Attackers don’t think in silos, and security tooling should defend across the increasingly interdependent mesh of our infrastructure. Today at KubeCon + CloudNativeCon North America, Uptycs is announcing enhanced container threat detection and hardening capabilities for Kubernetes and container deployments.
The offering unifies monitoring and container threat detection across the control plane (Kubernetes, including managed services) and data plane (running nodes and containers) of your environment so that your analysts have more context when triaging and investigating alerts. These enhancements also stretch back deeper into the CI/CD pipeline with registry scanning, secrets scanning during the build and deploy stages, and NSA/CISA Kubernetes hardening checks for drift detection.
Interested in the detailed product information? Download the product sheet for our KSPM and CWPP capabilities.
These capabilities are a natural enhancement to our unified cloud native application protection platform (CNAPP) and XDR solution, and are available as part of our Uptycs Secure module.
Container Threat Detection for the Kubernetes Control Plane
Real-time, normalized data is the foundation for detections across diverse asset fleets and scaling infrastructure. K8s and container detections are mapped to MITRE ATT&CK tactics and techniques of attacker behaviors, with Uptycs tracking both K8s audit logs and container process events to identify malicious behavior. The control and data plane have a special relationship that adds important context for analysts when trying to determine if an alert is legitimate and what the severity of the incident is.
Uptycs normalizes telemetry in real-time, meaning data from the control plane and data plane is ready to be correlated and easily JOINed immediately. This makes getting visibility into your assets much more accessible, and gives the strong foundation needed to build high-powered detections as outlined below through two examples.
Detection example 1: External request to command execution in pod - T1610 Execution Kubernetes
Issue: Attackers run 'exec' commands to execute malicious code and compromise resources within a cluster. This can lead to remote code execution or lateral movement.
Security control challenge: Administrators implement least privilege policies, limiting access to the "pods/exec" so that attackers don't get enough permissions to run exec cmds. With scaling infrastructure and rising number of clusters, tracking and remediating external exec commands strains the limits of security team resources and time.
Detection with Uptycs: Uptycs continuously monitors K8s runtime activities to detect malicious activities that try to execute commands within containers. For this detection, Uptycs detects the source IP address for the request_uri as an external request looking to pod exec into the container.
Detection example 2: Privileged pods being created in Kubernetes cluster - T1610 Execution Kubernetes
Issue: If attackers get access to a privileged container or start a new privileged container, then they can access host resources, compromise the host resources, or compromise other containers running on the same node.
Security control challenge: First, administrators can limit the number of privileged containers and create privileged pods only when required. Second, they configure Kubernetes Network Policies to restrict network access to privileged containers.
Detection with Uptycs: Uptycs continuously monitors K8s activities using Kubequery to detect and issues alerts at the control plane layer when privileged containers are created. For this detection, Uptycs detects during the creation process that a privileged container has been initiated. As per least privilege best practices, privileged containers should not be created. Attackers will look for privileged containers or create privileged containers themselves if they compromise the control plane.
By alerting on the creation process, teams can quickly assess and minimize the risk of these attacker tactics and techniques. There are alternatives to privileged nodes, for example: Add the necessary capability to a container rather than providing all privileges to a container by running it in a privileged mode.
Security Enhancements From Build Through Runtime
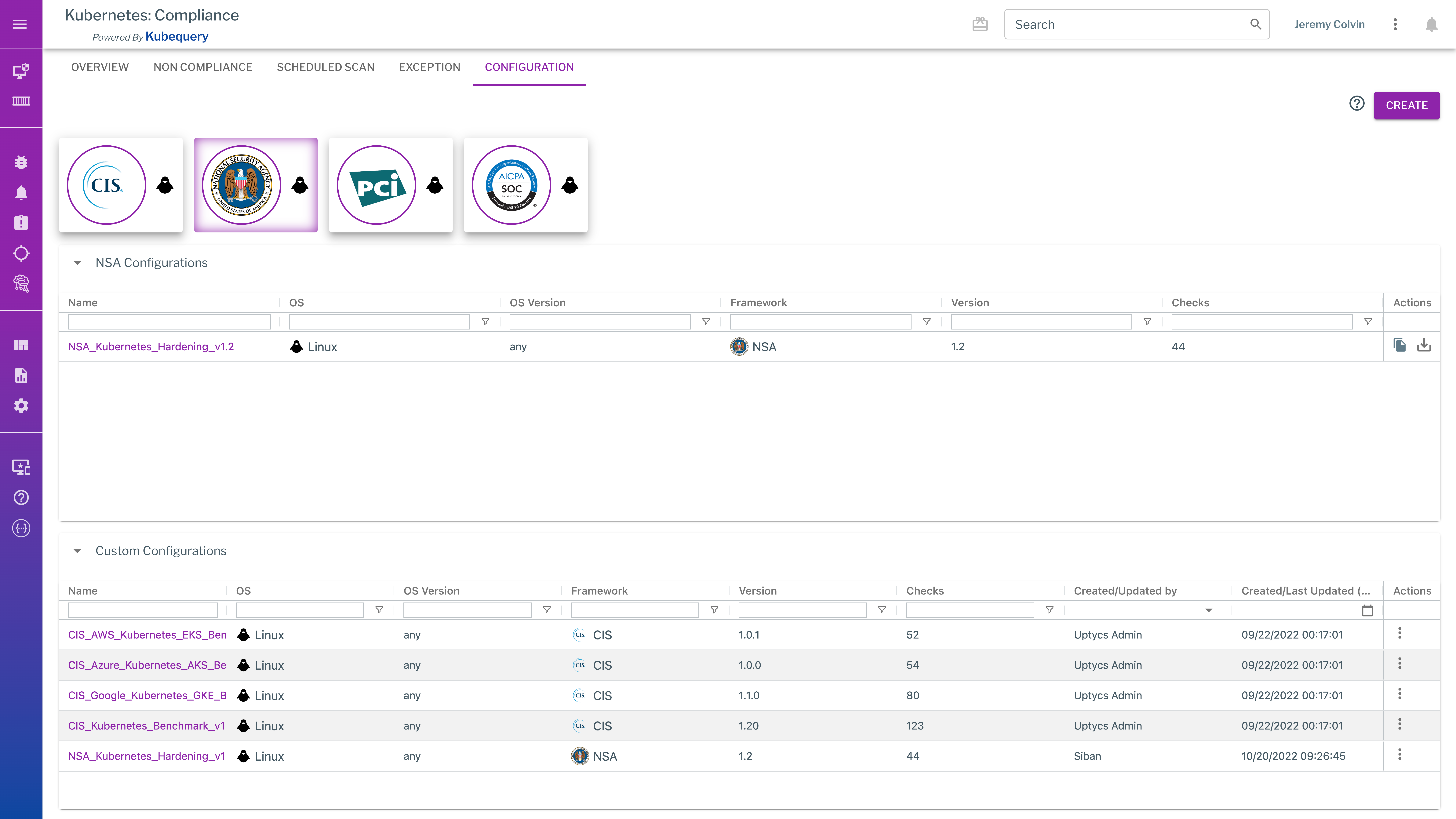
Compliance and Drift Detection with NSA and CISA Kubernetes Hardening Checks
Keep runtime assets secured and configured with recent Kubernetes hardening guidance from the U.S. National Security Agency and Cybersecurity and Infrastructure Security Agency. These checks provide clear answers to how you should harden a given K8s cluster or configure your pods.
Detection Enhancements for Control Plane and Data Plane
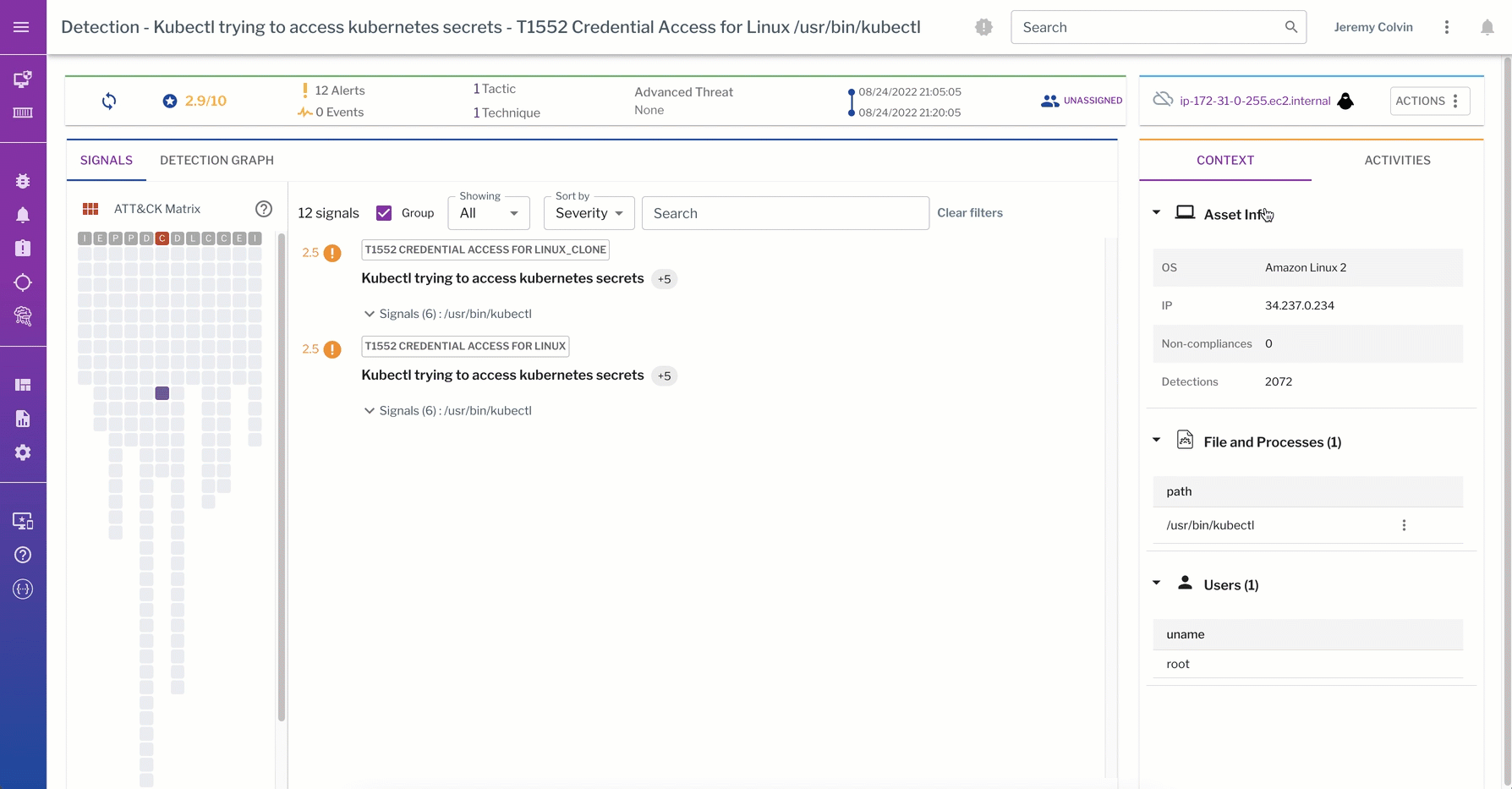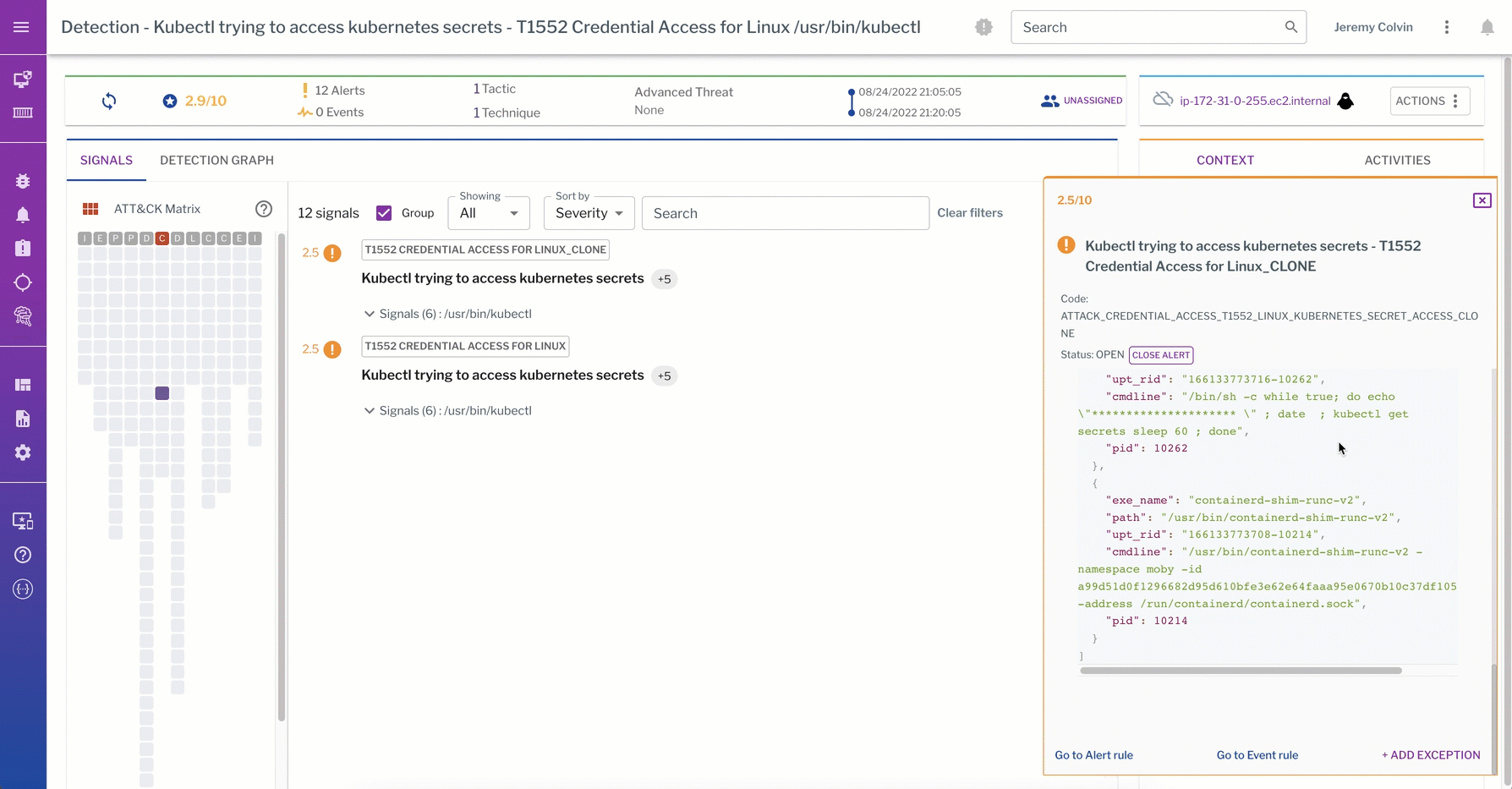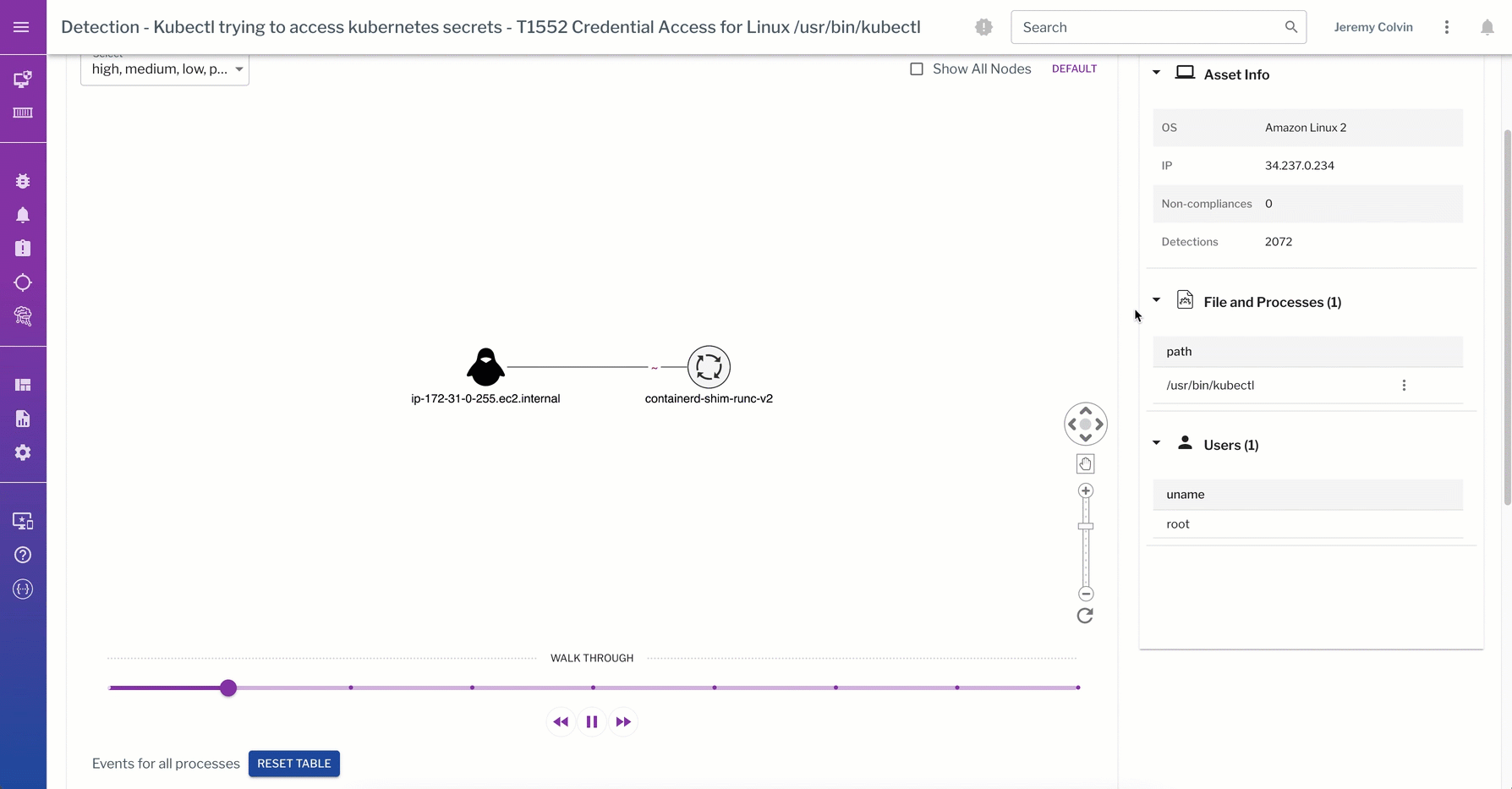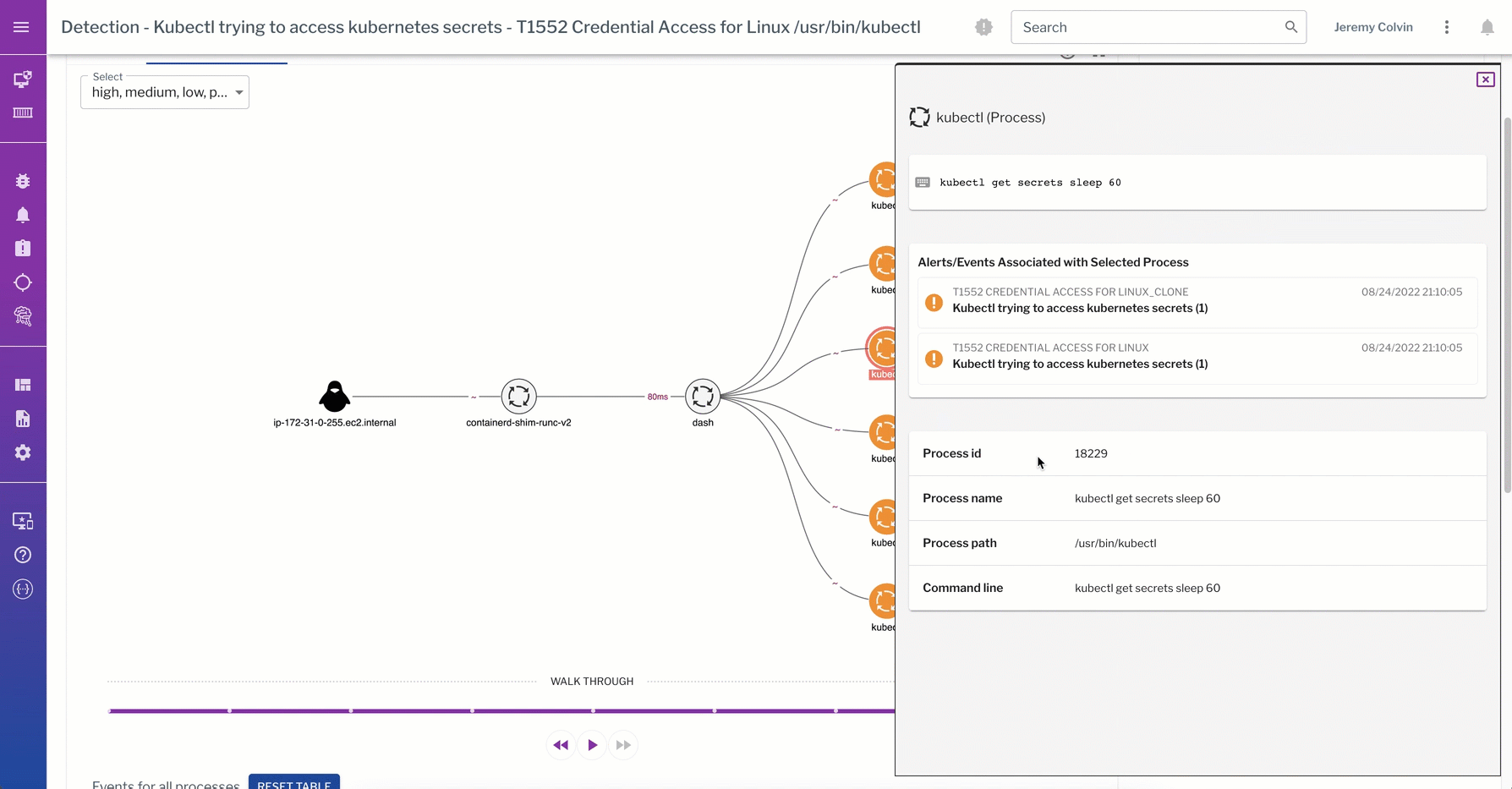
Rich process and socket event data are core to detections at the data plane that track what commands attackers ran in a container, what process events that command spawned, or even what data was actually touched. This data can be correlated back to the control plane to comprehensively track attackers and protect across both the control plane and data plane.
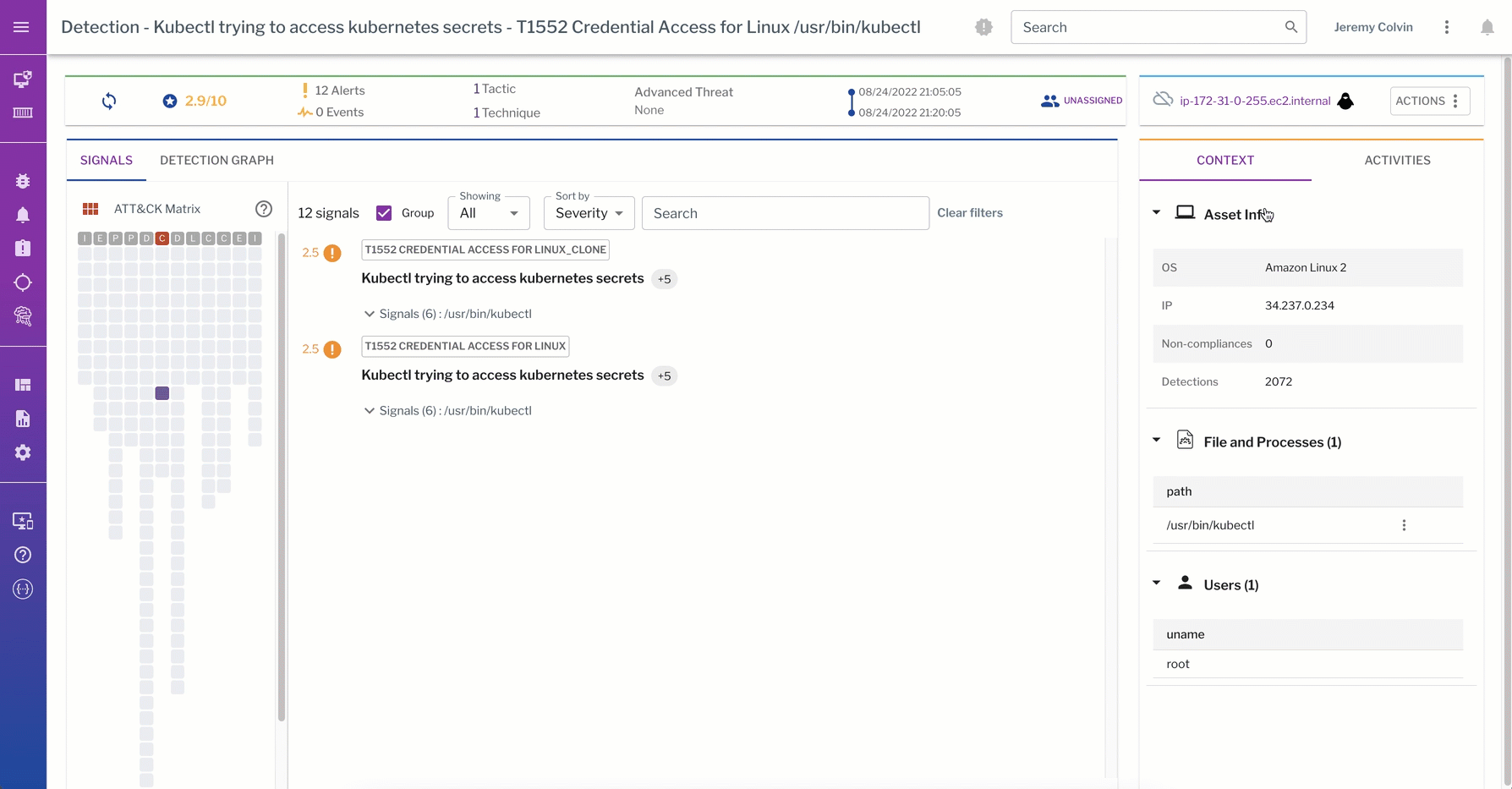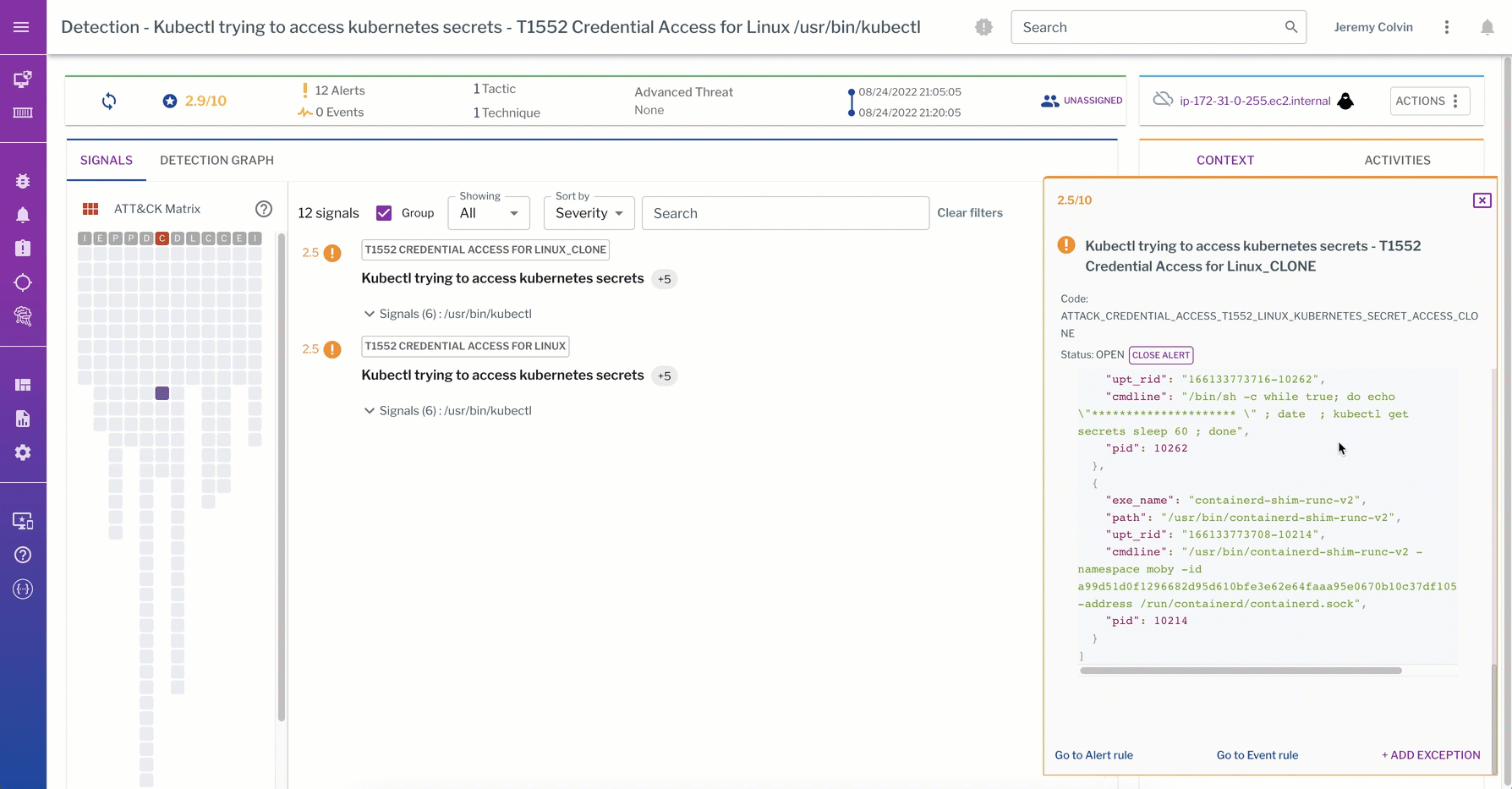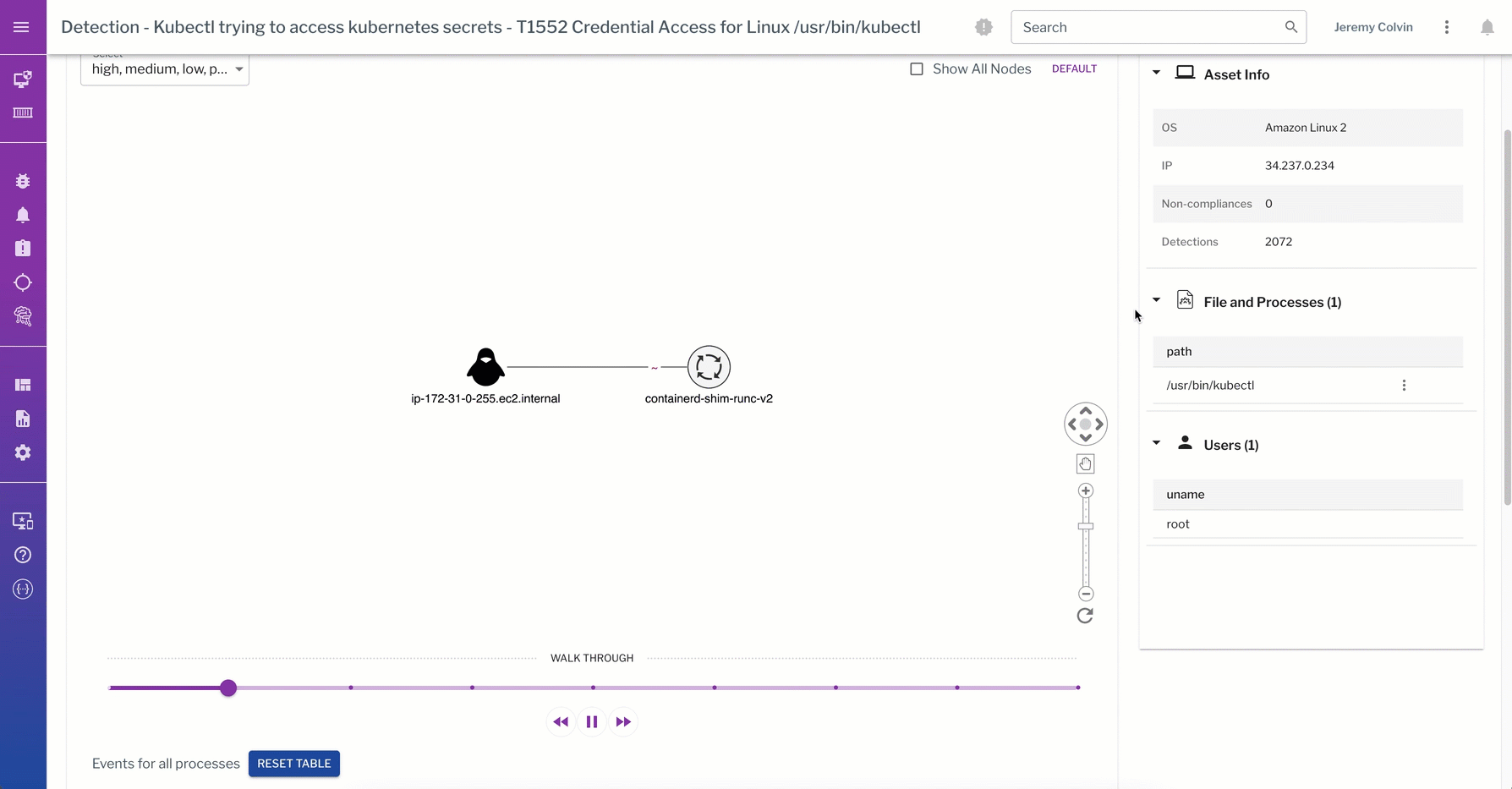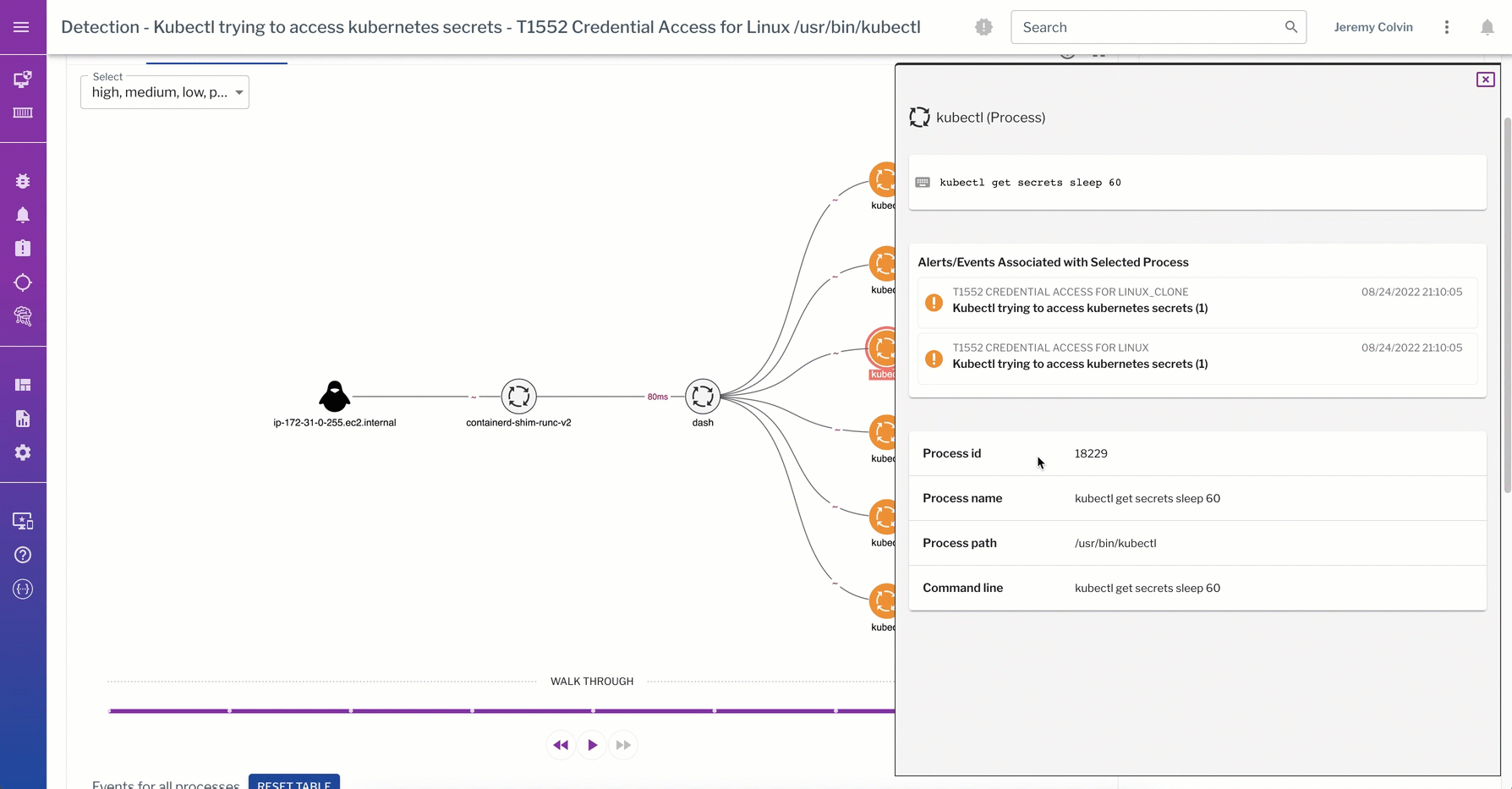
This detection from the data plane captures a kubectl trying to access K8s secrets. The process graph walks through the process events captured from the linux container during detection of the “kubectl get secrets” command.
Registry Scanning And Secrets Scanning
Automated registry scanning for Docker, JFrog Artifactory, Azure, and AWS ECR for vulnerabilities, using over 7M+ indicators with fix and exploit information provided. Apply exclusion lists or fail container images at deploy time based on known vulnerabilities or secrets in images, Secrets scanning uses YARA rules and 100+ regex based alerts, incorporated into your CI/CD pipeline for Jenkins, Gitlab, Github Actions and fails image builds when secrets are discovered.
Uptycs and the Kubernetes Community: KubeCon+ CloudNativeCon
Interested in learning more about these enhancements and our Kubernetes security solution? Uptycs will be at booth #G29 at KubeCon + CloudNativeCon. Stop by! We will have a virtual booth as well if you won’t be attending in-person.
In November, Sudarsan Kannan (Director of Product Management) joins us on Uptycs Live for a special webinar diving deep into the challenges around building container threat detection for Kubernetes, what makes container threat detection so powerful at the control plane and data plane, and the importance of implementing security controls in the build cycle.



.png?width=7680&height=4320&name=devk8con.uptycs.dev_ui_kubernetes_registry_selectedTab=registryScan(Hi%20Res%20Screenshot%20-%20New%20Breed).png)




