The current state of enterprise security: Fragmentation and fatigue
In a recent blog post, we discussed some of the issues with proprietary agents and the challenges they pose to enterprises. For example, most security solutions deploy separate and proprietary agents for audit and cloud compliance, with threat hunting tools or vulnerability scanning software, and incident response.
Solution silos with proprietary agents result in significant performance issues, escalating licensing costs, conflicts with other services running on the endpoints, maintenance headaches, difficulties with upgrades, and certification issues.
Moreover, it is difficult for most enterprises to break away from this paradigm, resulting in an array of point solutions implemented to cover the desired security functions across varied computing environments.
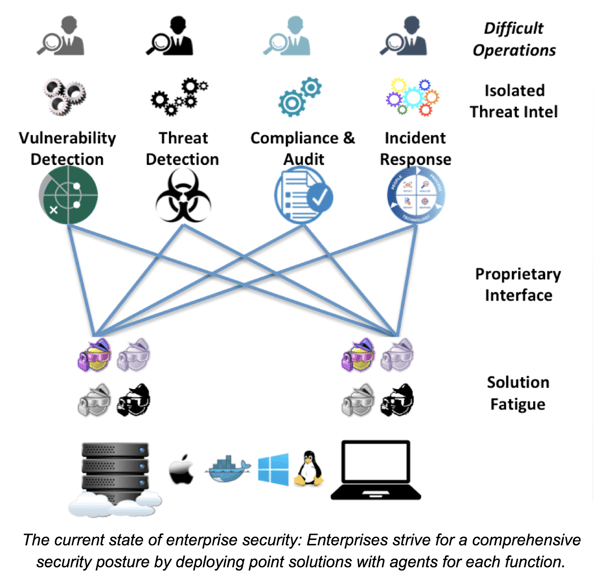
Because of this, most enterprises suffer from three main challenges in addition to agent fatigue:
- Siloed Solutions with proprietary interfaces: If you deployed several different solutions, your team has to learn how to use these solutions, each with its unique UI and data representation. Compounding this problem, you are adding more points of integration, more points of failure, and more sources collecting, creating, and manipulating data, which only adds to infrastructure complexity. Hiring, training, securing and monitoring are hard enough for one solution.
- Operational challenges: Security teams striving for operational efficiency are challenged with multiple solution silos, as expertise in one solution silo does not extend to another due to the proprietary nature of the solutions. This is a major concern for most organizations given the current industry shortage of cybersecurity skills.
- Isolated threat intel: Each solution silo ingests Threat Intel relevant to the supported security function and isolates it from other functions. This isolation leads to increased dwell time during incident investigation as it makes it challenging to gauge the broader impact to the security posture across the enterprise. For example, if vulnerability detection and endpoint threat detection are siloed solutions, each with its isolated Threat Intel, it is hard to correlate if a known software vulnerability led to data transmission to a destination with a known reputation.
Additionally, the irony of this strategy is that using multiple proprietary agents likely increases vulnerability in the long run.
Osquery offers a different approach
Instead of the siloed, “one agent per function” approach, engineers at Facebook decided to create an open, universal agent that could extract and normalize data from any operating system across a variety of computing environments. They called it osquery and in 2014 started an open source project on GitHub that has attracted well over 200 talented contributors to-date.
In addition to the ability to normalize system data and expose it as a relational database, osquery also uses SQL, one of the most popular and widely utilized database query languages. This means that you can now ask the same question, in the same way, across any mix of operating systems.
Osquery offers a disruption to and rethinking of the endpoint agent and security metrics using the structured approach of SQL with tables. With osquery, you have a single agent and an open universal source of tabular data that can be applied to solve a broad range of security use cases, accessed through a single interface via a standard query language.
Analyst firms, like 451 Research, have also taken notice of osquery and its unique placein the endpoint and cloud security markets with senior information security analyst Fernando Montenegro sharing, “Osquery is a very powerful co ncept, allowing for normalization across environments, and collaboration internally and within the open source community. The fact that security teams are becoming more adept at using open source components and with managing heterogeneous fleets points to continued momentum and increased adoption of osquery across the enterprise.” Read more about Fernando’s analysis of osquery and Uptycs in this exclusive 451 Research Market Impact Report.
ncept, allowing for normalization across environments, and collaboration internally and within the open source community. The fact that security teams are becoming more adept at using open source components and with managing heterogeneous fleets points to continued momentum and increased adoption of osquery across the enterprise.” Read more about Fernando’s analysis of osquery and Uptycs in this exclusive 451 Research Market Impact Report.
Osquery introduces the opportunity for collaboration across teams, eases learning curves, and can begin addressing the challenge of reducing the complexity of security infrastructure.
However, to fully realize the potential of osquery, organizations still need:
- A mechanism to configure, deploy and manage the osquery agent
- A place to store and analyze the system data that osquery produces
- Visualizations of the data to help solve for security use cases like intrusion detection, vulnerability management, audit/compliance, and fleet/workload visibility
- A mechanism to correlate system data with third-party Threat Intel and IOCs
- Alerts and workflows to handle and remediate suspicious activities
We see this as a tremendous opportunity - harnessing the potential of osquery and delivering it as a robust enterprise-grade security analytics platform that addresses security functions across the enterprise. This is much like the approach Salesforce adopted to address cross-functional business operations.
Uptycs sets its vision on building osquery security analytics at scale
Salesforce took the business operations market by storm - translating broad and complex business problems across sales, marketing, finance, and customer success into solutions using SQL to extract and then present data in meaningful ways. Inspired equally by the Salesforce approach and the challenges of today’s security practitioners, we have implemented a holistic approach using osquery and SQL to power the Uptycs Security Analytics Platform.
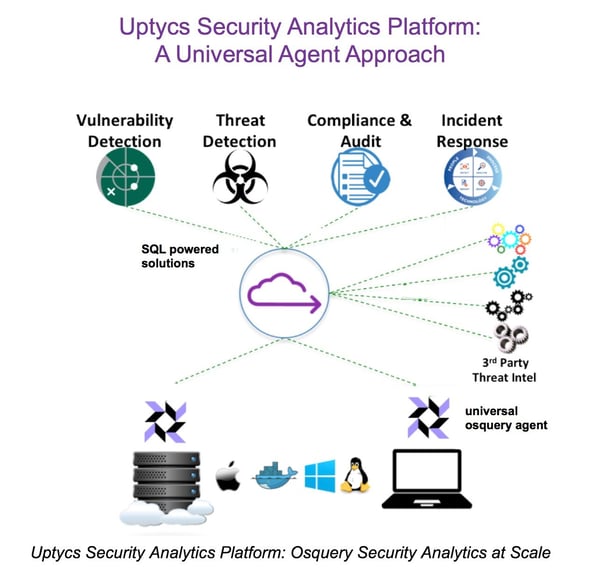
Our vision is to provide a cross-operating system solution for fleet visibility, intrusion detection, vulnerability management, and audit/compliance by providing meaningful views of data using SQL.
We believe this addresses the four most salient pain points of the fragmented security space:
- Eliminates agent fatigue: Uptycs leverages osquery’s universal open source agent to remove agent fatigue, lower overhead, and reduce the burden on processing power.
- Consolidates data collection: Osquery extracts rich system state information across operating systems and environments to help eliminate data collection silos.
- Provides integrated threat intel: Upytcs ingests third-party Threat Intel and normalizes this information into structured relational data that customers can automatically correlate with the stored and real-time visibility provided by osquery.
- Removes operational silos: A comprehensive and unified view of data used to solve a broad range of security use cases significantly reduces the cost and complexity of multiple operational silos.
Fernando Montenegro of 451 Research shares a further observation that, “The increased popularity of osquery as an open source agent may indicate what the future of endpoint security could look like: organizations collaborating on technology that address a wider variety of their security needs. Uptycs is betting on osquery for upending endpoint security - their combination of open source agent with cloud-based analytics opens up a number of possibilities.”
(Read more in the exclusive 451 Research Market Impact report: “
Uptycs emerges from stealth betting on SQL-based osquery for upending endpoint security.”)
We are excited to continue working with organizations of varying size and exploring ways to enable the fastest path to osquery value. Sometimes this means starting with a focused use case and expanding outward as the broader value of the Uptycs Security Analytics Platform is recognized. Sometimes it is a more rapid and expansive adoption of osquery for several security use cases.
We’d love to hear about your experience with osquery and the opportunities you see for how it can help deliver on the promise of upending endpoint visibility and addressing cloud workload security and monitoring.
Learn more about osquery: