Uptycs System Insight, Visibility, and User Behavioral Monitoring
Uptycs System Insight, Visibility, and User Behavioral Monitoring offers organizations a unified solution to gain deep visibility, manage assets, and monitor insider risk across hybrid cloud, on-premise, and containerized environments, providing real-time insights and advanced security controls to safeguard critical infrastructure.
Revealed: The Biggest Threats to Your Cloud Workloads
Comprehensive Security Solutions
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
With real-time monitoring and anomaly detection across users, systems, and containers, Uptycs allows organizations to identify and address unusual behavior that could lead to insider risks or compliance violations.
By consolidating asset, behavioral, and system data into one platform, Uptycs streamlines asset management and compliance reporting for improved operational efficiency.
Uptycs is designed to secure environments ranging from traditional on-premise data centers to complex multi-cloud infrastructures and containerized workloads.
Simplifying Security for Complex Hybrid Cloud Environments
Hybrid cloud adoption presents complex security challenges. Uptycs, as a leading cloud-native application protection platform (CNAPP), offers robust security and compliance capabilities across public, private clouds, and distributed infrastructures—all from a single platform. Gain real-time insights, establish behavior baselines, and take proactive risk management actions.
Powerful scanning, detection, and
remediation tools for the hybrid cloud
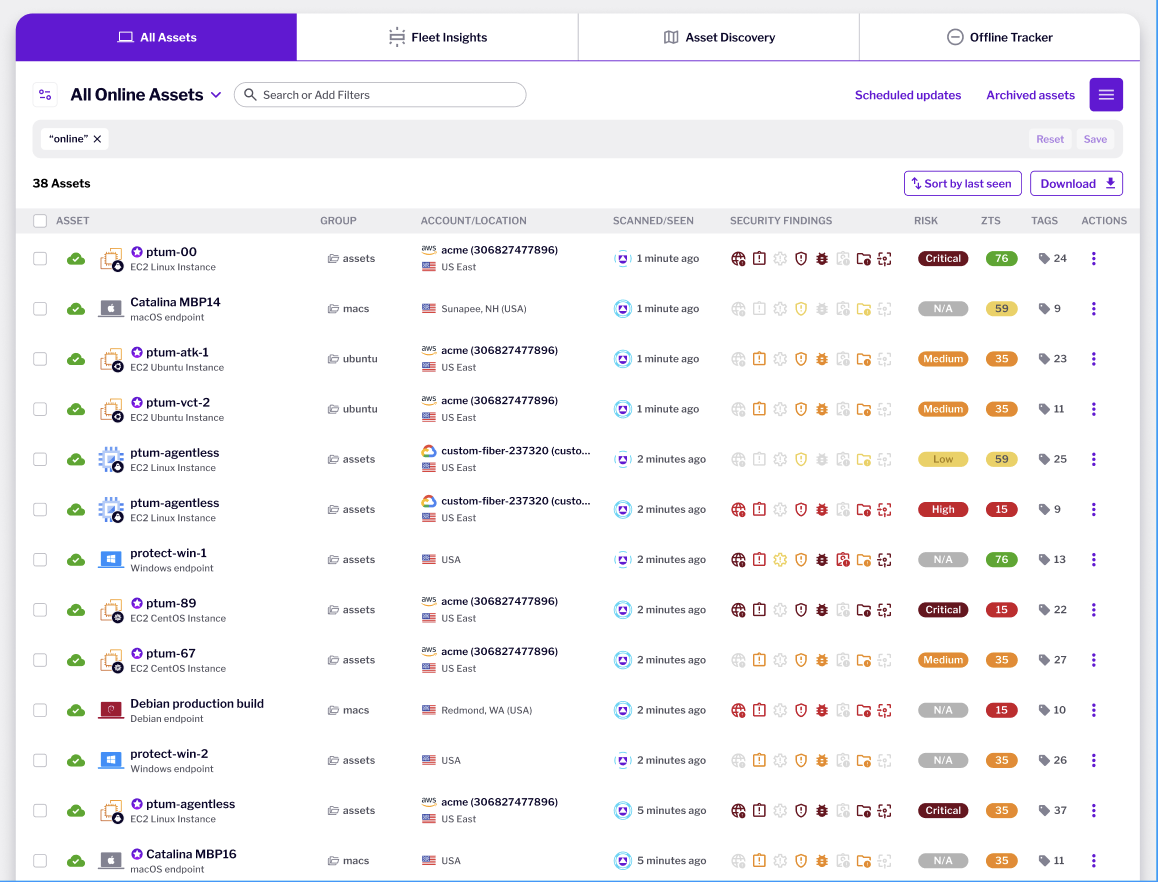
Comprehensive Visibility and Control
-
Asset Inventory and Reporting: Maintain a detailed, real-time inventory of hardware, operating systems, packages, and services across all assets. Software cataloging and license tracking enhance compliance and operational oversight.
-
Certificate Discovery: Easily track active and expired certificates to ensure consistent security standards and compliance throughout your environment.
-
SBOM (Software Bill of Materials): Obtain continuous visibility into software components for hosts, containers, and images, enhancing inventory accuracy and supply chain security.
-
Unmanaged Asset Discovery: Identify and bring under management previously overlooked assets, such as IoT devices, printers, and mobile devices, enhancing organizational security coverage.
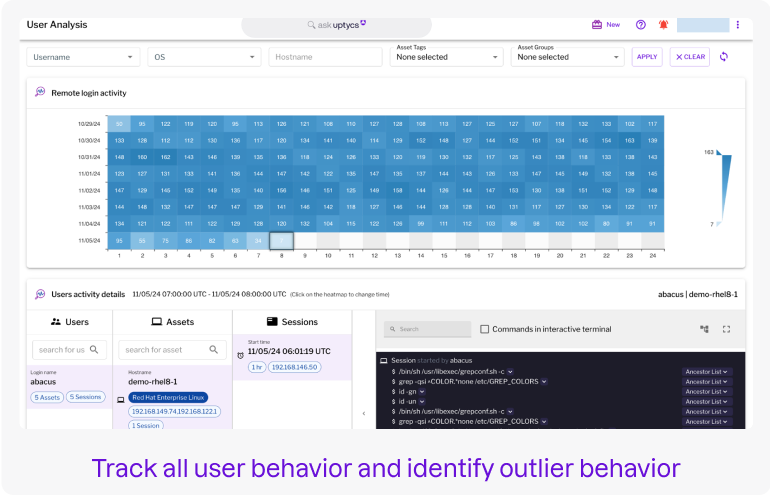
User and System Behavior Monitoring
-
User Behavior Monitoring: Track user activity with detailed insights into logins, processes launched, files accessed, and socket connections made. Uptycs builds behavioral baselines to detect deviations, ensuring enhanced protection against insider threats.
-
Anomaly and Outlier Detection: Uptycs develops baseline models for users, VMs, hosts, and containers, identifying anomalous activities that could signal insider risk or unusual system performance. This functionality is supported by over 2,000 detection rules, continuously monitoring for irregular behaviors.
Forensics, Debug, and Diagnostics
-
Live Diagnostics: Interact with hosts, VMs, and containers to examine live system states, review running processes, and inspect opened files. Uptycs supports file and memory carving. The carved files and memory can be downloaded for analysis by forensic investigation tools.
-
Performance Monitoring: Automatically gather performance metrics when certain thresholds are breached, such as CPU usage exceeding 85%, and quickly identify which processes are responsible for excessive resource consumption.
Public Cloud Discovery and Monitoring
Gain comprehensive visibility into your public cloud environment with Uptycs.
-
Resource Discovery: Discover all resources in your cloud infrastructure, report across regions, and monitor changes in real time to ensure operational consistency.
-
Identity Monitoring: Uptycs provides insights into roles, policies, and permissions, ensuring that permissions are right-sized and excessive permissions are flagged.
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your
team's work. That's why Uptycs works seamlessly with your existing tech stack.



Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
See Uptycs in action
Find and remove critical risks in your modern attack surface - cloud, containers, and endpoints - all from a single UI and data model. Let our team of experts show you how.

.png)