We’re able to share our results from the MITRE ATT&CK® Evaluations Enterprise Round 4. This is our second year participating in the ATT&CK Evaluations, and we are proud of our performance in both the Windows and Linux portions of the evaluation. The ATT&CK Evaluations are much-needed third-party assessments of detection efficacy.
Read more about the Uptycs results further below in this blog post, or watch the Uptycs live webinar covering the ATT&CK evaluation.
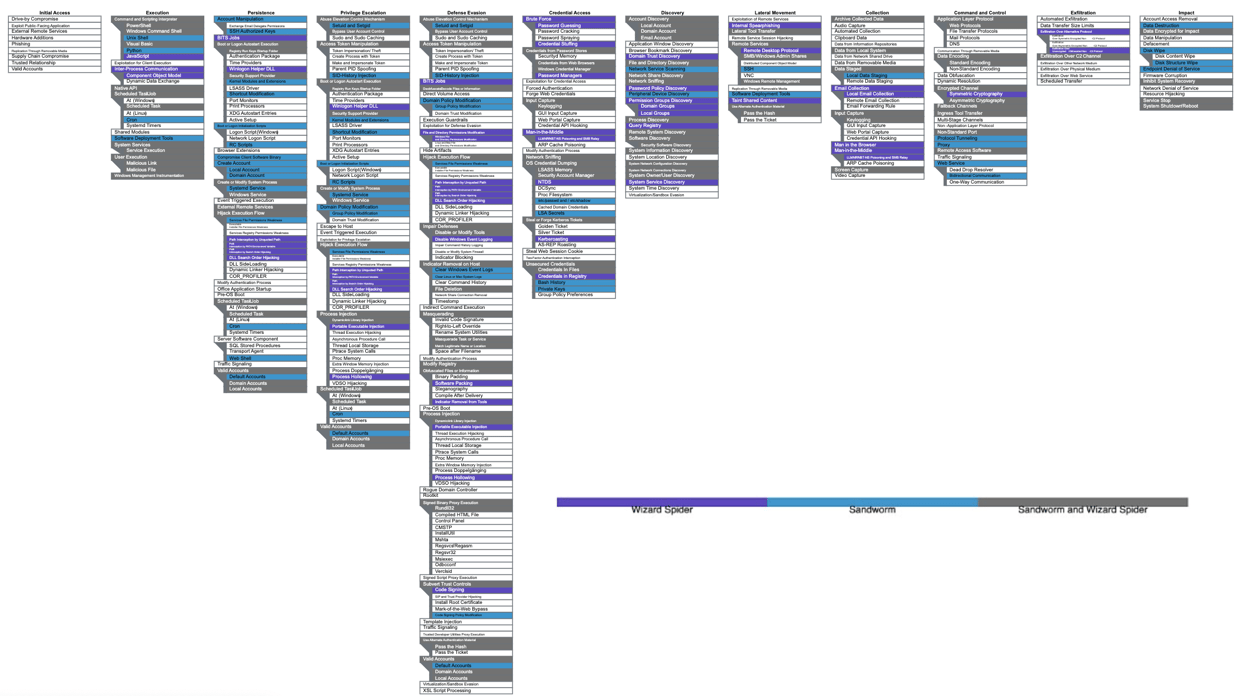
This round of evaluations focus on Wizard Spider and Sandworm threat groups that utilize ransomware and wiper malware, respectively—both categories that are top-of-mind for Security teams today. Importantly, this round is the first to measure vendors’ efficacy in detecting and blocking techniques in the Impact tactic, including Data Encryption for Impact, Data Wipe, and Inhibit System Recovery.
Wizard Spider: Ransomware
Fueled by the ease of monetization through cryptocurrency, ransomware has grown to become a multi-billion dollar criminal enterprise, with an entire ecosystem of ransomware software, services, and affiliate organizations. Ransomware actors have also become much more sophisticated in their operations, choosing targets highly susceptible to operational shutdowns and working for months to expand access within the organization to maximize their effect. MITRE Engenuity chose to focus on Wizard Spider because they are the purveyors of the infamous Ryuk ransomware family.
Sandworm: Wiper Malware
Destructive malware such as wipers have unfortunately also been in the headlines recently with the Russian hostilities against Ukraine. Although it may masquerade as ransomware, wiper malware is purely destructive in nature where the goal is to disrupt operations and not extort money. Recent wiper malware deployed against Ukrainian targets include HermeticWiper, Whispergate, IssacWiper, and CaddyWiper, and the U.S. CISA has warned international organizations to prepare for potential spillover.
The Sandworm group featured in this ATT&CK evaluation round is actually a Russian cyber military unit (allegedly the Russian GRU Unit 74455, according to attribution by the U.S. Department of Justice and U.K. National Cyber Security Centre). This group’s most notorious action was the 2017 NotPetya attacks that caused more than $10 billion in damages worldwide, including up to $300 million in lost revenues by the shipping conglomerate Maersk and $400 million in business impact for FedEx, just to name two examples.
MITRE ATT&CK Evaluations Enterprise Round 4 focused on the Wizard Spider and Sandworm threat groups, which use a subset of ATT&CK framework techniques, as shown above.
Linux in the ATT&CK Evaluations
This year is also the second time that the ATT&CK Evaluations have included a Linux component, reflecting the reality that the Linux operating system underpins critical computer systems. Historically, endpoint detection has focused on Windows. Securing Linux comes with its own complications, including the fact that some large organizations run their own customized distribution and the requirements around agent stability and performance.
Many Linux systems run production applications, making IT Operations teams wary about invasive agents that could cause a Linux kernel crash or force a reboot. The eBPF virtual machine included in newer Linux kernels has revolutionized security and observability of Linux by providing deep real-time telemetry without changes in the kernel code or loading kernel modules.
Uptycs Evaluation Results: Measurable Detection Capabilities for Ransomware
We’re extremely proud of our participation in this round of the ATT&CK Evaluations. See how Uptycs performed here. For Uptycs, these evaluations are not a marketing tactic, but an opportunity to improve and test our product. For example, as part of our preparation for the Wizard Spider and Sandworm evaluation round, we built:
- Ransomware detection: The Uptycs agent now provides generic detection and protection against ransomware attacks on Windows operating systems. The capability analyzes telemetry inside the endpoint agent so it can protect against the attacks in offline mode (as opposed to telemetry analysis in the Uptycs SaaS).
- Process code injection / DLL injection and process hollowing: The Uptycs agent now provides generic detection to process code injection and process hollowing on both Windows and Linux endpoints. Process code injection is a technique used by attackers to inject malicious code inside a trusted running process to evade detection.
- Master boot record (MBR) overwrite: The Uptycs agent now provides generic detection of MBR overwrite on Windows-based endpoints. MBR overwrite is a technique used by adversaries where the goal is to disrupt operations and make the system unusable.
- Lsass.exe memory credential dumping: To detect attacker attempts to steal credentials, the Uptycs agent now provides generic detection of lsass.exe (Local Security Authority Subsystem Service) memory credential dumping on Windows-based endpoints.
Windows, Linux, MacOS: Multiplatform Matters
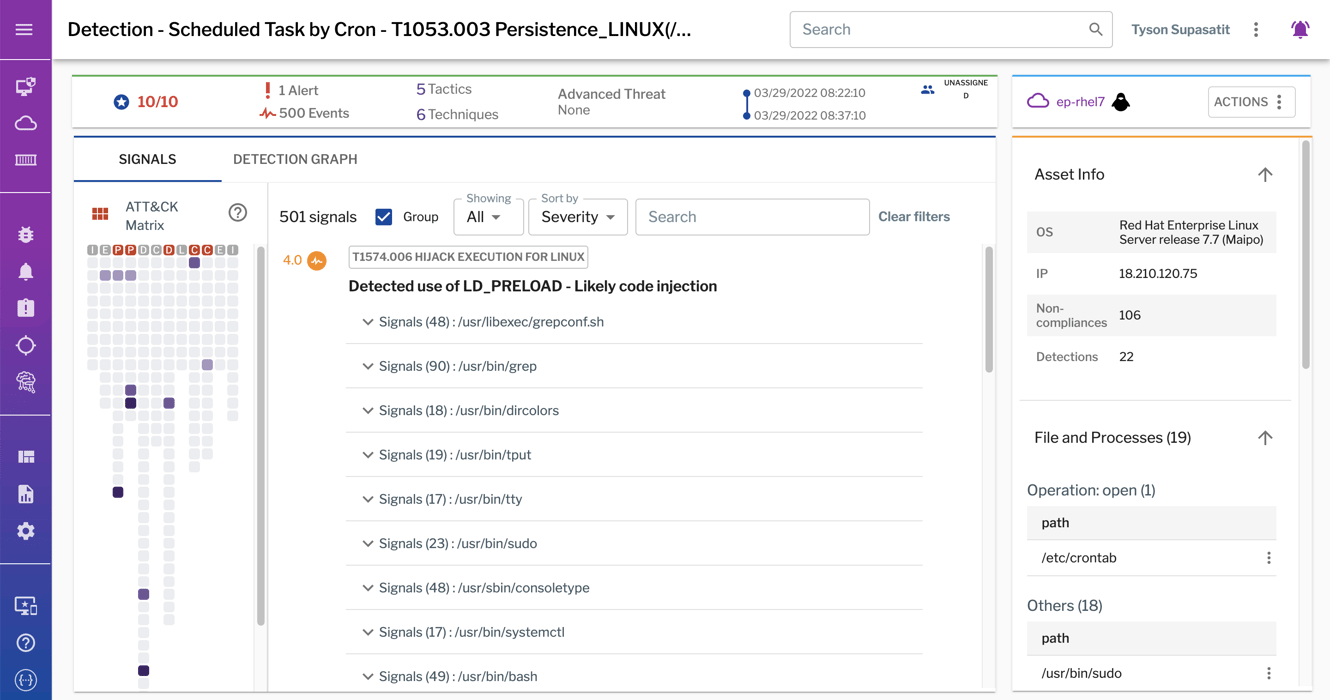
Adoption of macOS and Linux continues apace, making it more important than ever that endpoint detection platforms offer robust support across multiple platforms. Uptycs’ EDR solution performed phenomenally for both the Windows and Linux portions of the ATT&CK evaluation, identifying attempts to access SSH keys, modify the systemd service, use the crontab utility to add entries in cron jobs, and establish a remote SSH login.
Uptycs correlates signals into a single detection, providing analysts with the context they need to triage, assign severity, and investigate further.
Conclusion
The 2022 MITRE ATT&CK Evaluation couldn’t have focused on a more timely threat: ransomware and wiper malware. We’re grateful to have had the opportunity to participate. Our ATT&CK Evaluation results only measure a portion of the value that Uptycs can provide. Organizations that are evaluating endpoint security solutions should consider what else a product can provide beyond detection: file integrity monitoring (FIM), vulnerability monitoring, user-driven security, audit and compliance, and more. To learn more, download the datasheet: Why Choose Uptycs Over Traditional EDR