Tags
Threats
The Uptycs threat research team regularly monitors the TTPs (tactics, techniques and procedures) of the latest malware using our threat intelligence sources and systems. Organisations can use this bulletin as a tool to evaluate and form a more robust detection and protection posture against the latest threats in Windows, Linux and macOS platforms.
The threat bulletin covers several aspects, such as:
- Techniques used by the malware samples in our threat intel sources
- Commonly abused commands and utilities in Windows, Linux and macOS platforms
- Top prevalent malware families in the wild for Windows, Linux and macOS platforms
- Uptycs Threat Research articles published by the threat research team
- Threat actors observed for the quarter
- Malware/targeted attacks for the quarter
- Vulnerabilities/exploits in Windows, Linux and macOS platforms
- General recommendations based on our observations
The key highlights of our recently published Q3 threat bulletin are:
- In this quarter, we have observed the following prevalent malware
- Formbook and IcedID are the prevalent malware in Q4 for Windows platforms, taking that spot from Loki and Warzone RAT in Q3
- Tsunami and Mirai were seen in large numbers in Q4 mainly due to the log4j post exploitation attempts
- Shlayer continues its evergreen in action on macOS.
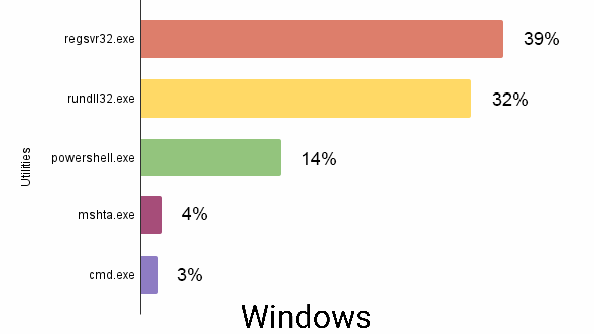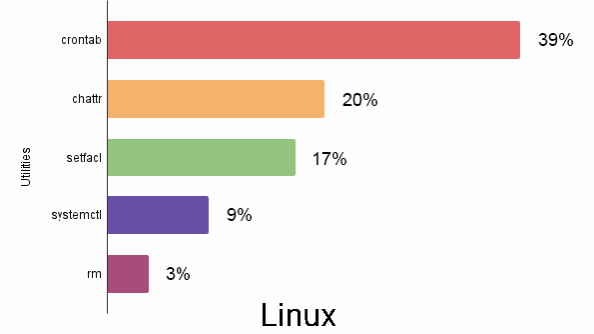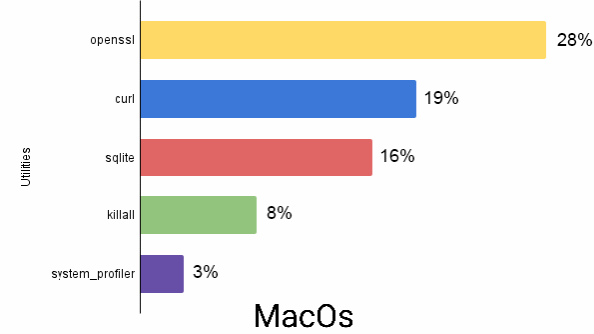
- Regsvr32.exe and Rundll32.exe are the most abused utilities for Windows platform and Crontab has been observed for Linux platform
- Apache Log4j, was plagued with a series of vulnerabilities (CVE-2021-45105, CVE-2021-45046, CVE-2021-44832, CVE-2021-44228) during the month of December 2021. These vulnerabilities were leveraged by threat actors to deploy different malicious payloads in the vulnerable machines
- Threat actor activity of MuddyWater, BlackByte, MosesStaff and Lazarus have been reported.
- We identified attackers deploying malicious container images on Docker Hub for performing coin mining operations.
- We came across reports on the return of the infamous Emotet malware.
An excerpt of the Commonly abused commands and utilities in Windows, Linux and macOS platforms (during October - December 2021) is shown below.