Data Security Posture Management (DSPM)
Discover sensitive data continuously and assess risk with context to enable targeted data protection and threat detection for your business-critical cloud workloads.
Revealed: The Biggest Threats to Your Cloud Workloads
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
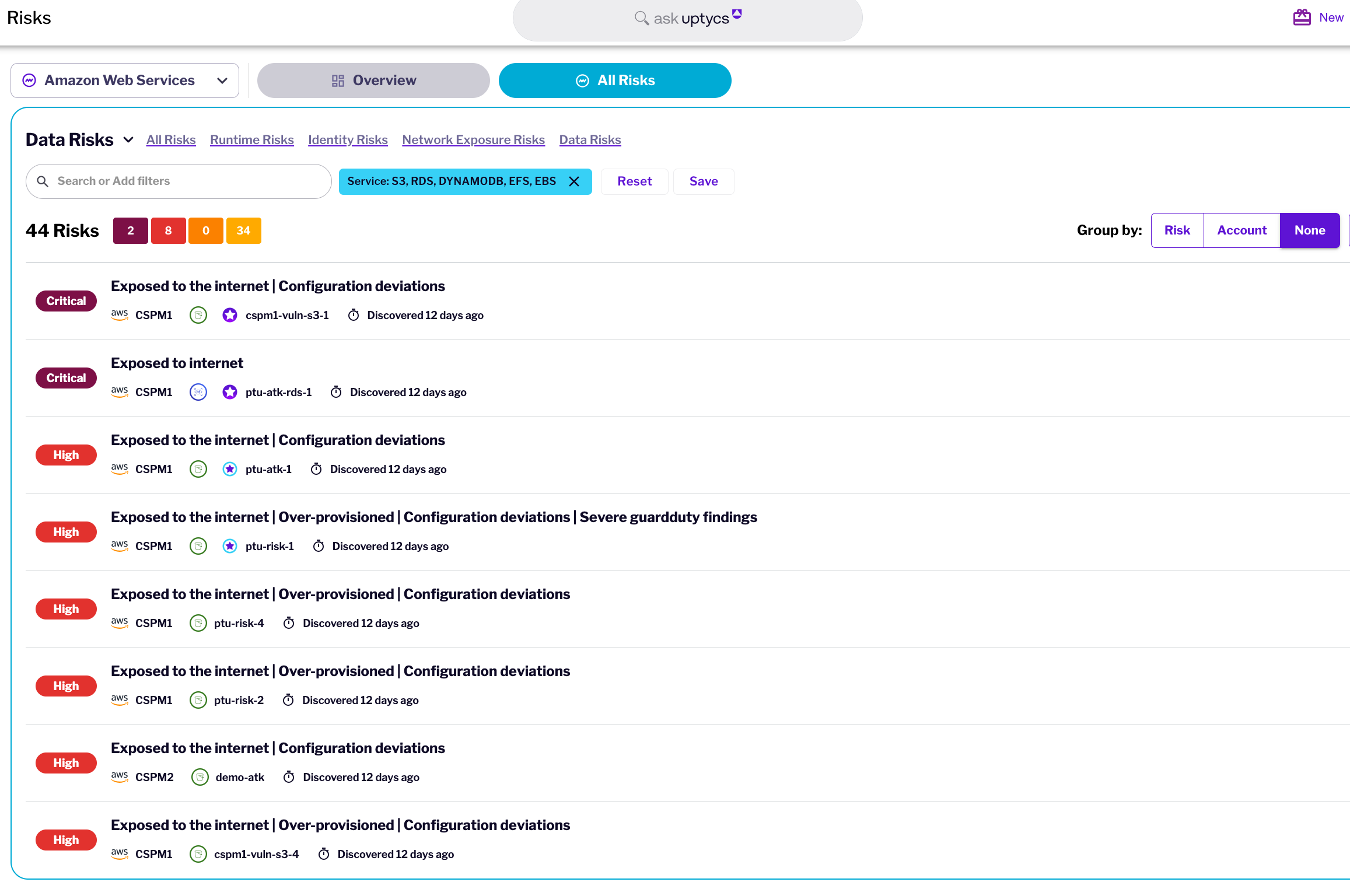
Provide continuous visibility into where regulated data resides across your cloud-native architectures, enabling you to implement precise data controls, meet compliance requirements, and strengthen your overall data security posture management to reduce security risks.
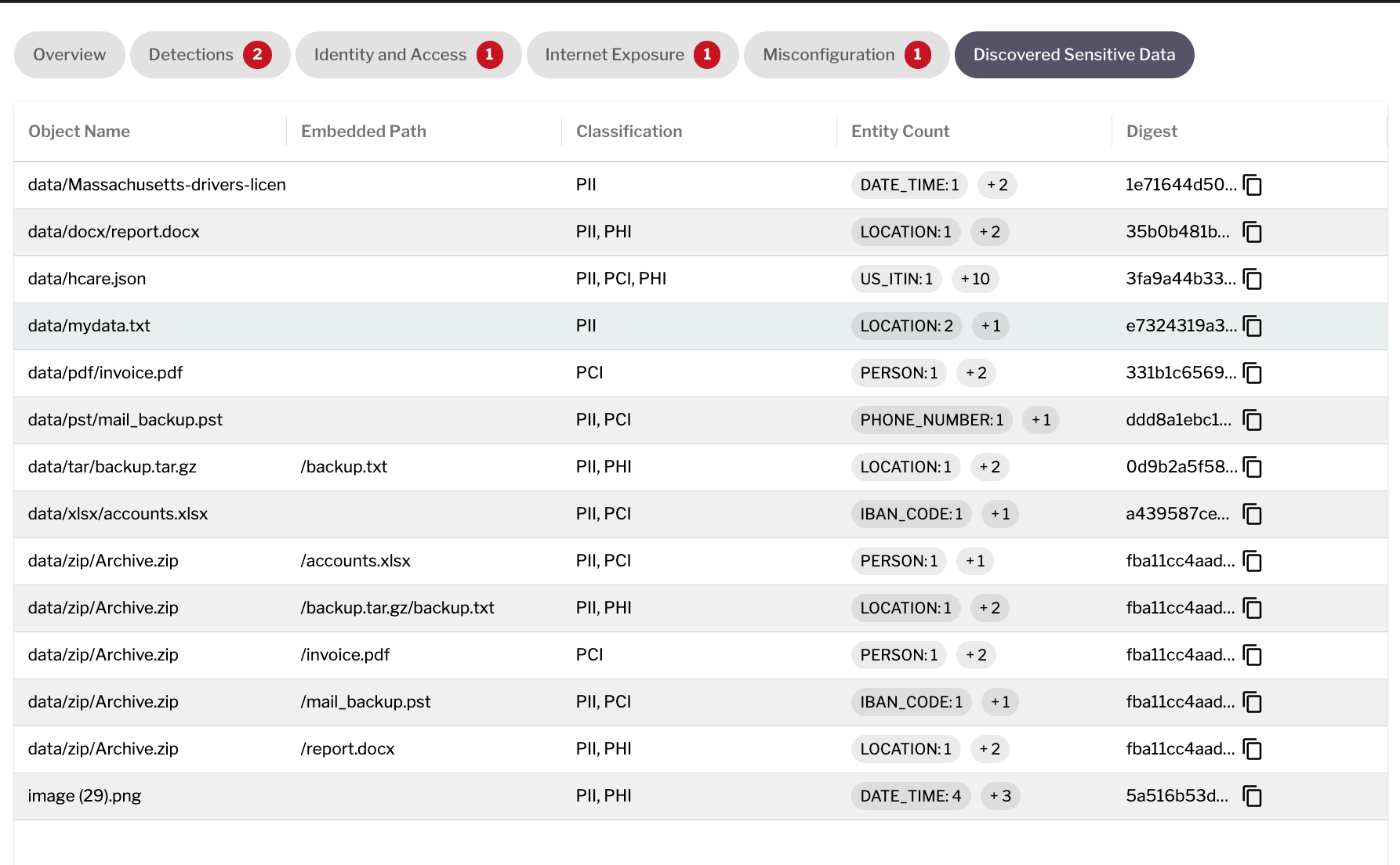
Accelerate classification of sensitive information across your cloud environments by intelligently analyzing context, content, and metadata patterns. Reduce your manual efforts and precisely classify PII, PHI, PCI data to enhance your data security posture management and
meet regulatory and compliance needs.
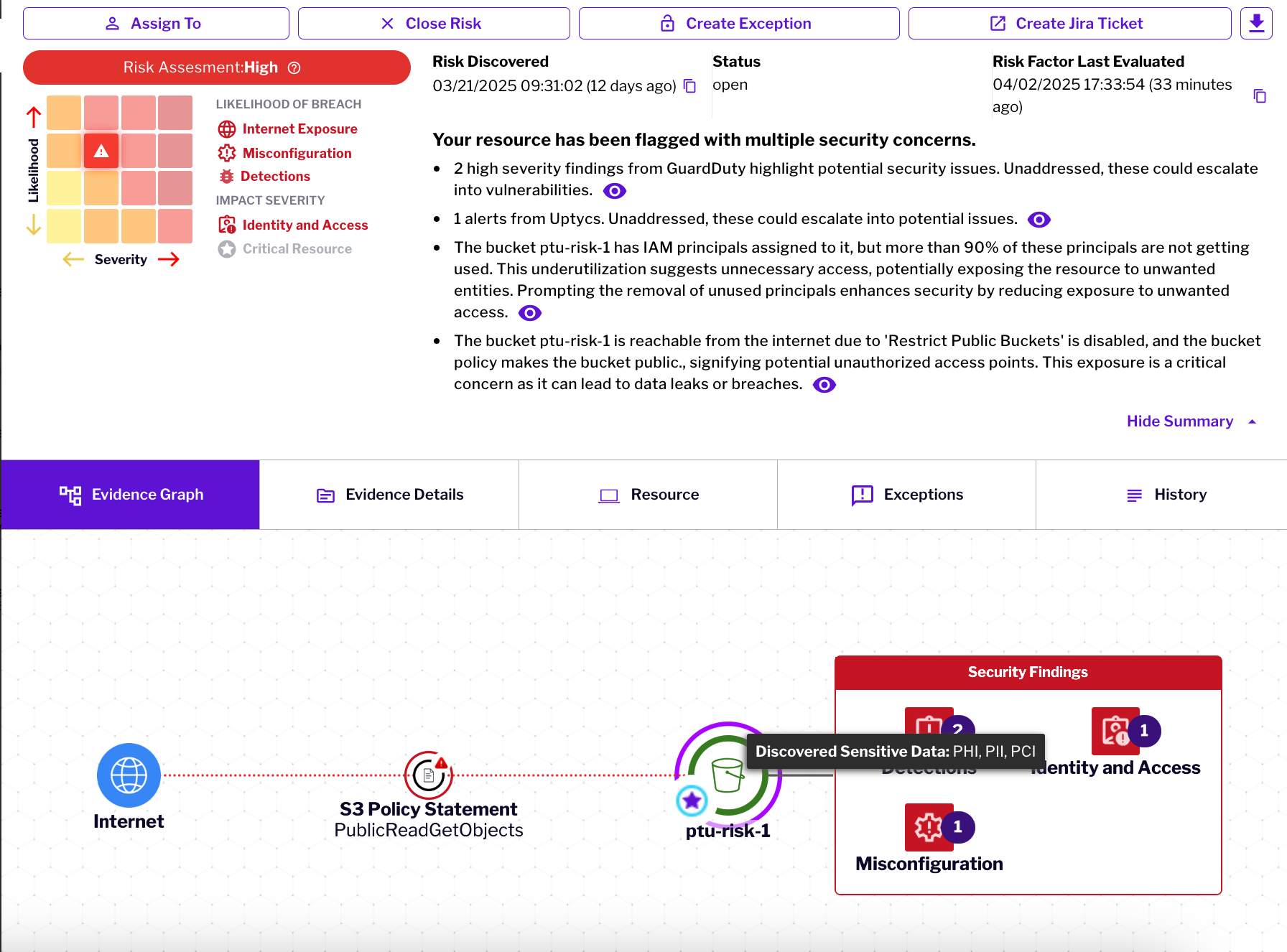
Focus remediation efforts on vulnerabilities posing genuine threats to workloads having access to sensitive data. By correlating infrastructure vulnerabilities with data context, organizations can effectively improve their data security posture management, distinguishing critical issues from theoretical concerns, reducing mean time to remediate for high-value targets.
Intelligent Data Security for Cloud-Native Environments
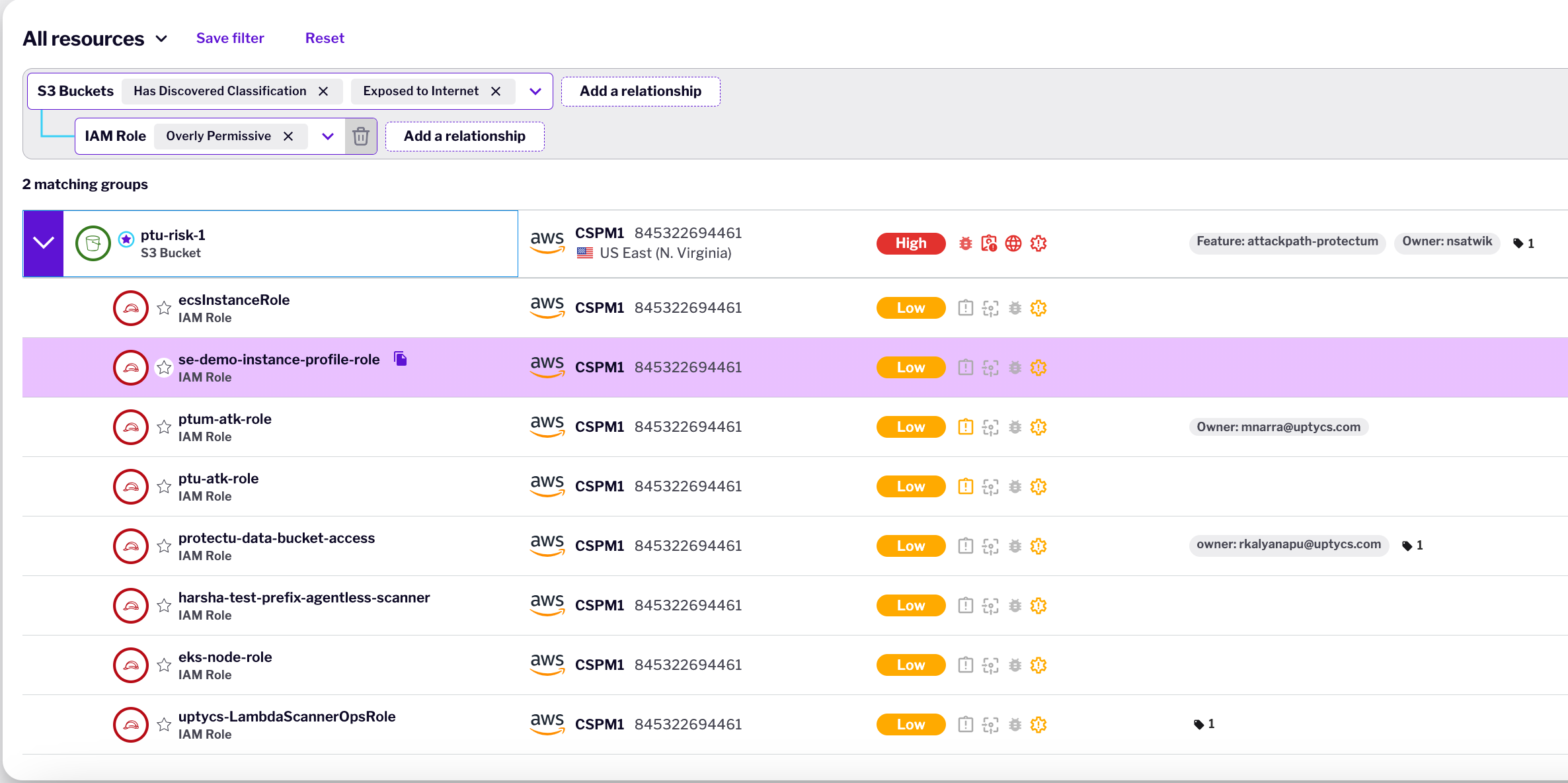
We combine agentless scanning with ML-powered content analysis to continuously discover and classify sensitive data across cloud assets. By correlating data sensitivity with exposure vectors, attack paths, and identity context, we provide real-time visibility into protection status and enable data-centric risk prioritization. Our approach detects anomalous behaviors indicating potential exfiltration while implementing precise security controls that maintain compliance and reduce your critical data's attack surface.
Powerful scanning, detection, and
remediation tools for the hybrid cloud
Intelligent Data Discovery and Risk Assessment
-
Deep content analysis: Combines machine learning algorithms with deep content analysis to automatically identify, classify, and prioritize sensitive data across cloud-native architectures
-
Continuous Agentless Scan: Continuously scan your cloud assets for sensitive data using friction free approach
-
Real-time Visibility: Maintain real-time visibility into data location, access patterns, and protection status
Understand Exploitability with Data Context
-
Contextualize Findings: Correlate data sensitivity with exposure vectors, attack paths and infrastructure vulnerabilities to generate meaningful risk
-
Prioritize Risk: Enable security teams to make data-centric risk decisions that protect high-value assets
-
Enable Security Controls For Regulated Data: Understand what data exists and how it's being used, implement precise security controls, and maintain continuous compliance posture
Identify and Govern Access to Sensitive Data
-
Data Threat Detection: Identify anomalous and behavioral indicators on data exfiltration attempts due to insider threats or external actors
-
Data Aware Access Intelligence: Correlate identity context with data sensitivity classification to enable risk-appropriate access policies and reduce overall attack surface on your critical business data
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your
team's work. That's why Uptycs works seamlessly with your existing tech stack.


Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”