The concept of lateral movement stems from the understanding that modern networks typically comprise numerous interconnected devices and systems. Once an attacker manages to breach the perimeter security or gains initial access to one machine, their goal is to stealthily navigate through the network, moving laterally from one device to another and progressively escalating their privileges. The objective is to explore and exploit the interconnectedness to find high-value targets, sensitive information, or critical resources.
Uptycs XDR for lateral movement detection
The Uptycs Threat Research team has consistently emphasized enhancing detections and correlation techniques related to lateral movement. In the previous blog, we mentioned some lateral movement detection capabilities. In line with this commitment, our Uptycs XDR solution has recently undergone significant advancements and gained a multitude of intriguing enhancements and capabilities.
Here is an in-depth overview of these new features, offering insights into the new capabilities of our solution when it comes to detecting lateral movement threats. With these enhancements, we continue to improve lateral movement detection capabilities, empowering organizations to stay one step ahead of evolving threats and bolster their overall security posture.
Uptycs’ XDR now has the following new capabilities to identify lateral movement activities:
- Network Events
- RPC Events
- Signals based on Advanced Correlation
Network events
Network events can play a crucial role in our ability to detect and establish connections between suspicious lateral movements within a system. By analyzing these events, we can identify potential attackers attempting attacks such as Ingress/Lateral Tool Transfer and Kerberoast Attack within the network. Uptycs XDR can now provide a powerful solution for detecting and mitigating such threats. Its advanced capabilities enable us to correlate and analyze network events, proactively identifying and responding to unauthorized lateral movements. With Uptycs XDR, we can strengthen our overall security posture by promptly detecting and thwarting potential attacks aimed at exploiting lateral movement vulnerabilities.
Here is an illustration of how Uptycs XDR Detection detects an attacker trying to transfer tools laterally.
The attacker laterally transfers tools to a Windows machine via smbclient tool running on a Linux machine, as shown in Figure 1.
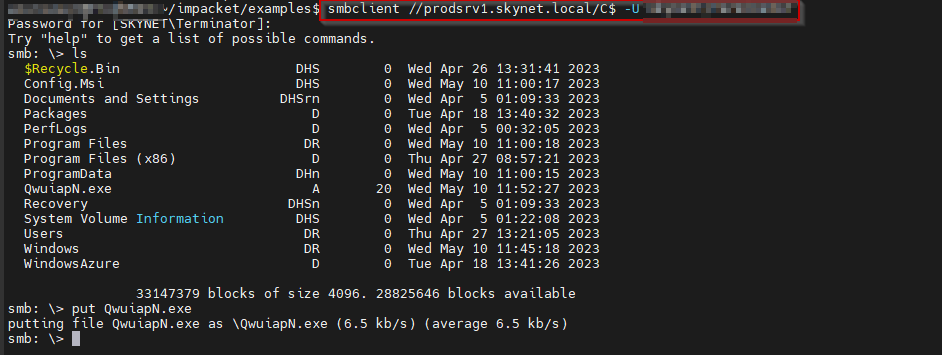
Figure 1 – File Transfers to Windows from Linux System
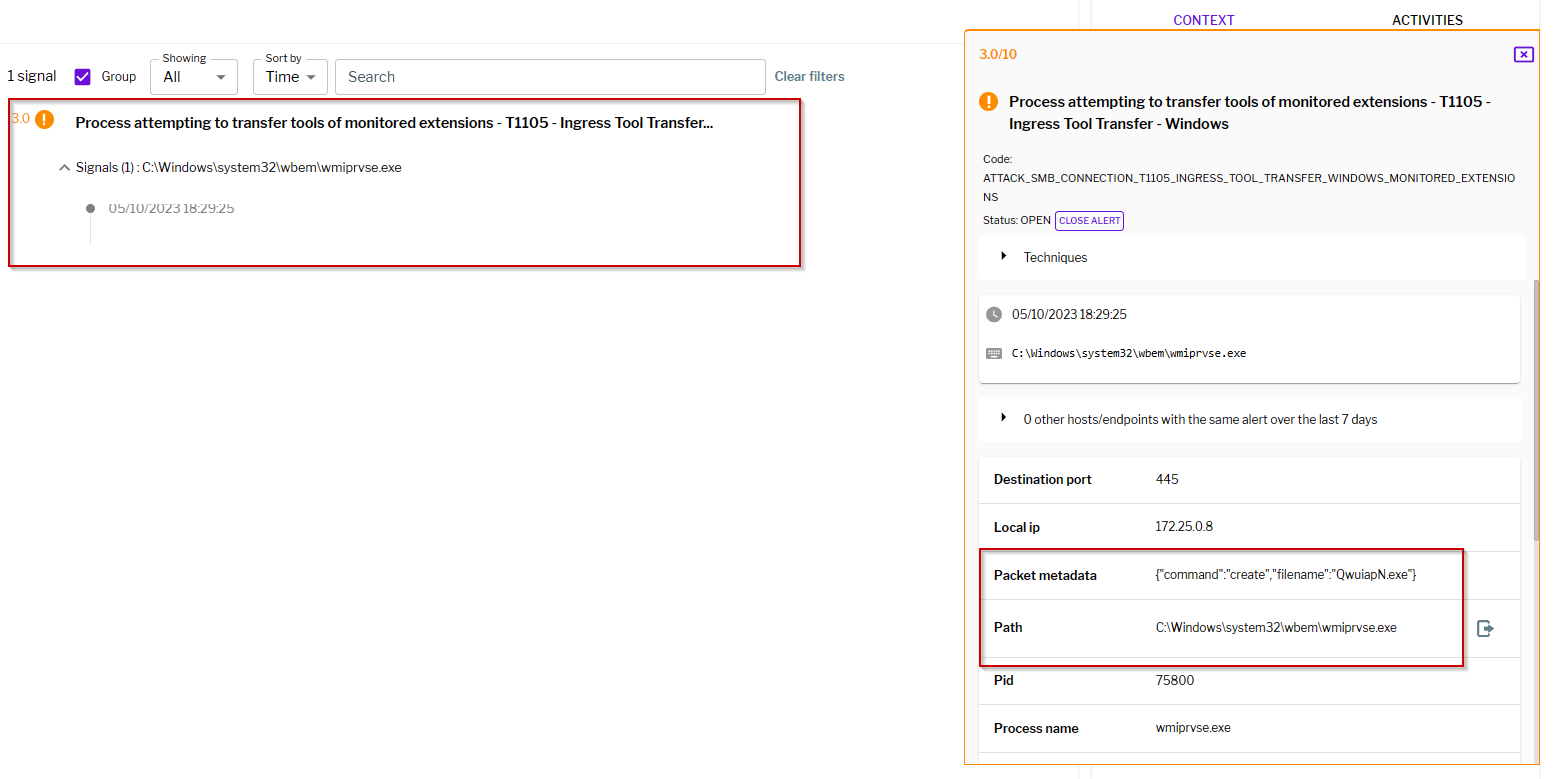
Figure 2 – Uptycs Detection of Ingress/Lateral Tool Transfer
RPC events
Our advancements in telemetry have taken us to a new level of detection, enabling us to gather comprehensive information on various lateral movement techniques. By utilizing RPC (Remote Procedure Call) Events, we can effectively collect and identify specific activities related to lateral movement within our systems. These activities encompass a range of potentially malicious actions, including the notorious DCSync attack, the creation of remote services, the scheduling of remote tasks, the utilization of a remote registry, and attempts by attackers to enumerate user or domain-related data.
Threat actors commonly employ these techniques with the intent to gather sensitive information or establish persistent access to remote systems within our organization. By harnessing the power of RPC Events, we can significantly enhance our ability to detect and respond to such lateral movement attempts, bolstering our overall security posture and safeguarding our critical assets from potential exploitation.
Several examples of lateral movement techniques and Uptycs XDR detections are shown below.
By leveraging PSExec, an attacker has exploited a victim's NTLM hash, acquired through a DCSync attack, to create a service on a remote system.
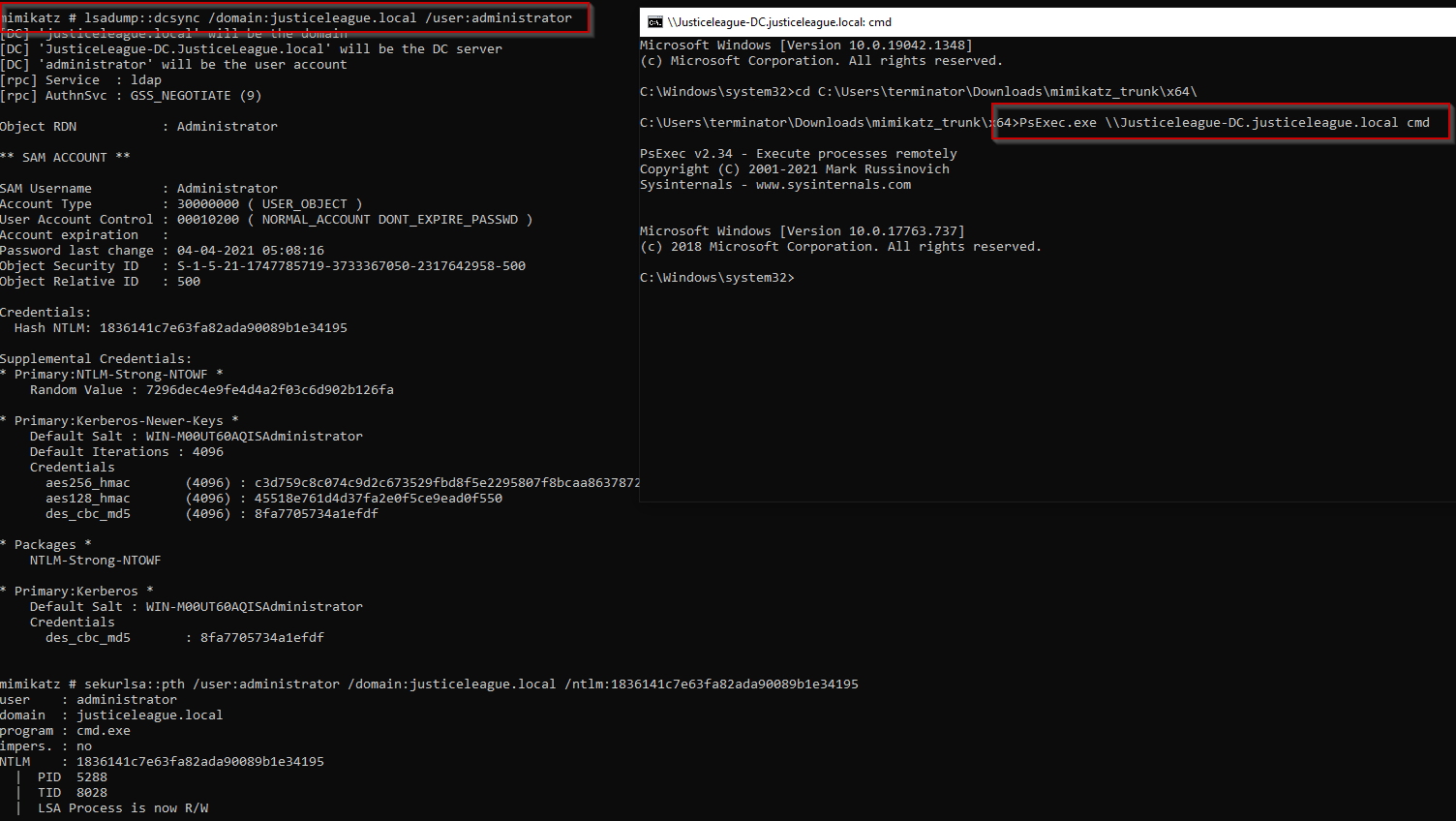 Figure 3 – Attacker performs DCSync Attack and creates service on the remote machine via PSExec.exe
Figure 3 – Attacker performs DCSync Attack and creates service on the remote machine via PSExec.exe
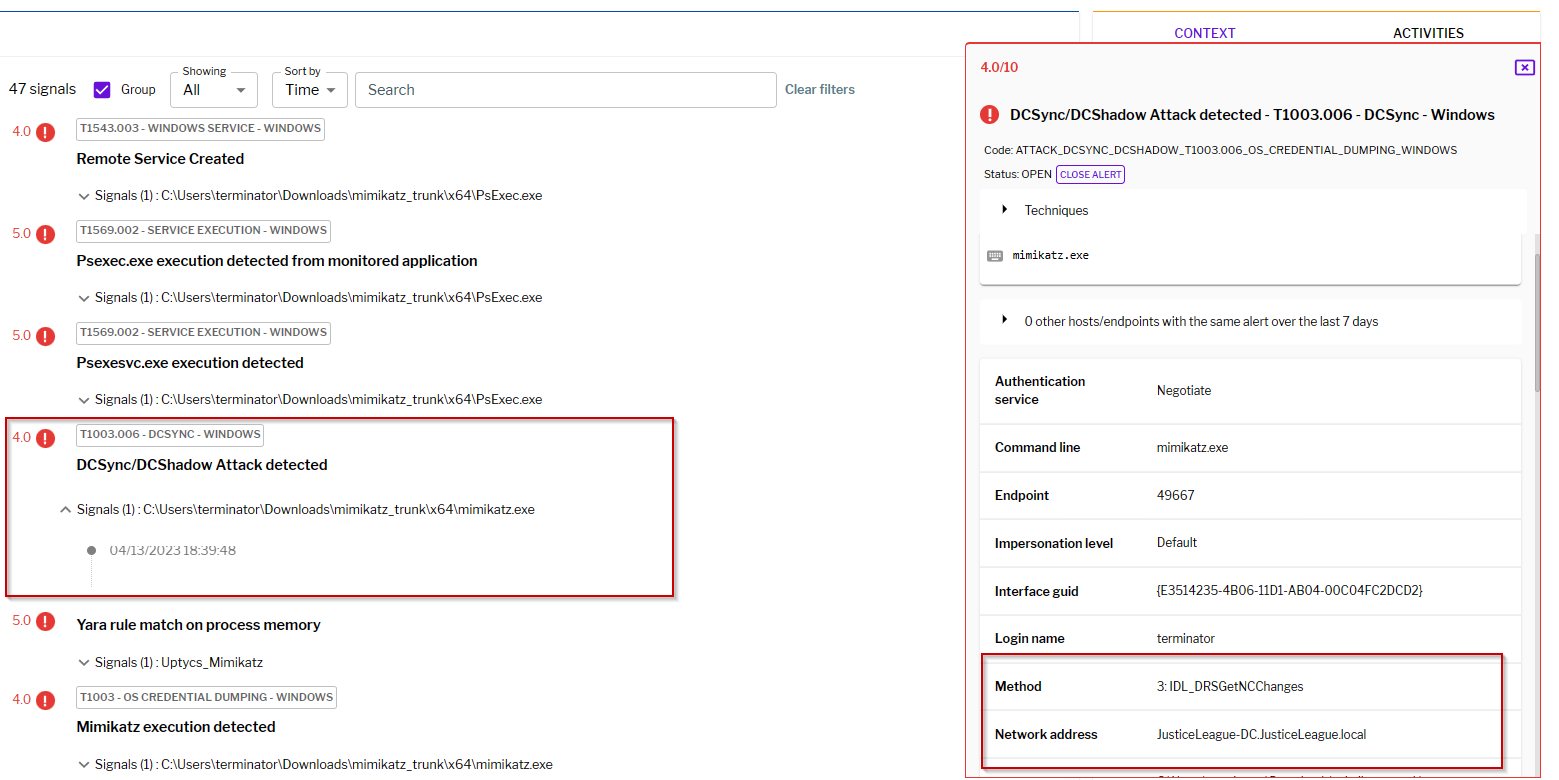 Figure 4 – Uptycs Detection of DCSync Attack on Domain Controller
Figure 4 – Uptycs Detection of DCSync Attack on Domain Controller
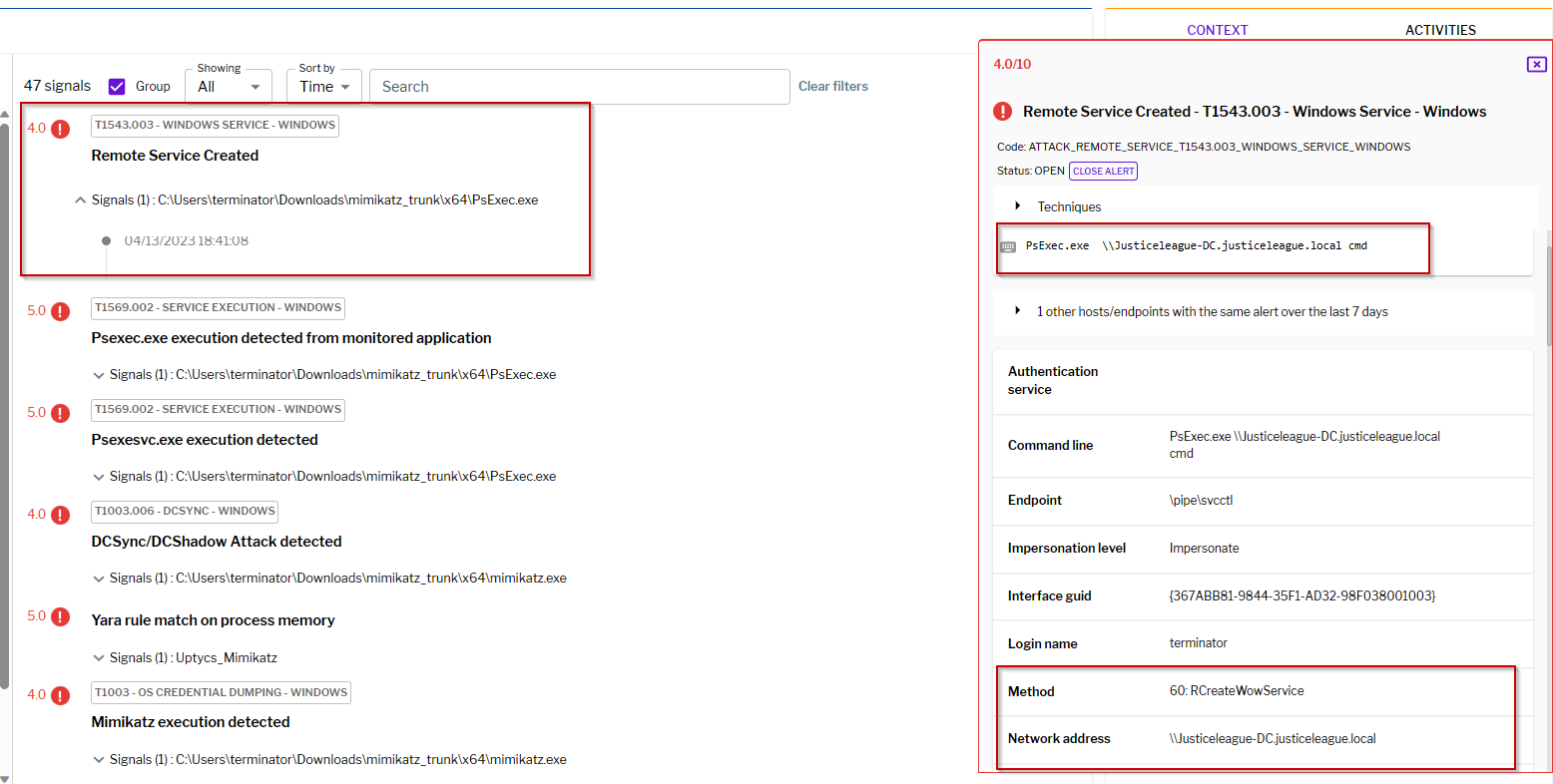
Figure 5–Uptycs Detection of Remote Service Creation on Domain Controller
Signals based on advanced correlation
To effectively identify and detect highly sophisticated attacks, such as the persistent and widely employed Kerberos Attack, Pass the Hash, and Pass the Ticket techniques, we have implemented additional signals that rely on telemetry correlation techniques applied to a multitude of underlying metrics.
These signals serve as vital indicators in our defense mechanisms, enabling us to identify and respond to these malicious activities proactively. We can uncover patterns and anomalies indicative of these specific attack methods by analyzing and correlating various metrics. This comprehensive approach allows us to stay ahead of sophisticated adversaries and fortify our security measures, safeguarding our systems and data from the potentially devastating consequences of such attacks.
Here is an illustration of how Uptycs XDR can detect the above-mentioned attacks:
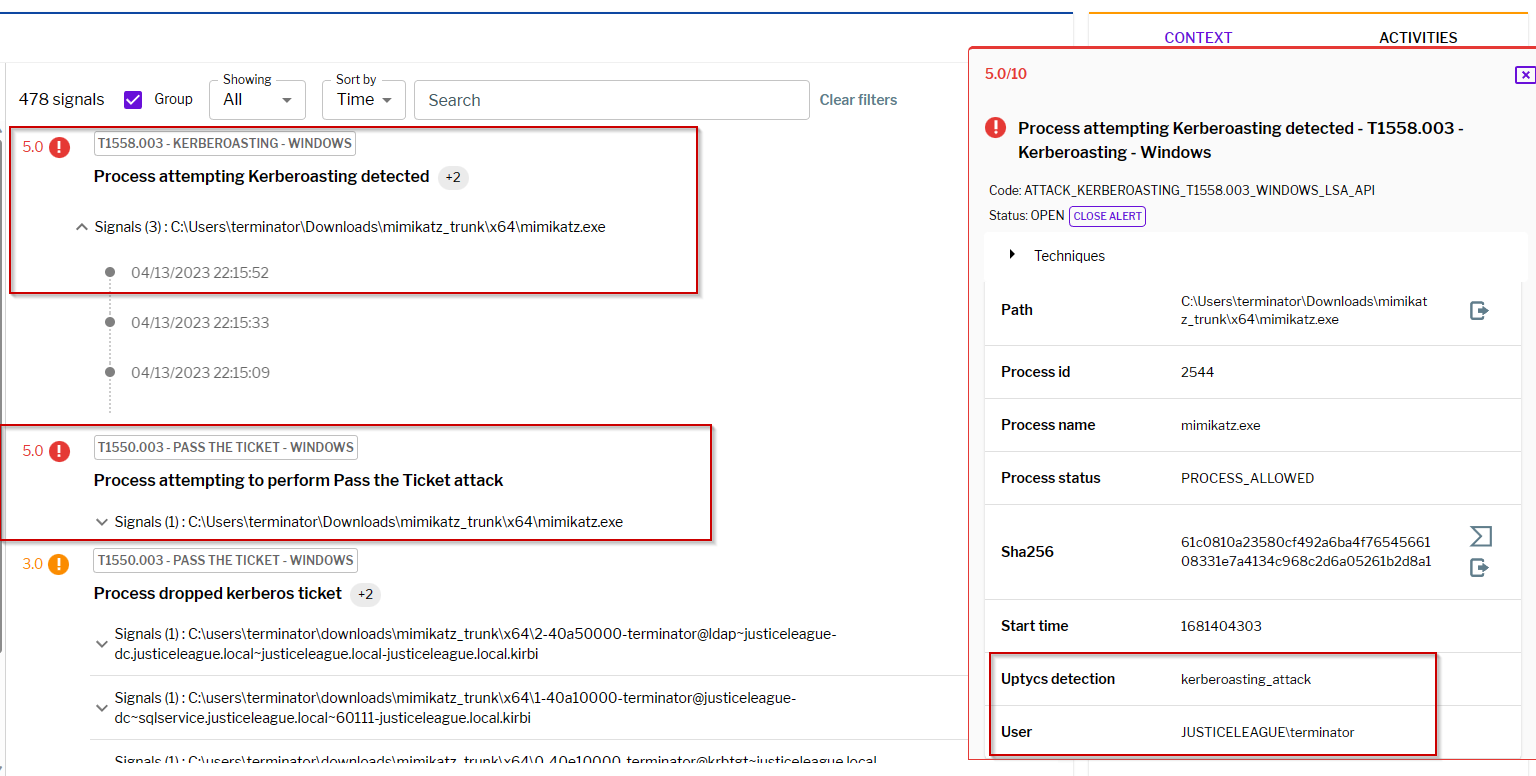 Figure 6 – Uptycs Detection of Kerberos and Pass the Ticket Attack
Figure 6 – Uptycs Detection of Kerberos and Pass the Ticket Attack
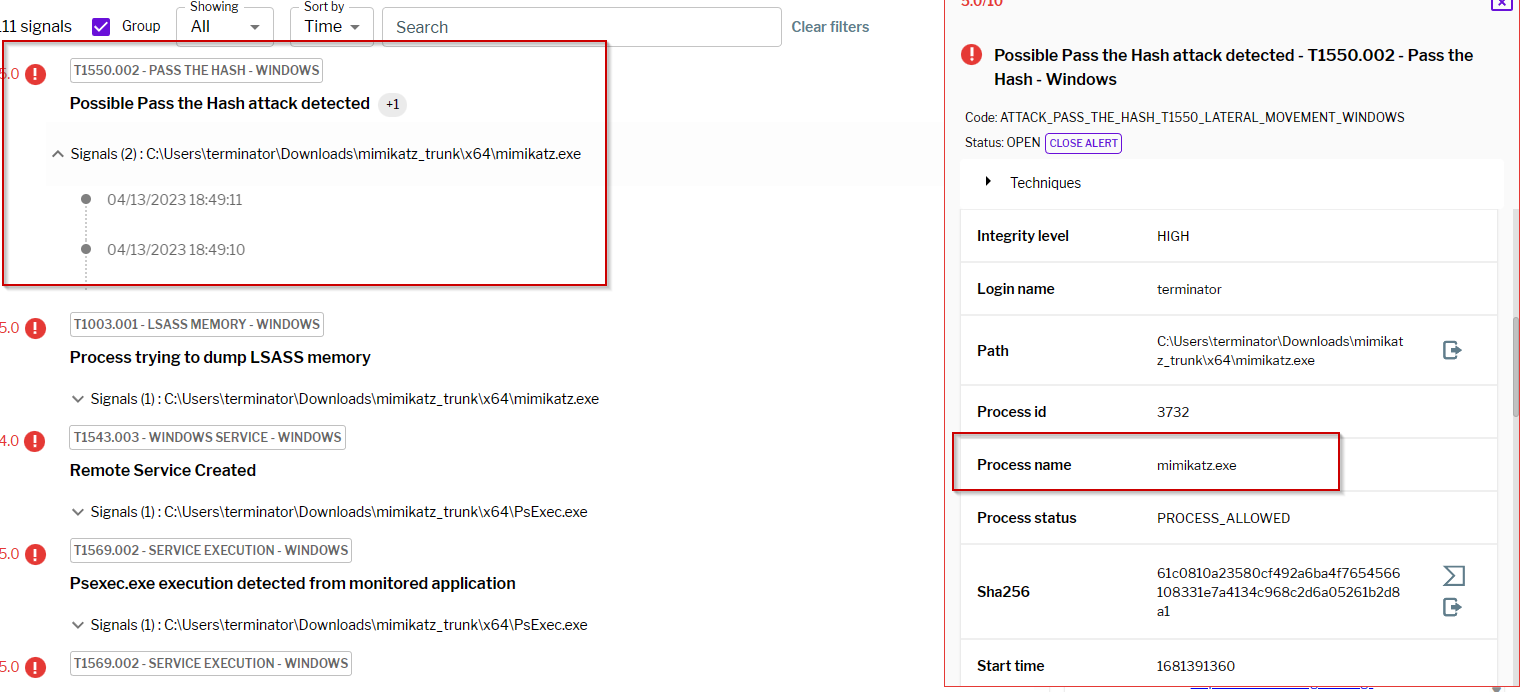 Figure 7 – Uptycs Detection of Pass the Hash Attack
Figure 7 – Uptycs Detection of Pass the Hash Attack
With Uptycs Protect enabled, users can respond proactively to alerts by taking manual action or automating responses, such as blocking suspicious activities or quarantining hosts.
Conclusion
Sophisticated attacks typically involve the compromise of multiple systems within a network. In such scenarios, detecting and correlating lateral movement becomes crucial. When you use Uptycs XDR for threat detection you can effectively prioritize incidents and gain a comprehensive understanding of the attack progression.
By analyzing and correlating the various lateral movement activities, we can establish the connections between compromised systems, allowing us to piece together a clear picture of how the attack has unfolded and spread across the network. This valuable insight enables us to significantly enhance our incident response capabilities and bolster our defenses against sophisticated and multi-faceted cyber threats.







