There’s a new vulnerability in the Java source code library that’s reminiscent of Log4Shell. The vulnerability, dubbed Text4Shell, is Apache Commons Text versions 1.5 through 1.9, and can allow arbitrary code execution or establishment of communications with external servers. The Text4Shell vulnerability (CVE-2022-42889) has a CVSS of 9.8, and the recommended remediation is to upgrade to Apache Commons Text 1.10.0.
The problem—as with Log4Shell—is figuring out which systems might have the vulnerable software and then prioritizing remediation. That’s where osquery and Uptycs can help.
Java software is on everything from backend servers to multifunction printers. Because of obscure software dependencies, sometimes application owners are not aware that they have the Apache Commons Text library in their applications. You need to answer the questions: “Do we have a vulnerable version of Apache Commons Text in our software supply chain?” and “Does this vulnerable library exist in any of our third-party applications or hardware?”
Uptycs Is Here to Help!
As it happens, we recently released an extension to osquery that helps you detect Java vulnerabilities. The extension adds a java_packages table that allows you to dig into details like software versions.
We have the queries that will identify systems vulnerable to Text4Shell at the bottom of this blog post. These queries will give you an inventory of all your Text4Shell-vulnerable jar files, with location and versions. Reminder, the java_packages table is supported in Uptycs osquery. The broader osquery community can use the extension we open sourced.
Query For Apache Commons Text Jar In Non Containerized (Host) Environments
WITH procs AS
(
SELECT pid, name, cmdline FROM processes WHERE is_container_process = 0
),
jars AS
(
SELECT DISTINCT o.pid, o.path, p.name, p.cmdline
FROM process_open_files o JOIN procs p USING (pid)
WHERE o.system_type = 'host' AND o.path LIKE '%._ar' AND o.path NOT LIKE '%/jre/lib/%'
)
SELECT j.*, p.artifact_id, p.group_id, p.version, p.filename, p.description, p.size, p.directory,
p.path AS embedded_path, p.system_id FROM java_packages p JOIN jars j
WHERE p.file = j.path AND system_type = 'host' AND ( length(p.version) < 4 or p.version =
'1.0-beta-1' ) and p.filename like '%commons-text-%'
Query For Apache Commons Text Jar In Containerized Environments (Docker)
WITH jars AS
(
SELECT DISTINCT path AS file, system_id, system_type FROM process_open_files
WHERE system_type = 'docker_container' AND path not like '%/jre/lib/%' AND path LIKE
'%._ar'
),
open AS
(
SELECT d.name, d.image, d.image_id, j.* FROM docker_containers d, jars j WHERE d.id =
j.system_id
)
SELECT j.file AS path, j.system_type, j.system_id, j.image, j.image_id, p.artifact_id,
p.group_id, p.version, p.filename, p.description, p.size, p.directory, p.path AS embedded_path
FROM java_packages p JOIN open j USING (file, system_type, system_id)
WHERE ( length(p.version) < 4 or p.version = '1.0-beta-1' ) and p.filename like
'%commons-text-%';
Query for Apache Commons Text Jar In Containerized Environments (Containerd)
WITH jars AS
(
SELECT DISTINCT path AS file, system_id, system_type FROM process_open_files
WHERE path not like '%/jre/lib/%' AND path LIKE '%._ar' and system_type =
'containerd_container' AND system_id NOT IN ( SELECT id FROM docker_containers GROUP
BY 1 )
),
open AS
(
SELECT d.image, j.* FROM containerd_containers d, jars j WHERE d.id = j.system_id
)
SELECT j.file AS path, j.system_type, j.system_id, j.image, p.artifact_id, p.group_id, p.version,
p.filename, p.description, p.size, p.directory, p.path AS embedded_path
FROM java_packages p JOIN open j USING (file, system_type, system_id)
WHERE ( length(p.version) < 4 or p.version = '1.0-beta-1' ) and p.filename like '%commons-text-%';
Addendum For Uptycs Customers
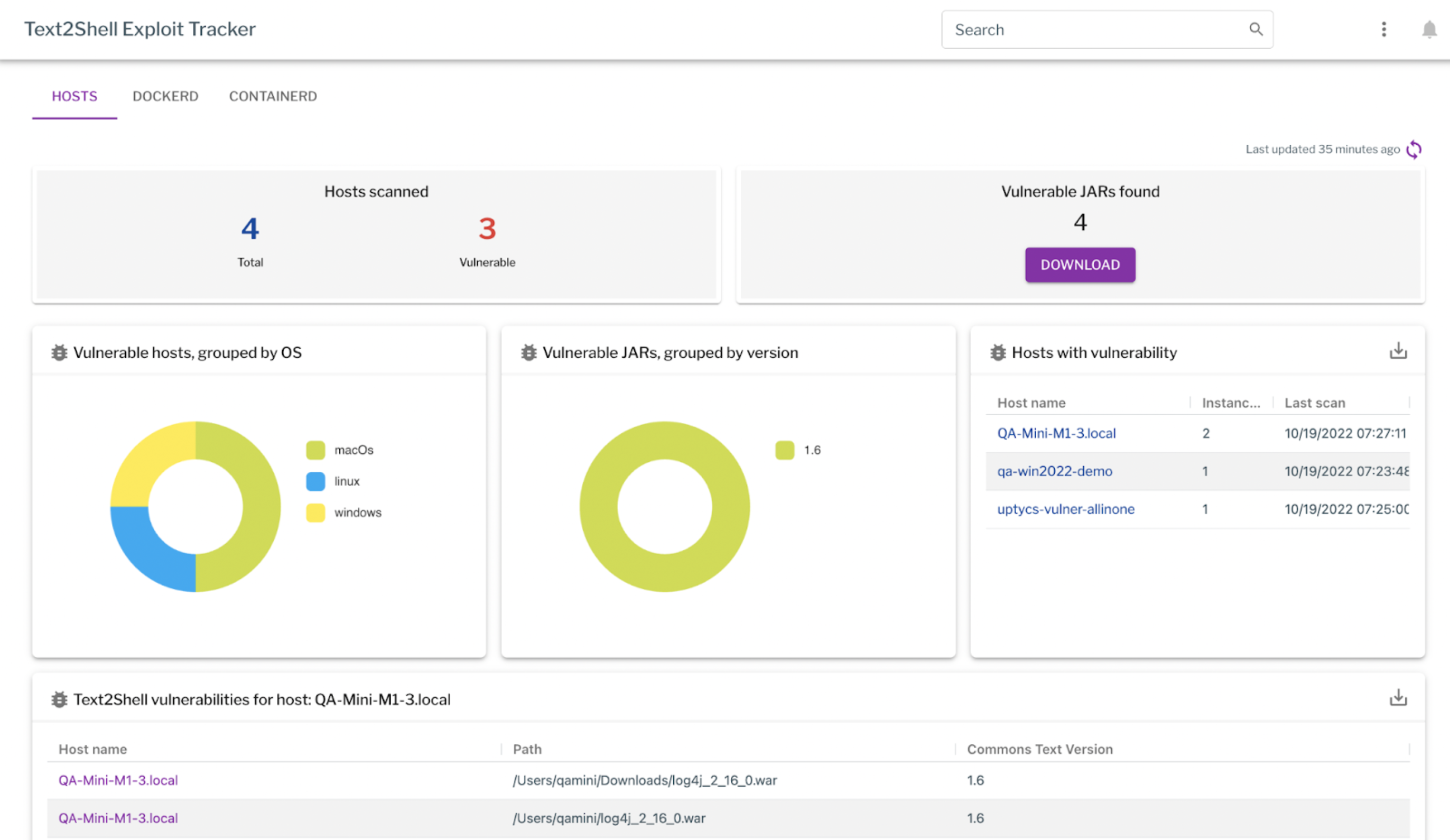
Uptycs has added the Text4Shell vulnerability detection to the existing exploit dashboards. The Uptycs Customer Success team will be in contact with you to enable the collection of vulnerable jars. Once enabled, the vulnerable jars will be visible in the dashboard. The details can be downloaded from the dashboard.
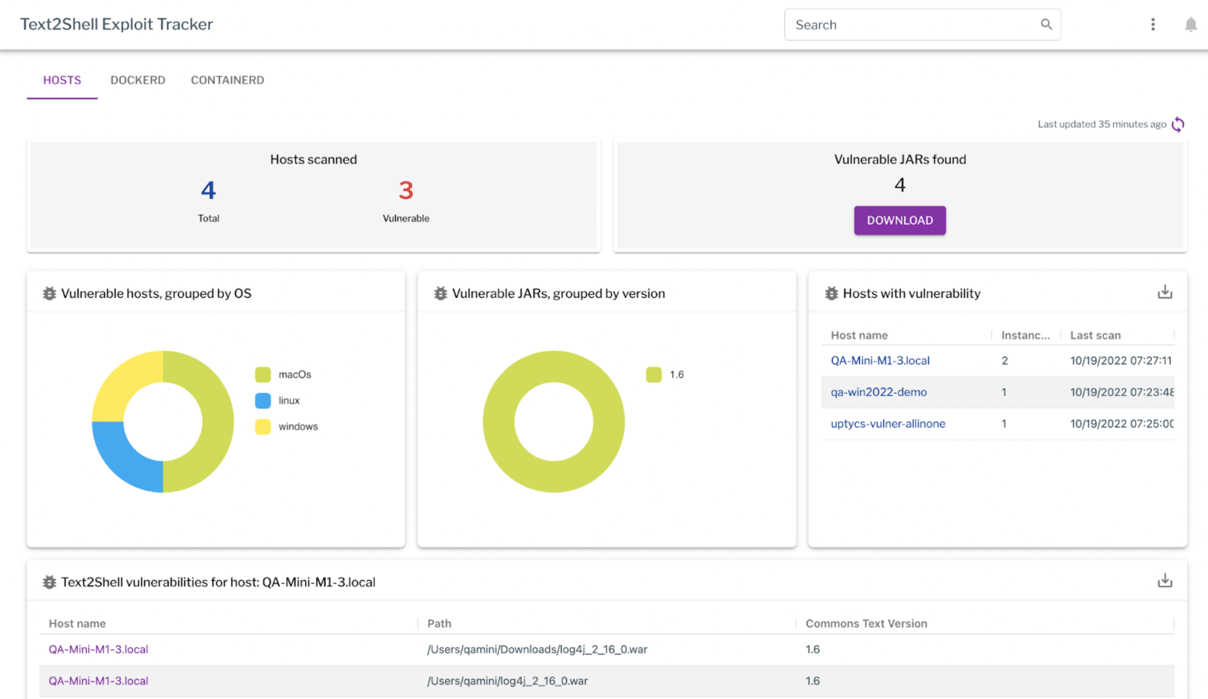
Figure 1: The exploit tracker showing vulnerable hosts
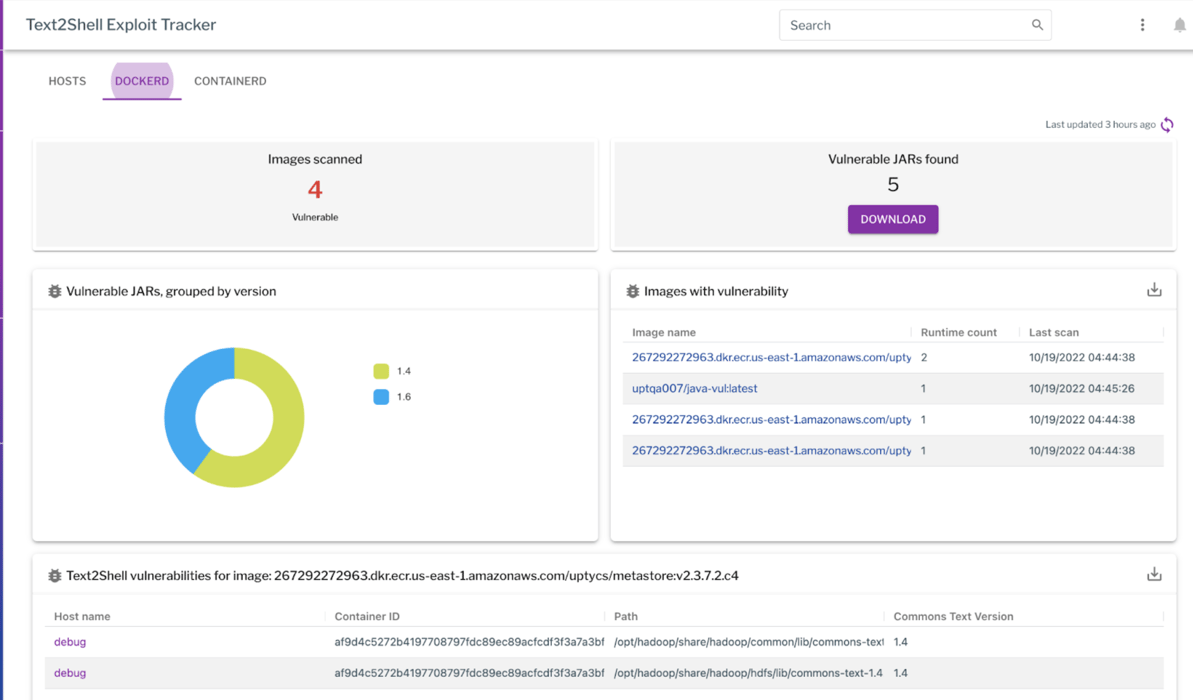
Figure 2: The exploit tracker showing vulnerable Docker containers