End-to-End Security from Code to Runtime
The Uptycs and Checkmarx integration bridges the gap between development and production, offering unparalleled visibility and security across the entire software lifecycle. This partnership allows teams to prioritize and remediate vulnerabilities more effectively, combining deep runtime insights from Uptycs with Checkmarx’s static code analysis and SAST findings.
Secure your applications from code to container runtime
Enable actionable insights with runtime and exposure context across your Kubernetes environments
Build pathways for code remediation and trusted deployments
Elementum cras viverra placerat
Feature one here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
Feature two here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
Feature three here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
Feature four here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
Integration Highlights
Key Features of the Uptycs-Checkmarx Partnership
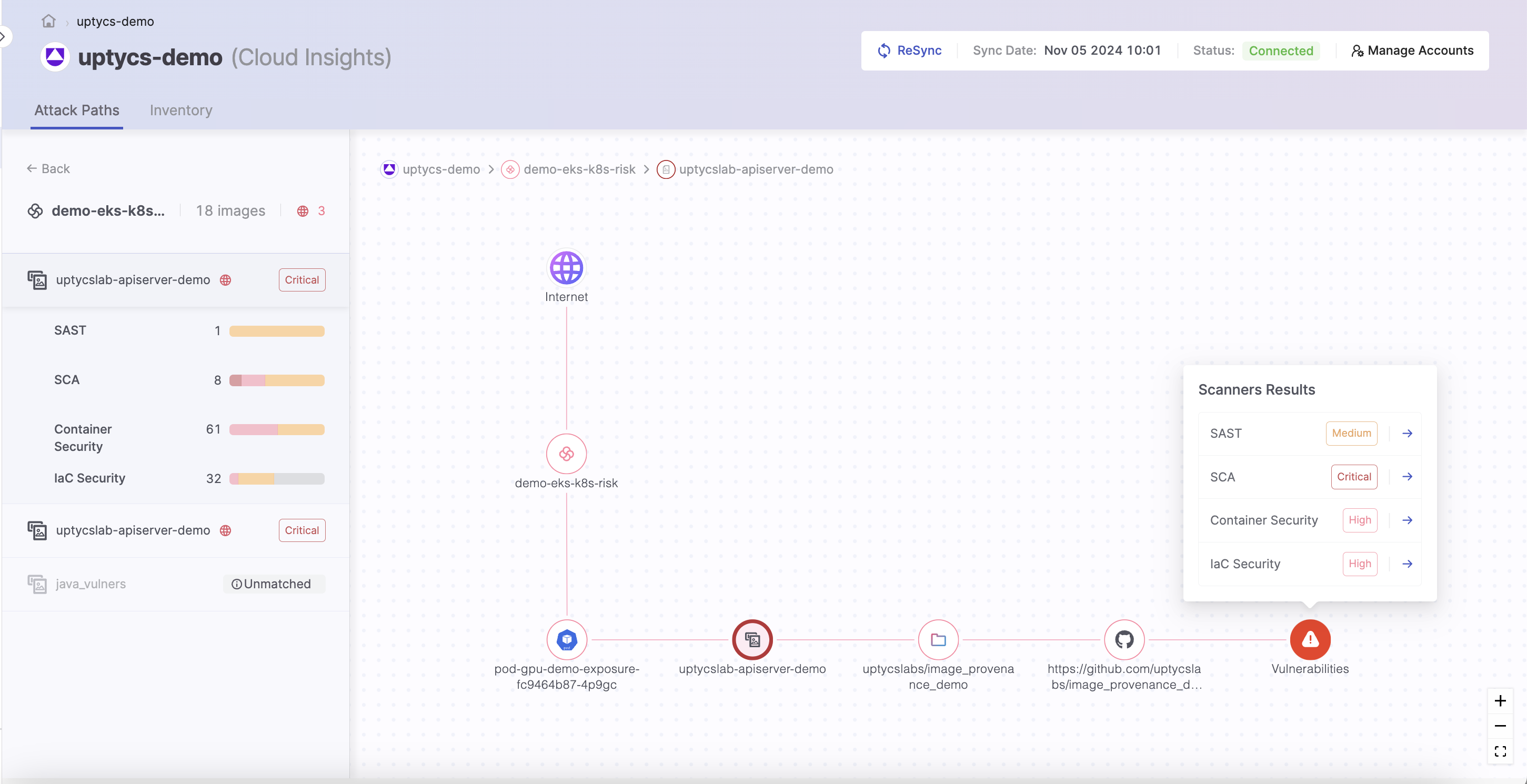
Prioritize More Effectively With Runtime and Exposure Context
Add runtime intelligence to Checkmarx findings, prioritizing vulnerabilities on exposed images with critical attack paths. Streamline remediation by focusing on the vulnerabilities for the most business critical assets
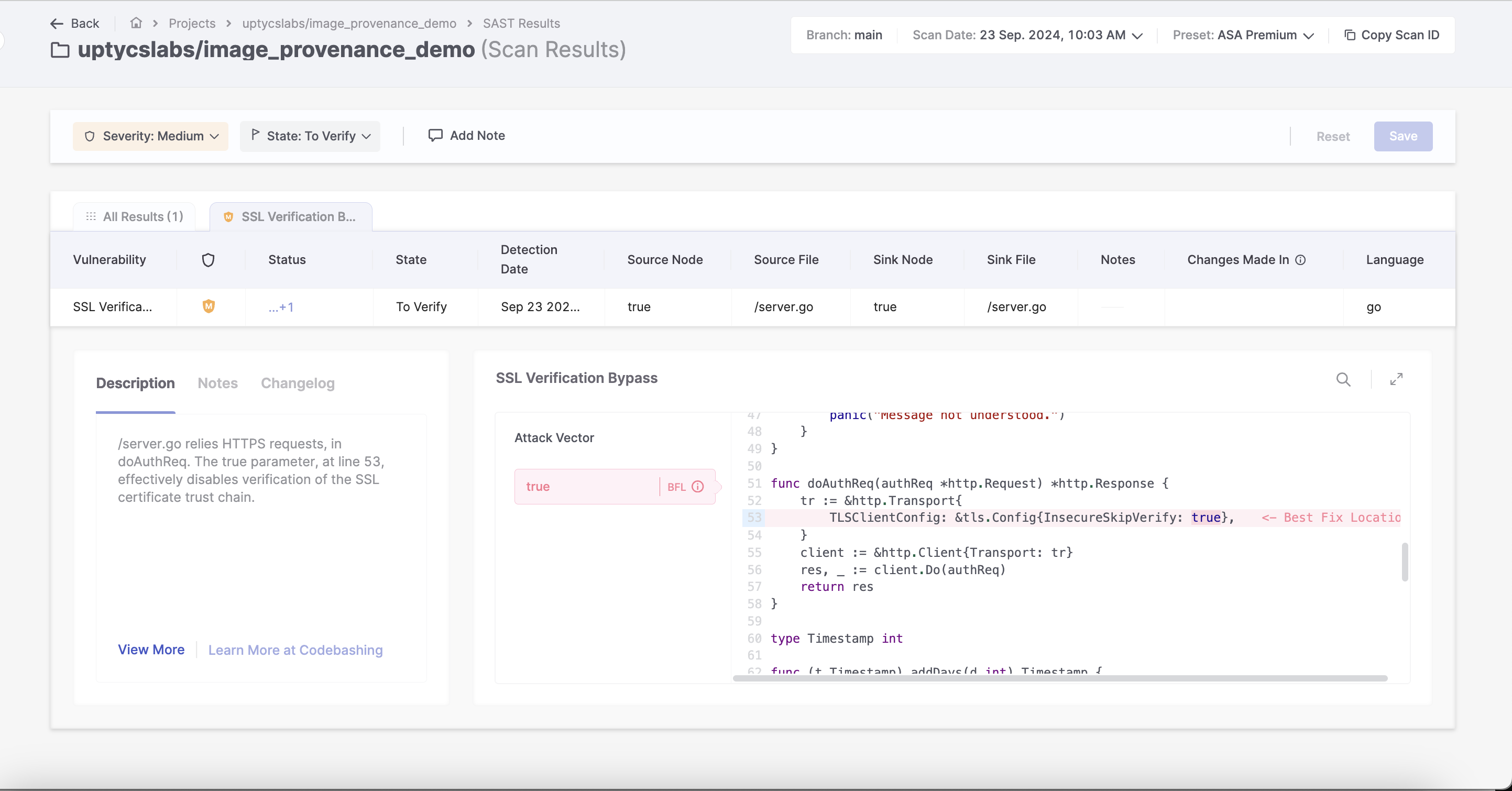
Detect and Remediate Open Source Risk
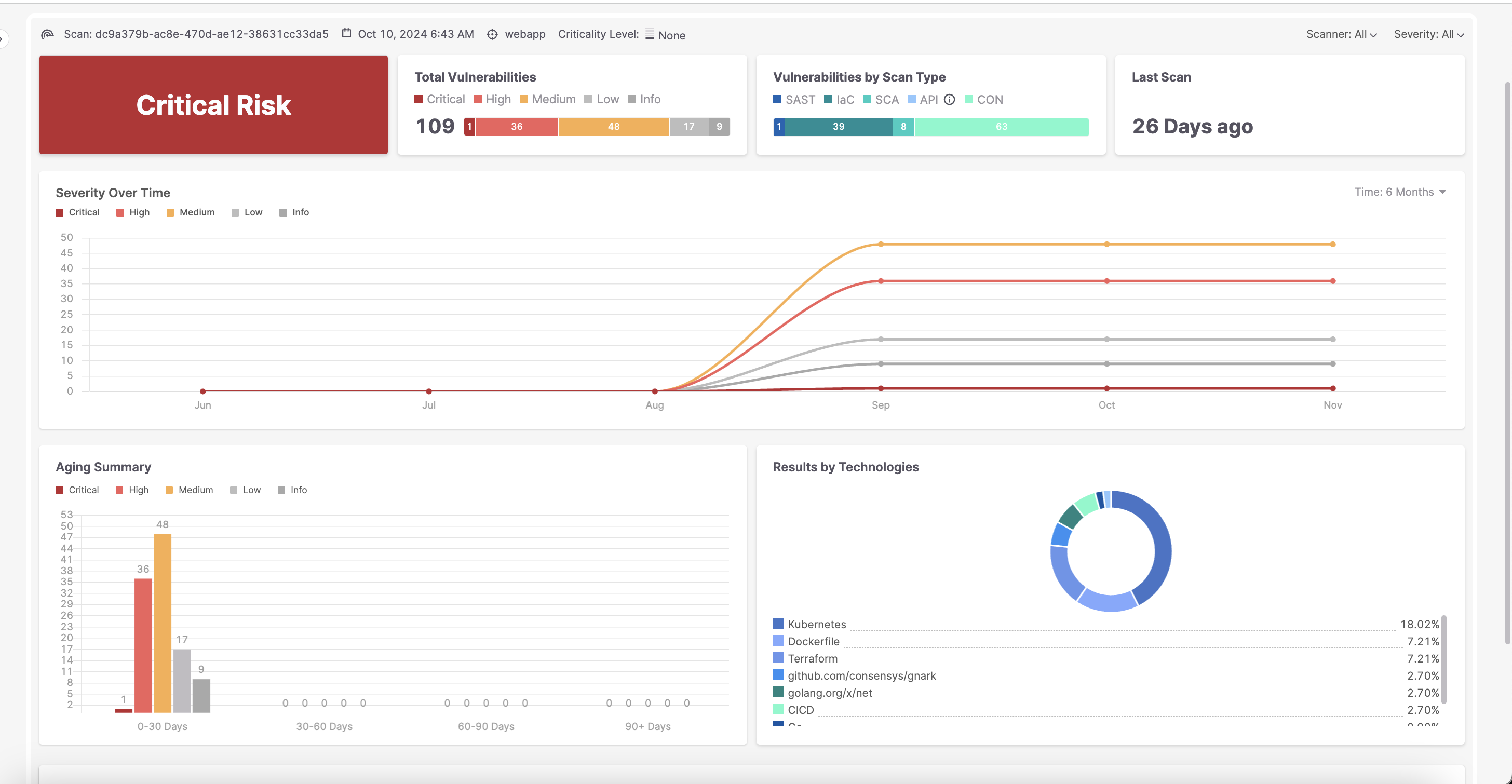
Ensure Full Application Lifecycle Security
Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”


