Research by: Karthickkumar K
Qbot (a.k.a. Qakbot or Pinkslipbot) is a banking trojan that steals sensitive information from victims’ machines and sends it to a Command and Control (C2) server. This threat was identified in 2007 and is still active with different variants.
The Uptycs Threat Research team recently observed a few changes in the infection flow of Qbot. A DLL side-loading method to execute malicious code helps malware bypass detection mechanisms. Another technique we’ve observed in the Qbot binary is self-debugging (using environment variables) which it uses to check if the system is already infected. Further, some new versions of Qbot binary target the wermgr.exe process to inject the malicious code.
Infection Flow
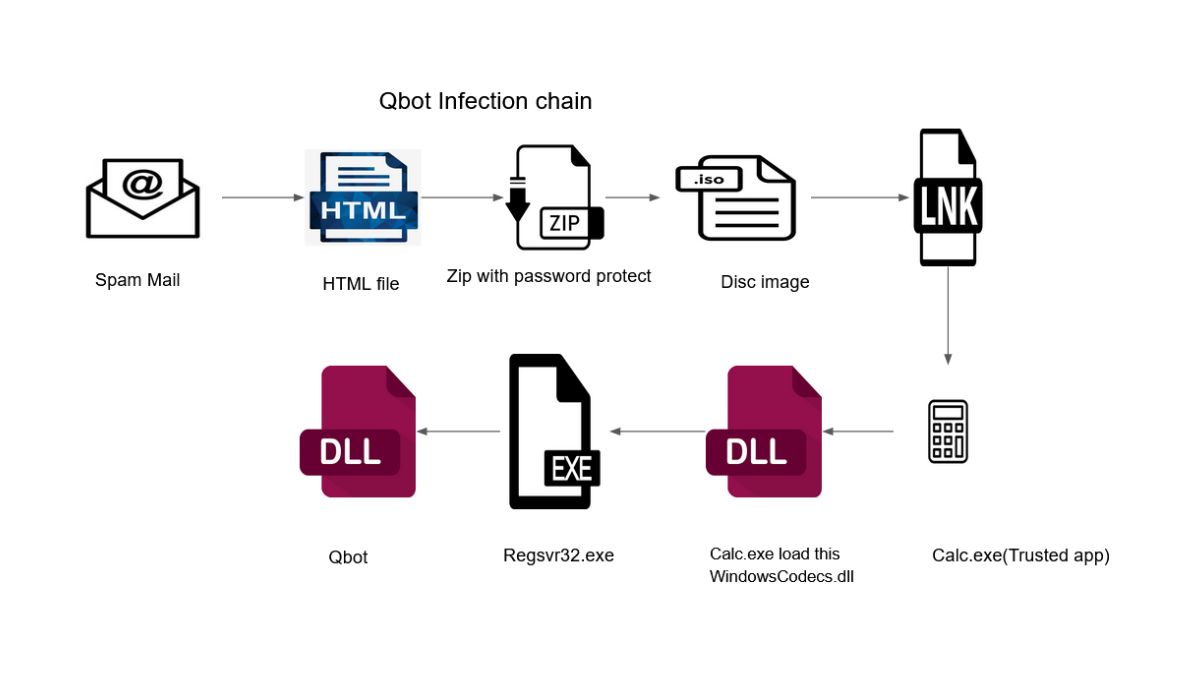
The below figure shows the infection chain of the newer versions of Qbot binary (Figure 1):
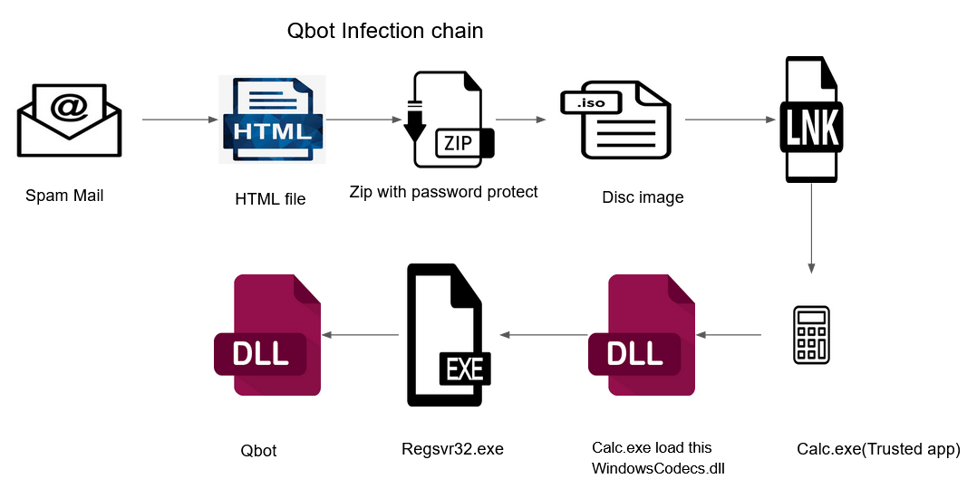
Figure 1 - Infection chain
As we can see in the above diagram, the infection chain for newer binaries includes trusted apps like calc.exe for DLL side-loading.
Upon opening the HTML file which comes via spam email, it drops a password-protected ZIP file named “TXRTN_2636021.zip” into the local system. The below screenshot (Figure 2) shows the HTML page from spam email.

Figure 2 - HTML file
By extracting the ZIP file using the password mentioned in the HTML page, we can get an ISO file. The ISO file contains the following:
- LNK file : TXRTN_8468190 - This is LNK file is the execution trigger point
- WindowsCodecs.dll - Windows file (masqueraded name) for executing malicious payload
- Calc.exe - Legitimate windows file with hidden attribute
- 102755.dll - Qbot DLL with hidden attribute
The below screenshot shows the files inside the ISO file.
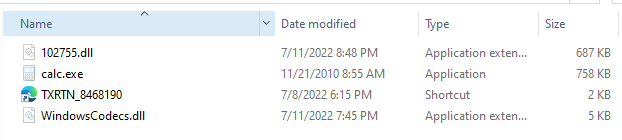
Figure 3 - Inside the ISO file
Upon executing the LNK file, it launches the “Calc.exe”. On execution of “Calc.exe”, it loads the file named “WindowsCodecs.dll” (name masquerading) which contains the malicious code. This creates a new process with malware payload “102755.dll” and the below command line:
- “C:\Windows\Syswow64\regsvr32.exe 102755.dll” (see Figure 4)
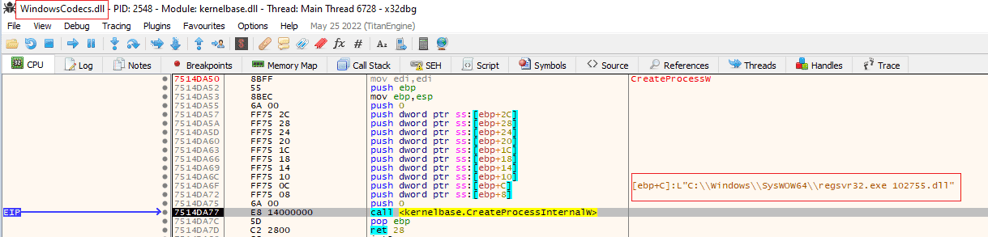
Figure 4 - Regsvr32 execution
The below screenshot shows the process chain of Qbot.

Figure 5 - Process execution flow
This way the malware uses the DLL side-loading technique to execute malicious payloads without being detected—unless you know what you’re looking for.
Technical Analysis
102755.dll
The DLL file (102755.dll) is a x32 bit Delphi compiled binary, which has no export functions.
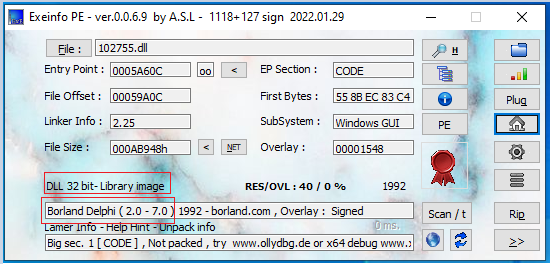
Figure 6 - Initial Qbot payload
Upon execution of the DLL file, it decrypts the XOR encoded payload in memory. The payload is a VC compiled binary. The Dump 1 (see Figure 7) shows the payload along with an API function.
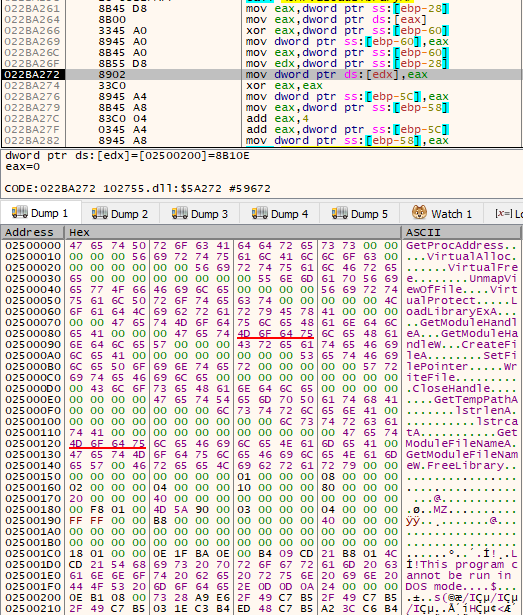 Figure 7 - Decryption loop and the dumped payload binary
Figure 7 - Decryption loop and the dumped payload binary
Qbot Payload
The Qbot payload first checks for the Microsoft Defender emulation folder using GetFileAttributes API. This condition is checked with the string “C:\INTERNAL\__empty”. If the condition is satisfied, the payload gets terminated.
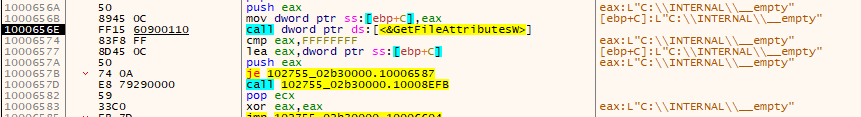
Figure 8 - Emulation check
Next, the payload checks for the environment variable “SELF_TEST_1” to check if the victim is already infected. If the flag is set, it will clear the memory and terminate itself.
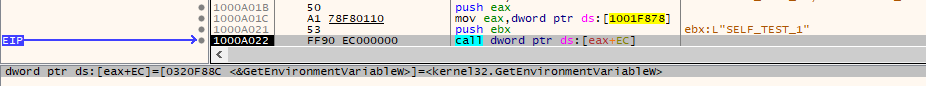
Figure 9 - Self check
If the victim PC is not already infected, the payload binary creates a new thread and starts the execution.
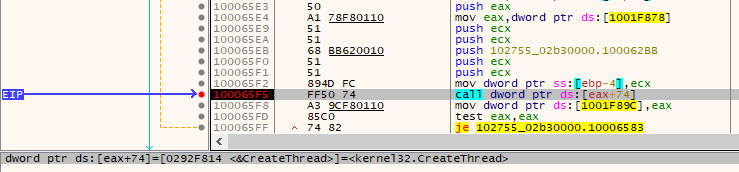
Figure 10 - Thread Creation
The first thread function runs an API hashing function that restructures the new IAT table as follows:.
- Kernel32.dll
- Ntdll.dll
- User32.dll
- Netapi32.dll
- Advapi32.dll
- Shlwapi.dll
- Shell32.dll
- Userenv.dll
- w32_32.dll
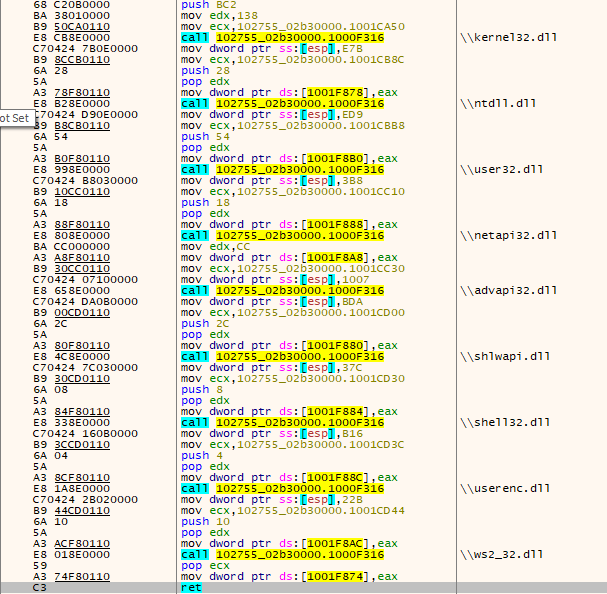 Figure 11 - Restructured IAT table
Figure 11 - Restructured IAT table
The payload also involves the anti-debug check using GetTickCount() API. After the anti debug check, it collects the sensitive system information from the victim PC such as Computer name, GetVolumeInformation, User Account name, Module Name, Type of process, and OS version info.
The payload contains the XOR encoded AV process names in a list. After decoding, the payload checks against the running processes in the system. The payload uses a combination of CreateToolhelp32Snapshot,Process32First and Process32Next APIs.
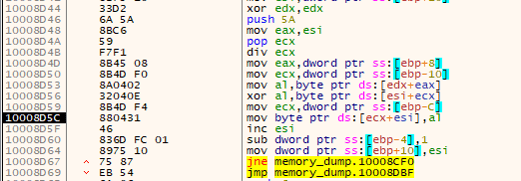
Figure 12 - Decryption loop for AV name check list
Below is the list of process names checked by the payload:
- ccSvcHst.exe
- Avgcsrvx.exe
- Avgsvcx.exe
- avgcsrva.exe
- MsMpEng.exe
- mcshield.exe
- Avp.exe
- kavtray.exe
- Egui.exe
- ekrn.exe
- Bdagent.exe
- Vsserv.exe
- vsservppl.exe
- AvastSvc.exe
- coreServiceShell.exe
- PccNTMon.exe
- NTRTScan.exe
- SAVAdminService.exe
- SavService.exe
- fshoster32.exe
- WRSA.exe
- Vkise.exe
- Isesrv.exe
- cmdagent.exe
- ByteFence.exe
- MBAMService.exe
- mbamgui.exe
- fmon.exe
- Dwengine.exe
- Dwarkdaemon.exe
- dwwatcher.exe
Previously, the Qbot malware tried to inject malicious content in any of the processes from the list below:
- %SystemRoot%\SysWOW64\Explorer.exe
- %SystemRoot%\SysWOW64\OneDriveSetup.exe
- %SystemRoot%\System32\OneDriveSetup.exe
- %SystemRoot%\Explorer.exe
- %SystemRoot%\SysWOW64\mobsync.exe
- %SystemRoot%\System32\mobsync.exe
- %ProgramFiles%\Internet Explorer\iexplorer.exe
- %ProgramFiles(x86)%\Internet Explorer\iexplorer.exe
- %SystemRoot%\SysWOW64\msra.exe
- %SystemRoot%\System32\msra.exe
This time Qbot changes the list of target processes.
- C:\Windows\SysWOW64\wermgr.exe
- C:\Windows\SysWOW64\msra.exe
- C:\Program Files (x86)\Internet Explorer\iexplore.exe
Once the target process is chosen (in our case wermgr.exe), the payload uses a process-hollowing technique to inject into the legitimate target process.
Conclusion: Detect & Stop Qbot Attacks
Our research on Qbot showed the advancements in its attack chain. Enterprises must have tight security controls and multi-layered visibility and security solutions to identify and detect malware like Qbot. Uptycs’ EDR correlation engine detected the Qbot activity by correlating generic behavioral rules and YARA process scanning capabilities.
Uptycs EDR Detection
Uptycs endpoints detection and response (EDR)—armed with YARA process scanning, advanced detections, and the ability to correlate Registry Events, Process File Events, Process Events and API Events—successfully detects different types of tactics carried out by Qbot.
Additionally, Uptycs EDR contextual detection provides important details about the identified malware. Users can navigate to the toolkit data section in the detection alert and click on the name to find out the behavior as shown below (Figures 13 & 14).
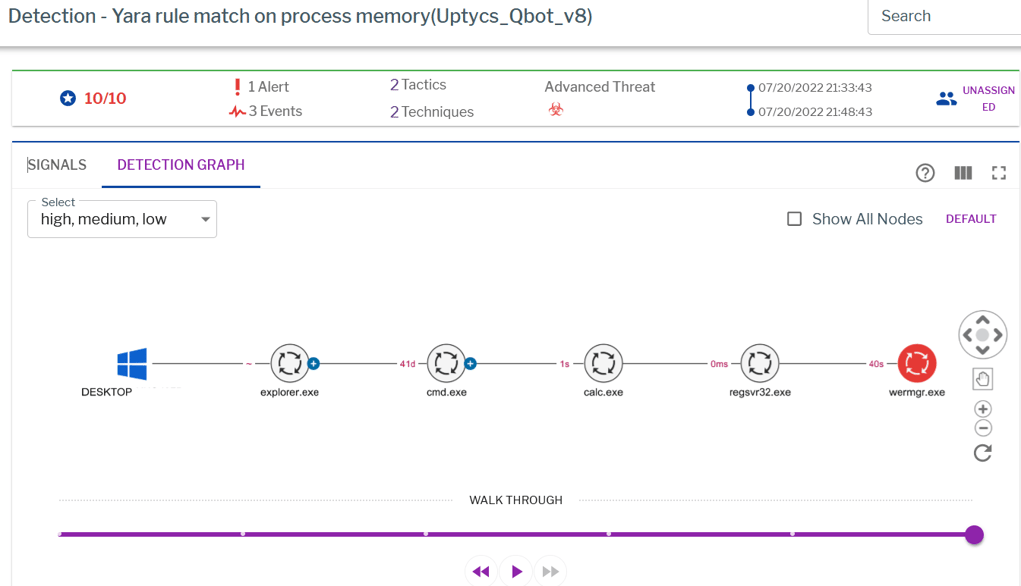
Figure 13 - Uptycs EDR detection
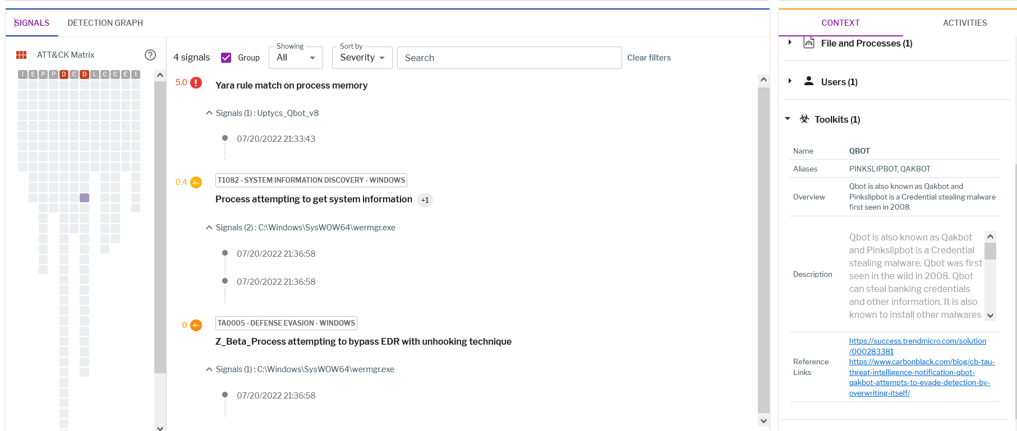
Figure 14 - Uptycs EDR detection
IOCs
|
File Name |
MD5 |
|
HTML |
5cb20a0bfc5e3e2ae8398b1840adf7ae |
|
TXRTN_2636021.zip |
a61219832554d574a0b5e17c0e82f2ef |
|
TXRTN_2636021.iso |
17be394b5cd6d74c3709e39f02cd1aa3 |
|
TXRTN_2636021.lnk |
eea824215afd2936b4b9c428558a11ed |
|
calc.exe |
60b7c0fead45f2066e5b805a91f4f0fc |
|
WindowsCodecs.dll |
491e9489c9e11f8b9d3d77239559a194 |
|
102755.dll |
217f7ddedf40dbe456ce13bf01bd74fc |
To Lean More About the Latest Threat Research Conducted by the Uptycs Team, Check out Our Most Recent Threat Bulletin.