The Uptycs threat research team regularly monitors the TTPs (tactics, techniques and procedures) of the latest malware using our threat intelligence sources and systems. Organisations can use this bulletin as a tool to evaluate and form a more robust detection and protection posture against the latest threats in Windows, Linux and macOS platforms.
The threat bulletin covers several aspects, such as:
- Techniques used by the malware samples in our threat intel sources
- Commonly abused commands and utilities in Windows, Linux and macOS platforms
- Top prevalent malware families in the wild for Windows, Linux and macOS platforms
- Uptycs Threat Research articles published by the threat research team
- Threat actors observed for the quarter
- Malware/targeted attacks for the quarter
- Vulnerabilities/exploits in Windows, Linux and macOS platforms
- General recommendations based on our observations
The key highlights of our recently published Q3 threat bulletin are:
-
In this latest quarter (July - September 2021), we observed the following prevalent malware:
-
Loki and Warzone RAT are the prevalent malware in Q3 for Windows platforms, taking that spot from Agent Tesla and Qbot in Q2.
-
XorDDOS is the most prevalent malware for Linux. Mirai continues to be seen in Q3 as well with small numbers of Gafgyt.
-
Shlayer & Bundlore are still in action during Q3 on macOS.
-
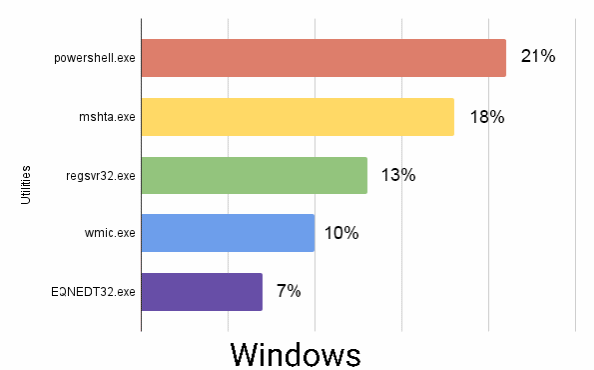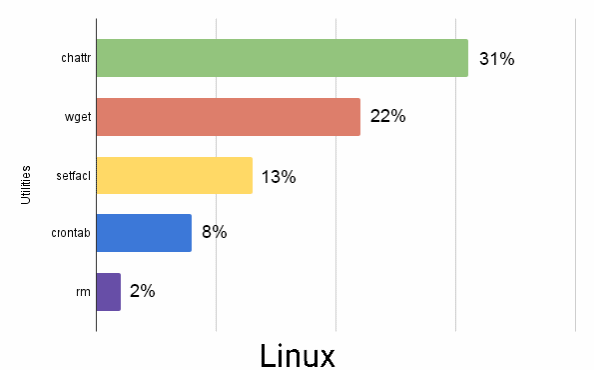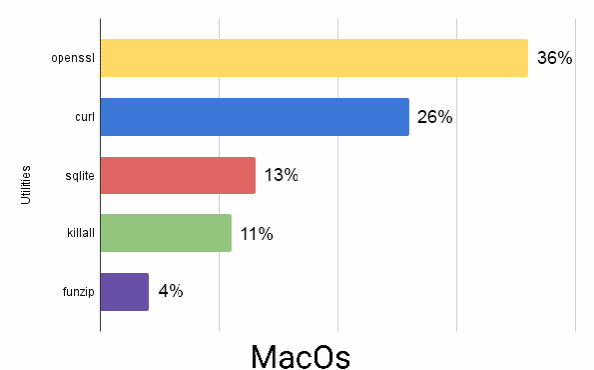
A majority of Loki malware and AgentTesla leveraged the EQNEDT32.exe Windows utility with decoy documents in the Execution phase of the attack lifecycle.
-
Threat actor activity of APT31, APT41, FIN8, SharpPanda, InkySquid, Lyceum, Praying Mantis and DarkOxide have been reported in the news.
-
REvil and DarkSide Ransomware gangs are in the limelight actively performing attacks on corporate entities, as reported in the news.
-
Windows Print Spooler Remote Code Execution Vulnerability (PrintNightmare) is being leveraged by threat actors in malware attacks.
-
Critical vulnerabilities in IOT devices like CVE-2021-31755, CVE-2021-1497, CVE-2021-22502 were targeted by some of the active variants of Mirai.
An excerpt of the Commonly abused commands and utilities in Windows, Linux and macOS platforms is shown below.