Meet Red Team Curly and Blue Team Linus. Hijinx will ensue.
Ever wondered how everyday, innocuous linux commands and utilities can be leveraged by bad actors? Curious how you can detect if they’re being used maliciously in your ecosystem?
Curly will stop at nothing to infiltrate Hackington and exfiltrate all the data he can find. There’s just one problem. Linus-- always vigilant, alert to anything suspicious, and wise to Curly’s tricks.
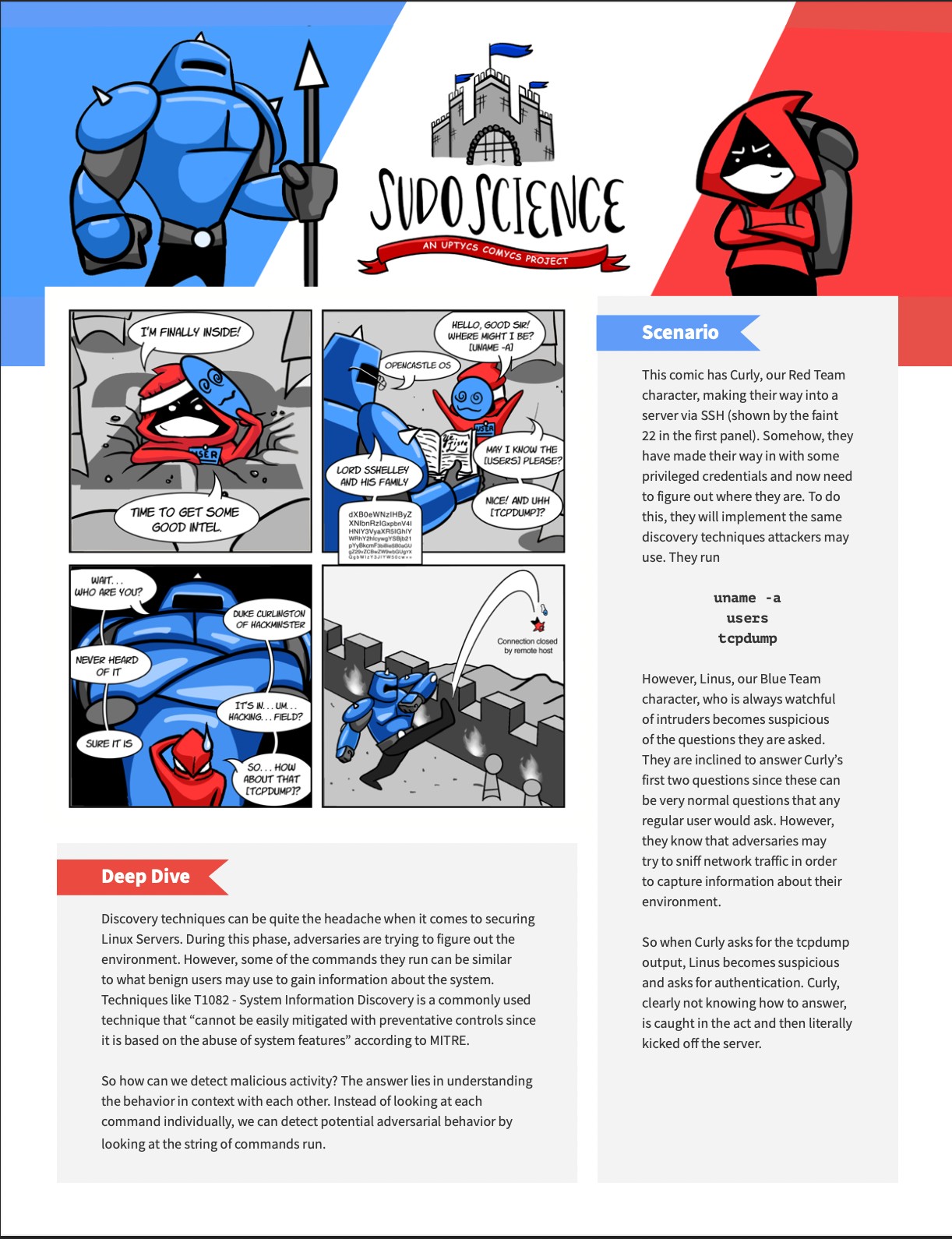
This episode of Sudo Science has Curly, our Red Team character, making their way into a server via SSH. Somehow, they have made their way in with some privileged credentials and now need to figure out where they are. To do this, they will implement the same discovery techniques attackers may use. They run
uname -a
users
tcpdump
Click here to downloadDeep Dive
Discovery techniques can be quite the headache when it comes to securing Linux Servers. During this phase, adversaries are trying to figure out the environment. However, some of the commands they run can be similar to what benign users may use to gain information about the system. Techniques like T1082 - System Information Discovery is a commonly used technique that “cannot be easily mitigated with preventative controls since it is based on the abuse of system features” according to MITRE. So how can we detect malicious activity? The answer lies in understanding the behavior in context with each other. Instead of looking at each command individually, we can detect potential adversarial behavior by looking at the string of commands run.
Want to see the full Sudo Science Comyc? Download your copy here.
Or click here for more Sudo Science action.


