The OpenSSL Project released details about two vulnerabilities that affected OpenSSL versions 3.0.0 to 3.0.6. This blog post provides resources to Uptycs customers to help inventory and prioritize vulnerable systems for patching.
While it was initially announced as a critical vulnerability, the OpenSSL Project released two vulnerabilities that were downgraded to high. Testing done in the leadup to the full disclosure suggested that it was unlikely that the vulnerabilities could result in remote code execution (RCE) but would likely result in a crash (causing a denial of service), meaning it no longer qualified for the more serious rating according to OpenSSL’s security policy. Though, they note that with the many variations in implementation, RCE could still be possible in some cases.
Initial Vulnerability Fix Announcement
On October 25 2022 (UTC), the OpenSSL Project Team provided a public update that there was a “forthcoming release of OpenSSL version 3.0.7” that was to be made available to the public on the 1st November 2022 (UTC).
The Open SSL Project Team indicated that this patch would address a critical vulnerability that had been discovered in the OpenSSL 3.x.x library. Based on the OpenSSL’s Project Security Policy, the critical designation means the vulnerability “affects common configurations and which are also likely to be exploitable.”
Uptycs Products Are Unaffected
Uptcys has confirmed that our products, both the endpoint client software running on customer systems along with our on-premises software and our cloud servers, were not impacted by CVE-2022-3602 and CVE-2022-3786 and did not present a risk to our customers or their systems.
CVE-2022-3602: How It Works
Email Address 4-byte Buffer Overflow
This is a buffer overflow vulnerability in the code for TLS certification. Attackers would have to first get a trusted CA to sign a certificate. It mostly affects clients, not servers, since the vulnerability is in the certification verification process—which generally happens on the client side.
Most implementations have stack overflow protections, which would likely prevent remote code execution—resulting in a denial-of-service condition occurring on the system. It also may be mitigated by the stack layout for any given platform or compiler.
If an attacker were able to achieve the prerequisites, they would then “craft a malicious email address to overflow four attacker-controlled bytes on the stack,” according to OpenSSL.
CVE-2022-3786: How It Works
Email Address Variable Length Buffer Overflow
CVE-2022-3786 also involves X.509 email address buffer overflows, and the mechanisms by which it might be exploited are similar. It also appears to be unlikely to enable a remote code execution.
What’s the difference? According to Open SSL, for this vulnerability, “an attacker can craft a malicious email address in a certificate to overflow an arbitrary number of bytes containing the `.' character (decimal 46) on the stack.”
How To Identify Vulnerable Systems And Exploitation
Due to the potential seriousness of the vulnerability, Uptycs has enabled all customers with a dashboard to automatically detect if they have systems running the vulnerable OpenSSL library. Uptycs provided detections in the Vulnerabilities Dashboard and a custom dashboard for all customers on November 2nd 2022 (UTC) that identifies both of the vulnerabilities.
The custom dashboards will appear with the following names.
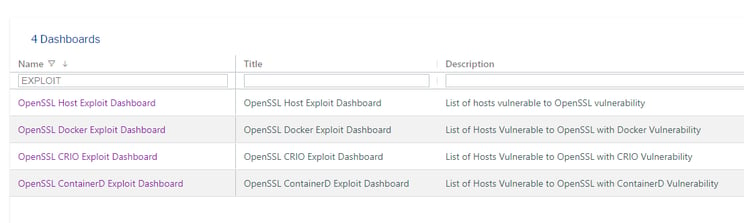
The OpenSSL vulnerability dashboards in Uptycs helps you to inventory and prioritize vulnerable systems for patching.
Vulnerable systems can be found in the host or container images vulnerabilities list, as shown below.
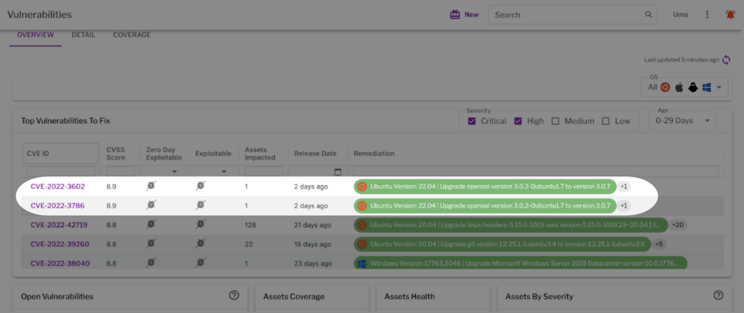
Vulnerable hosts shown within Uptycs.
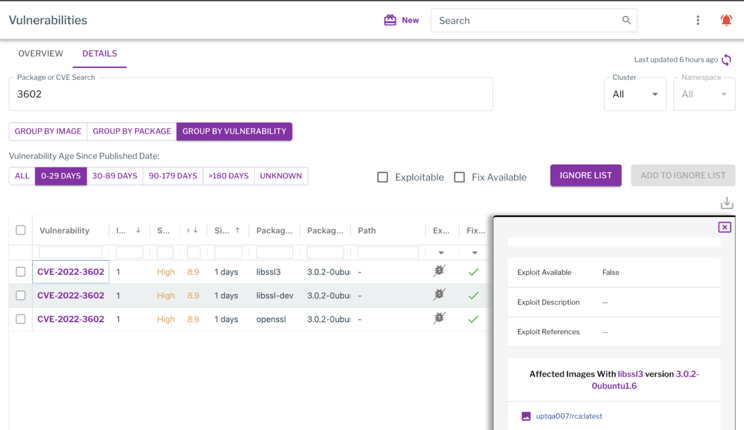
Vulnerable container images showing within Uptycs.
How To Detect If You Have A Vulnerable System Without Osquery
On most systems, you should be able to run the following command to determine what OpenSSL library is in use:
openssl version
If the version shown is between “OpenSSL 3.x.x” and “OpenSSL 3.0.6” then you need to apply the OpenSSL version 3.0.7 patch immediately. An example of what this might look like is below.

Systems may also report “OpenSSL 1.1.1 11 Sep 2018”, which is not currently known to be vulnerable.
The team at ICS is currently tracking common systems and their known OpenSSL library in use.







