Visualizing complex cloud architecture and resources presents a significant challenge for any security team. This becomes even more daunting when tasked with discovering and understanding the full scope of your environment across various isolated environments (such as AWS accounts, Azure subscriptions, and GCP projects) and geographical locations (including AWS and Azure regions, as well as GCP regions and zones).
Enter Uptycs' Cloud Discovery, which not only simplifies the discovery process across all accounts and regions, but also provides invaluable assistance in troubleshooting network connectivity and IAM access through intuitive visualizations. With Cloud Discovery, what used to be a complex and error-prone process becomes a near-effortless, one-click action. Comprehending the intricate web of your cloud infrastructure transforms from a burdensome task into a seamless experience, bringing clarity to what was once a convoluted process.
Notably, Uptycs Cloud Discovery also lays the foundation for advanced security features like Attack Path analysis, the creation of a comprehensive Security Graph, and the utilization of Ask Uptycs.
Once Cloud Discovery comprehensively identifies all resources and the full extent of an environment, these capabilities become highly effective, offering a more integrated and intelligent approach to cloud security.
Traditional methods, by contrast, can be cumbersome, often involving a laborious process of navigating through multiple consoles and interfaces to gain a comprehensive view of diverse cloud resources. This can lead to a disjointed and potentially error-prone understanding of your cloud environment. This complexity is compounded when dealing with multiple subscriptions, each potentially spanning different regions and containing a variety of resources.
Bringing clarity to complex challenges: Uptycs Cloud Discovery in action
Uptycs Cloud Discovery extends beyond theoretical applications, offering real-world solutions that greatly enhance the capabilities of security teams. This blog delves into how Cloud Discovery's innovative approach to visualizing intricate cloud environments translates to significant benefits in varied practical scenarios. Read on to discover some of the key use cases Cloud Discovery addresses:
Use case 1: Discovery across all accounts and regions
Use case 2: Help troubleshoot network connectivity through visualizations
Use case 3: Help troubleshoot IAM access through visualizations
Use case 1: Discovery across all accounts and regions
Cloud Discovery offers unparalleled visibility across all your accounts and regions, a critical foundation for understanding and safeguarding your cloud environment. Consider the daunting task of determining inter-business unit communications across a multinational corporation. Without Cloud Discovery, security teams would typically engage in the cumbersome process of manually correlating data across multiple cloud accounts and regions, comparing and contrasting security groups, network policies, and access controls. This approach is not only time-consuming but also prone to oversights and errors due to its complexity.
For example, a security analyst trying to verify if two business units in North America and Europe are inadvertently exposed to each other due to misconfigured network rules would traditionally face a daunting challenge. Without Cloud Discovery, they would need to manually review network configurations in each region—a task akin to finding a needle in a haystack given the volume of data and the intricacy of cloud environments.
Uptycs Cloud Discovery, through its tagging system, simplifies this complex task. By grouping and displaying systems and connections with matching tags, it provides a clear view of their interactions. This capability is crucial for security teams, enabling them to quickly grasp the communication flow within the organization, regardless of geographical or account-based divisions. This not only saves time but also bolsters security oversight.
The comprehensive view offered by Cloud Discovery enhances other features, like Attack Path, which simulates potential cyberattacks exploiting interconnected vulnerabilities and misconfigurations. It also enriches the Security Graph with a nuanced perspective of the security landscape. Additionally, it empowers Ask Uptycs, enabling it to provide detailed and accurate responses to security queries, which can be asked in plain English. This feature of asking questions in simple language, supported by the thorough insights from Cloud Discovery, makes Ask Uptycs highly user-friendly and effective.
In essence, Cloud Discovery is not just a tool for visibility; it's a foundational element for an integrated, intelligent approach to cloud security, facilitating more sophisticated analysis and proactive defense strategies.
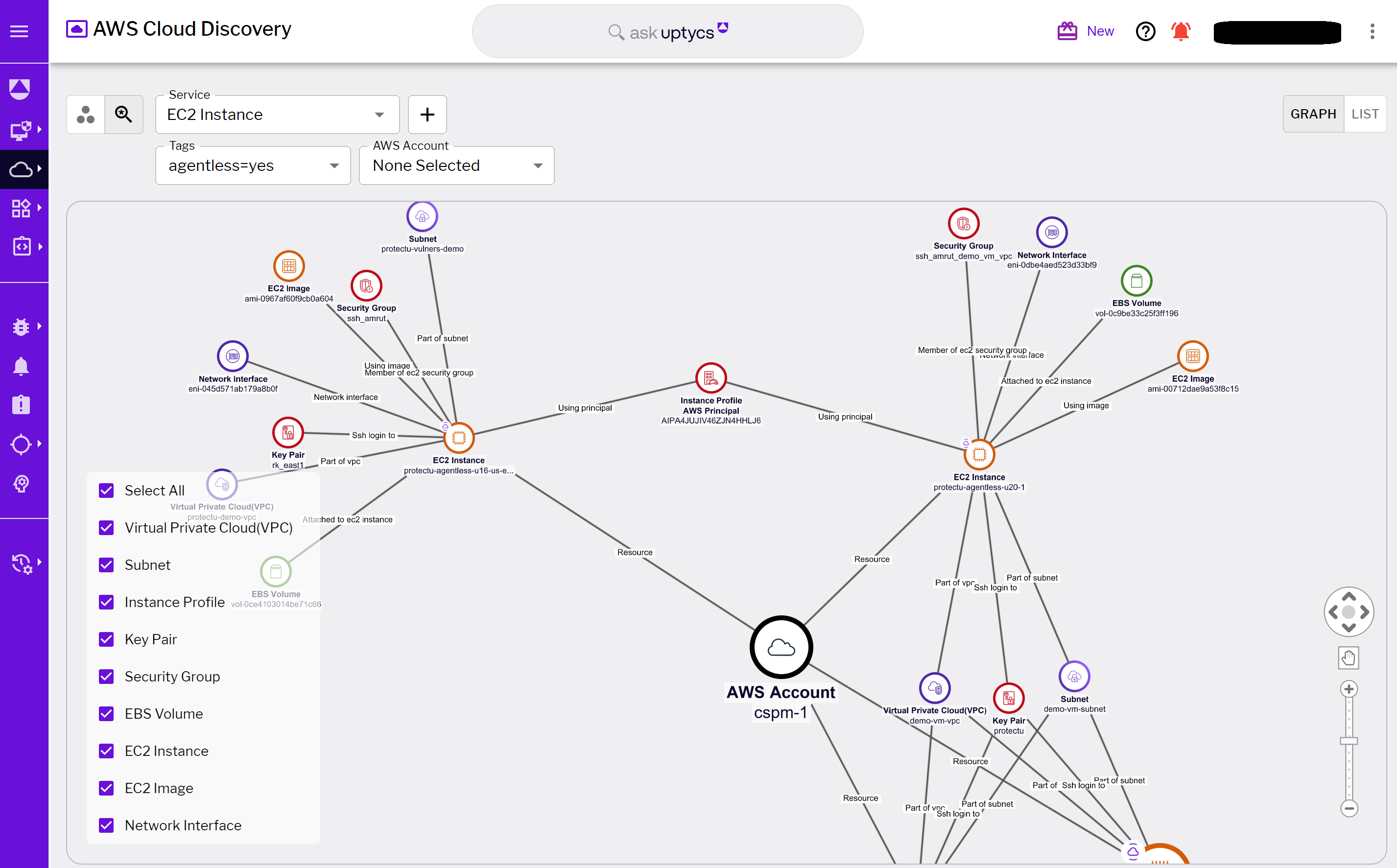 Figure 1 - Discovery assets across accounts
Figure 1 - Discovery assets across accounts
Use case 2: Help troubleshoot network connectivity through visualizations
Cloud Discovery excels in troubleshooting network connectivity issues with its visual tools, simplifying what is traditionally a complex and labor-intensive process. Without such a tool, security teams often face the daunting task of manually mapping network connections and dependencies.
For instance, consider the scenario where a security team needs to identify why certain EC2 instances are unable to communicate with a specific service in another VPC. Traditionally, this would involve meticulously checking each network component – tracing routes, verifying IP addresses, reviewing security group settings, and scrutinizing VPC peering connections. This process can be incredibly time-consuming and error-prone, especially in large and complex environments with numerous VPCs and interdependencies.
With Cloud Discovery, this complex task becomes far more manageable. It provides a logical view of connections, assisting in tracing routes, IPs, and Security Groups tied to subnets and EC2 instances, as well as all network connections of one or more VPCs. This comprehensive visualization allows security teams to quickly identify and address the root cause of connectivity issues, significantly reducing the time and effort required.
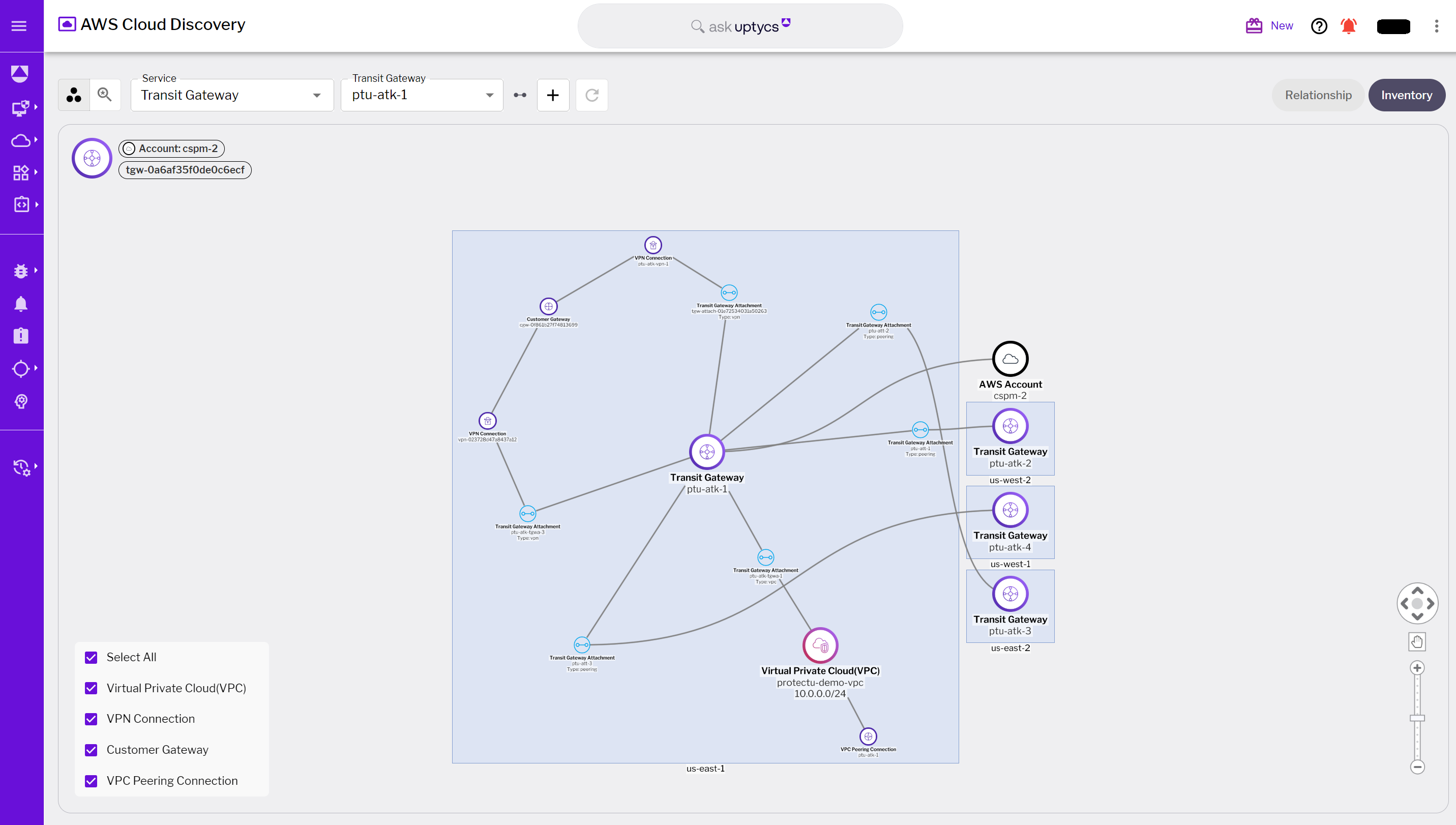
Figure 2 - Transit Gateway relationships
Once equipped with the insights provided by Cloud Discovery, security teams can leverage the powerful 'Ask Graph' feature to pivot to specific resources and gain deeper insights. This feature allows users to ask plain English questions about any resource in their cloud environment, offering an intuitive and efficient way to access detailed information.
For example, a security team might want to examine all network connections for a particular subnet. By simply asking, "Show network connections for this subnet?" in the 'Ask Graph' feature, Cloud Discovery promptly presents a detailed visualization of all the network connections associated with that subnet. This includes aspects like route tables, VPCs, and Internet Gateways, and any other relevant network attributes.
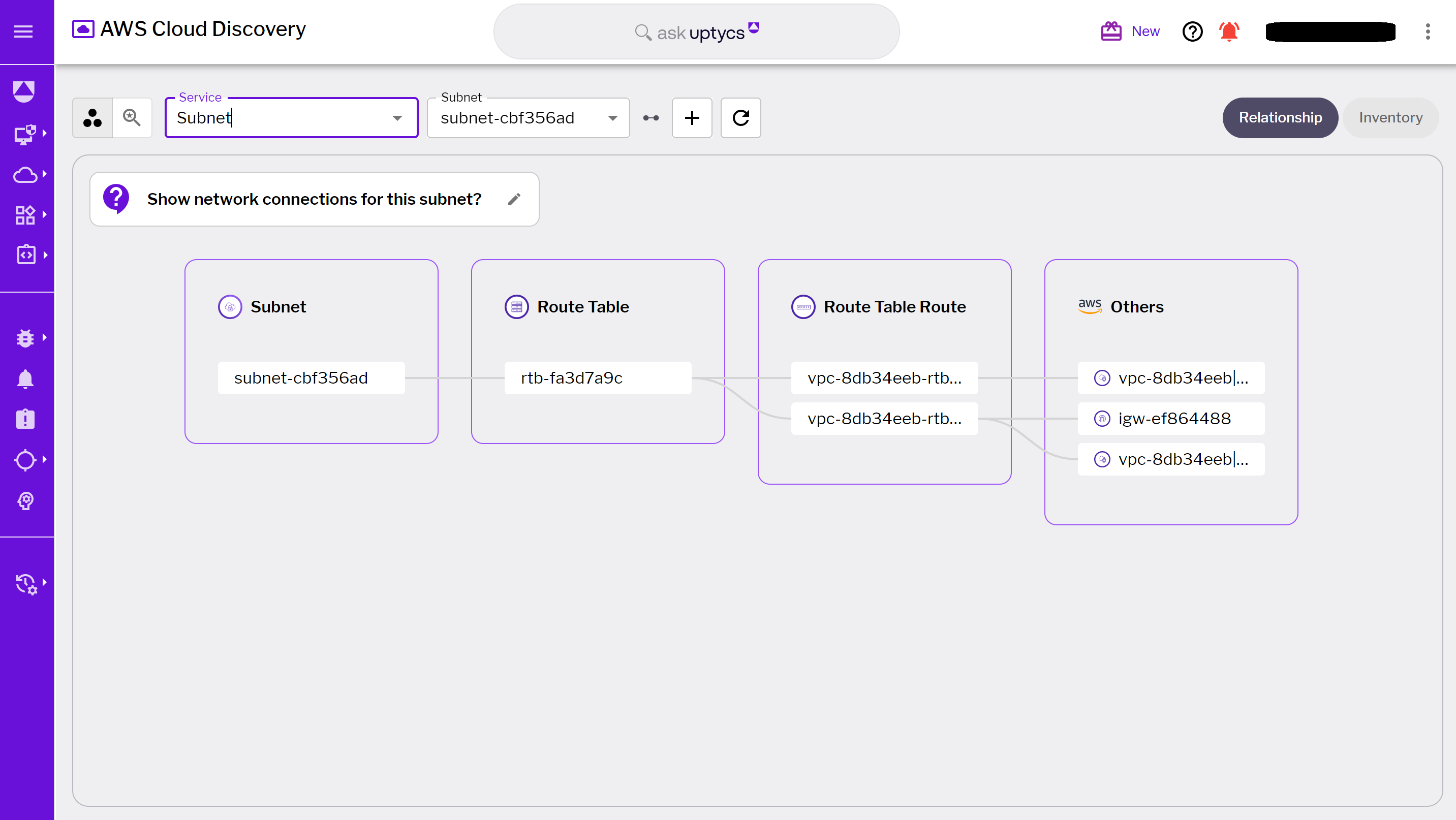 Figure 3 - Subnet network connections
Figure 3 - Subnet network connections
Use case 3: Help troubleshoot IAM access through visualizations
Cloud Discovery provides a comprehensive view of IAM access, a task that is often complex and cumbersome when approached through traditional methods. Without a sophisticated tool, security teams frequently struggle to gain a clear understanding of who has access to what resources in the cloud environment.
For instance, consider the challenge of auditing IAM policies and roles in a large organization with multiple teams and projects. Traditionally, this would involve manually combing through each IAM policy and role, cross-referencing them with the resources to ensure proper access controls are in place. This process is not only tedious but also prone to oversights, given the intricate nature of IAM configurations and the possibility of changes being made frequently.
In such scenarios, the lack of a consolidated view can lead to security blind spots. For example, an inadvertently assigned permission might grant a user more access than intended, creating a potential security risk. Identifying such misconfigurations manually is like searching for a needle in a haystack, especially in complex and dynamic cloud environments.
With Cloud Discovery, this critical task becomes significantly more manageable. It provides a clear and comprehensive view of IAM access, detailing who has permissions to various resources. When this information is combined with the network view, it becomes a powerful tool for mitigating blind spots that threat actors could exploit. For security teams, this capability is invaluable as it allows them to proactively identify and rectify potential security threats, ensuring a more robust and secure cloud environment.
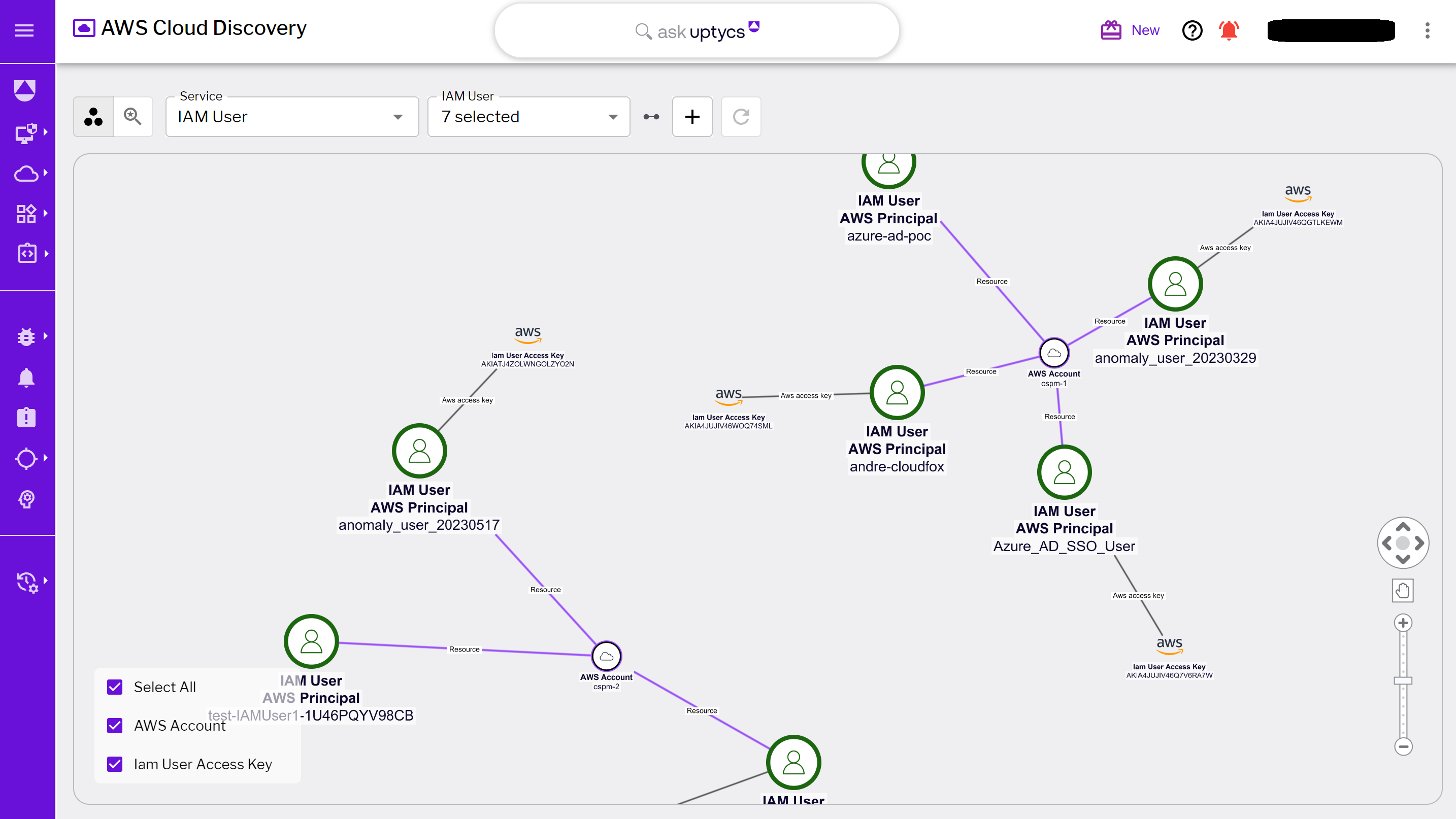 Figure 4 - IAM principals and access keys
Figure 4 - IAM principals and access keys
Embracing the future of cloud security with Uptycs Cloud Discovery
Reflecting on the challenges of traditional cloud discovery methods underscores the value of Uptycs' Cloud Discovery. By simplifying and streamlining the process, it not only saves time but also enhances the overall security posture of your cloud environment. Uptycs Cloud Discovery is not just a tool; it's a strategic partner in your journey towards a more secure, efficient, and comprehensible cloud infrastructure. Embrace the future of cloud security with Uptycs, where complexity meets clarity and informed decisions drive your cloud strategy.
More from the series
Mastering Cloud Security #1: Understanding Attack Paths and Risk
Mastering Cloud Security #2: Uptycs Security Graph

-1.png?width=200&name=image%20(4)-1.png)





