Uptycs' threat intelligence team collects over a million indicators every week to provide the latest threat data. All of this data is downloaded from more than 40 publicly available sources which we then put into eight categories including:
- Malware: All of the domains or IPs that are part of malware activity like command and control or malware downloads.
- Phishing: All of the domains or IPs that are part of credential theft/phishing activities.
- Not recommended website: All of the domains or IPs that can potentially compromise the endpoint systems indirectly like pirated software websites or low reputation websites.
- Attack: All of the IPs that are part of some attack related activities like ssh bruteforce, DDoS etc.
- Coinminer: All of the domains or IPs that are part of crypto currency mining related services.
- Anonymizer: All of the domains or IPs that are associated with anonymization services.
- Nrd: All of the domains that are newly registered.
- Dga: All of the domains generated using a domain generation algorithm.
The largest amount of data we get is from the NRD (Newly registered domain) category. The graph below shows the data we received on a daily basis spanning a week in early March.
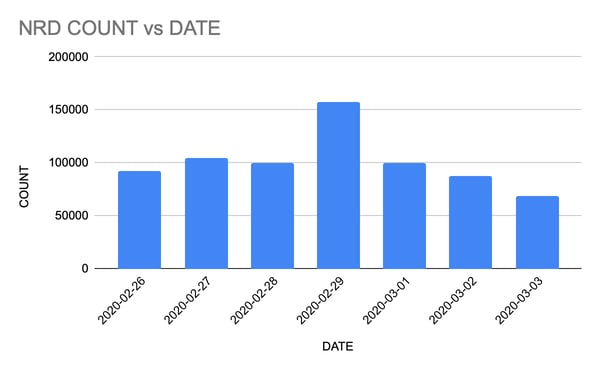
One of the drawbacks of this data is the volume of alerts it produces for customers in the newly registered domain category, when they do not block them with some network control. After analyzing the malicious events and other domain parameters, we keep newly registered domains for a month. After a month we expire the domains from our database. The real question that arises from this vetting process is: “Is it worth looking at the newly registered domains?
So, Is It Worth Monitoring Newly Registered Domains?
Before answering the question let's take a look at the following graph that shows the amount of NRD’s that gets converted into a malicious domain on a daily basis, meaning we first received these domains as NRD, and some time later we received the same domains in the malware category.
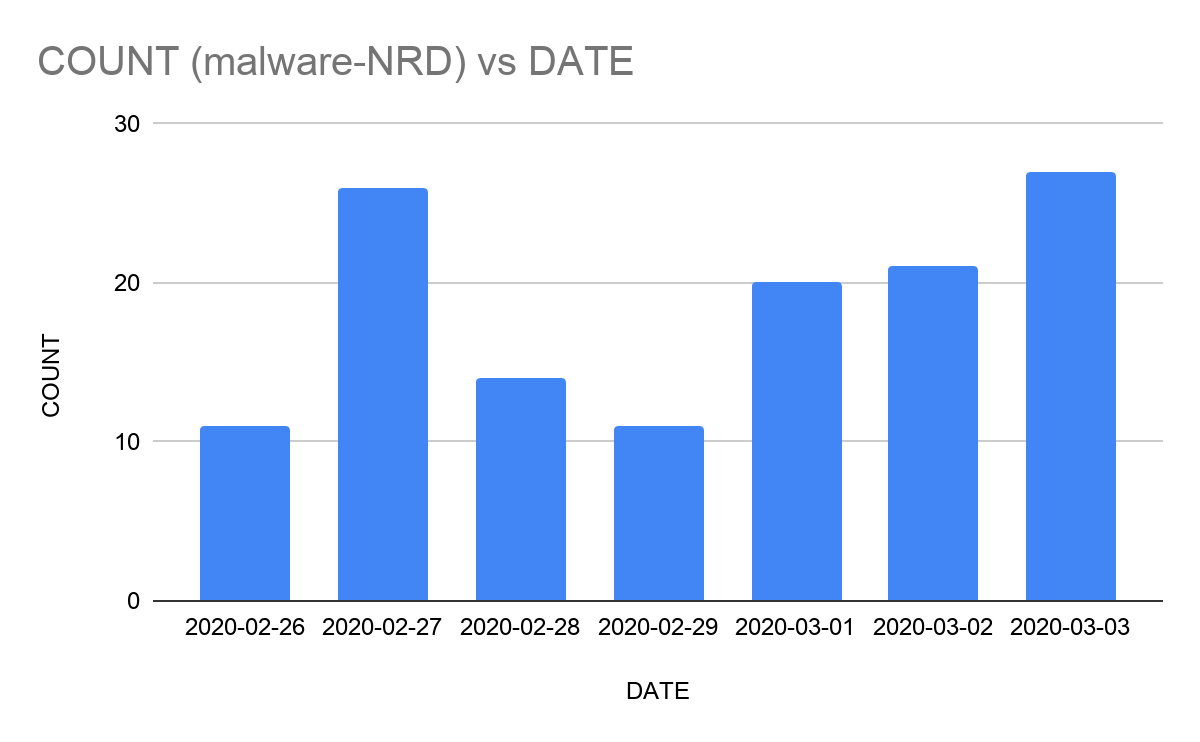
As we can see in the graph that on an average 20 NRD domains get converted into the malware category on a daily basis. This number may seem to be low in comparison to the NRD domains but if we take a look at the number of unique malware domains received on a daily basis as shown in the following graph then this number becomes significant.
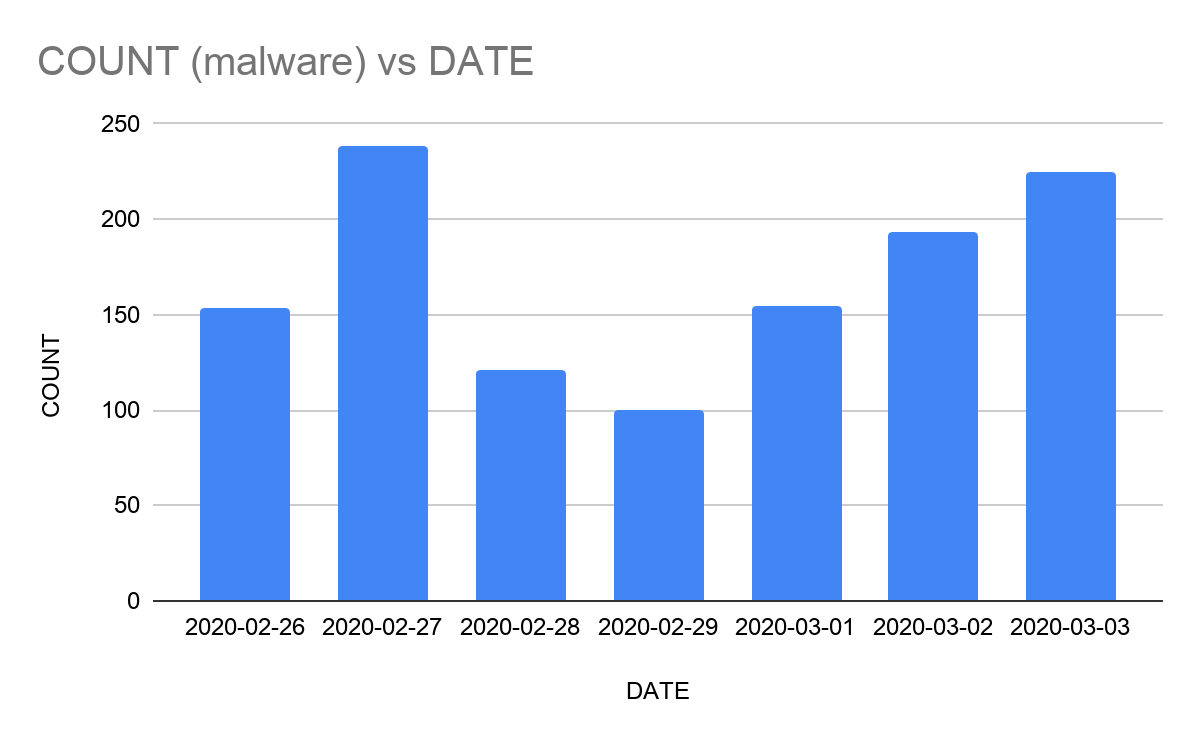
On an average we received 169 unique malware domains and IPs out of which 11.83% ((20/169)*100) are from the NRD category. It means that more than 10% of malware domains and IPs are contained in the NRD category for a period of time. Essentially, malware often uses new domains rather than piggybacking on existing ones. If the numbers are not enough to convince the importance of NRD blocklist then let's take an example of a high profile case.
The Wipro Breach:
On 15th April 2019, Brian Krebs published an article about the breach at Wipro. Later on 17th April 2019, he published another article with IOCs. At that time we quickly looked into our threat intelligence platform and confirmed that we had coverage for some of the domains through NRD. Based on the IOCs published in the article following domain were NRD during the attack time frame.
xsecuremail[.]com:
| Indicator | Category | Added_On |
| xsecuremail.com | nrd | 2019-03-07 |
| xsecuremail.com | malware | 2019-04-18 |
wipro365[.]com:
| Indicator | Category | Added_On |
| wipro365.com | nrd | 2019-03-25 |
| wipro365.com | malware | 2019-04-18 |
encrypted-message[.]cloud:
| Indicator | Category | Added_On |
| encrypted-message.cloud | nrd | 2019-03-22 |
| encrypted-message.cloud | malware | 2019-04-18 |
We classified all of the domains as malware on 18th April 2019 after the public disclosure of IOCs. But as we can see these domains were registered on 7th, 22nd and 25th March 2019 respectively and were classified as NRD in our threat intelligence portal before the public disclosure. This clearly indicates that the attackers registered the new domains at the time of attack to carry out the malicious activity.
Coronavirus/Covid-19:
WHO declared the coronavirus a pandemic. This deadly virus is currently threatening lives and businesses across the globe. It appears as though, even as humanity grapples with these difficult times, malicious actors are busy trying to exploit the situation for their benefit. People registered more than 10,000 domains related to coronavirus in the last two and a half months. Of course not all of the domains are malicious but a large number of domains are getting registered on a daily basis as shown in the following graph.
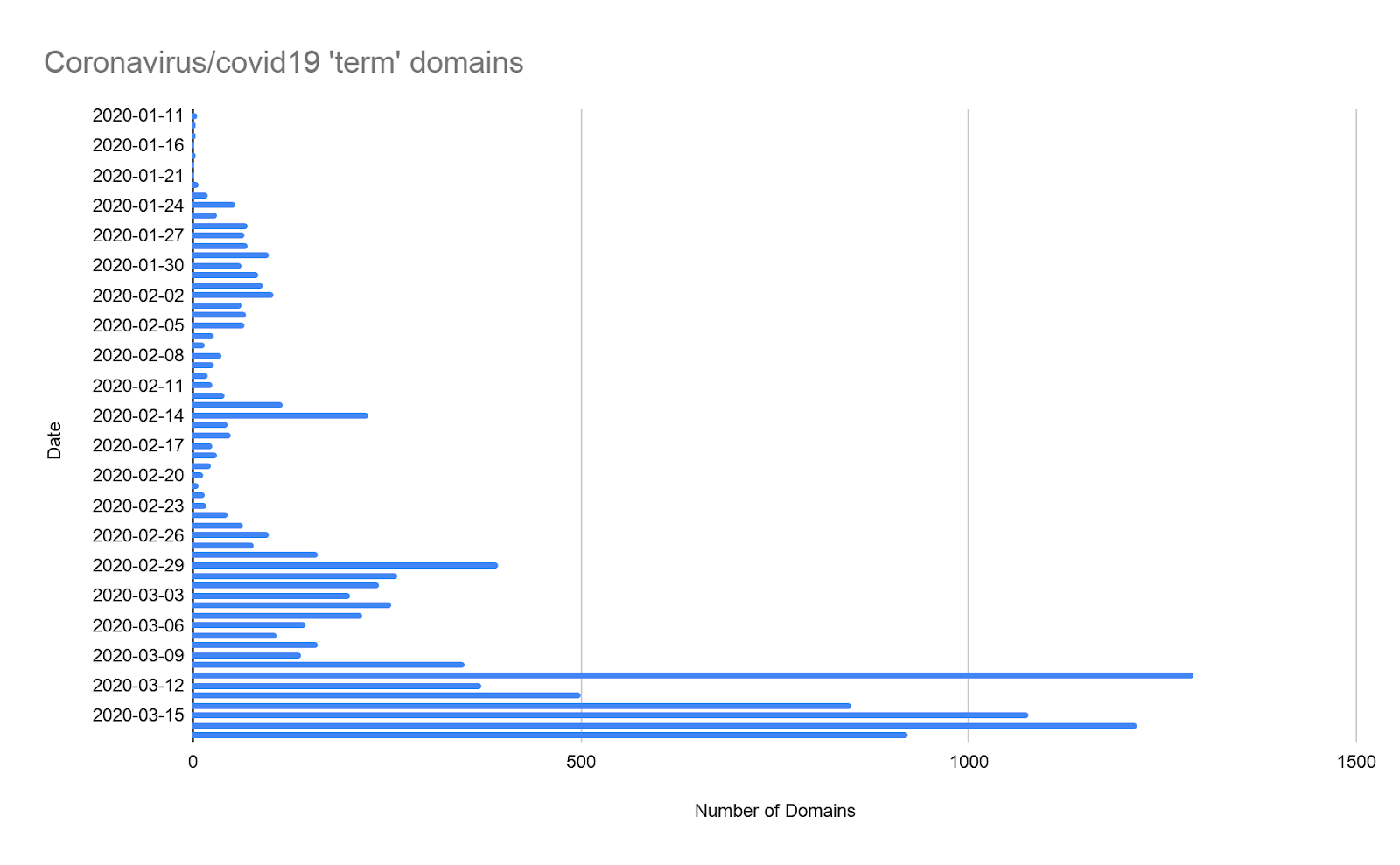
This is not normal. Many of these registered domains will eventually deliver malware and infect innocent users.
Newly Registered Domains Should Be Considered Suspicious
Newly registered domains (NRD) can’t be classified as malicious by default, but can be considered suspicious. At Uptycs, we highly recommend blocking queries to newly registered domains, for a period of at least 15 days, which is the amount of time it usually takes for malicious domains to be either withdrawn, or to be classified into one of the other, more precise categories.



%20On-Demand%20(1).png?width=600&name=YARA-osquery%20Webinar%20(Banner)%20On-Demand%20(1).png)



