Revealed: The Biggest Threats to Your Cloud Workloads
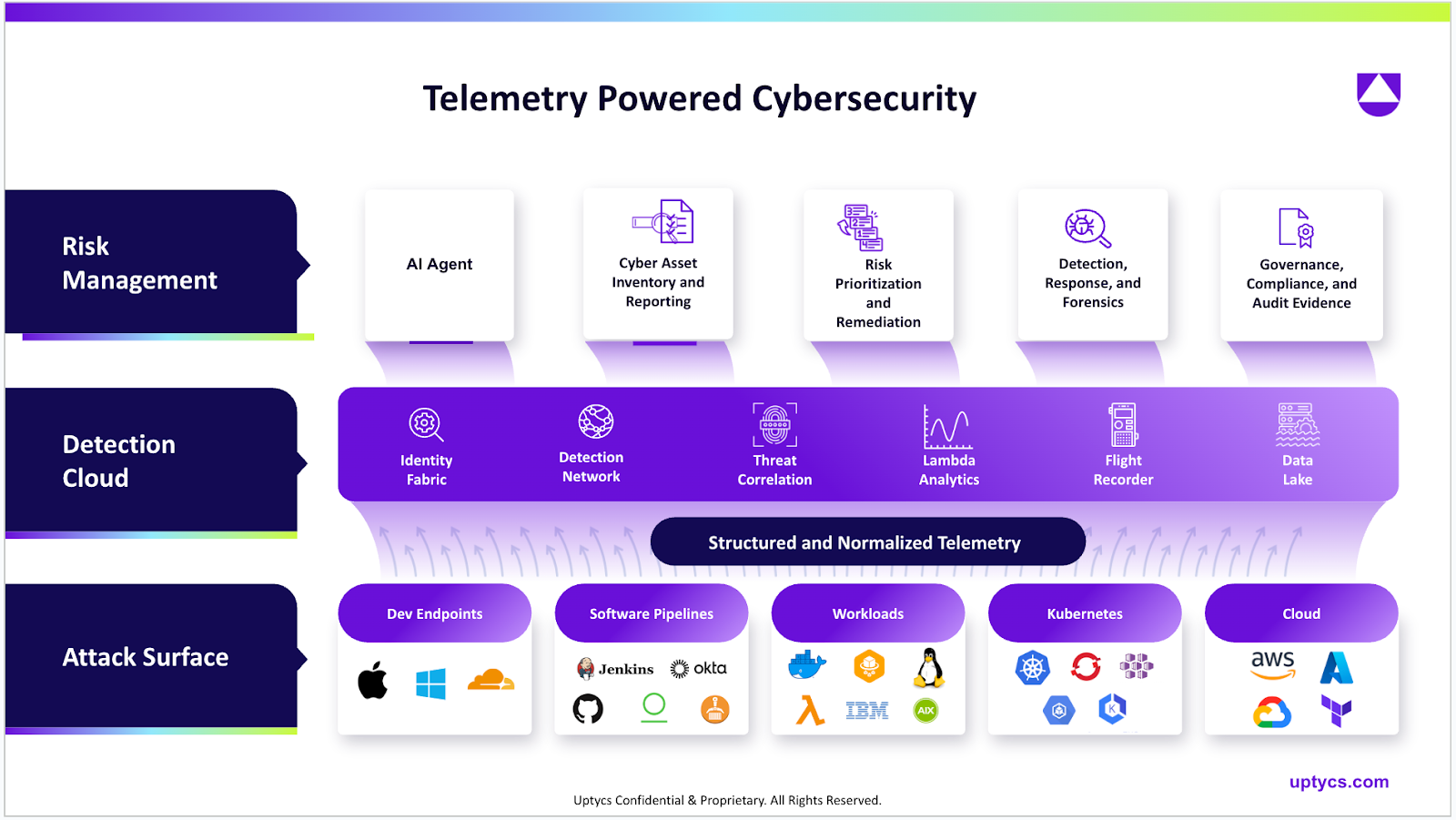
Continuously collect, correlate, and analyze telemetry data
to strengthen your security posture.
Capture telemetry from endpoints, cloud environments, applications, and networks for full visibility across all attack surfaces.
Identify zero-day threats and behavioral anomalies using machine learning models trained on structured telemetry data.
Correlate multi-source events, trigger real-time alerts, and automate investigations with historical context.
Structured telemetry at the source enables real-time detection and response, without complex pipelines.
We collect telemetry across your environment and structure it using AI-ready schemas. This allows direct ingestion for machine learning analysis, real-time correlation, and natural language–driven investigations, no ETL processes or custom engineering required.
Powerful Scanning, Detection, and
Remediation Tools for the Hybrid Cloud
Cloud Environments
Uptycs provides comprehensive cloud security monitoring across major cloud providers including AWS, Azure, and GCP.
-
Cloud resource inventory and configuration assessment
-
Continuous monitoring of cloud service configurations against best practices
-
Detection of misconfigurations and compliance violations
-
Cloud activity monitoring for suspicious behavior
-
Identity and access management oversight
The platform's multi-cloud architecture ensures consistent security controls and visibility regardless of which cloud providers your organization uses.

Kubernetes & Container Security Telemetry
Uptycs delivers specialized security for containerized environments and Kubernetes orchestration.
-
Runtime container security monitoring and threat detection
-
Kubernetes cluster configuration assessment and hardening
-
Container image vulnerability scanning and policy enforcement
-
Kubernetes RBAC analysis and least privilege validation
-
Network policy monitoring and segmentation verification
The platform helps organizations secure their container environments throughout the development lifecycle while maintaining visibility into runtime behavior.

Endpoint Telemetry
Uptycs delivers advanced endpoint security through continuous monitoring and real-time threat detection.
-
Process execution monitoring with behavioral analysis
-
File integrity monitoring and malware detection
-
Network connection tracking and DNS monitoring
-
User activity auditing and privilege escalation detection
-
Memory analysis for fileless malware detection
The platform protects all types of endpoints including laptops, servers, virtual machines, and containers, providing unified visibility and protection across your entire endpoint fleet.

Applications & SaaS security capabilities of Uptycs, powered by rich telemetry
Uptycs provides source control visibility, pipeline correlation, repository scanning, and activity mapping to monitor development environments like GitHub, GitLab, Bitbucket, DockerHub, and more. By connecting code changes to runtime activity and detecting anomalies, Uptycs helps organizations secure their software supply chain—an increasingly critical focus in the cybersecurity industry. It brings comprehensive insight into modern DevOps and SaaS workflows.

User Behavior Analytics Telemetry
User Behavior Analytics (UBA), a key cybersecurity capability offered by Uptycs, powered by telemetry. Uptycs helps detect compromised accounts and insider threats through behavioral insights like login pattern analysis, privilege escalation detection, and file modification monitoring. These features alert on anomalous access, unauthorized privilege changes, and suspicious file alterations—enhancing proactive threat detection. UBA is vital in the modern cybersecurity landscape for identifying subtle, high-risk user activity across hybrid cloud and enterprise environments.

Incident Investigation & Forensics Telemetry
Incident Investigation & Forensics is a vital part of the Uptycs cybersecurity platform. Leveraging historical telemetry, Uptycs enables attack timeline reconstruction, impact assessment, and audit & compliance support. These capabilities help security teams investigate root causes, understand what data was accessed or altered, and generate compliance-ready reports. In today’s threat landscape, such forensic depth is essential for rapid response, minimizing damage, and ensuring regulatory alignment across hybrid cloud environments.

Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your
team's work. That's why Uptycs works seamlessly with your existing tech stack.

Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”