Uptycs Incident Response Capability
Detect, protect, and analyze incidents with Uptycs, including post-incident analysis, containment, recovery, and hygiene. Our comprehensive incident response capability ensures that organizations can act swiftly and effectively in the face of emerging threats.
CNAPP Visibility That Reliably Scales
What We Do
Incident Response with Uptycs
Detection, Protection, and Analysis
Identify and confirm security incidents and protect from malicious activity
Incident Response with Uptycs
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Identify and confirm security incidents and protect from malicious activity
Perform root cause analysis of the incident
Map malicious activity to MITRE ATT&CK Framework and correlation with threat intelligence.
What We Do
Incident Response with Uptycs
Identify and confirm security incidents and protect from malicious activity
- Act on the telemetry within seconds of occurrence
- Scan process memory and files on disk using Yara rules to detect 700+ malicious toolkits
- Behavioral rules for unusual system behavior
- Monitor for anomalous behavior
- File Integrity Monitoring
- Inventory of your infrastructure
- Catalog of all software and related licensing information
Detection
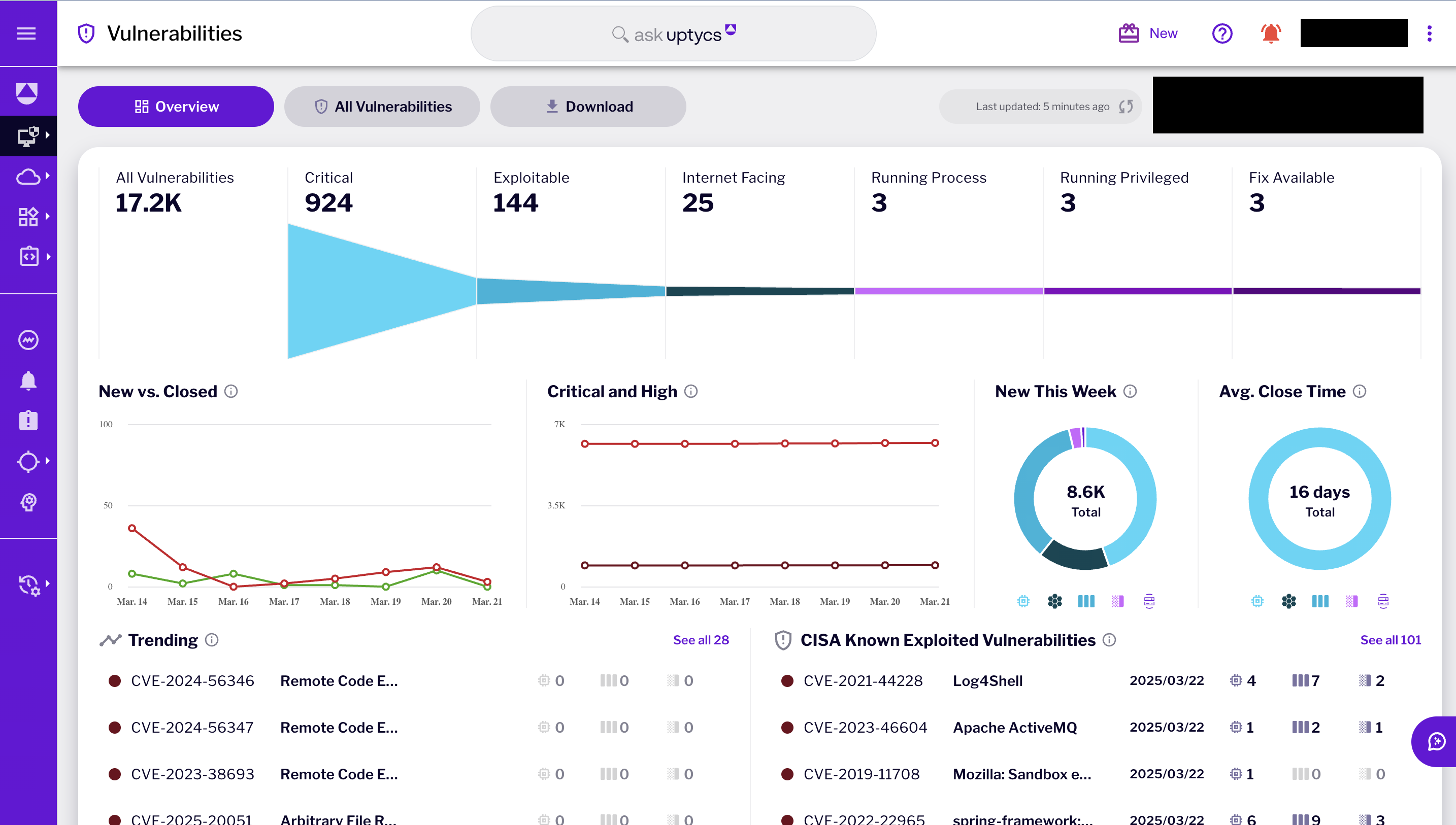
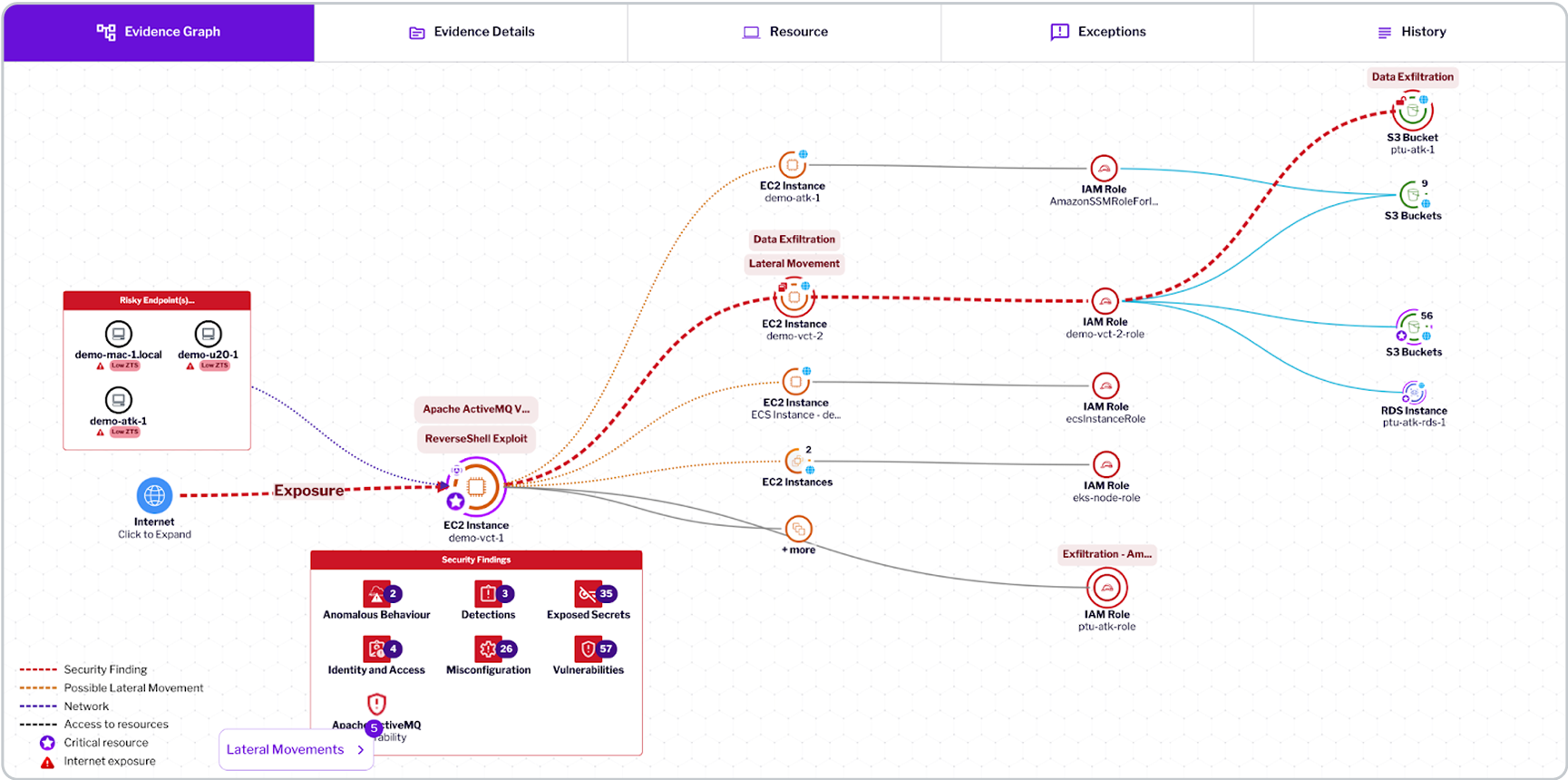
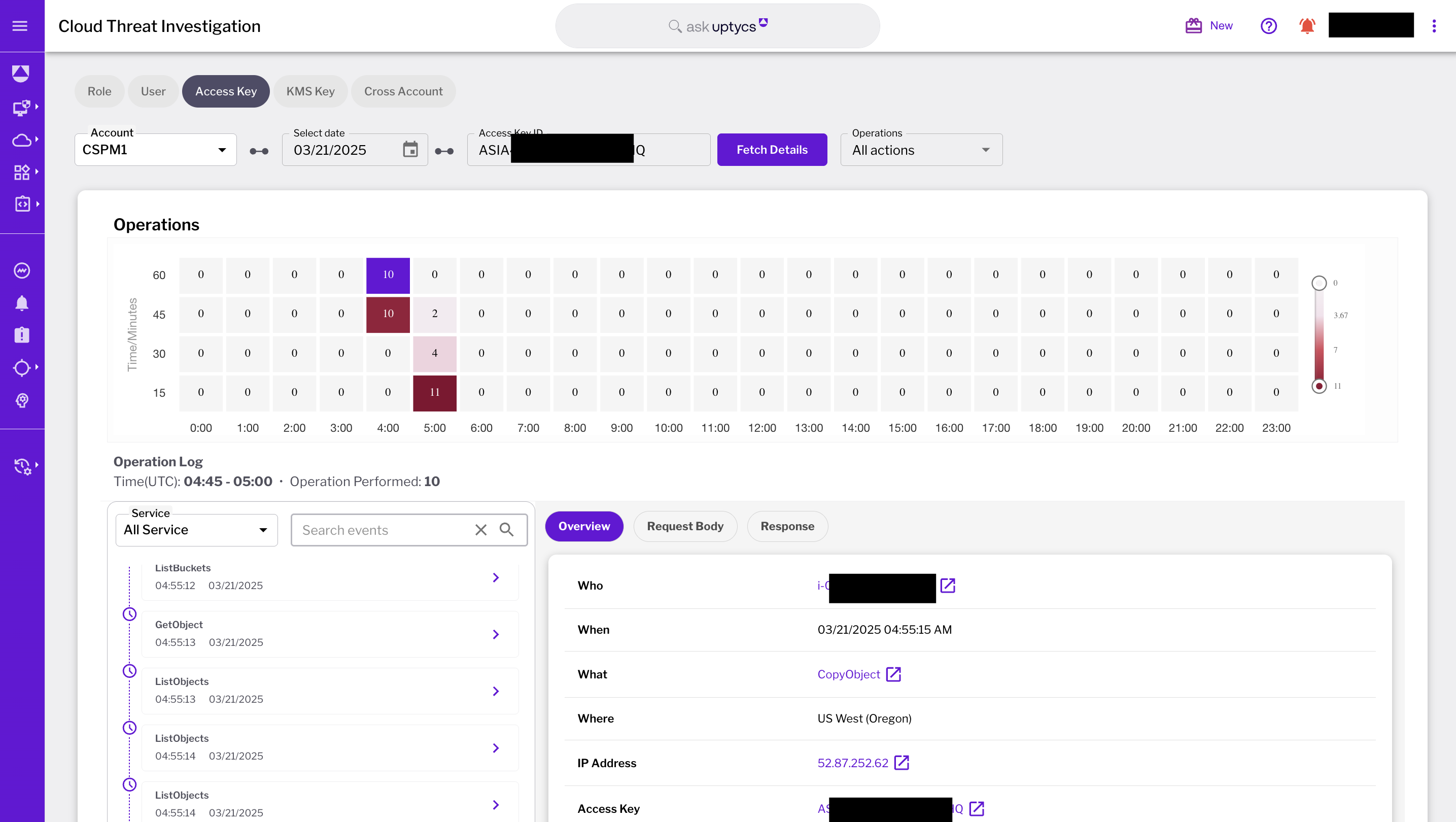
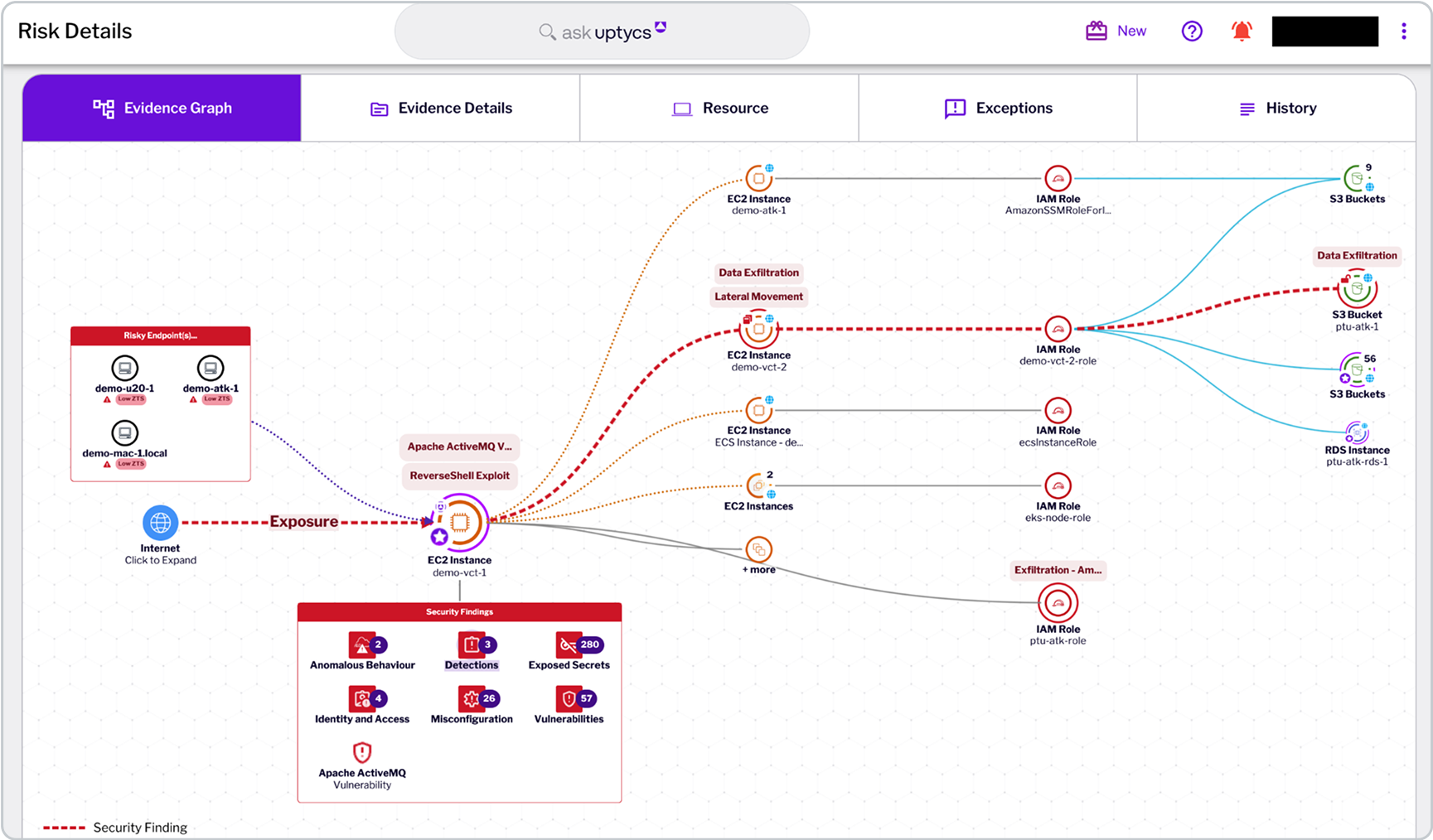
Uptycs CNAPP provides a comprehensive view of the malicious activity discovered in your cloud environment. Using the configuration and API activity data (e.g. Cloudtrail), a detailed account of how the malicious activity and when the malicious activity occurred is shown in a graphical visualization. What misconfiguration led to the internet exposure, what vulnerability led to the attacker getting a foothold in a virtual machine are clearly shown in the evidence graph. With the telemetry from the optional sensor in your virtual machines, Uptycs is able to detect that the attacker executed several AWS commands using the AWS CLI, assumed roles and executed an ssh command to move laterally to a neighboring VM. This deep visibility significantly enhances your incident response capability in dynamic cloud environments.

Uptycs provides context and evidence around what happened, when it happened, how it happened and who was responsible. In addition to the evidence, Uptycs provides remediation actions to contain the malicious activity—key elements of a strong incident response capability.

To protect from future threats Uptycs provides recommendations to right size your configuration. After analyzing the network activity across your environment for up to 90 days, Uptycs recommends the right Security group recommendation based on actual observed traffic. After observing the usage (this data comes from tracking the Cloudtrail activity for up to 90 days) of Roles, Users, Keys and Permissions used in your environment Uptycs provides recommendations to rightsize IAM policies.
Recommendation to rightsize IAM Policy:

Recommendation to rightsize Security Group configuration:


We also know that the virtual machine has exploitable vulnerabilities. See below for all of the vulnerabilities found.

So far we have seen evidence that a malicious actor leveraged internet exposure and took advantage of the ActiveMQ vulnerability to get a foothold on the virtual machine. What did the actor do after gaining a foothold? If the victim machine is running an Uptycs sensor, we have full visibility into every single command executed by the malicious actor. This level of visibility is essential for any organization looking to improve its incident response capability.
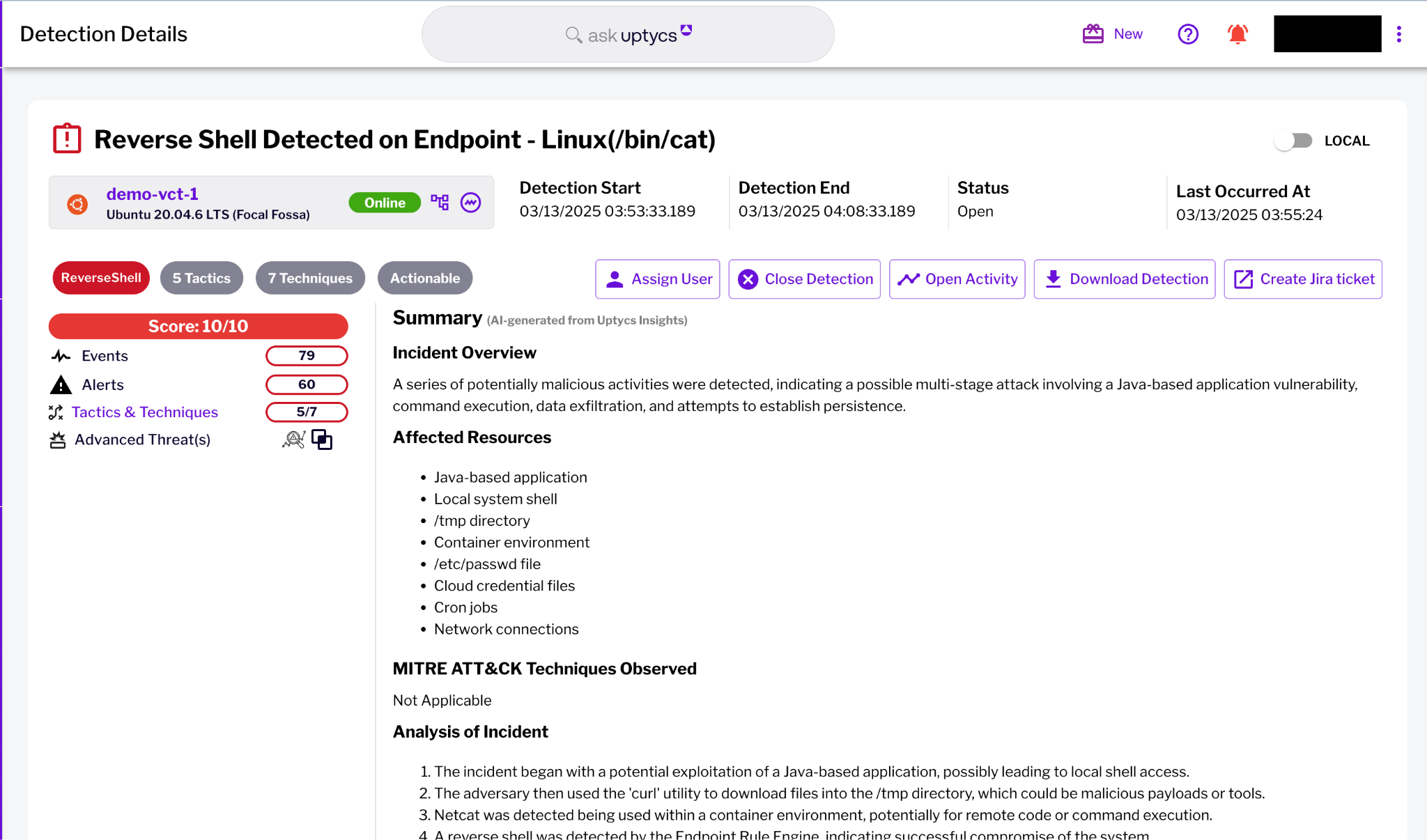
AI summarizes malicious activity by analyzing all signals contributing to the detection through an LLM. This summary offers security analysts a concise incident overview, highlighting observed MITRE techniques and tactics, along with actionable remediation recommendations.

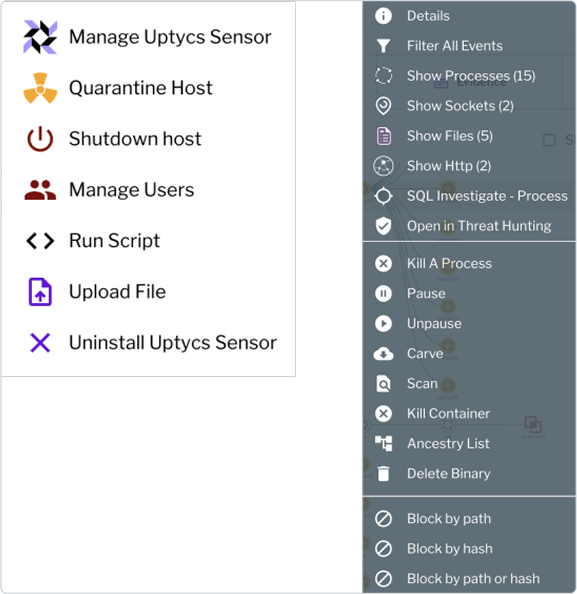
What did the malicious actor do? Every single command executed, every socket connection made, every domain lookup done are captured in the graph shown below. The details of the command line, process ancestry etc are captured. Get a clear view of all of the activity. Take remediation action like killing a process, carving process memory, deleting a file, quarantining the host etc.

Look into every single command executed by the malicious actor.

Take an in-depth look at all of the interesting signals produced. Every signal is mapped to the MITRE tactic and technique. All signals are scored and the entire detection gets a composite score that indicates the severity of this detection.

Take remediation action like shutting down/restarting the host, enable/disable users, quarantining the host, running any arbitrary script on the host.

Protection
Monitor and protect instantly against malicious activity like reverse shells, coin miners, ransomware. Act on the telemetry within seconds of occurrence

Analysis
Map all malicious activity in your environment to MITRE ATT&CK Framework and correlation with threat intelligence

- Run Live Investigations across your infrastructure from SaaS Console
- Run commands/scripts across your infrastructure from SaaS Console
- Hunt across endpoints, Kubernetes nodes, cloud resources. Telemetry from all sources is stitched together by Uptycs, makes root cause analysis quick and accurate
- Historical Look Back, store all activity in your infrastructure for any number of days.
- Carve files for forensic investigation
- Carve process memory for forensic investigation
- Scan entire disk for malicious files
- Discover unmanaged assets
Cybersecurity post-incident forensic tools help organizations investigate the root cause of attacks, identify compromised systems, and collect evidence for legal or compliance purposes. These tools enable security teams to analyze system logs, user activity, system call activity, and file changes to reconstruct the sequence of events, detect persistence mechanisms, and prevent future threats. Without effective forensic capabilities, organizations risk prolonged exposure to attackers, data loss, and compliance violations. Implementing robust forensic analysis tools ensures a swift, accurate, and comprehensive response to security incidents, ultimately strengthening an organization's overall incident response capability.
Hunt across historical data, start your hunt with the information you have, like suspicious user name, suspicious process name etc. Understand the timeline of malicious activity. Were any malicious artifacts left behind? Clean up using remediation scripts. Quarantine a contain the malicious activity.


Hunt across your cloud. What API call did a user/role/key execute. In what sequence were the calls executed. Get complete details on data exfiltration, what file was stolen from which bucket.

Monitor your infrastructure in real time. Carve files and process memory to your laptop for forensic investigation.


Detection, Protection & Analysis
-
Act on the telemetry within seconds of occurrence
-
Scan process memory and files on disk using Yara rules to detect 700+ malicious toolkits
-
Behavioral rules for unusual system behavior
-
Monitor for anomalous behavior
-
File Integrity Monitoring
-
Inventory of your infrastructure
-
Catalog of all software and related licensing information
Immediate containment after a cyber attack is crucial to prevent further spread, data exfiltration, and financial losses while preserving forensic evidence for investigation. It helps minimize downtime, disrupts attacker persistence, and ensures regulatory compliance. Rapid action also protects business operations, maintains stakeholder trust, and sets the stage for effective recovery and remediation.

Detection, Protection & Analysis
-
Act on the telemetry within seconds of occurrence
-
Scan process memory and files on disk using Yara rules to detect 700+ malicious toolkits
-
Behavioral rules for unusual system behavior
-
Monitor for anomalous behavior
-
File Integrity Monitoring
-
Inventory of your infrastructure
-
Catalog of all software and related licensing information

Immediate containment after a cyber attack is crucial to prevent further spread, data exfiltration, and financial losses while preserving forensic evidence for investigation. It helps minimize downtime, disrupts attacker persistence, and ensures regulatory compliance. Rapid action also protects business operations, maintains stakeholder trust, and sets the stage for effective recovery and remediation.
Cybersecurity hygiene is crucial because it helps prevent attacks, reduce vulnerabilities, and maintain a strong security posture. Good hygiene practices—such as regular software updates, compliance to best practices, compliance to industry standards, and employee awareness training—minimize the risk of breaches and malware infections. It also ensures compliance with security regulations, protects sensitive data, and enhances incident response capability. Just like personal hygiene prevents illness, cybersecurity hygiene proactively safeguards systems from threats, reducing the likelihood of costly and disruptive cyber incidents.



Detection, Protection & Analysis
-
Act on the telemetry within seconds of occurrence
-
Scan process memory and files on disk using Yara rules to detect 700+ malicious toolkits
-
Behavioral rules for unusual system behavior
-
Monitor for anomalous behavior
-
File Integrity Monitoring
-
Inventory of your infrastructure
-
Catalog of all software and related licensing information

Why Uptycs
Reliable Incident Response
Uptycs CNAPP consolidates cloud security silos into a unified platform, providing a single security console, policy framework, and data lake. This unification enables greater automation, simplifies policy enforcement, and extends security coverage, all while reducing security risks and improving your organization's incident response capability.
Pricing starts at just $2/endpoint/month, offering unmatched value for streamlined osquery fleet management.
Expand your capabilities with add-ons designed to provide deeper insights and operational flexibility. These optional features make it easy to tailor Uptycs Nexus to your needs.
Optional Add-on
Flight Recorder ($1/endpoint/month): Store collected data for seven days, enabling historical data analysis and easier investigations.
Optional Add-on
Export Raw Telemetry ($1/endpoint/month): Export telemetry data in compressed ORC or JSON format to object stores like S3 for long-term usage and integrations.
Optimize Fleet Management with Uptycs Nexus:
Affordable Pricing and Flexible Add-Ons
Standard Price
Pricing starts at just $2/endpoint/month, offering unmatched value for streamlined osquery fleet management.
Optional Add-on
Flight Recorder ($1/endpoint/month): Store collected data for seven days, enabling historical data analysis and easier investigations.
Optional Add-on
Export Raw Telemetry ($1/endpoint/month): Export telemetry data in compressed ORC or JSON format to object stores like S3 for long-term usage and integrations.
Optimize Fleet Management with Uptycs Nexus:
Affordable Pricing and Flexible Add-Ons
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Pricing starts at just $2/endpoint/month, offering unmatched value for streamlined osquery fleet management.
Flight Recorder ($1/endpoint/month): Store collected data for seven days, enabling historical data analysis and easier investigations.
Export Raw Telemetry ($1/endpoint/month): Export telemetry data in compressed ORC or JSON format to object stores like S3 for long-term usage and integrations.
Explore our most popular tools and integrations below
Pricing starts at just $2/endpoint/month, offering unmatched value for streamlined osquery fleet management.
Flight Recorder ($1/endpoint/month): Store collected data for seven days, enabling historical data analysis and easier investigations.
Export Raw Telemetry ($1/endpoint/month): Export telemetry data in compressed ORC or JSON format to object stores like S3 for long-term usage and integrations.
Optimize Fleet Management with Uptycs Nexus:
Affordable Pricing and Flexible Add-Ons
Pricing starts at just $2/endpoint/month, offering unmatched value for streamlined osquery fleet management.
Flight Recorder ($1/endpoint/month): Store collected data for seven days, enabling historical data analysis and easier investigations.
Export Raw Telemetry ($1/endpoint/month): Export telemetry data in compressed ORC or JSON format to object stores like S3 for long-term usage and integrations.
Success Stories
“We've gotten a significant ROI on our Uptycs investment by playing to its strengths - the single data model and backend analytics.”

“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”

“I would not want to do security anywhere without this level of visibility.”