Threat Hunting
Threats may be hiding
in plain sight
Be proactive with Uptycs. Hunt for the most hidden threats across your entire infrastructure, without limits to your hypotheses, and avoid waiting for someone else to discover a breach in your network.
Form hypotheses and
investigate at every level
Get a head start with threat books
Threat hunts often start with known IOCs shared in information sharing groups. Speed up the process of searching for IOCs with Threat Books, sets of known IOCs aligned with certain threat actors.
- Create and update your own Threat Books using file hashes, JA3 signatures, domains, and IP addresses
- Take advantage of up-to-date Threat Books created by our Threat Research team
- Pre-set to automatically search your environment for a specified period

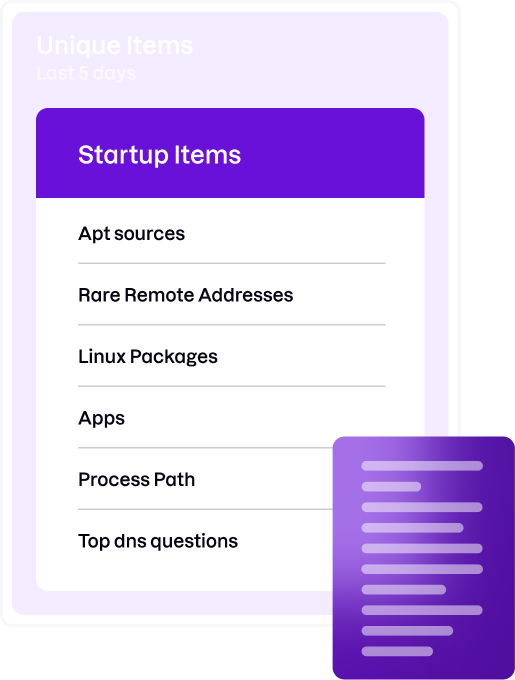
Spot outliers across your endpoint fleet
Anomalous activities can be a valuable indicator of potential threats within your environment. Uptycs offers insights into anomalous behaviors across your on-premises and cloud-based macOS, Linux, and Windows devices.
- Identify rare startup items and packages, including prevalence and date first seen
- Highlight rare process paths by operating system
- See rare DNS queries and remote IP addresses to help spot potential phishing or command-and-control
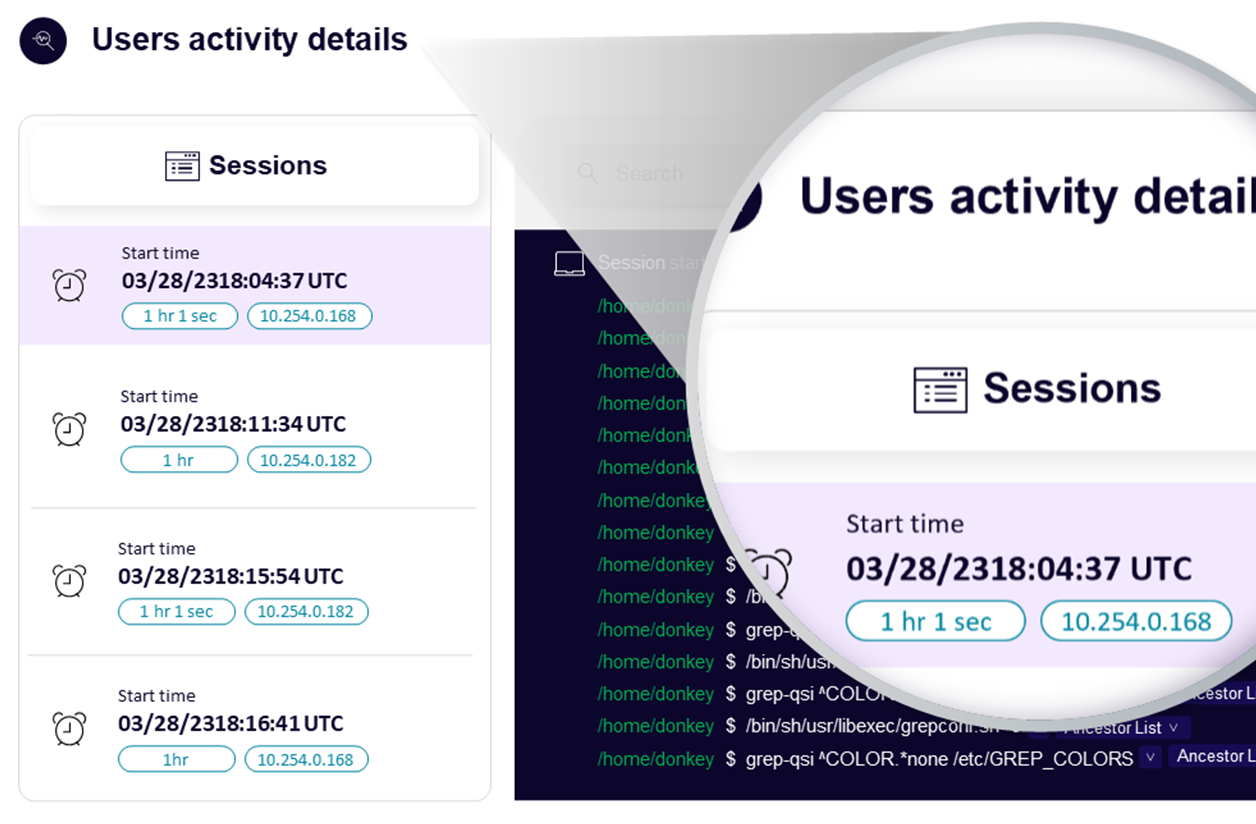
Analyze remote user activity
Attackers or insiders may frequently use remote sessions in unusual ways, making it challenging to identify deviations in behavior. Uptycs visualizes remote user sessions in a heatmap, enabling you to easily detect and investigate peculiar patterns.
- Filter remote login activity by user name, operating system, and hostname
- Drill into remote session activity including commands
- Understand actions taken by the remote user by viewing the process tree graph for the session
Stay vigilant when hunting threats
Explore our cutting-edge solutions for accelerated threat hunting, proactive threat detection, and user behavior insights.
Resources for
the modern defender
Prepare for any challenges that lie ahead by choosing
the right tools today.
Gartner® CNAPP Market Guide
ESG Report: Secure the Expanding Cloud-native Attack Surface

Quarterly Threat Bulletin #7

See Uptycs in action
Find and remove critical risks in your modern attack surface - cloud, containers, and endpoints - all from a single UI and data model. Let our team of experts show you how.
