This article was originally published in 2019 and updated in October 2022.
A cyber security strategy is fundamental in helping your company take a proactive approach to security instead of reacting to every new threat, which can be time consuming and expensive. Whether you have an outdated strategy in place or you are starting from scratch, you can use this guide to get started building an effective and strategic cyber security plan.
What Is a Cyber Security Strategy?
A clear, detailed plan that standardizes security across an organization, a cybersecurity strategy helps CISOs shift from reactive to proactive security, ensuring that they are ready and prepared to respond to various relevant threats.
What Are the Elements of a Cybersecurity Strategy?
Three critical elements organizations should consider to gain maximum impact are governance, technology, and operations.
Governance
How an organization directs and controls IT security. With a cybersecurity program that has a designed governance structure, organizations are afforded a specific and clear plan stating what actions to take and who is authorized to make decisions. Practices, policies, and procedures fall under governance.
Technology
An organization’s infrastructure to withstand cybersecurity threats over time as users interact with it, technology includes the network, logical, and physical environment that protect an organization’s data and assets. The technical element of cybersecurity that must be taken into account includes conducting regular network penetration tests, access control reviews, and physical security assessments.
Operations
How an organization exercises security by putting the governance and technical elements into action. For example, though an organization may have a well written incident response (IR) plan with great detection technology, if the (IR) plan is not exercised by the organization then it is still at a higher risk.
Step 1: Lay the Foundation For a Sound Security Strategy
First, Determine What You Have to Protect
Gain an understanding of the assets your company has to protect. While you cannot protect everything 100%, you can focus on what you absolutely need to protect first. Start with reviewing your business processes and understanding how revenue is generated by the company as well as what systems would have the ability to disrupt that by being unavailable or having their data stolen. You should also identify the data and other IT assets such as applications, devices, servers, and users that are critical to your business.
Identify What You’re Legally Required to Protect
While compliance and security aren’t the same thing, most organizations put the responsibility of maintaining compliance or security compliance frameworks on the CISO. Non-compliance is costly and damaging to your business. Ensuring you design your strategic cyber security plan with required compliance frameworks in mind while help ensure your plan prioritizes legal requirements.
Understand Your Company’s Risk Appetite
Before you begin developing a cyber security strategy, understand your organization’s risk appetite, or the total risk your organization is prepared to accept in pursuit of its strategic objectives. (Tweet this!)
Risk appetites differ depending on your company’s financial strength, industry, objectives being pursued, and more. The cyber security strategic plan that works for a startup likely won’t work for a large, established corporation. By understanding your company’s risk appetite, you can ensure you’re not over- or under-protecting your business.
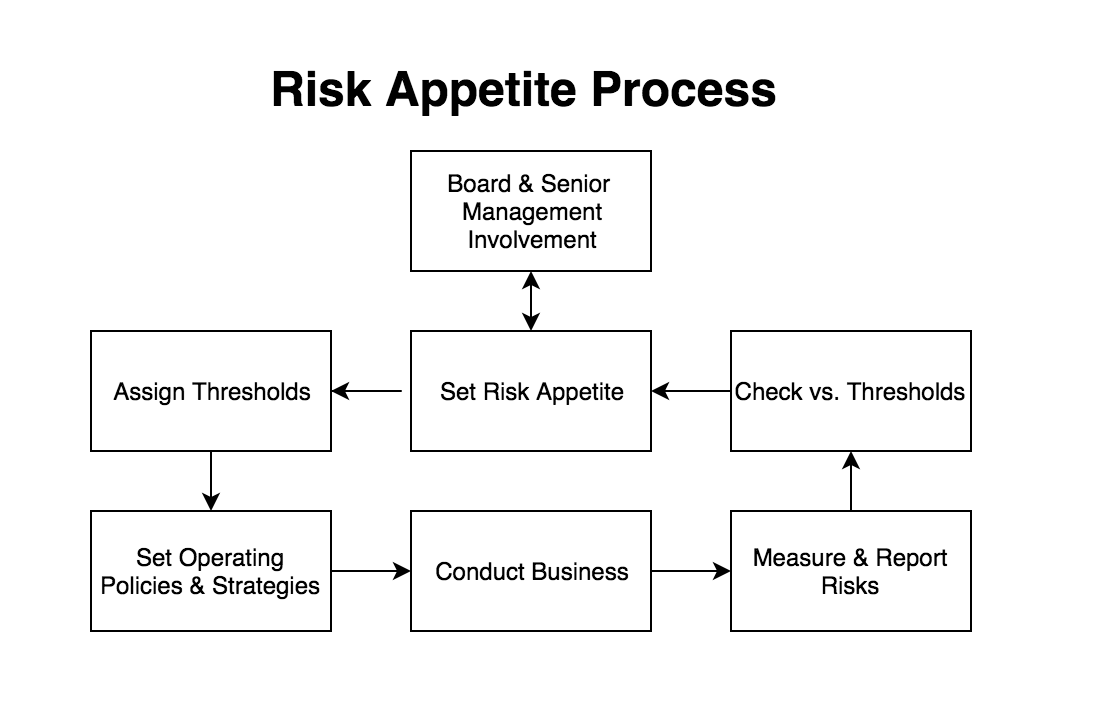
Risk appetite process chart
Step 2: Get to Know the Threat Landscape
Once you know what you need to protect, you need to analyze the threat landscape. To do that, you’ll need to first understand the environment in which your company operates. Who are your customers? What are you selling? Who would benefit from disrupting your business? The answers to these questions help you become more familiar with the general environment.
You’ll also want to look at what is happening with your competitors. What threats do they face? Has their security been breached in the past? The threats your competitors are facing are almost always the same threats that may impact your business.
Finally, understand the types of threats that your business needs to protect itself against. What types of resources do potential attackers have? What are their motivations for shutting you down? Knowing these answers will give you the upper hand in defending your business against these threats.
Step 3: Build Your Strategic Cyber Security Plan
Pick a Framework, Identify the Current State of Your Security Environment & Establish a Timeline
To build your plan, you need to pick a framework to use. Options include CIS Controls, ISO, and NIST. It’s important to choose a framework so you can effectively track progress while prioritizing the most important steps. For instance, the CIS Controls provide you with a set of prioritized actions to protect your organization and the order in which you should take these actions. This allows you to track progress so that you know where you are in the process and what you still have to do.
When you know what needs to be protected from a processes and risk management point of view, evaluate the effectiveness of your current security measures. Are you protecting the right assets? Do you currently have the right processes in place for compliance?
You’ll also need to decide on a timeline, which will depend on the current state of your security. Things will change over time, requiring occasional updates to the timeline. However, it’s important to have a target timeline in mind to get to what your organization considers an acceptable level of risk. With a two- or three-year plan, you’ll need to spend the first year focused on IT hygiene while addressing the greatest or most-likely-to-be-exploited risks.
Evaluate Your Company’s Security Maturity Level
Using either in-house staff or an outside consultant, evaluate your organization’s security maturity level. The concept of security maturity refers to a company’s adherence to security best practices and processes; measuring it helps you identify gaps and areas for improvement. Whether you do this analysis yourself or hire a consultant, make sure the process is repeatable. That way, when you check your security maturity in the future, you’ll have a benchmark with which to compare the results.
Keep in mind that as digital transformation has accelerated thanks to the COVID-19 pandemic, many organizations are now becoming cloud native– meaning they operate entirely in the cloud. This can materially impact the maturity level of your organization, as defending in the cloud can require new tools, technology, skills and staff.
Evaluate Your Technology Stack
Then, look at the technology you currently have in place and identify tools you aren’t currently using to their full benefit. Underutilized software or other tools are only costing you money, time, and increasing your attack surface. Find out if the solutions you’ve identified here are fulfilling their original purposes, and if there is any way to get better use of them. If not, consider getting rid of it.
You can also use the Cyber Defense Matrix to identify any gaps you may have in security. There are a lot of cyber security solutions on the market, and making sure that all aspects of your company are protected can be challenging. The Cyber Defense Matrix helps you understand what you need so when you start looking at security solutions, you can quickly understand which products solve what problems.
Identify Foundational Items & Quick Wins
While building your cyber security strategy, identify the foundational items, quick wins, and high risk items that need to be addressed in the beginning. Identify what is fundamental to the future steps of your plan, and prioritize these actions first. Quick wins are things that are easy to fix or require few resources. In the first year of implementation, make sure you have a combination of both foundational tasks and quick wins.
Step 4: Evaluate Your Organization's Ability to Execute the Plan
The final step in the process of developing a cyber security strategy is assessing your organization’s ability to get the necessary security work done. You’ll need to take a look at your current IT and security teams to understand their skill sets and bandwidth. If you don’t have the resources you need, you may need to plan to hire additional team members or outsource some of your security work in order to execute your strategic cyber security plan.
During this step, it’s also important to think about what the future holds for your business or the IT team.
- Does your company have any big product launches coming up, or a possible merger or acquisition on the horizon?
- Will your IT team be handling any large scale, company-wide projects in the foreseeable future?
- Is your IT team working on a major workstation upgrade program for next year? This could be the perfect time to harden them, as applications will need to be tested for compatibility with the new operating system anyway!
Keep these details in mind as you plan so you can prioritize and plan efficiently.
How Uptycs Can Help You Identify, Detect & Respond
In addition to helping you identify the software you have in your environment, Uptycs can also help ensure your configurations are compliant with the frameworks you’ve identified, and that the security posture of your devices is how you expect it to be over time. Uptycs also helps you see all your network connections and executed applications, as well as which users are using which devices, all while detecting any malware that may be present.
Uptycs can then help with incident response by allowing you to easily investigate suspicious activity or known security issues. Queries can be run on your entire infrastructure —whether it be macOS or Windows workstations, Linux servers running in the cloud, or containers—simultaneously, showing you how a threat has affected different areas of your security. Uptycs also easily integrates with other tools - like Demisto - that help orchestrate and implement repeatable incident response and compliance workflows across your business.
Want to Learn More About How You Can Improve Your Cloud Native Security Strategy? Download Your Copy Today.