Revealed: The Biggest Threats to Your Cloud Workloads
A Comprehensive Solution for Hybrid Cloud Asset Management
Uptycs Unified Inventory offers a comprehensive view of your hybrid cloud environment, providing real-time updates and detailed asset information. This enables you to identify vulnerabilities, assess risks, and optimize costs, ensuring effective security outcomes.
Uptycs optimizes software asset management, ensuring compliance and security. It provides instant visibility into hybrid cloud vulnerabilities for efficient threat detection and response. By identifying affected systems, Uptycs helps IR teams accelerate incident response.
Uptycs' powerful discovery capabilities allow you to find information about your cyber assets using natural language or pre-built questions. With an extensible open schema and graph-based architecture, you can easily visualize relationships and assess the impact of potential breaches.
Uptycs offers unified asset management, real-time updates, and advanced analysis for effective security outcomes
Uptycs gathers, standardizes, and combines data to create a complete inventory of cloud assets. Uptycs helps optimize software asset management, identifies security gaps using graph-based architecture and visualization, and speeds up incident response through advanced analysis and a flexible open schema.
Powerful scanning, detection, and
remediation tools for the hybrid cloud
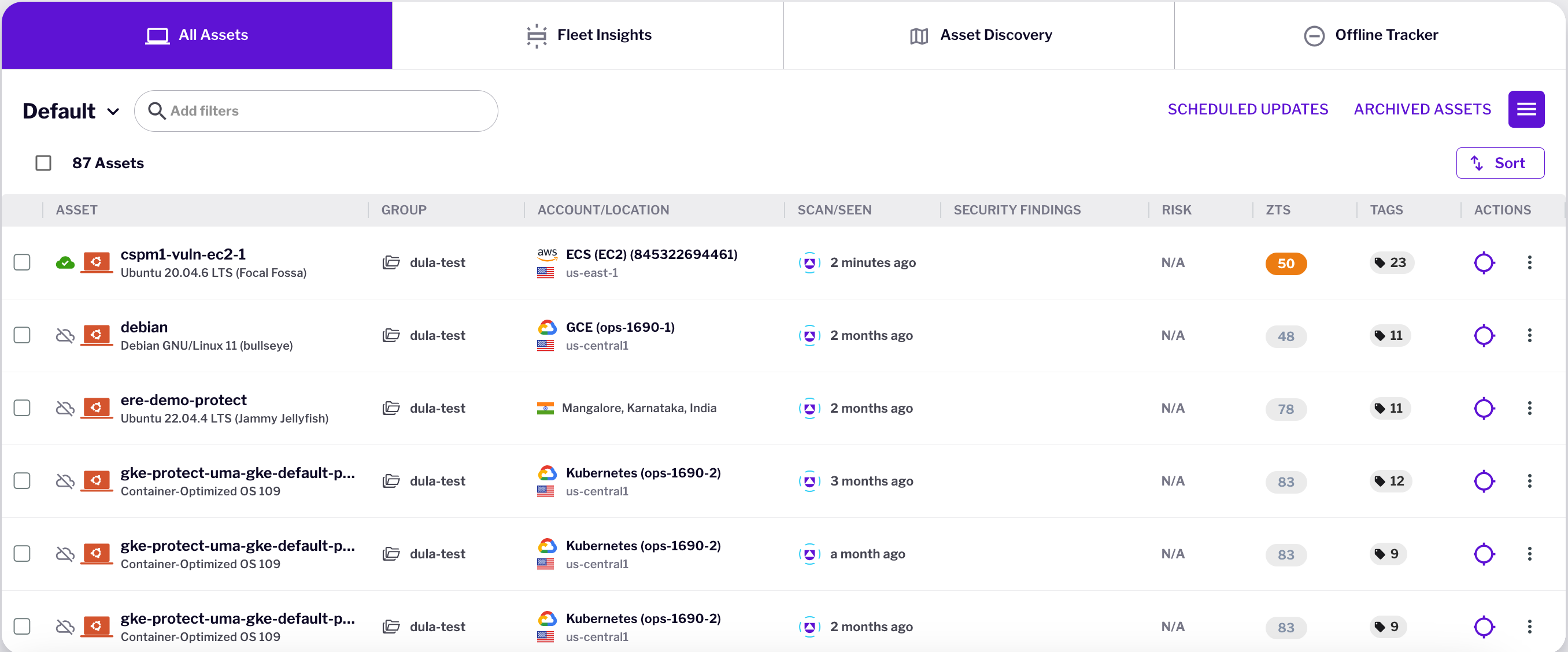
Comprehensive Hybrid Cloud Asset Discovery and Management
-
Unified Inventory: A comprehenisve inventory of assets across Cloud, Kubernetes and on-premise including servers, clusters, applications, endpoints, and identities in a single platform
-
Real time Updates: Provides continous monitoring to ensure inventory is up to date with changes in the environment for improved risk and detection outcomes
-
Detailed Asset information: Discover, Observe, and Analyze each CLoud asset for its configuration, vulnerabilities, and compliance posture for better cost optimization and faster response to security incidents
.gif)
AI augmented Software Asset Catalog
-
Discover Crown Jewels: Understand the location of your AI workloads and critical data. A deep understanding of your infrastructure and workloads allows you to prioritize the protection of your most valuable assets.
-
Optimize software asset management: Ensure software running on your critical workloads are licensed, patched and updated in a timely manner to meet your Risk and Compliance objectives.
-
Assess hybrid cloud vulnerability instantly: Gain instant visibility into critical applications running across your entire hybrid cloud estate and assess for potential vulnerabilities, deviations for effective triaging
-
Accelerate Incident Response: Assist IR teams to reduce mean time to contain/mean time to recover by identifying affected systems and take appropriate actions
.gif)
Identify Cyber Asset Attack Surface Weakness
-
Outcome Driven Discover: Find any information you need about your cyber asset with the powerful Discovery capability. Use natural language questions to get answers about your cyber assets
-
Extensible Open Schema: Uptycs provides an extensible open schema to investigate your assets and uncover valuable insights using SQL queries.
-
Graph-based architecture: provides a clear visual representation of your cyber assets. This makes it easy to understand relationships and assess the impact of a breach. By visualizing your environment, you can quickly take action to mitigate risks
.gif)
Integrate Seamlessly with Your Security Stack
Uptycs FIM integrates with popular tools such as Slack, PagerDuty, JIRA, and more, allowing for streamlined
alert management and incident response.
Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”