I recently had the privilege of participating in a SANS panel discussion about MITRE D3FEND and the audience contributed many interesting ideas, which I’ll share below. SANS analyst Matt Bromiley hosted the discussion and led off with an overview of MITRE ATT&CKⓇ and the newer D3FEND matrix.
What Is MITRE D3FEND?
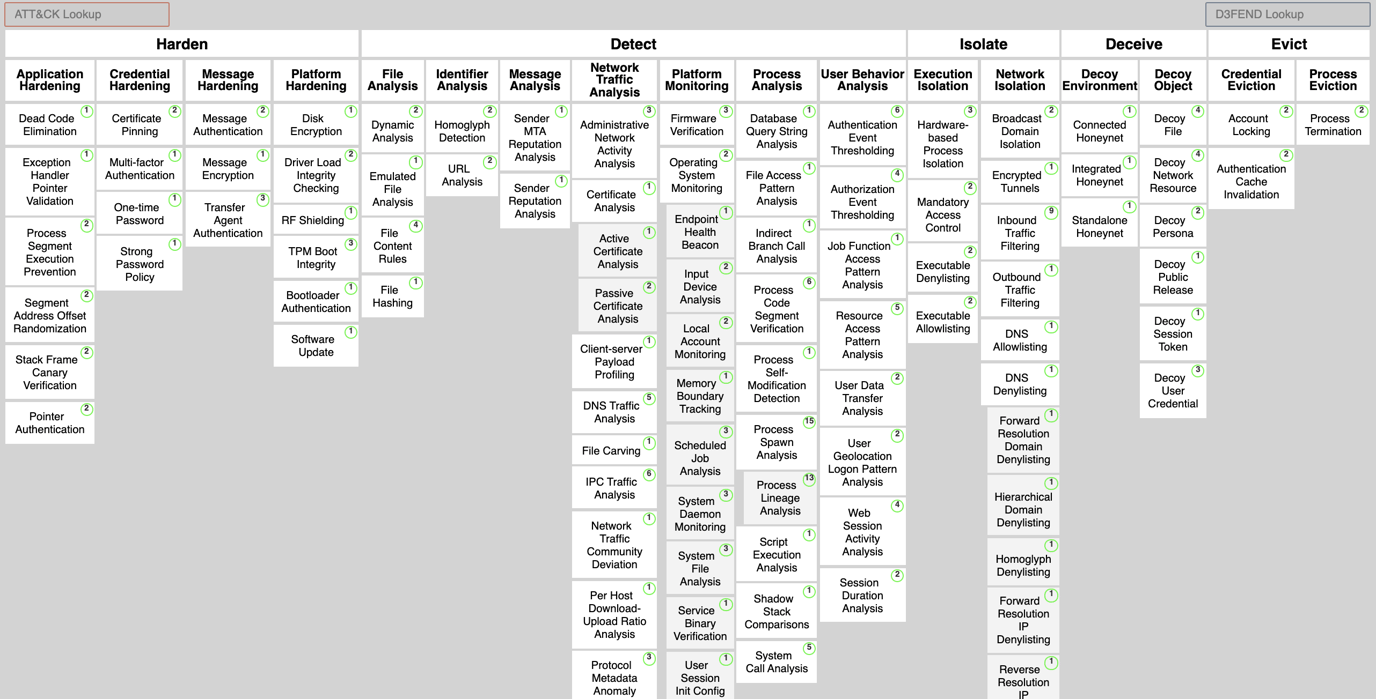
MITRE D3FEND is a new matrix designed to help Blue Teams prioritize and implement countermeasures for attacker techniques described in the ATT&CK matrix. MITRE describes D3FEND as a knowledge graph and admits that this first, early version is not complete and may have inconsistencies. However, the framework is solid conceptually and will serve as a scaffold for the contributions of the cybersecurity community. There’s really nothing else like it out there.
A side note: D3FEND was launched last summer with funding from the U.S. National Security Agency (NSA). The NSA’s involvement is significant, I think. Their charter not only includes collecting foreign intelligence (often through hacking), but also protecting U.S. entities against the efforts of their nation-state counterparts. With D3FEND, the NSA is helping American firms improve their cybersecurity defensive technical capabilities (although it’s an open framework and will help everyone regardless of nationality). So if they think it was important enough to invest in, then I think it’s worth paying attention to.
D3FEND is in the early stages, and MITRE is soliciting feedback and contributions from the community. In a year’s time, I think we can expect to see forward-thinking organizations (both end-users and vendors) starting to develop best practices for using D3FEND.
The MITRE D3FEND matrix, a knowledge graph of cybersecurity countermeasures
Key Insights From the Webinar Q&A
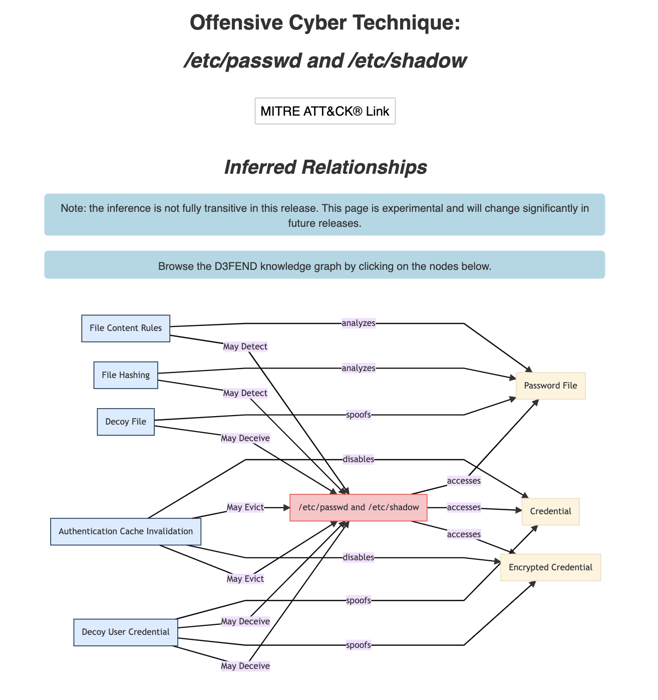
In the SANS webinar, Bromiley did an excellent job describing how D3FEND allows Blue Teamers to map the appropriate defensive countermeasures against ATT&CK techniques. If you are a retail organization and need to defend yourself against the FIN7 criminal group, MITRE provides you with the ATT&CK tactics and techniques that the community has observed that particular group using. You can then map those techniques against the countermeasures prescribed by D3FEND.
Example of mapping D3FEND countermeasures to offensive ATT&CK techniques
During the audience Q&A time, we had many interesting points come up. Several people asked how to use ATT&CK and D3FEND to communicate with upper management, and another asked about how it would apply to the Log4j response. The two questions are related, as ATT&CK and D3FEND can be used to show management how your team is improving your security posture, especially tailored to the specific threats targeting your business.
In regard to Log4j, D3FEND includes a Hardening tactic with a Software Update technique—inventorying your software and patching your systems may not be as sexy as threat detection, but is equally if not more important, as Log4j has shown us.
I thought one audience member had an interesting suggestion: Vendors could include recommendations or SOAR playbooks to help security operations teams speed up remediation. Many detection and response vendors map their detections to ATT&CK (including Uptycs), and this helps junior analysts understand the implications of an alert. But what if vendors went one step further to incorporate recommended D3FEND countermeasures for the same detections? Those could be put into a periodic report for IT or Network teams to remediate. The possibilities are exciting! But it wouldn’t have even been possible without a common vocabulary for countermeasures, which is what D3FEND is here for.
Our customers have been leveraging ATT&CK for years within the Uptycs Platform—we’ve built out hundreds of detections to cover the techniques and sub-techniques described in the framework. Check out this blog post on how and why we’ve embraced the ATT&CK lifestyle!
This was an exciting discussion to be a part of!
Click below if you'd like to watch the entire panel session on-demand.