Integrated Compliance Platform
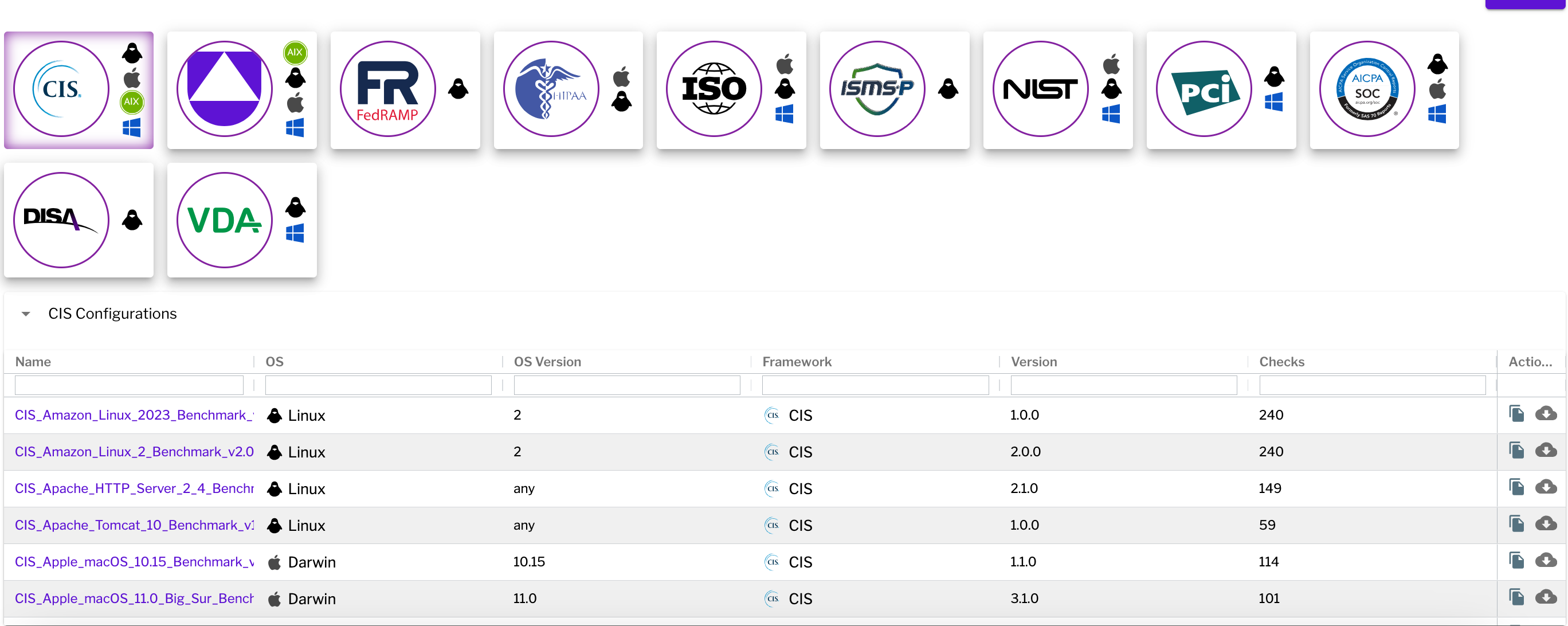
Uptycs offers real-time compliance evaluations, evidence gathering, reporting, policy control, and risk management to fulfill your governance, risk, and compliance (GRC) goals. Uptycs provides pre-built support for standards like CIS, PCI, NIST, HIPAA, STIG, and others, delivering an all-encompassing integrated compliance platform.
Revealed: The Biggest Threats to Your Cloud Workloads
Integrated Compliance Platform
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Real-time automated assessments and evidence collection help organizations ensure compliance, identify deviations, and support investigations. Reporting and alerting provide clear visibility into compliance status and enable timely remediation of issues. These features are core to our integrated compliance platform, ensuring that compliance is continuously maintained.
The central policy repository stores and manages all security policies, simplifying their creation and management. The flexible framework allows for customized compliance checks tailored to your specific environment. Pre-built industry standard templates expedite policy development, enforcement, and the identification of deviations, all within our integrated compliance platform.
Identify, assess, and rank potential risks based on their likelihood and impact. Implement mitigation measures to reduce the likelihood or impact of identified risks, all within our integrated compliance platform.
Comprehensive compliance and risk management solutions
Uptycs provides real-time assessments, evidence collection, reporting, policy management, and risk management to ensure compliance and mitigate risks. Our integrated compliance platform offers comprehensive solutions to meet governance, risk, and compliance goals across various industries.
Powerful scanning, detection, and remediation
tools for the hybrid cloud
Continuous Compliance Monitoring and Reporting
-
Real-time automated assessments: Ensure cloud assets, and activities are consistently tracked, checked against compliance standards, allowing for immediate identification and resolution of any deviations.
-
Evidence Collection: Demonstrate compliance to regulators during audits, support investigations, and prevent future violations. By collecting and analyzing evidence, customers can strengthen their compliance program
-
Reporting and Alerting: Provide a clear visual representation of compliance status, allowing organizations to easily identify gaps and track progress. Ensure that critical compliance issues are promptly addressed with our integrated compliance platform.
Tools for Aligning with Industry Best Practices
-
Centralized Policy Repository: Centralized location for storing and accessing all security policies, making it easier to create, manage lifecycle of policies including exceptions to reduce noise
-
Extensible Framework: Create and review policies for Utilize templates based on industry standards (e.g. NIST, AWS Benchmark) to accelerate policy development and ensure completeness
-
Policy Enforcement: Implement Technical controls, like access controls and intrusion detection, help prevent unauthorized access, while monitoring and auditing deviations from policies and standards through log analysis, network monitoring, and security audits.
Prioritizing Data Privacy, Cyber Threats, and Regulatory Compliance
-
Risk Identification: Identify risks related to data breaches, cyberattacks, regulatory violations, and operational disruptions and Evaluate the likelihood, impact of each identified risk.
-
Risk Prioritization: Rank risks based on their likelihood and impact to determine which ones require immediate attention. This helps focus resources on the most critical risks.
-
Risk Mitigation: Implement measures to reduce the likelihood or impact of identified risks. This may involve technical controls, administrative procedures, or a combination of both
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your team's work. That's why
Uptycs works seamlessly with your existing tech stack.

Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“We've gotten a significant ROI on our Uptycs investment by playing to its strengths - the single data model and backend analytics.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”