Research By: Karthickkumar K
The Uptycs Threat research team recently noticed a new Agent Tesla malware attack campaign. In the campaign, we observed that the threat actors are now trying to drop Agent Tesla malware via WSHRAT malware. WSHRAT is VBScript/Javascriptbased malware that uses multi-stage infection for the purpose evading AV/EDR detection. This combination of WSHRAT dropping an Agent Tesla payload was observed for the first time.
WSHRAT is a remote access trojan (RAT) capable of keylogging and stealing sensitive PC info like OS information, computer name, username, running process info, etc. from the victim PC. The RAT code is publicly available here. The Agent Tesla malware, on the other hand, has the ability to steal browser credentials and other sensitive information like VPN client credentials, FTP client credentials, etc. from the victim system. The WSHRAT dropping Agent Tesla was initially reported by 0xToxin.
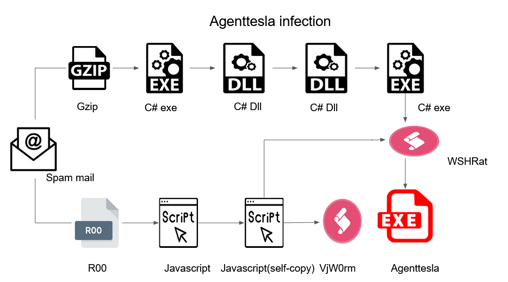
In this campaign, the initial vector used by the threat actors was a spam email which had two archives attached, a GZ file and an R00 file. Figure 1 shows the infection flow.
Part 1: GZip Attachment
As mentioned above, the spam mail contains two types of archive files. The GZ archive contains a C#-compiled 32-bit executable binary file (Copia de pago.exe). Upon executing the binary, it drops two files in the Roaming folder:
- MGosm.vbs - WSHRAT script file
- nicon4.0origin.exe - C# executable Agent Tesla
Figure 2 shows the execution flow of the binary.
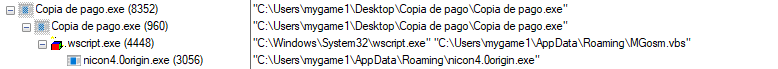
Figure 2:Process execution flow of GZip attachment
Stage 1:
The binary Copia de pago.exe uses the Steganography method to embed PE binary in an image file to evade AV/EDR. which gets decrypted during its execution. The decrypted data in virtual memory address (0xD000) contains a new DLL binary.
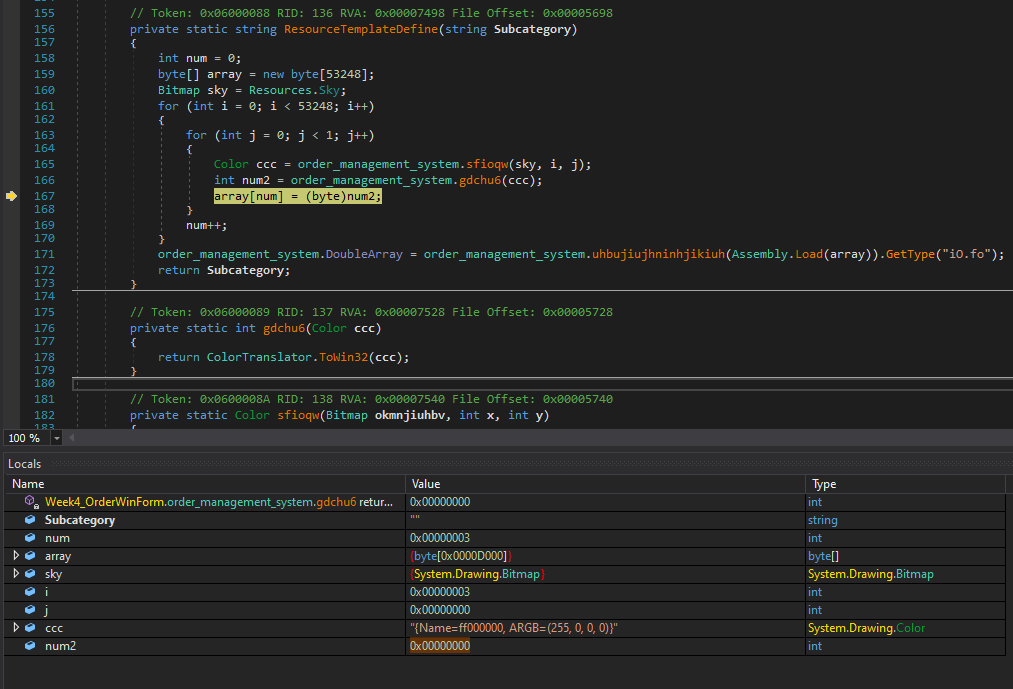
Figure 3: DLL decrypted from Copia de pago.exe resource
The Copia de pago.exe loads the DLL in memory (see Figure 4).
![]()
Figure 4: Copia de pago.exe loads decrypted DLL in memory
Stage 2:
The newly loaded DLL binary file contains base64-encoded gzip compressed data (see Figure 5). The compressed data is just another DLL binary which gets loaded in memory during stage 2’s DLL execution.
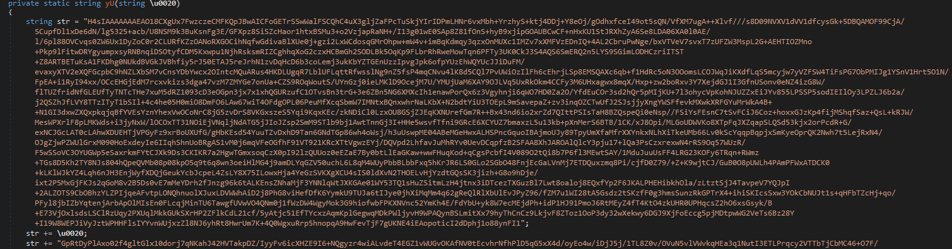
Figure 5: base64-encoded gzip compressed data
Stage 3:
The DLL binary file decrypted in stage 2 contains XOR-encoded data. The decoded content is an exe file which drops the WSHRAT malware.
Stage 4: WSHRAT Malware
The decoded exe (in stage 3) contains base64-encoded WSHRAT which gets dropped in %appdata%\Roaming\ folder.
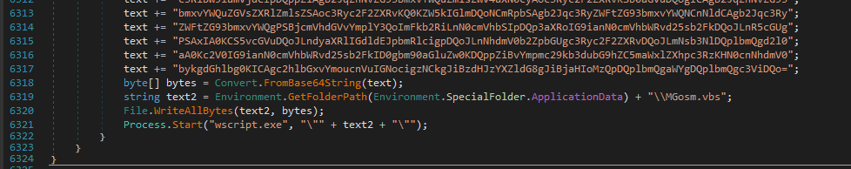
Figure 6: base64-encoded WSHRAT
The WSHRAT malware gathers:
- Computername
- Username
- OS information
- Country details
- Installed antivirus software details
- Install/Uninstall software
Along with these, the malware also creates auto startup entry:
HKCU\<id>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MGosm: "wscript.exe //B "C:\Users\mygame1\AppData\Roaming\MGosm.vbs""
This RAT contains a list of commands which could be used by the threat actor remotely:
|
Command |
Action in victim machine |
|
disconnect |
Quite wscript from execution |
|
reboot |
System restart |
|
shutdown |
System shutdown |
|
execute |
Execute application/payload |
|
install-sdk |
Install software development kit |
|
remove-sdk |
Remove software development kit |
|
passgrabber |
Retrieve password |
|
get-pass-offline |
Retrieve password from installed browser |
|
update |
Malware script file |
|
uninstall |
Uninstall application |
|
up-n-exec |
Download |
|
bring-log |
Upload log to attacker server |
|
down-n-exec |
Sitedownloader |
|
filemanager |
Monitoring through fm-plugin.exe |
|
rd-plugin.exe |
Monitoring through rd-plugin.exe |
|
h-browser |
Monitoring though hb-plugin.exe |
|
rev-proxy |
Reverseproxy |
|
exit-proxy |
Kill reverseproxy |
|
keylogger |
Monitoring though kl-plugin.exe |
|
offline-keylogger |
Monitoring though kl-plugin.exe |
|
browse-logs |
Browser activity |
|
cmd-shell |
Shell command |
|
get-processes |
Enumerate running process |
|
disable-uac |
Disable UAC |
|
check-eligible |
Updated |
|
rev-rdp |
Reverserdp |
|
uvnc |
Remote application |
|
force-eligible |
Forcefully updated |
|
elevate |
Execute script files |
|
if-elevate |
Updated |
|
kill-process |
Exit process |
|
sleep |
Sleep |
The payloads inside the vbs file (WSHRAT) are base64-encoded, gzip-compressed data.
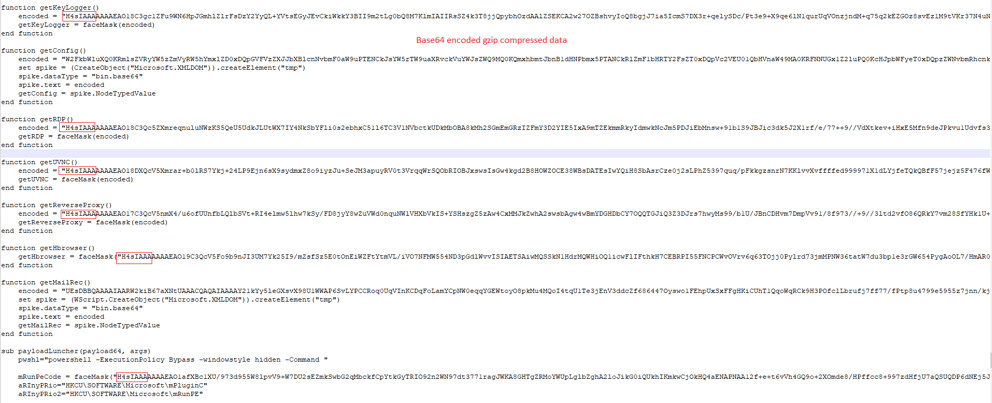
Figure 7: Payloads inside are base64-encoded, gzip-compressed data
As we can see in Figure 8, along with the payloads (see Figure 7) the vbs file (WSHRAT) contains base64-encoded Agent Tesla payload. The Agent Tesla malware binary file gets dropped inside %appdata%\Roaming folder.
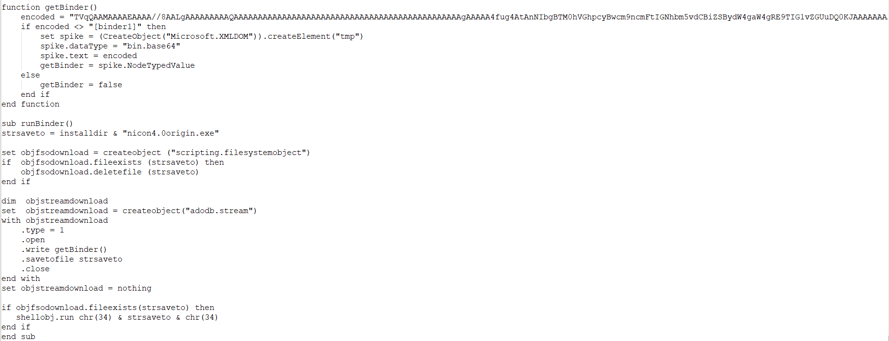
Figure 8: base64-encoded Agent Tesla
Part 2: R00 Attachment
The R00 archive contains a JavaScript file which while executing drops three files in the Roaming folder:
- Recibo de pago.js - Self copy file
- dohKlqYtRl.js - Vjw0rm
- Nicon4.0origin.exe - Agent Tesla
The execution flow of the R00 is shown in Figure 9.
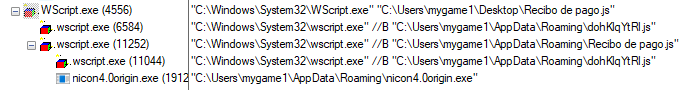
Figure 9: Process execution flow of R00 attachment
The Recibo de pago.js file contains the base64-encoded Vjw0rm and WSHRAT (see Figure 10), While the JavaScript file drops the Vjw0rm script in the Roaming folder. Alongside dropping the Vjw0rm, the JavaScript file also runs WSHRAT binary in memory.

Figure 10: Decoded Recibo de pago.js
Later, the WSHRAT drops Agent Tesla binary in the Roaming folder and runs it (see Figure 8).
Conclusion: Detect & Block Agent Tesla Attacks
Our research on Agent Tesla showed the advancements in its attack chain. Enterprises must have tight security controls and multi-layered visibility and security solutions to identify and detect malware like Agent Tesla. Uptycs’ EDR correlation engine detected the Agent Tesla activity by correlating generic behavioral rules and YARA process scanning capabilities.
Uptycs EDR Detection
Uptycs EDR—armed with YARA process scanning, advanced detections, and the ability to correlate Registry Events, Process File Events, Process Events and API Events—successfully detects different types of tactics carried out by Agent Tesla.
Additionally, Uptycs EDR contextual detection provides important details about the identified malware. Users can navigate to the toolkit data section in the detection alert and click on the name to find out the behavior as shown below (Figures 11,12,13, & 14).
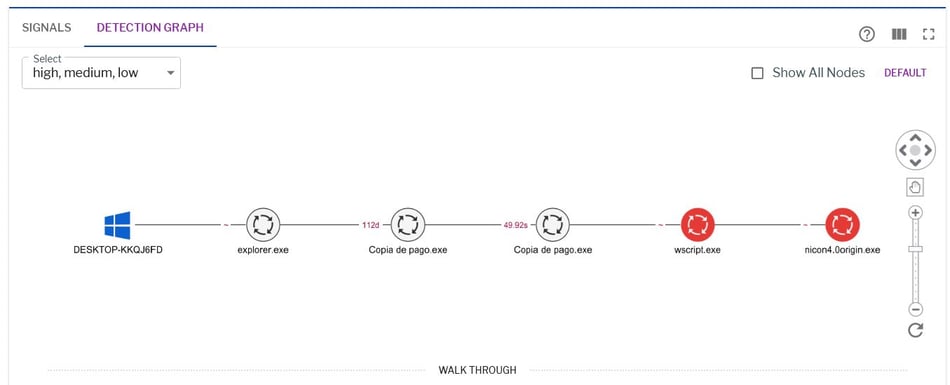
Figure 11: A process tree showing the execution of files inside the gzip attachment in Uptycs EDR
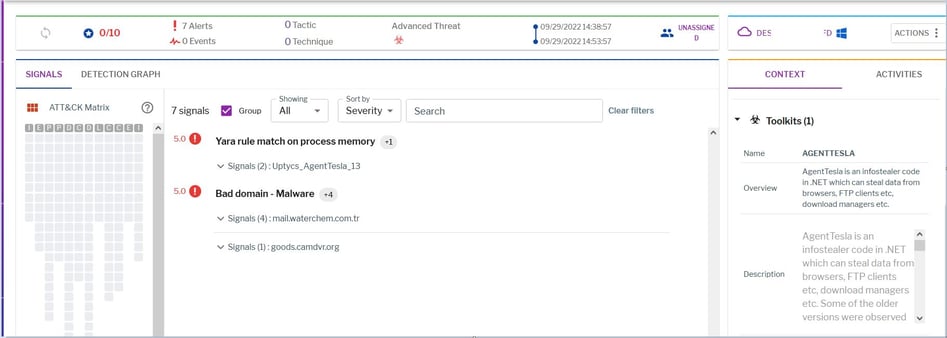
Figure 12: Uptycs EDR detection of the gzip attachment
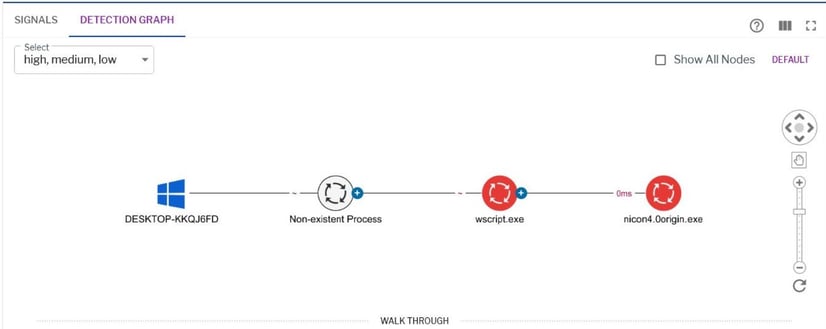
Figure 13: A process tree showing the execution of files inside the R00 attachment in Uptycs EDR
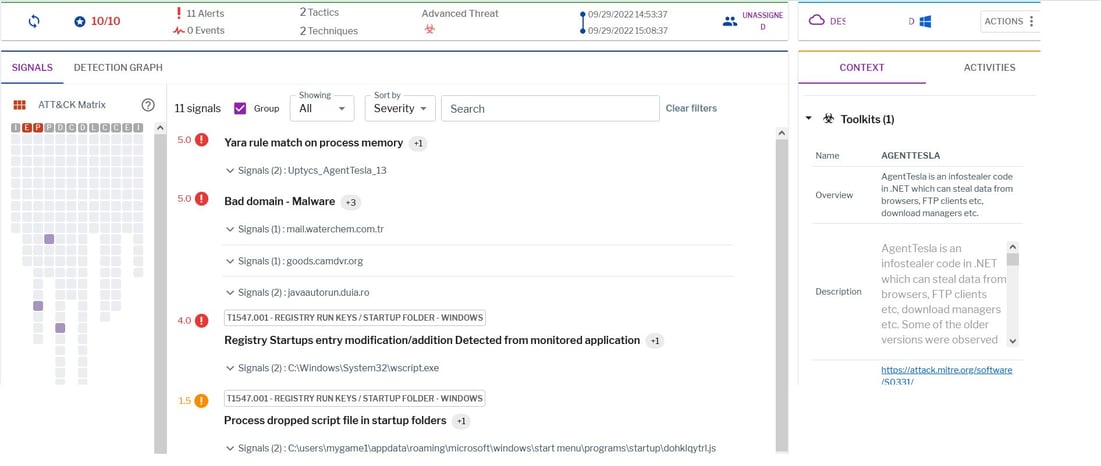
Figure 14: Uptycs EDR detection of the R00 attachment
IOCS
GZip Attachment:
|
File name |
Md5 hash |
|
Copia de pago.gz |
3915b18cb04787f2273b56f15ba2c164 |
|
Copia de pago.exe/stage 1 |
6d231b98f7bc3098fd9797c0e1d6744f |
|
stage 2 |
9ce9b744dcd250e04ddd2a08e6b40c37 |
|
stage 3 |
7d0626010ba6a5408a5844be37fc51b0 |
|
stage 4 |
75f9dd638c7c601e48d2f3ecada80e27 |
|
MGosm.vbs/stage 5 |
42bc41987e5e104aafa3570d52cd4b0c |
|
nicon4.0origin.exe/stage 6 |
993c330b4f0e94b46664f2f0bf3309c2 |
R00 Attachment:
|
File name |
Md5 hash |
|
.Roo |
ac46457e480306c3be0df227c2b329a2 |
|
Recibo de pago.js |
7d685c3a21c226778a183ced19fcac28 |
|
dohKlqYtRl.js |
82334b4f98af5abc62a6fcfe554fc0d7 |
|
Vjw0rm |
bd992a0055c8f5b4ee92fedac8fa39cd |
|
nicon4.0origin.exe |
993c330b4f0e94b46664f2f0bf3309c2 |
To learn more about the latest threat research conducted by the Uptycs Team, check out our most recent threat bulletin below.