path, where the attacker accesses and extracts sensitive information, achieving their ultimate objective.
![[7]](https://www.uptycs.com/hs-fs/hubfs/%5B7%5D.png?width=2874&height=1789&name=%5B7%5D.png)
Uptycs Attack Path: A proactive approach to cybersecurity
Uptycs’ Risk Prioritization intelligently leverages data from the revolutionary Attack Path Analysis to elevate cloud security strategies. By pinpointing and evaluating initial vulnerabilities, such as those arising from Internet Exposure and their connection to Lateral Movement possibilities, it enables organizations to identify and concentrate on the most pressing security gaps. This integrated, prioritized approach shifts the focus from merely reacting to threats to proactively strengthening defenses against potential cyber intrusions, thus transforming cloud security into a proactive, strategic asset.
Here's how the Attack Path can assist your cloud security team in addressing the scenarios outlined previously:
1. Pre-attack visualization with Uptycs Attack Path Analysis
The Uptycs Attack Path Analysis provides a preemptive visual representation of potential attack vectors. In our example, Uptycs prominently displays the exposed EC2 instance named ‘jenkins-test’, highlighting it as a high vulnerability. It also shows other EC2 instances it has reachability to. More importantly, it maps out the privileges and credentials associated with this instance, creating a visual blueprint of the resources that could be compromised. This visualization serves as a risk assessment tool and a strategic planner, guiding security teams in bolstering defenses where they are most needed.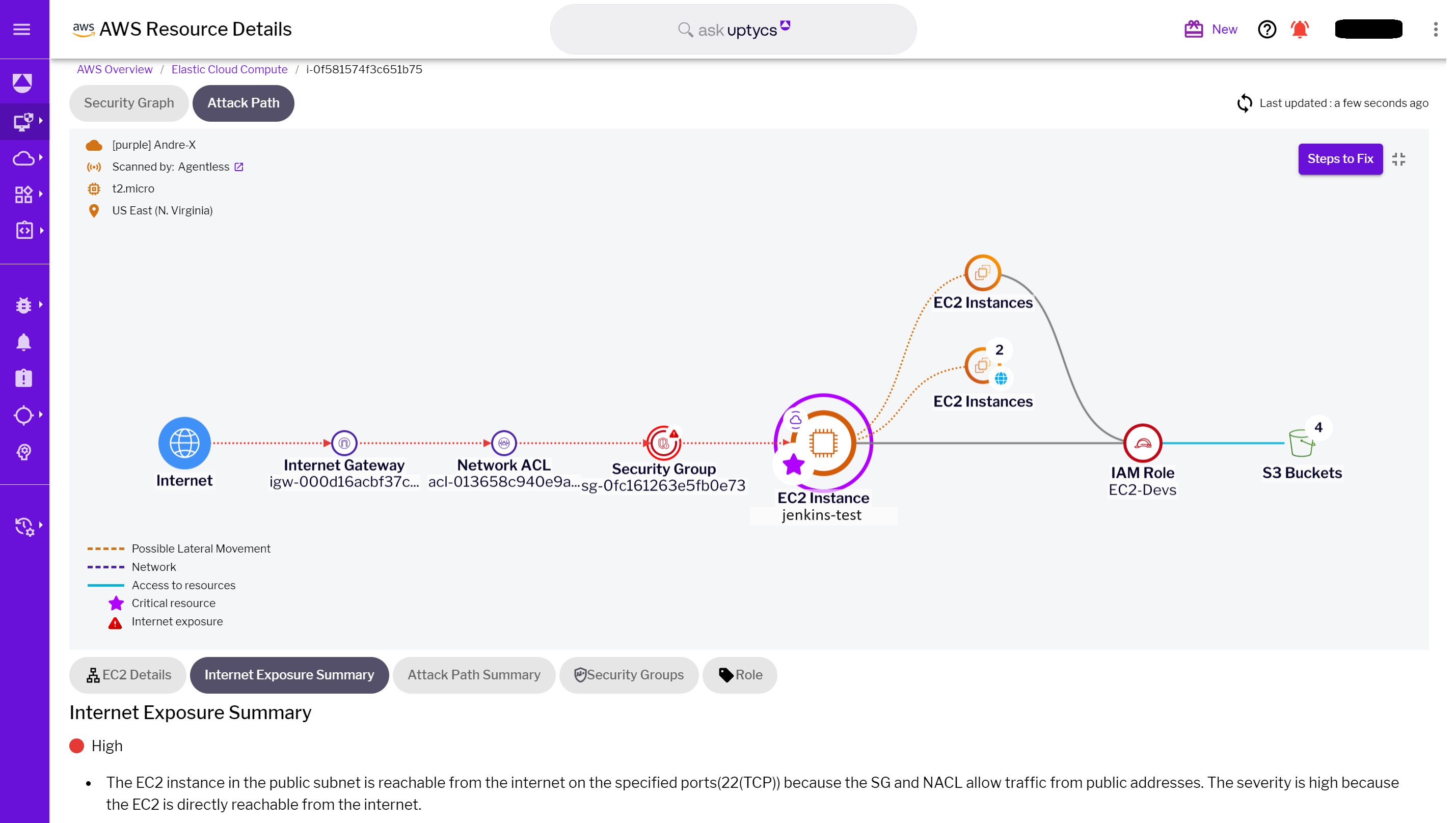
For those with the Uptycs sensor deployed on laptops connecting to the cloud, the Security Graph Attack Path Analysis reveals which secrets are stored on these laptops and the cloud resources to which they can connect. Additionally, it provides insights such as socket connections, listening processes, and ports, offering a richer context for cloud security teams.
The compromised credentials reveal the full extent of the attack surface. By focusing on the next targeted EC2 instance, named ‘dev-integration-prod,’ we can see a graphical illustration that shows the instance's access rights. This includes reaching sensitive data stores such as S3 and RDS, which is further clarified with a summary. This comprehensive visualization, paired with the summary, is crucial for understanding the layered risk landscape that arises from a single vulnerability. 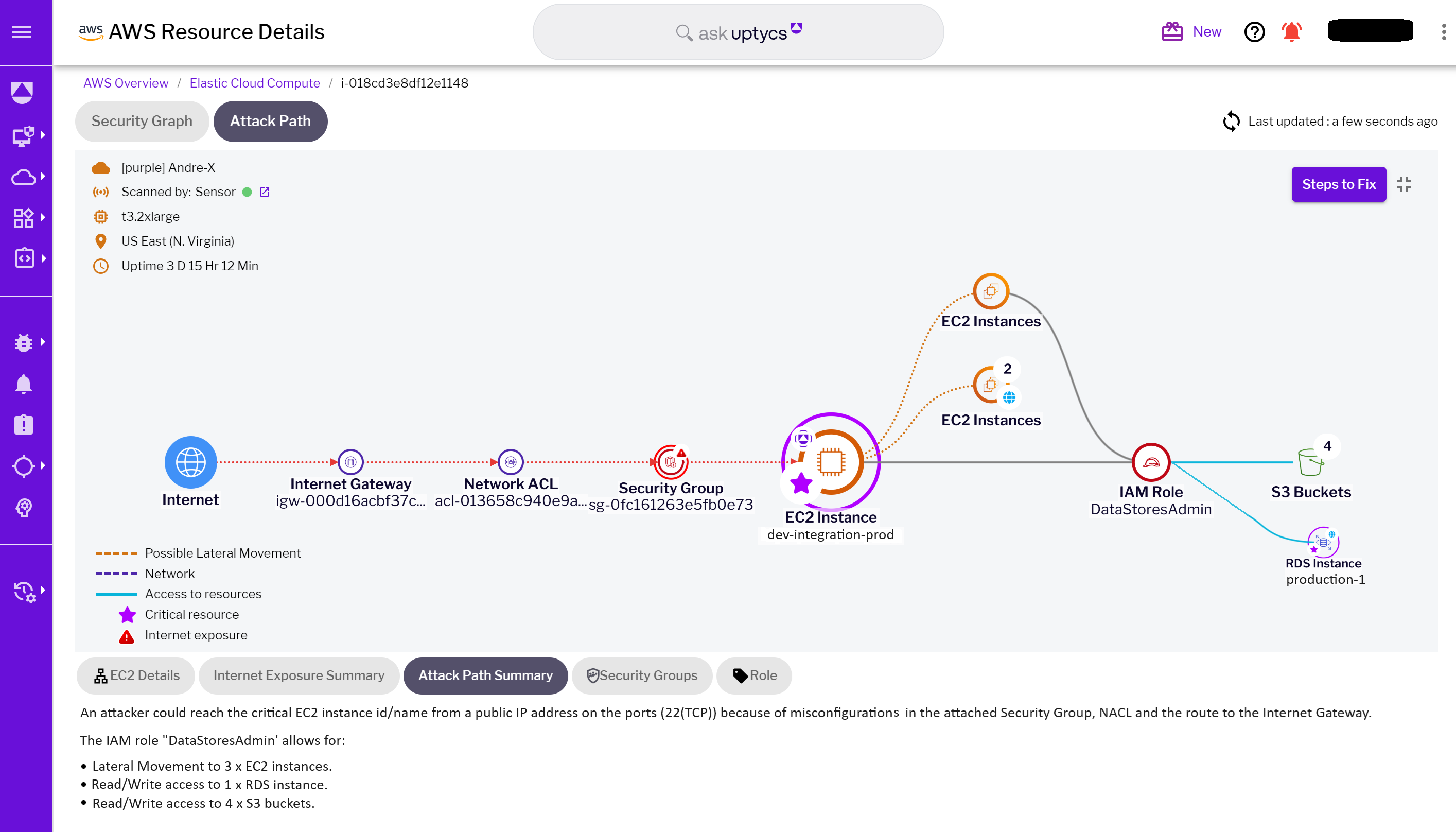
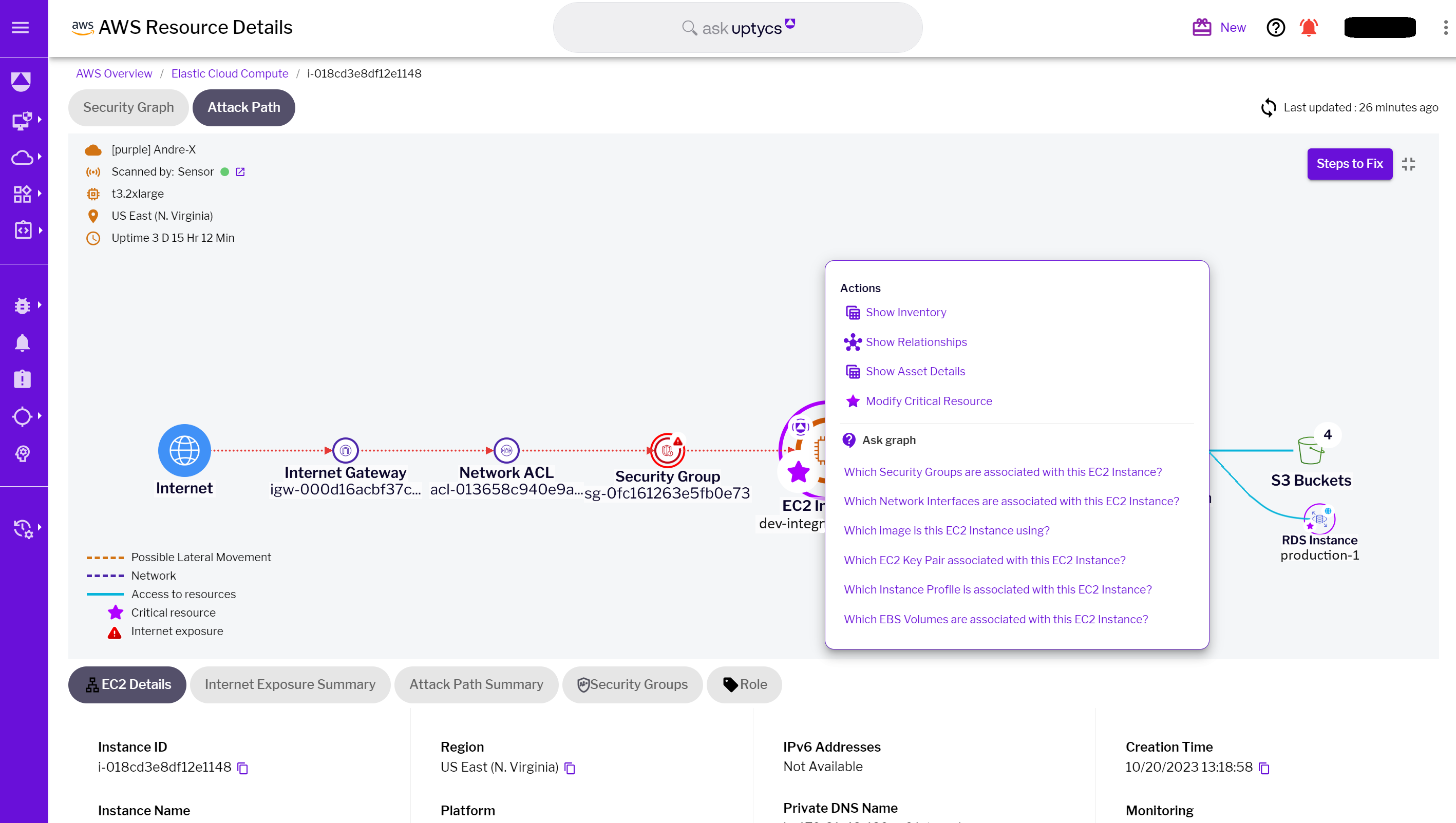
Incorporating the "Ask Graph" feature enhances Attack Path Analysis by providing an intuitive and integrated experience, particularly useful when examining resources within the scope of the attack path. For example, when analyzing an exposed EC2 instance, security teams can leverage "Ask Graph" to query the resource directly using plain English questions. This not only offers immediate insights, crucial for identifying the origin and trajectory of an attack but also significantly reduces the mean time to investigate relationships or configurations during the analysis.
By streamlining the investigative process and eliminating the need for complex queries, "Ask Graph" simplifies the unraveling of complex relationships and configurations within the cloud environment. Consequently, it makes deciphering the intricacies of a cyberattack more accessible and actionable, enabling teams to respond with the precision and speed demanded in today's cloud security landscape.
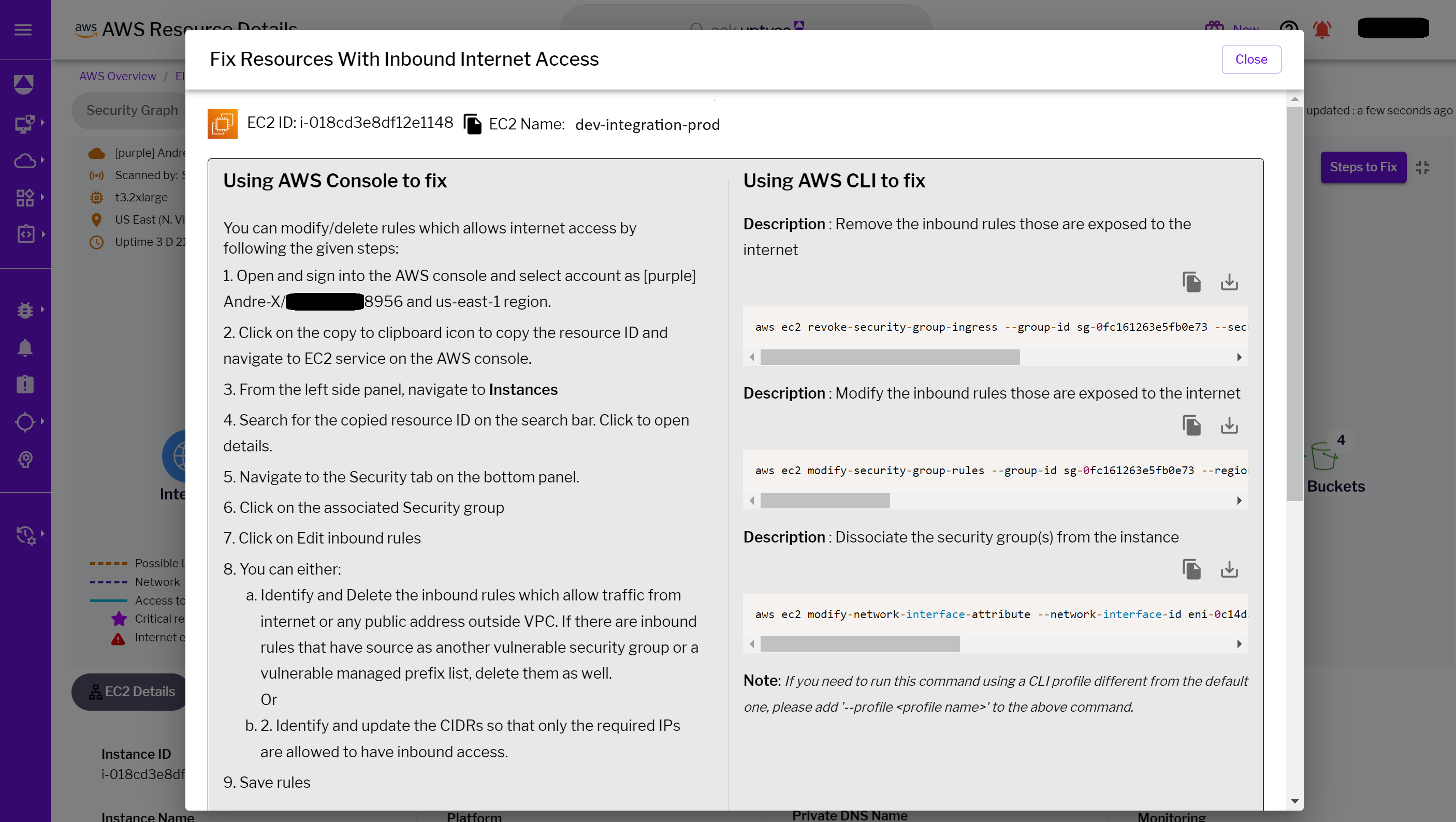
The Uptycs Attack Path doesn’t just stop at detection; it also offers actionable insights for robust defense strategies. Based on its analysis, it might suggest reinforcing security group configurations, revising IAM roles, or implementing additional security measures like encryption and MFA. These recommendations are tailored to directly address and neutralize the identified threats in the attack path.
How it works:
- Data collection: Uptycs collects comprehensive data on all cloud resources, akin to a detailed snapshot of your cloud environment's current state—essential for evaluating security postures.
- Data storage: The gathered information is securely archived within our data repository, functioning like a well-curated library of your cloud's configurations, accessible at any moment for reference and analysis.
- Analysis and relationship mapping: Uptycs continuously analyzes both existing and incoming data, exploring the configurations of your resources and their interconnections. This process is analogous to assembling a puzzle, revealing the overarching security landscape of your cloud setup.
- Identifying security insights: Leveraging a sophisticated analysis engine, Uptycs scrutinizes the web of cloud data, identifying security risks throughout your infrastructure. It delves into the nuances of how different elements interact, uncovering vulnerabilities and key risk indicators such as potential internet exposures and lateral movements. This in-depth risk analysis is vital for preemptive threat management.
- Visualizing attack paths and security landscape: Uptycs employs the processed data to craft a visual representation, the Attack Path Analysis, illustrating potential routes an attacker might take within your cloud environment. This visual tool is instrumental in highlighting the robustness of your defenses and pinpointing areas requiring enhancement.
- Integrated risk prioritization: Within this framework, Uptycs' Risk Prioritization mechanism taps into the Attack Path data, utilizing it to gauge the severity of threats. It systematically categorizes risks by assessing the gathered insights and visualizations, and assigning a priority level based on potential impact and exploitability. This refined analysis ensures that high-risk areas receive immediate attention, streamlining your security strategy to focus on the most critical aspects first. It's a strategic approach that elevates risk management from a static checklist to a dynamic, informed process
In conclusion, the Uptycs Attack Path, enriched by the "Ask Graph" feature and deeply integrated with Risk Prioritization, stands as an indispensable tool for navigating the complex terrain of cloud security. This comprehensive approach allows for the visualization and understanding of cyber threats and ensures that the most critical risks are promptly identified and addressed. By converging real-time data across various dimensions of cloud security, including Attack Path, Internet Exposure, and Lateral Movement, Uptycs elevates situational awareness and fosters a nimble response to evolving threats.
The categorization of risk into tiers—Critical, High, Medium, or Low—enables security teams to focus their efforts where they are needed most, aligning with the unique security posture and business objectives of each organization. This refined prioritization streamlines operations and offers a strategic advantage, melding technical details with business contexts for a proactive, informed defense strategy. With Uptycs, organizations are not just reacting to threats but anticipating them, staying several steps ahead in the ever-evolving cybersecurity landscape.
More from the series
Mastering Cloud Security #2: Security Graph

-1.png?width=200&name=image%20(4)-1.png)





