Atlassian Confluence users are facing yet another serious threat with the emergence of a new critical vulnerability, CVE-2023-22518. This comes on the heels of the recent alarming discovery of the zero-day vulnerability CVE-2023-22515 outlined in a previous blog post.
Atlassian Confluence is a widely used enterprise collaboration platform that allows teams to create, share, and collaborate on content and projects. It functions as a sophisticated wiki system, enabling the organization and documentation of knowledge, decisions, and ideas. Confluence integrates seamlessly with other Atlassian products like Jira, offering a centralized platform for document management, team collaboration, and project tracking.
This security flaw, already being exploited in the wild, marks a significant escalation in enterprises’ challenges related to their reliance on Confluence for collaboration and documentation needs. Following the disclosure of a zero-day vulnerability less than a month ago, CVE-2023-22518 emerges as a potent risk that demands immediate attention.
This latest vulnerability allows unauthenticated attackers to gain unprecedented control, enabling them to reset a Confluence instance and create new administrator accounts. This breach threatens the confidentiality and integrity of sensitive corporate data and jeopardizes the overall availability of enterprise systems.
In this blog, we reveal how this vulnerability threatens the confidentiality and integrity of sensitive corporate data and the nature of CVE-2023-22518, its potential impacts, and the immediate actions required to mitigate this critical threat, offering insights and solutions to help secure your digital infrastructure against this alarming security lapse.
About the vulnerability
CVE-2023-22518 is categorized as an “improper authorization vulnerability” by Atlassian security advisory. The vulnerability lies in "setup restore" endpoints on Confluence instances, which were accessible to unauthenticated users. Following are the endpoints that only the administrator user should be able to access:
- /json/setup-restore.action
- /json/setup-restore-local.action
- /json/setup-restore-progress.action
Using this, the adversary can upload a specially crafted .zip archive file using an HTTP Post request. The zip file can contain a web shell, which allows the attacker to perform remote code execution.
The fixes are available in 7.19.16, 8.3.4, 8.4.4, 8.5.3, 8.6.1, and later versions from Atlassian's official website. The vulnerability does not affect Atlassian Cloud sites (Confluence site if accessed via an atlassian.net domain). It only affects on-premises deployments of Confluence Server and Confluence Data Center.
Active exploitation
Within a few days after the vulnerability disclosure on October 31, a script to check vulnerable systems was available to the public. The script sends a POST request to confluence the server with data of three forms. One of the forms contains a zip attachment with some garbage data.
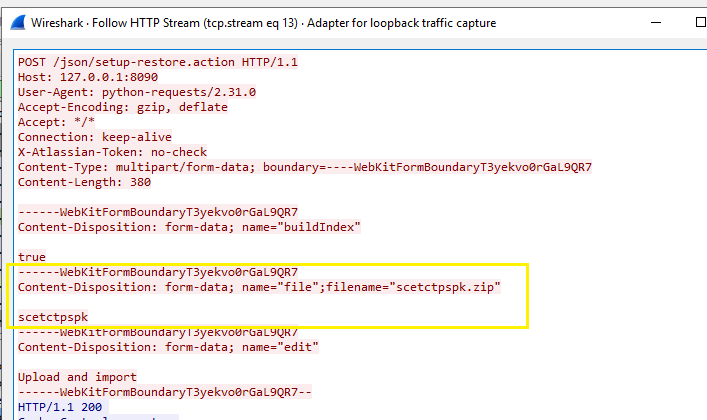 Figure 1 - HTTP request containing zip file data
Figure 1 - HTTP request containing zip file data
If the system is vulnerable, the server responds with HTTP status code 200 containing the path of the restore directory.
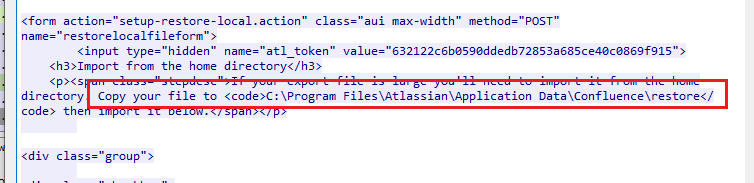 Figure 2 - Response containing backup restore directory path
Figure 2 - Response containing backup restore directory path
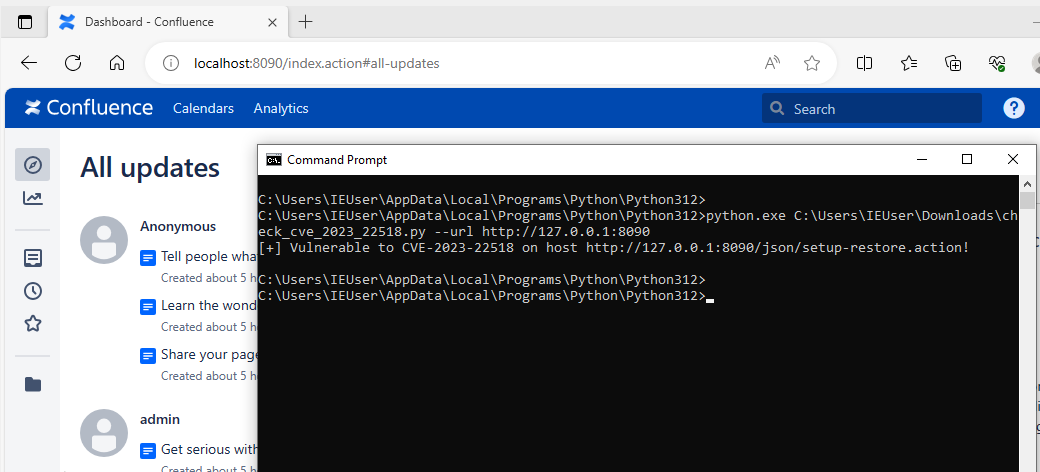 Figure 3 - Script detects vulnerable Confluence version
Figure 3 - Script detects vulnerable Confluence version
According to reports, the vulnerability is actively exploited in the wild on Windows and Linux hosts. Ransomware payload is also dropped in some of the attacks. Atlassian initially assigned this vulnerability a CVSSv3 score of 9.1, but it has now escalated to 10.0 after ransomware attacks were observed in the wild. CISA has also added the CVE to the Known Exploited Vulnerabilities Catalog list.
Mitigations and actions
Considering the vulnerability’s severity, upgrading to fixed versions is highly recommended (7.19.16, 8.3.4, 8.4.4, 8.5.3, 8.6.1, and later).
If an immediate upgrade is not possible, the following mitigations and actions are suggested by Atlassian on a temporary basis:
- Restrict external network access until the upgrade is done.
- Take a backup of your confluence instances.
- Block access to "/json/setup-restore*" endpoints.
- Keep monitoring access log files for endpoints mentioned in the exploitation part, and also check for newly created administrator accounts.
Detection through Uptycs XDR
To inventory vulnerable versions of Confluence Server, Uptycs unified CNAPP and XDR platform offers robust vulnerability scanning features for timely detection.
Uptycs XDR solution stores vulnerability scan results in a dedicated table, accessible via SQL queries, as shown below:
select * from vulnerabilities where cve_list = 'CVE-2023-22518'
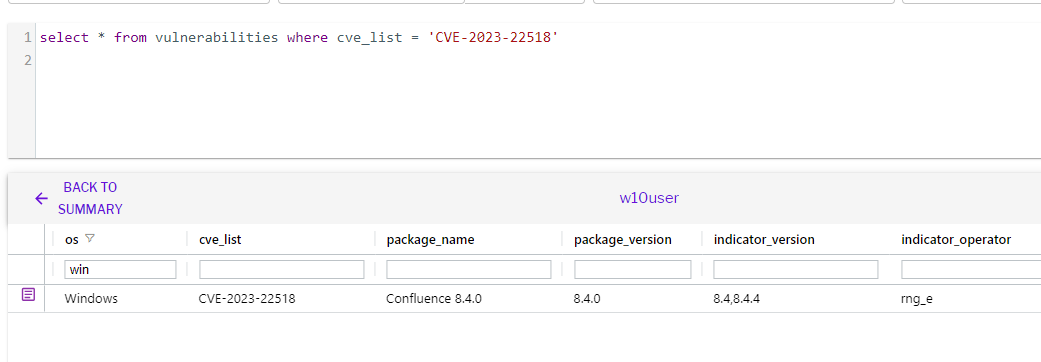 Figure 4 - Detection of CVE-2023-22518 using vulnerability scan
Figure 4 - Detection of CVE-2023-22518 using vulnerability scan
Conclusion
Atlassian Confluence is a vital enterprise application that may contain confidential documents and project plans of organizations. Hence, protecting against attacks on CVE-2023-22518 is necessary if Confluence is hosted on-premises. With a series of critical vulnerabilities coming up in Confluence, it highlights that monitoring logs and making backups of Confluence instances is as important as upgrading the versions to protect the production machines from any zero-day attacks.







