Secure Your Hybrid Cloud from Dev to Runtime
Secure Your Hybrid Cloud from Dev to Runtime
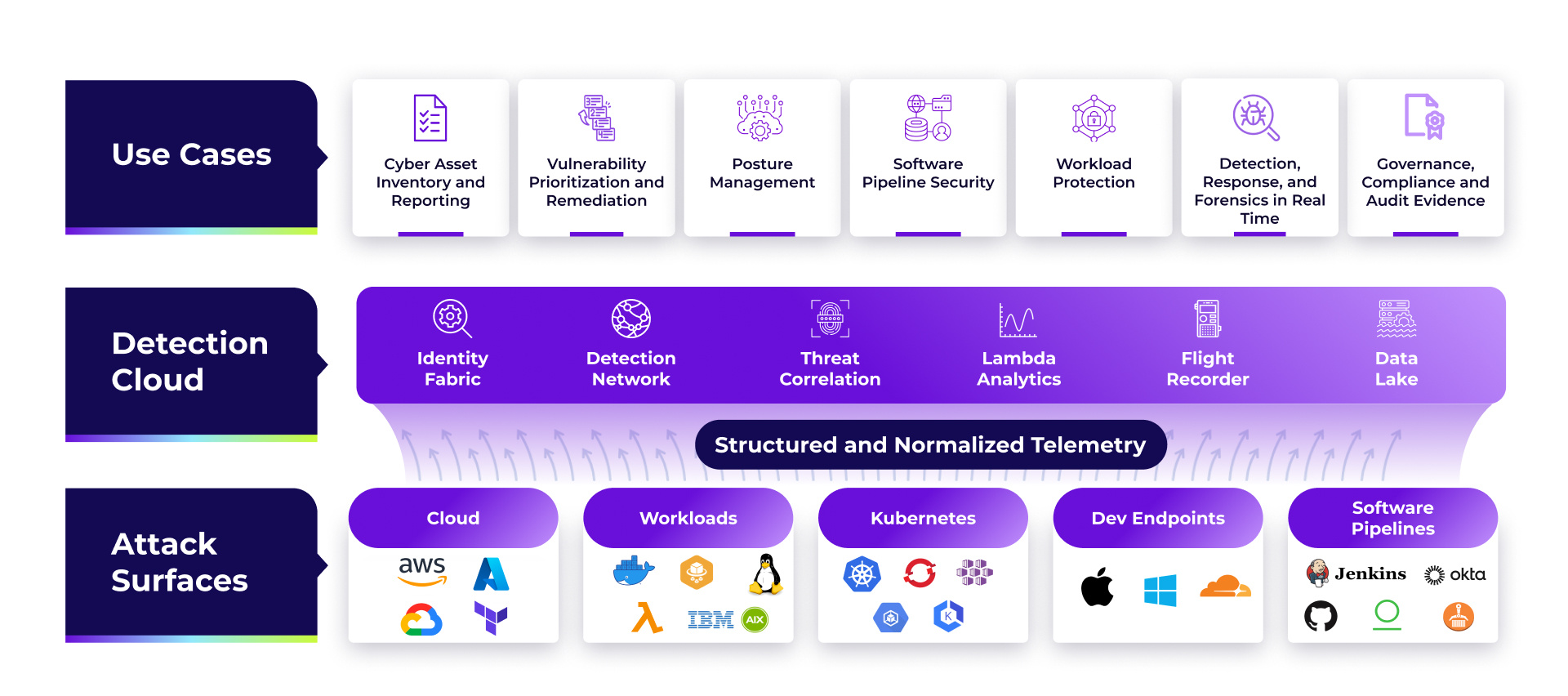
Unified Risk Visibility, Protection, and Prevention
From Buildtime To Runtime For Every
Hybrid Cloud Workload
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Uptycs offers continuous and real-time workload visibility and scanning, correlating insights across agentless scans and runtime insights with eBPF. Visualize insights across every layer from packages to processes on every workload to the entire software catalog across all your assets.
Prioritize and root cause the most critical risks, vulnerabilities and threats in your environment with unified risk scoring for every workload and cloud asset. The cloud-native application protection platform helps map out attack paths to critical crown jewels and leverages the power of build-to-runtime provenance to trace runtime threats and vulnerabilities to committed code in your developer pipeline.
Respond to malicious threats with automated and policy driven frameworks. Remove operational silos to enable development teams to address key vulnerabilities and compliance issues before artifacts are deployed into runtime.
The Uptycs Approach to Cloud Security
1
Structured telemetry
Collect and normalize telemetry close to its source.
2
Cloud power
Deliver security analytics and alerts in real time.
3
Standards and APIs
Base data models and modes of interoperability on standards, using an API-first approach.
4
Unified data model
Simplify workflows and boost correlations with a single source of truth for all security data.
5
Effortless Scalability
Scale seamlessly from hundreds to millions of workloads.
Streamline, Secure, and Save
Uptycs CNAPP consolidates cloud security silos into a unified platform, providing a single security console, policy framework, and data lake. This unification enables greater automation, simplifies policy enforcement, and extends security coverage, all while reducing security risks.
Powerful scanning, detection, and
remediation tools for the hybrid cloud
Deep Visibility and Assessment For Every Workload
-
Performs deep scanning going beyond eBPF to build build to runtime context for every workload from process activity to cloud configuration and developer build provenance
-
Leveraging these insights and GenAI intelligence, Uptycs is able to catalog your entire workload fleet to give you a baseline and wide understanding of every piece of software that is running in your environment.
Simplified Risk Prioritization and Root Cause Analysis
-
Uptycs blends insights into one single risk score for every cloud workload reducing mean time to prioritize and remediate risk.
-
Understand the most critical vulnerabilities, threats and attack paths with unified context from your cloud and Kubernetes as well as key security misconfigurations in your code repo and CI/CD pipelines.
Detect and Stop Threats In Real-Time
-
Stop threats such as cryptominers and reverse shells proactively and in real-time with the ability to define customized policies for FIM and YARA to catch masqueraded threats in your environment.
-
Leverage Uptycs threat hunting at scale to trace behavioral threats and anomalies based on key indicators of compromise including traceability to vulnerable packages and malicious code in your development pipeline
Build Pathways For Embedded Security Into Development
-
Build trusted gateways through unified policy and exception management for vulnerabilities and image scans that embeds seamlessly into your development workflow.
-
Give developers context at every layer with the ability to grant exceptions to minimize any compromise of developer productivity.
Unified Compliance Reporting
-
Build unified reports and drill-down dashboards for continuous governance and compliance with the ability to leverage and customize out of the box reports including SOC2, CIS, PCI DSS, HiTrust and more.
-
Reduce your TCO and learning curve through unified compliance management that is applicable to any cloud environment and asset.
Simplified Remediation Of Misconfigurations and Vulnerabilities
-
Detect key misconfigurations and vulnerabilities in real-time and accelerate time to remediate by detecting key issues early on with build-time scanning of AMIs, Images, and IaC.
-
Implement scanning of your code repositories to catch code scanning alerts as well as key vulnerabilities from 3rd party dependencies.
Accelerate Incident Response and Forensics
-
Accelerate investigations with Attack Path, Ask Uptycs and Unified Threat Hunting.
-
Help hunters quickly understand relationships between users and assets, and focus investigations with both historical and real-time queries.
-
Customize compliance checks with adjustable parameters
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your
team's work. That's why Uptycs works seamlessly with your existing tech stack.


Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”










